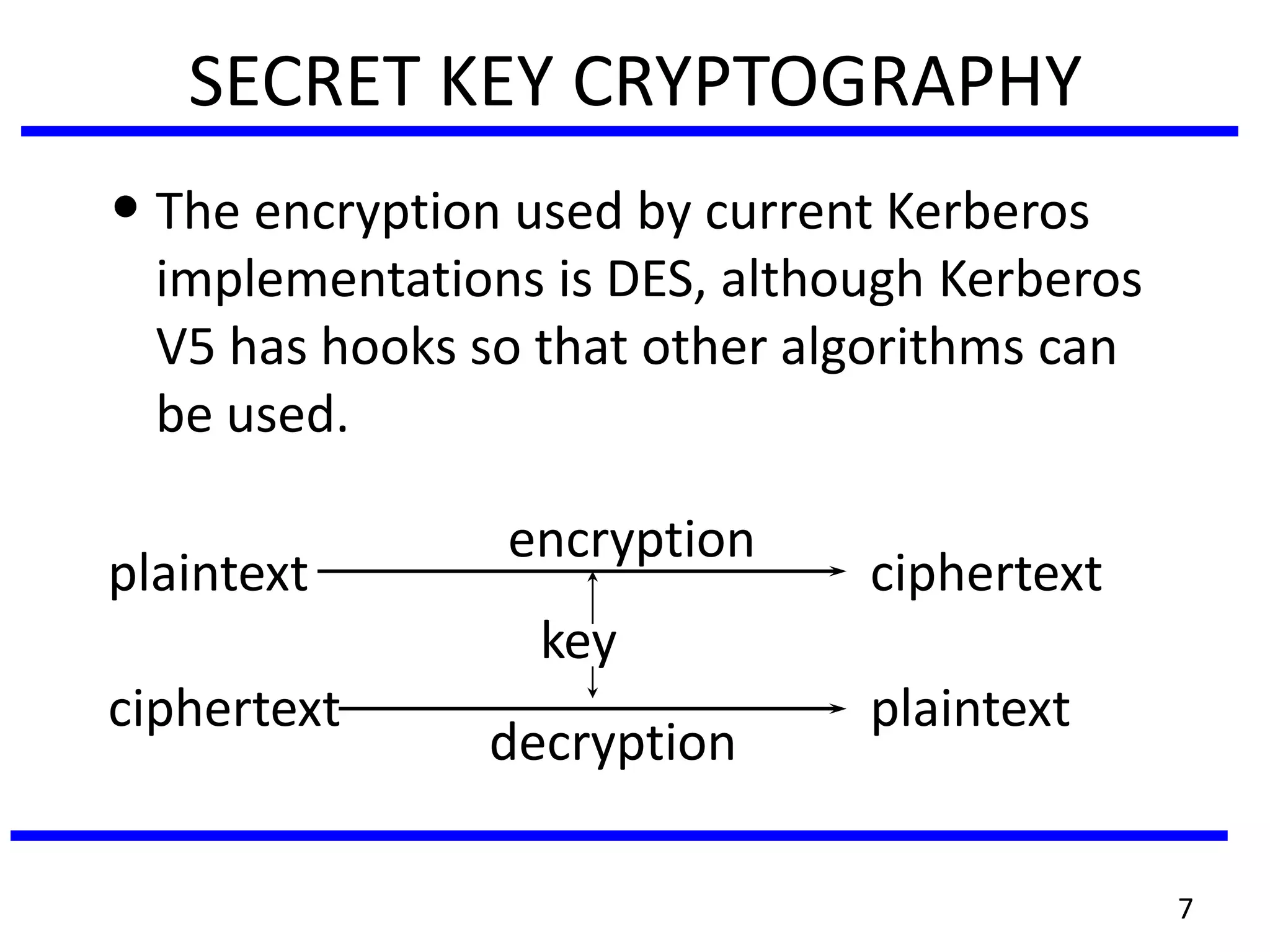
