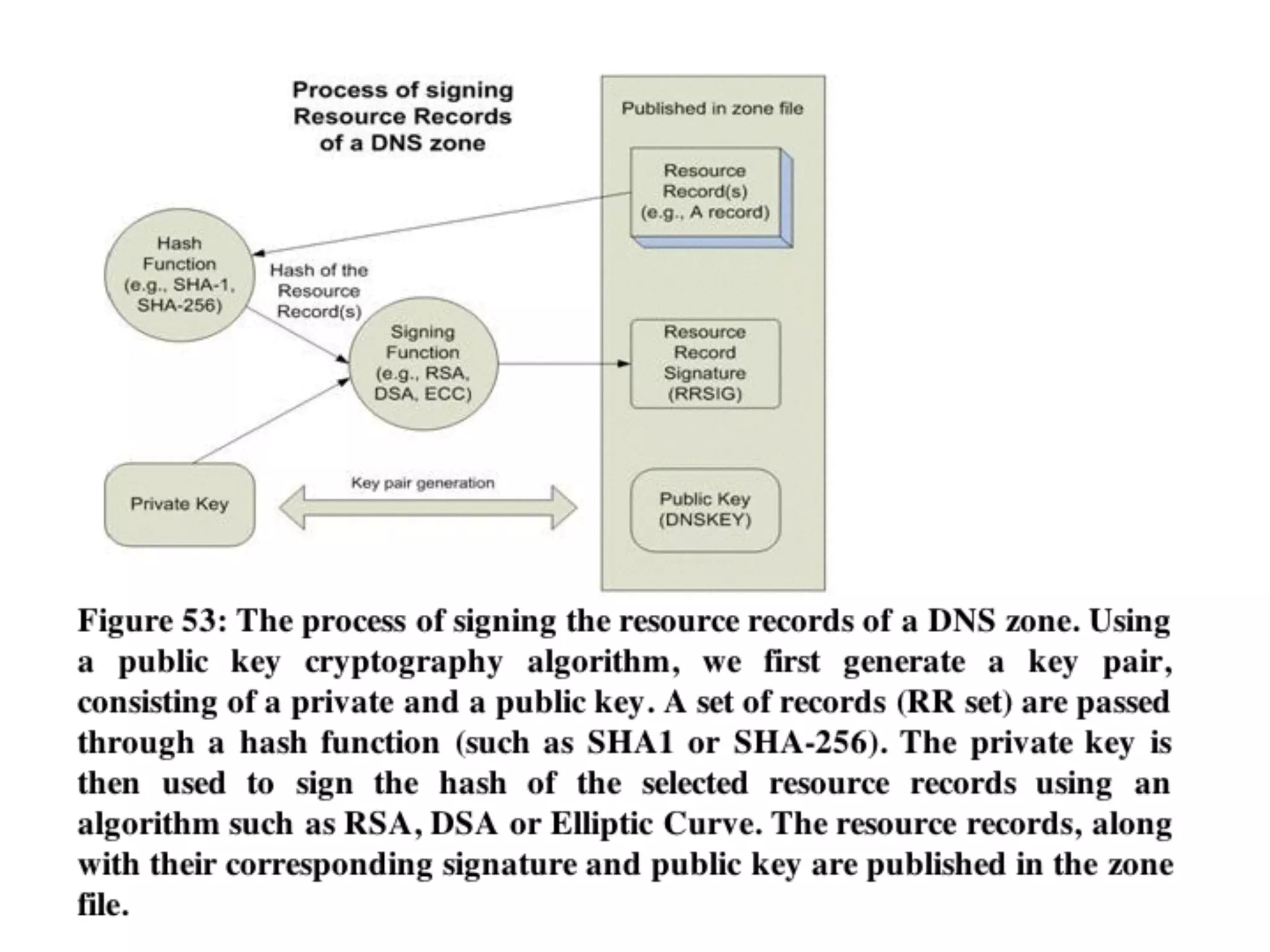
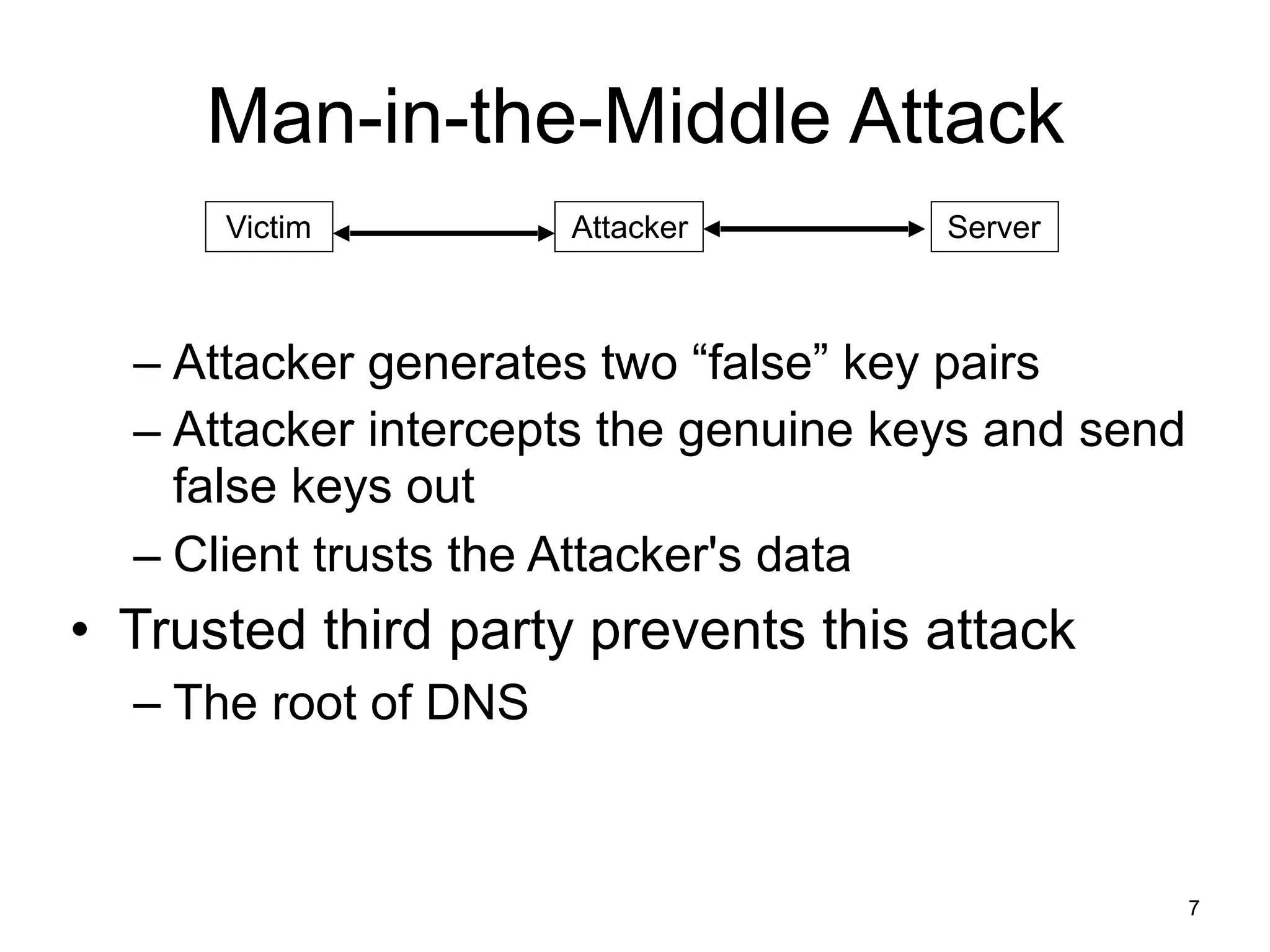
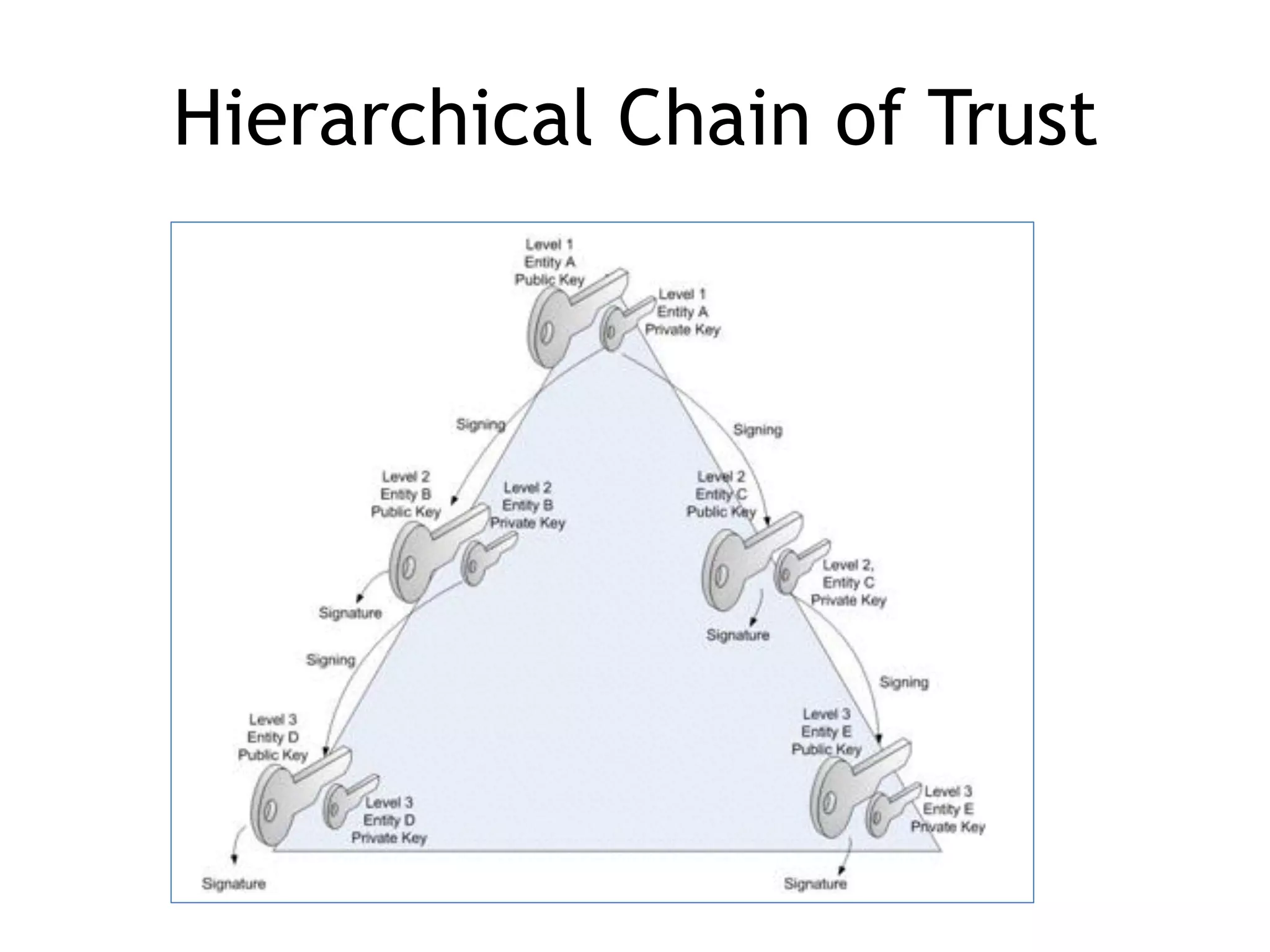
