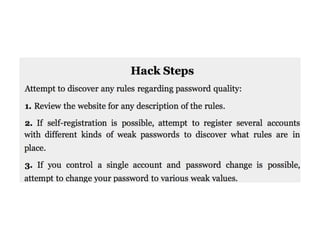
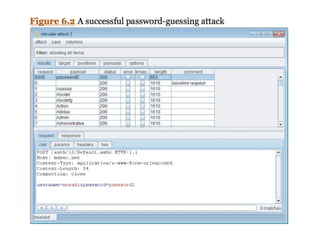
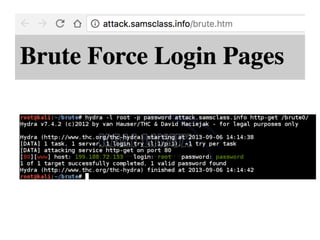
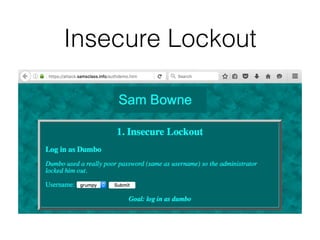
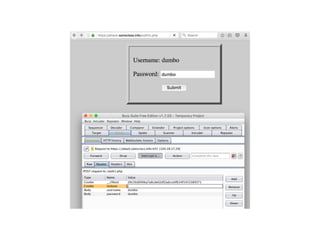
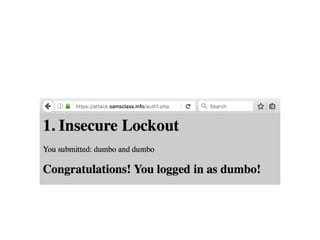
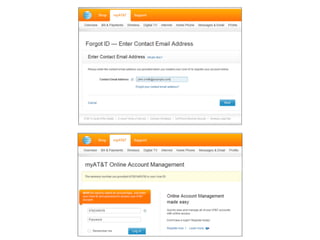
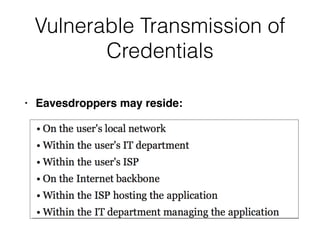
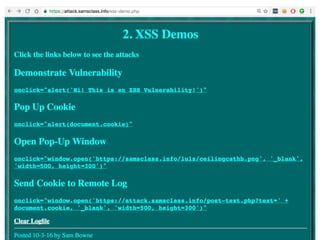
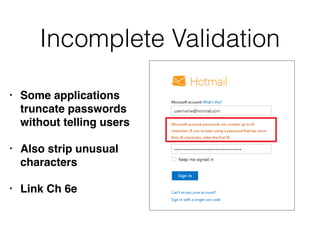
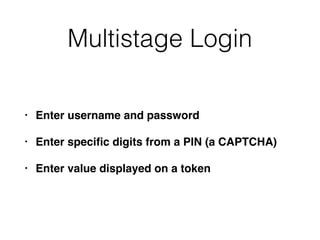
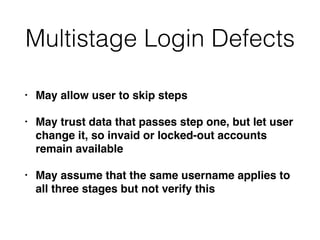
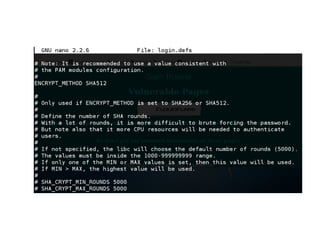
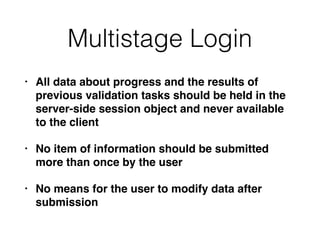
Chapter 6 discusses various security vulnerabilities in web application authentication methods, highlighting the risks associated with username and password systems as well as the importance of two-factor authentication. It covers common attack vectors such as brute-force attacks, insecure password reset mechanisms, and information leakage during login processes. Recommendations for securing authentication include strong password policies, proper validation of user inputs, and secure transmission and storage of credentials.