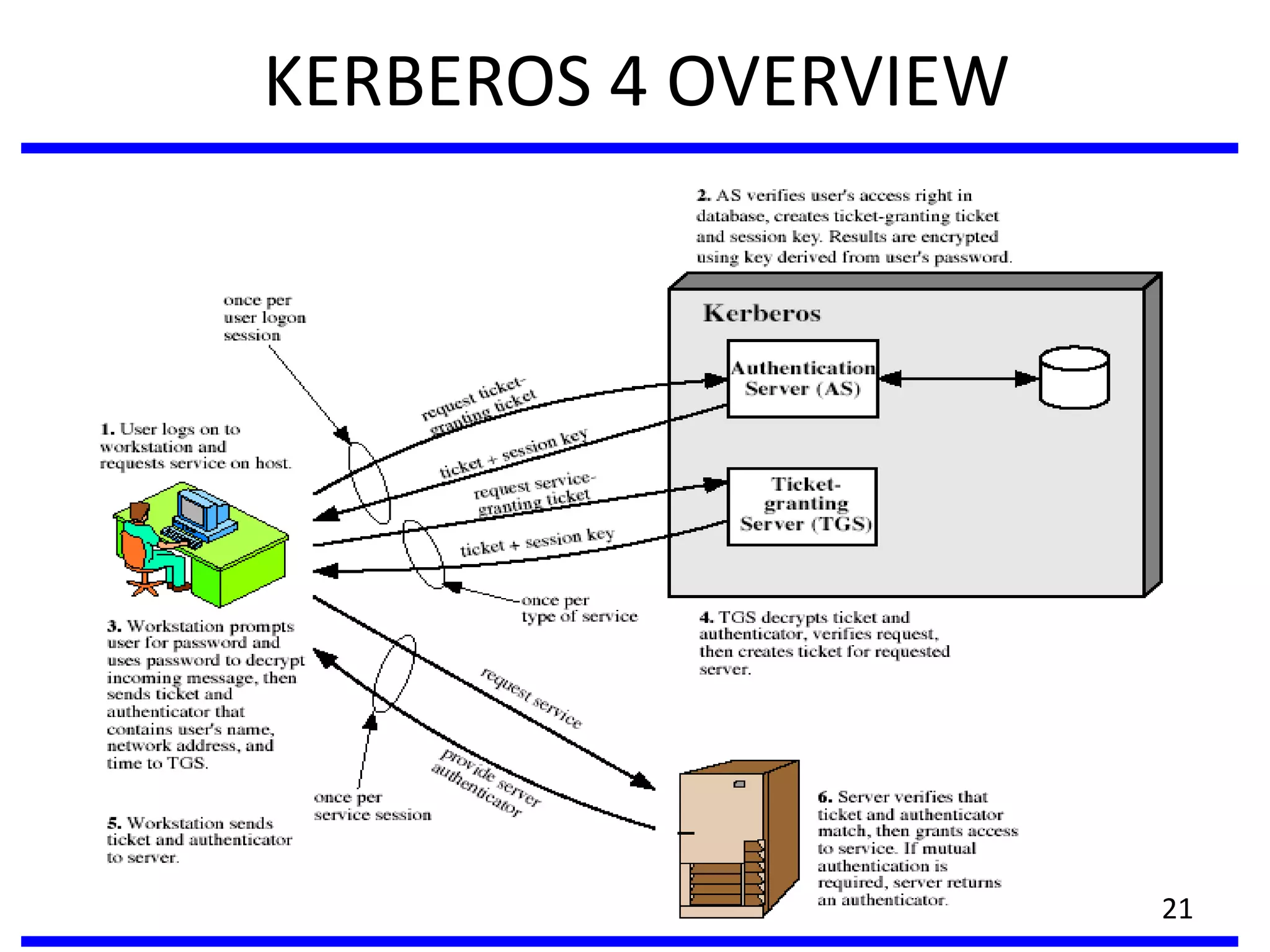