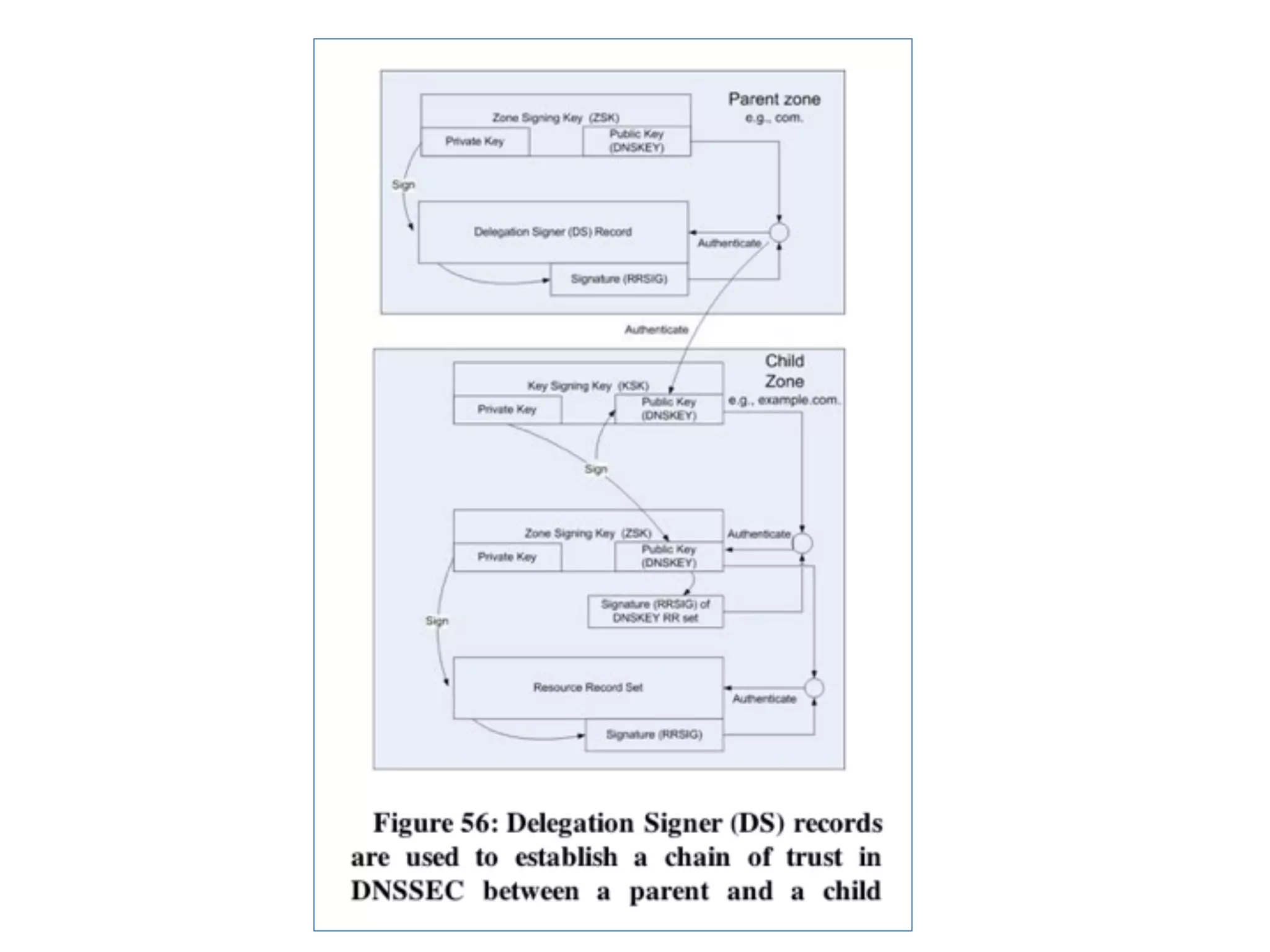
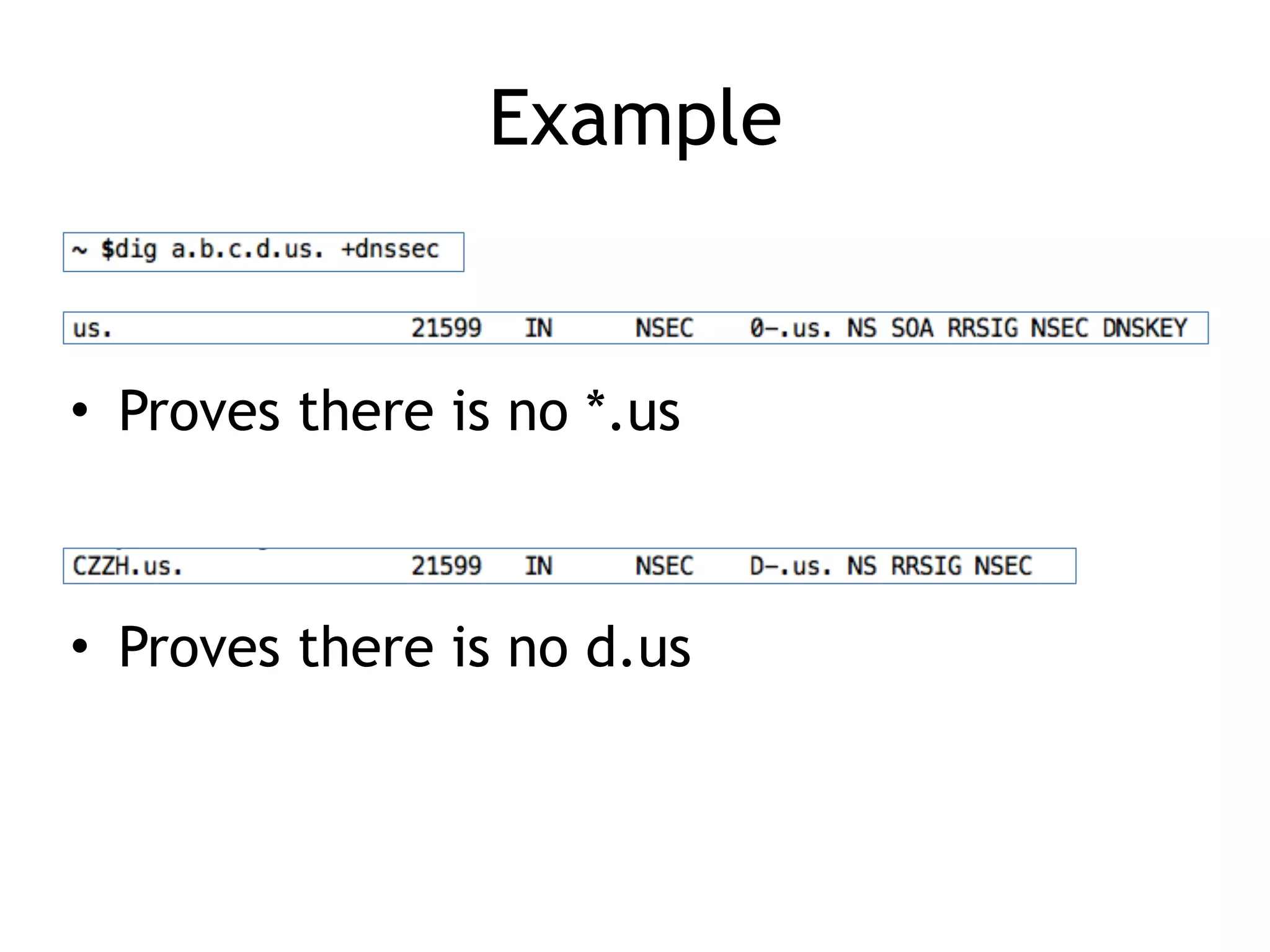
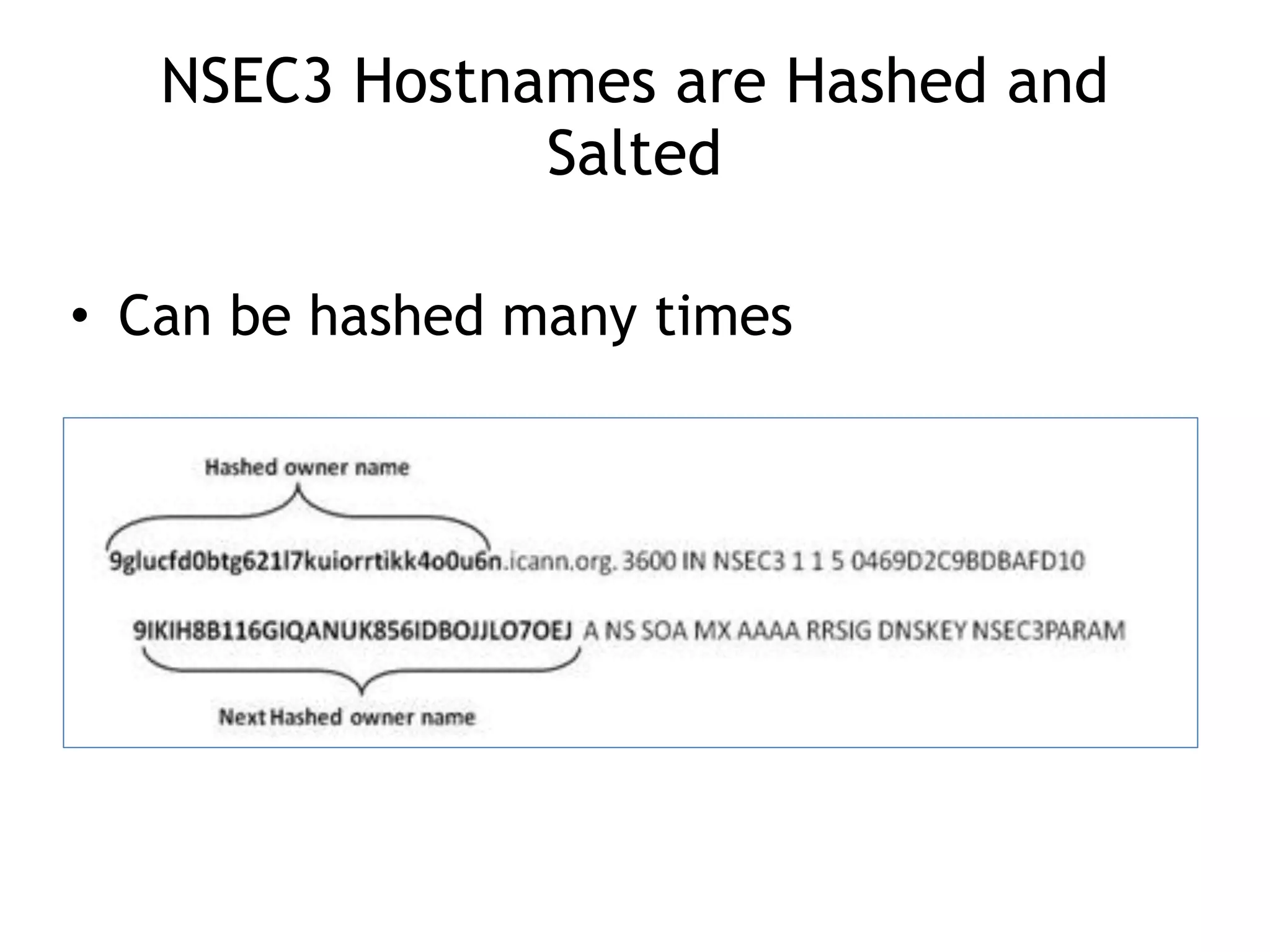
