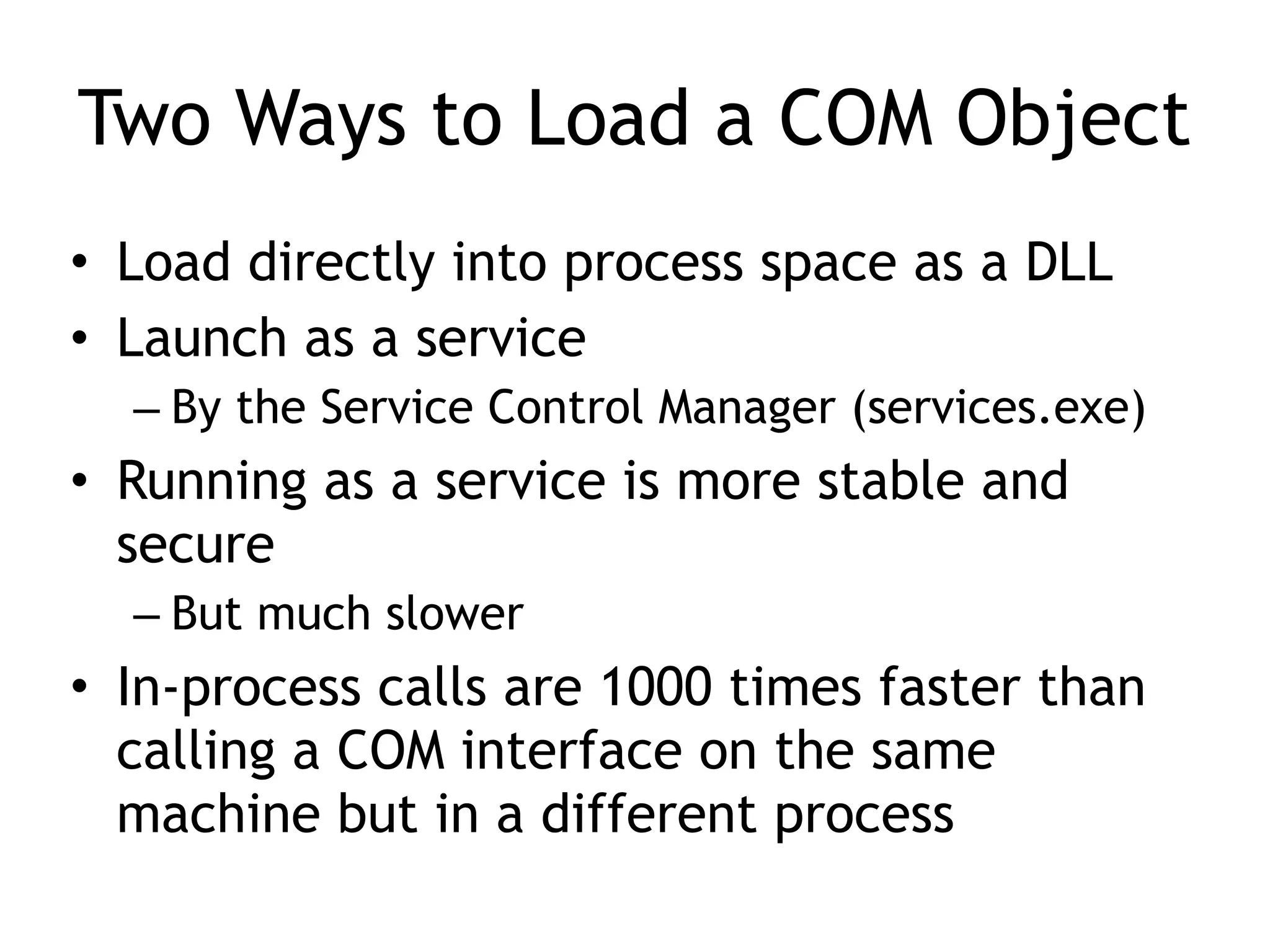
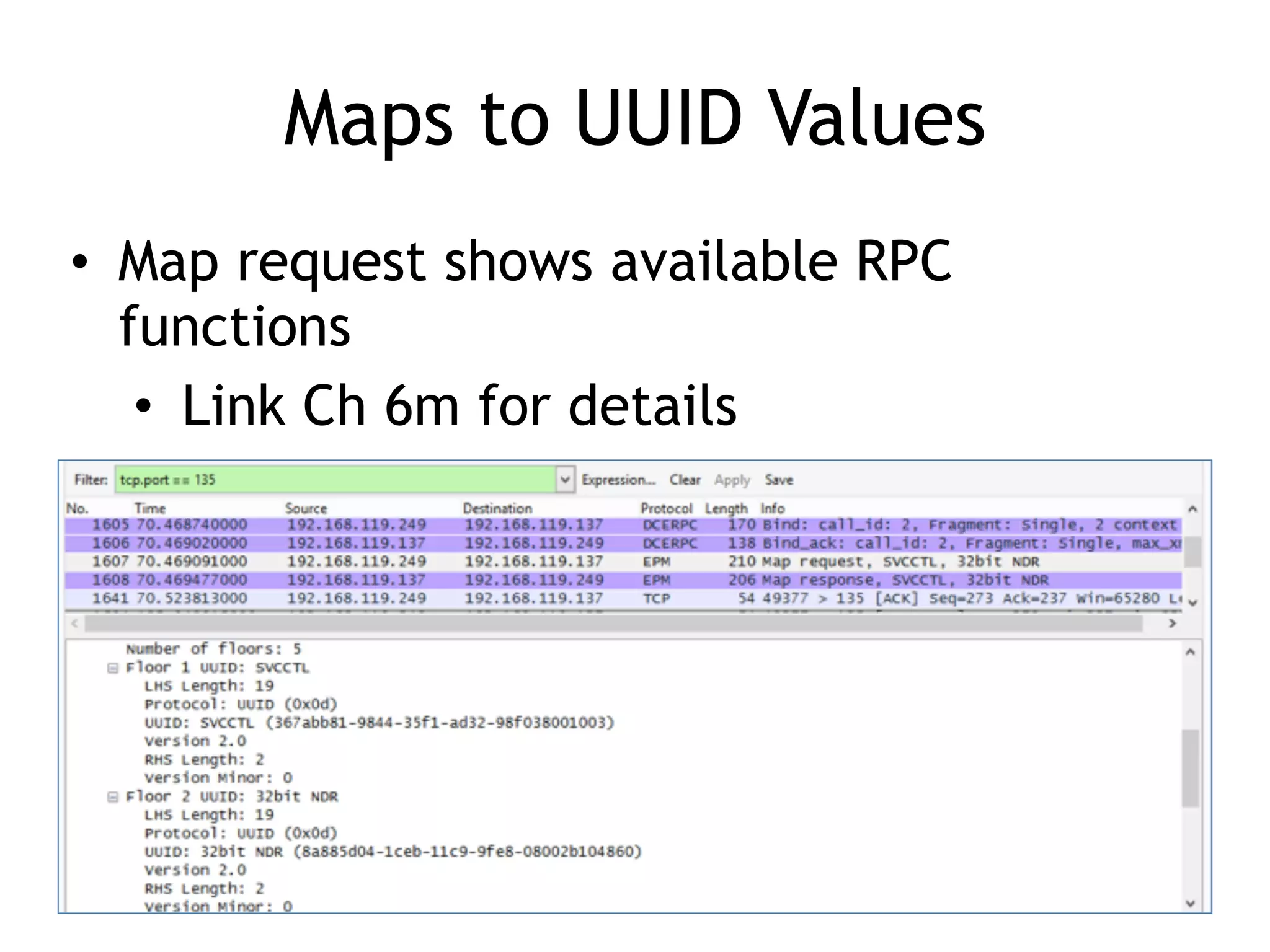
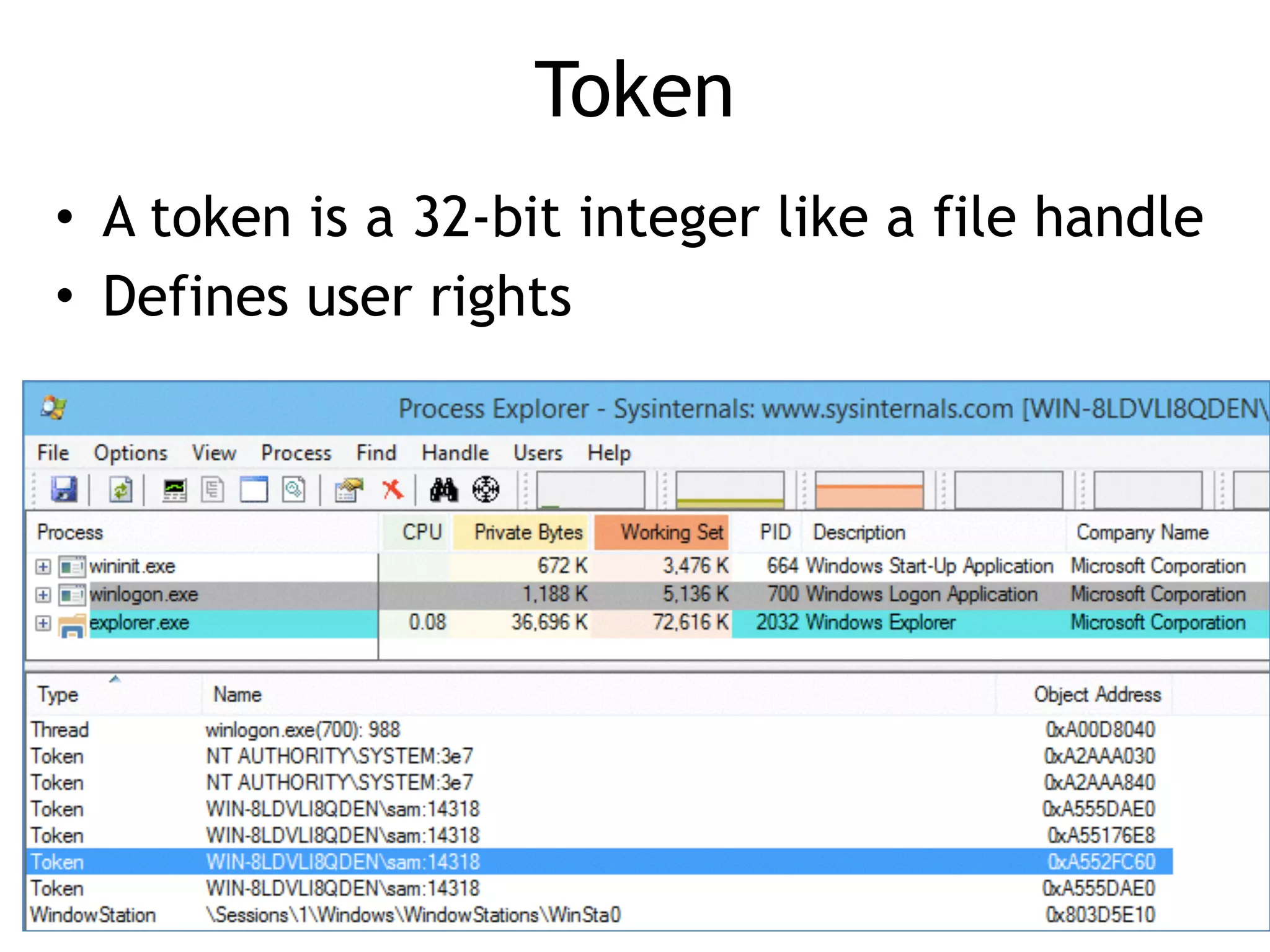
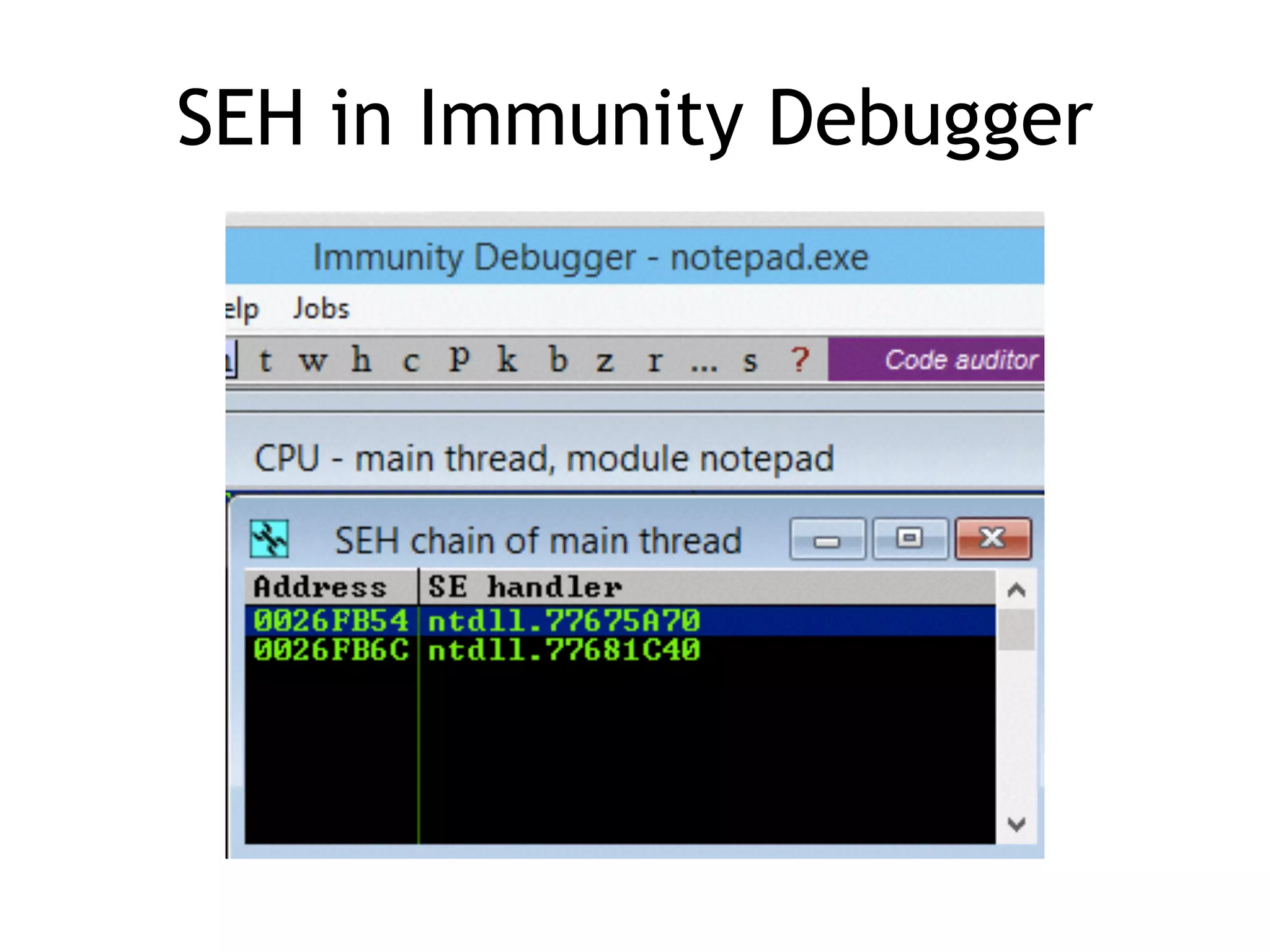
The document discusses various aspects of exploit development in Windows, covering topics such as the Windows API, dynamic link libraries (DLLs), and the Portable Executable (PE) file format. It explains how APIs interact with processes and the importance of exception handling, DCOM, and remote procedure calls (RPC) in the Windows environment. Additionally, it touches on debugging tools available for exploit development, highlighting their functions and capabilities.