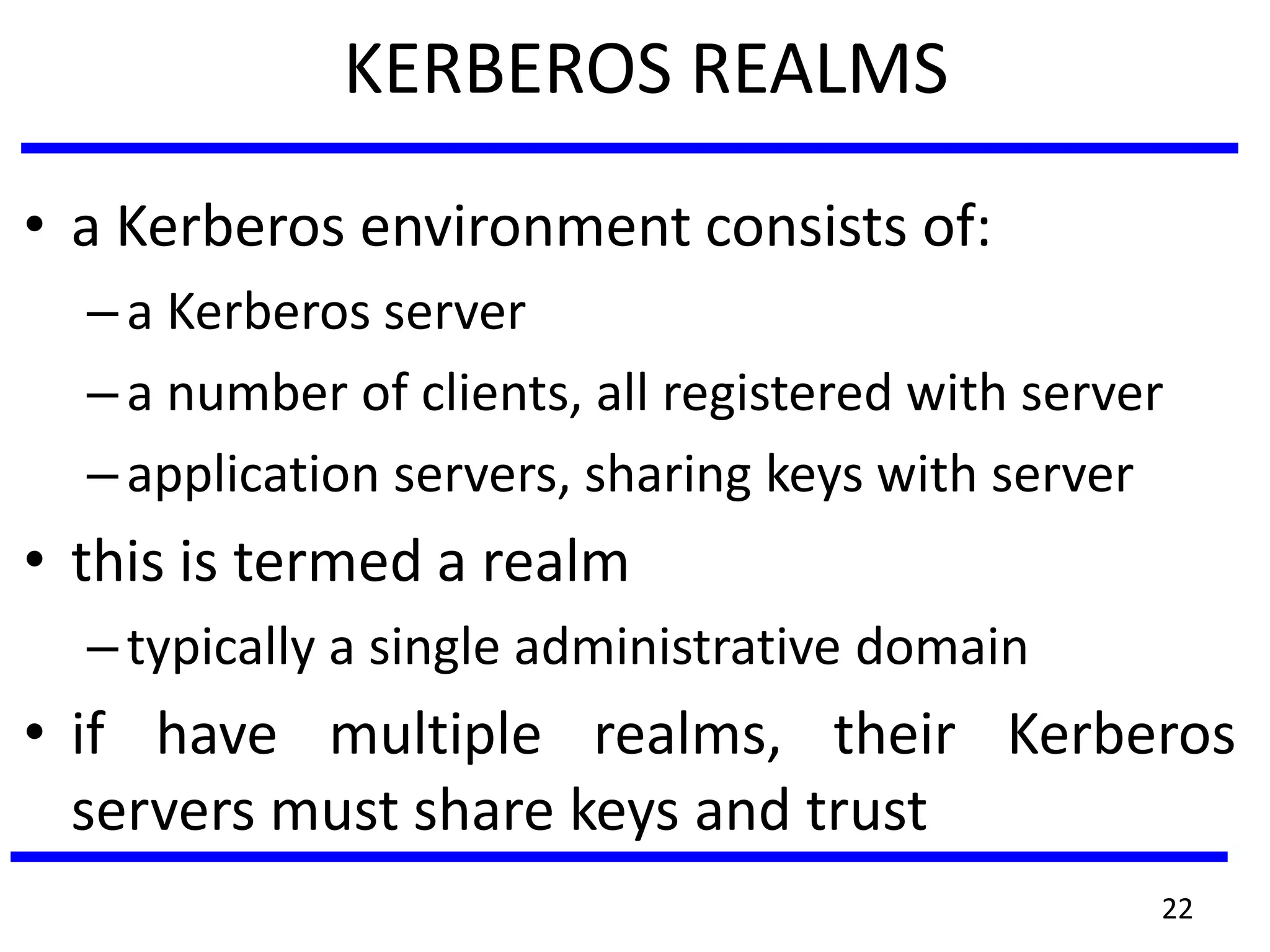