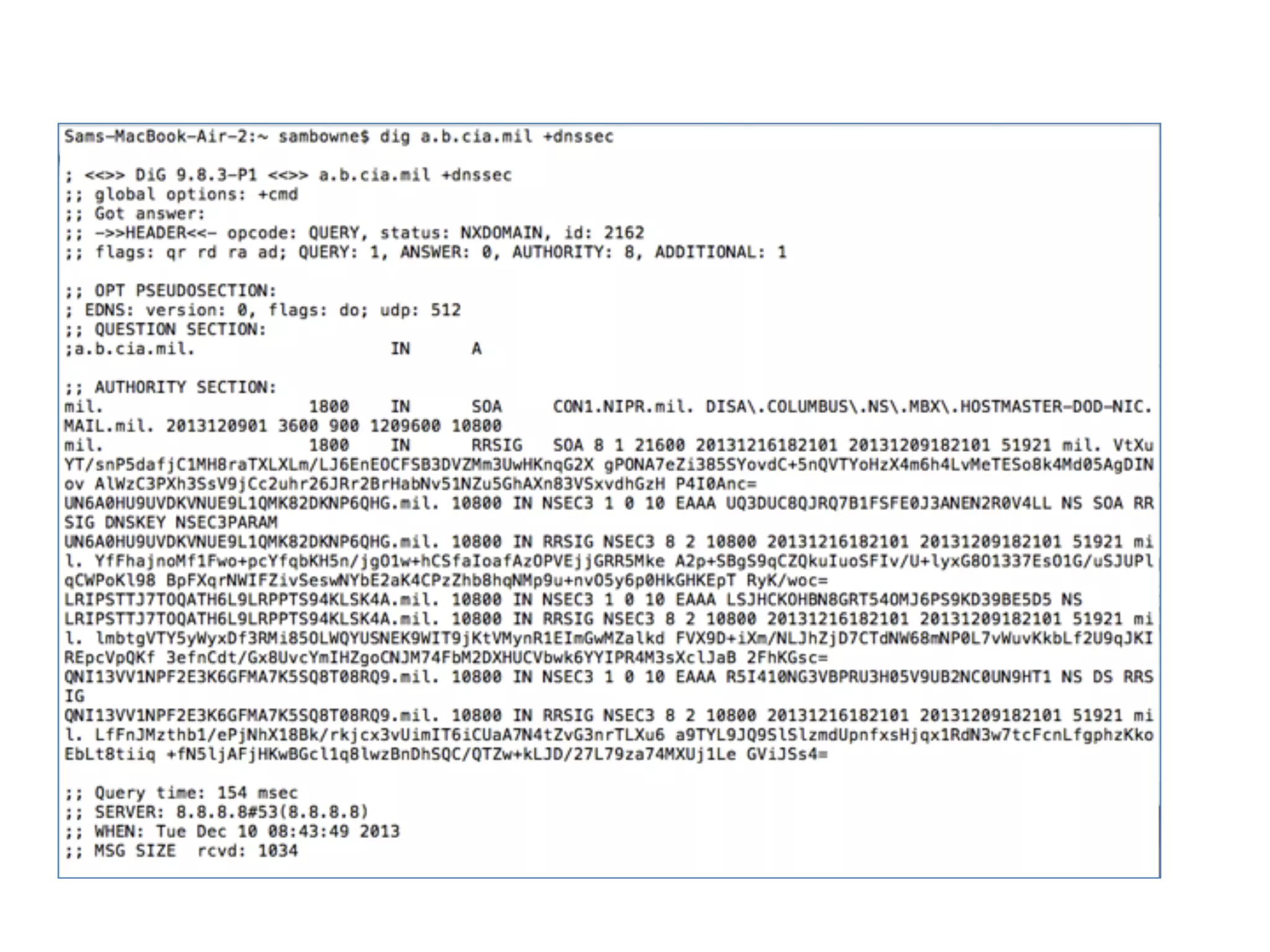
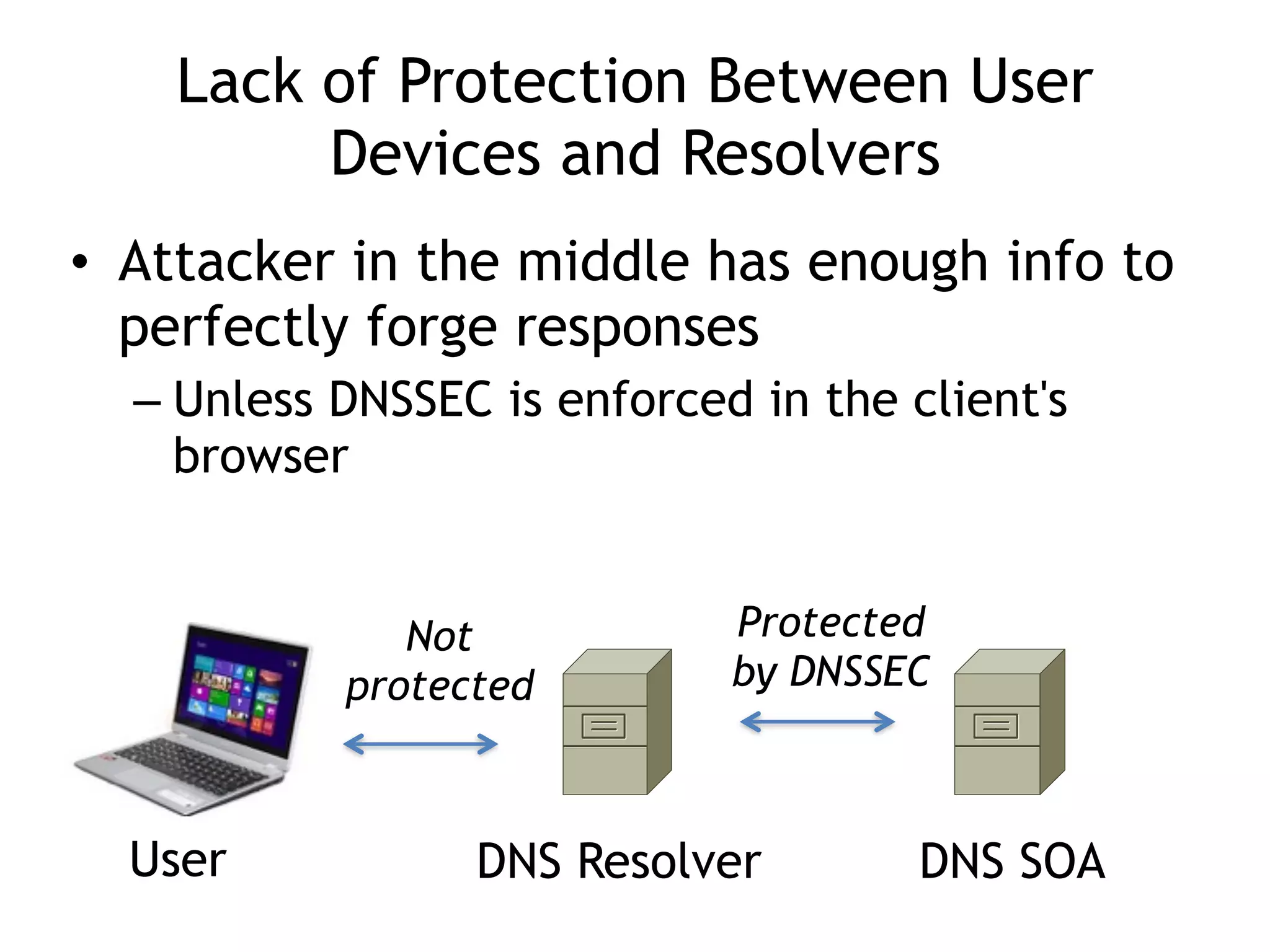
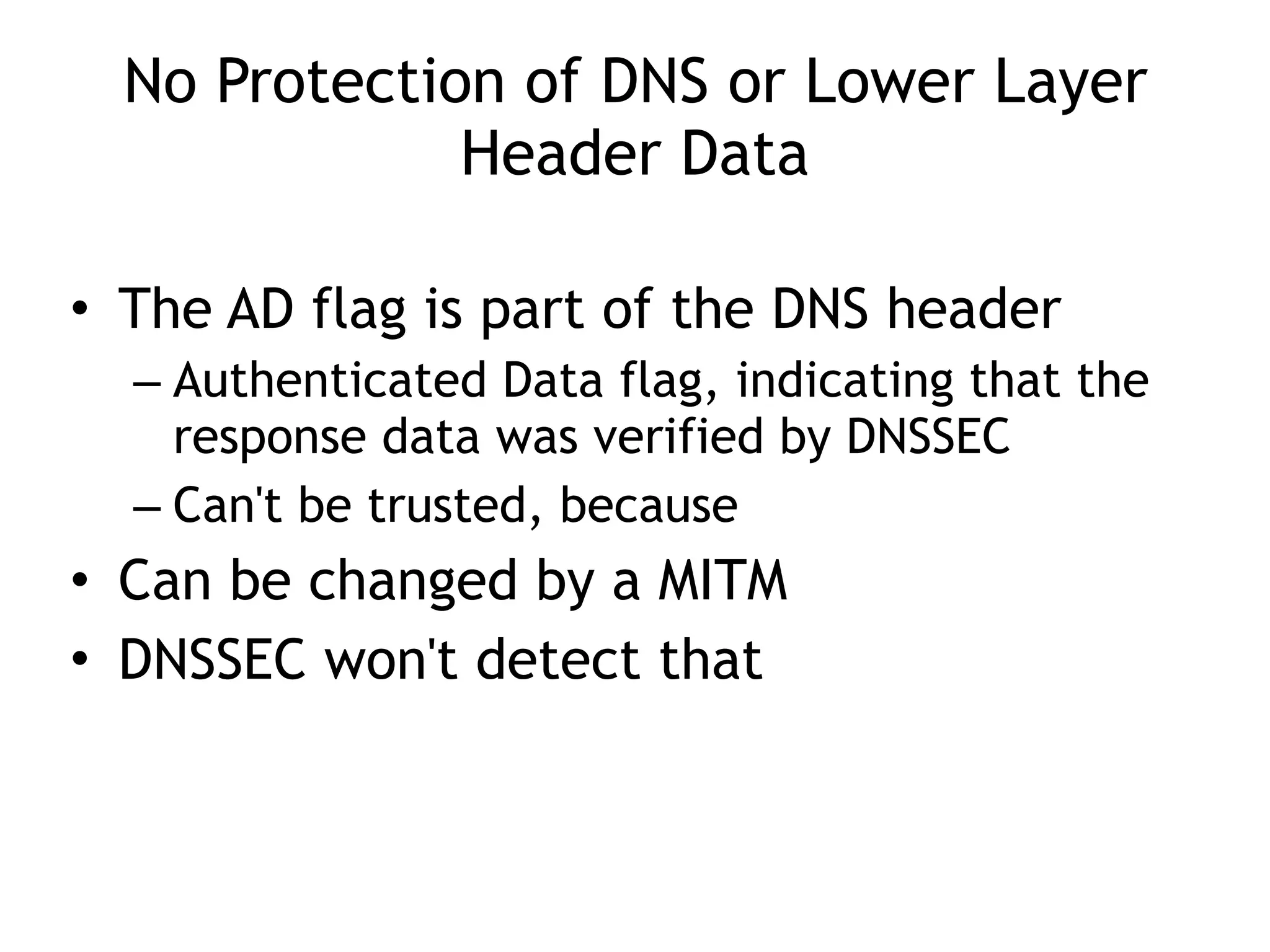
