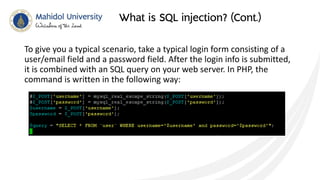
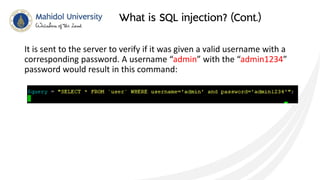
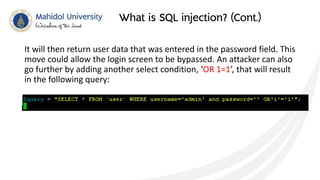
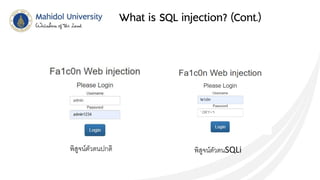
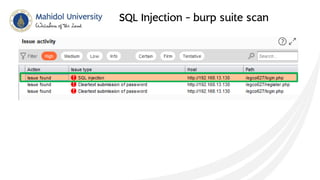
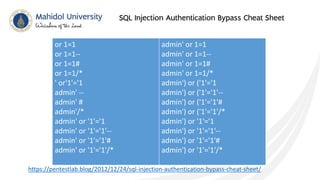
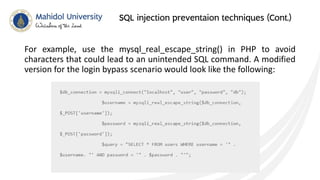
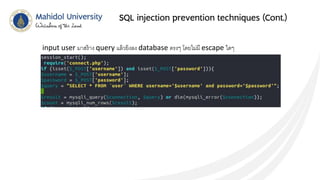
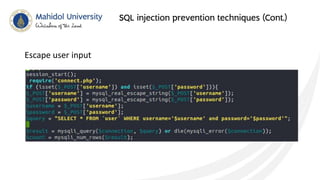
This document discusses SQL injection and techniques to prevent it. SQL injection occurs when malicious SQL statements are inserted into an entry field to exploit vulnerabilities in the underlying database. Attackers can use SQL injection to bypass login screens or retrieve sensitive data. To prevent SQL injection, developers should escape special characters in user input before submitting queries, use prepared statements with bound parameters, and validate and sanitize all input. Input escaping involves using database-specific escape functions like mysql_real_escape_string() to avoid unintended SQL commands. Proper input validation and escaping helps prevent SQL injection attacks.