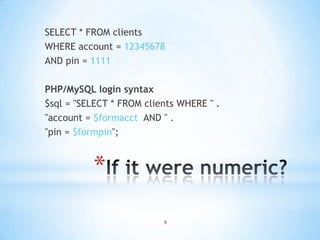
The document discusses SQL injection attacks and how they work. SQL injection occurs when user input is inserted directly into an SQL query string without proper validation or escaping. This allows attackers to alter the structure of the intended SQL query and potentially gain unauthorized access to sensitive data or make unauthorized changes to the database. The document provides examples of vulnerable queries and how attackers can exploit them to inject malicious SQL code. It also lists some common techniques used in SQL injection attacks and provides recommendations for preventing SQL injection vulnerabilities.