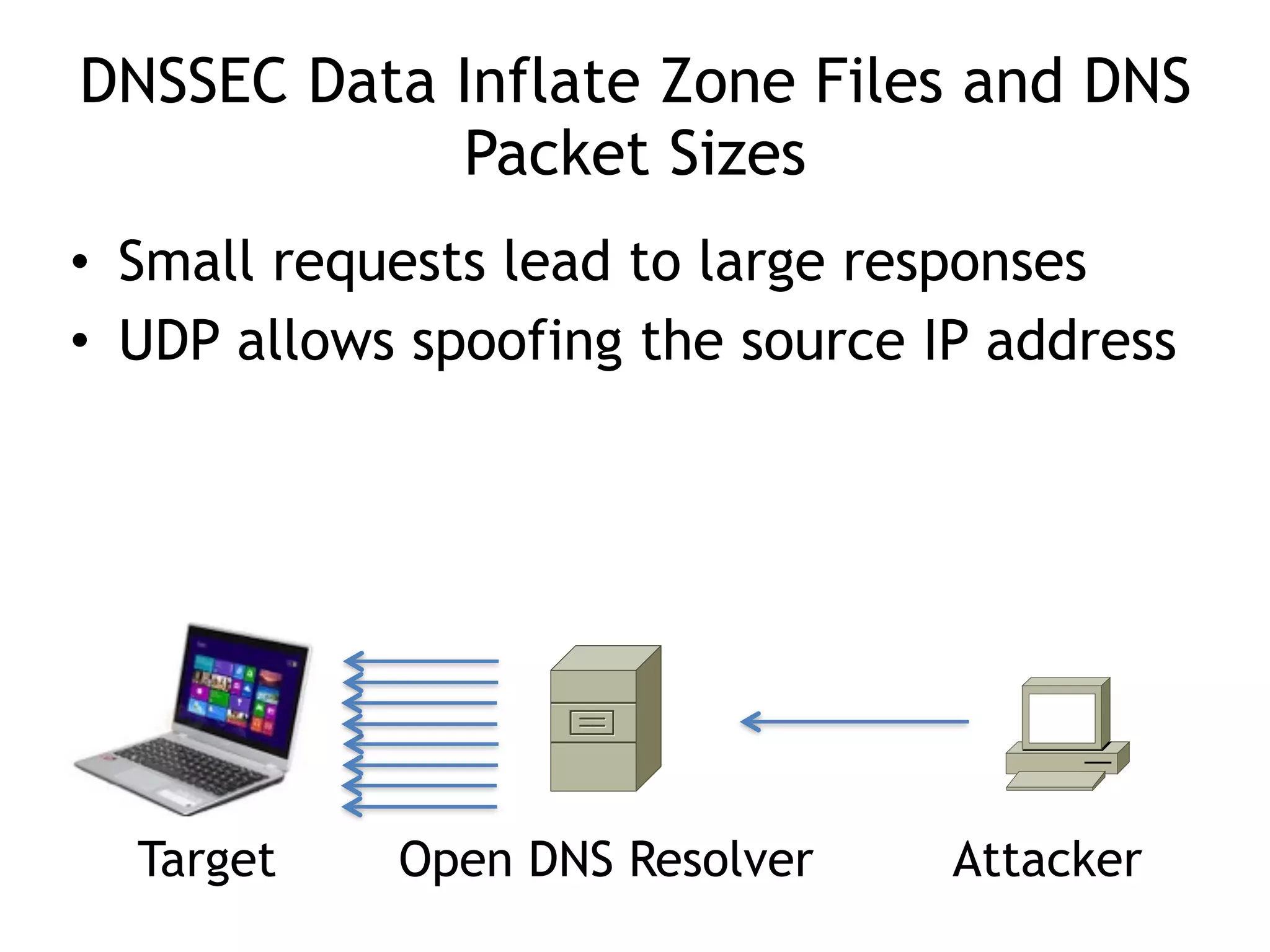
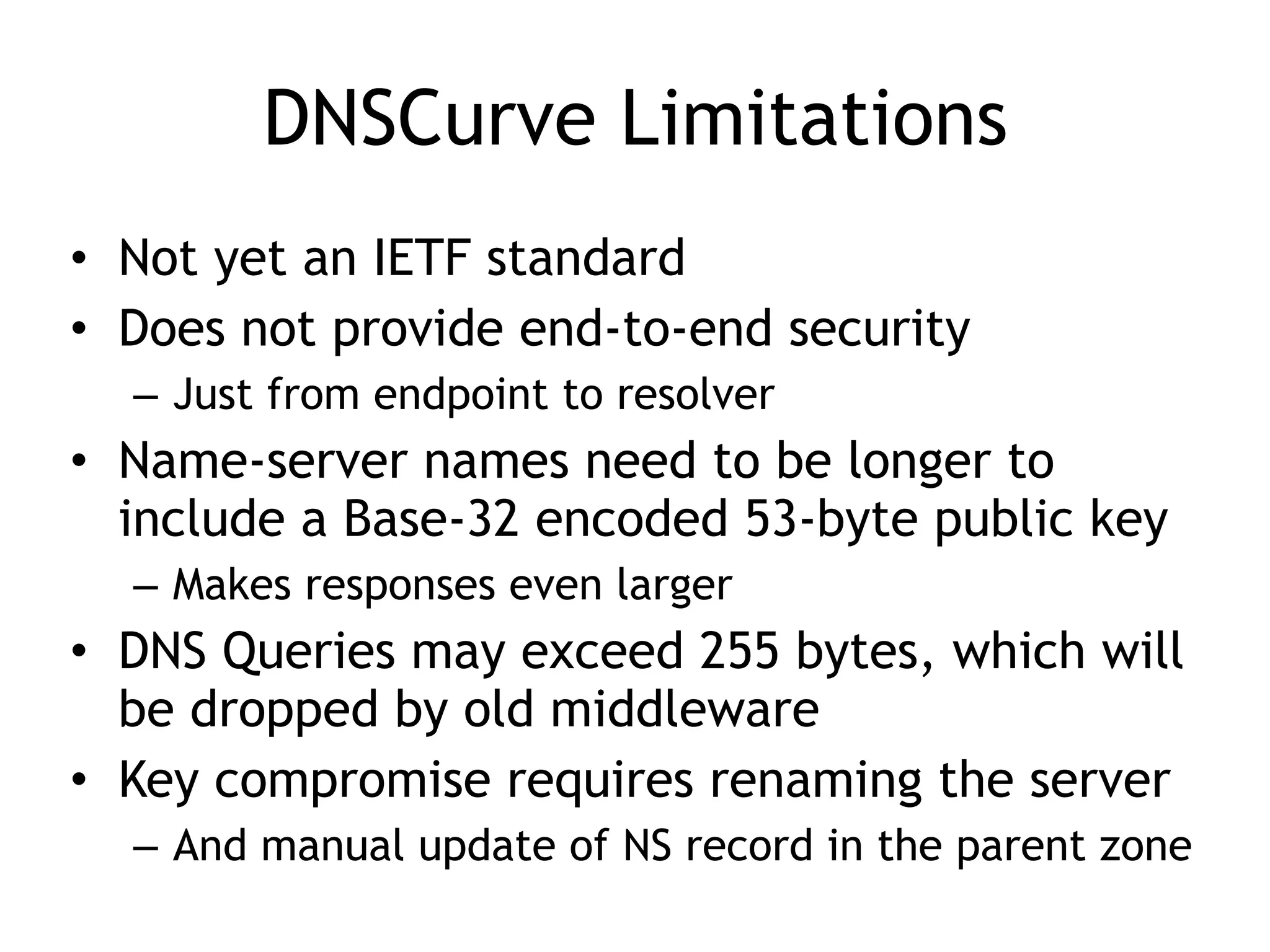
The document discusses DNSSEC, focusing on its objectives like data origin authentication and integrity, and details its development through various RFCs. It outlines vulnerabilities, such as man-in-the-middle attacks, along with limitations like lack of glue record protection and issues with key changes not propagating effectively. Additionally, it introduces DNSCurve for encrypted packets using elliptic curve cryptography but notes its limitations in providing end-to-end security.