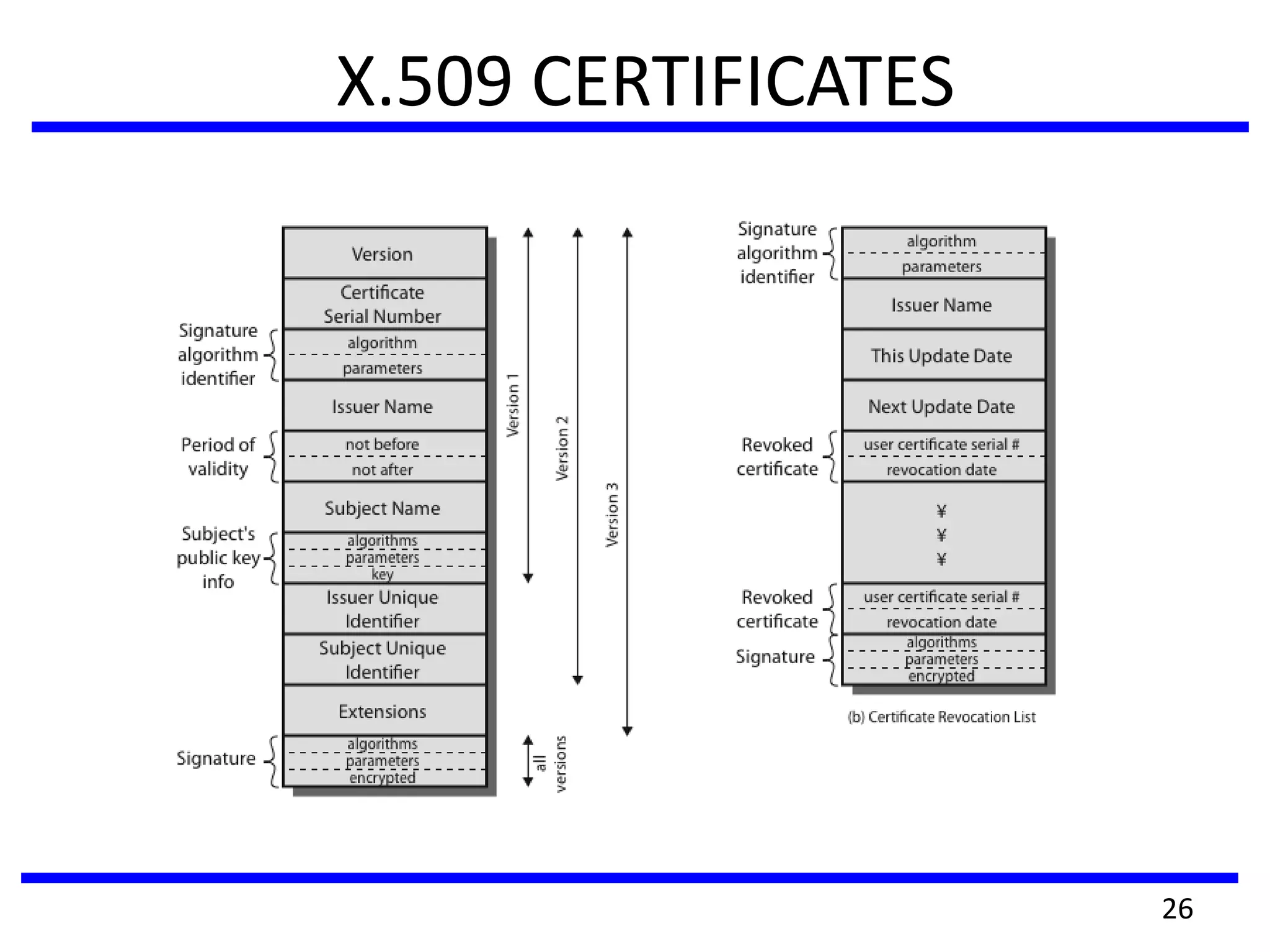
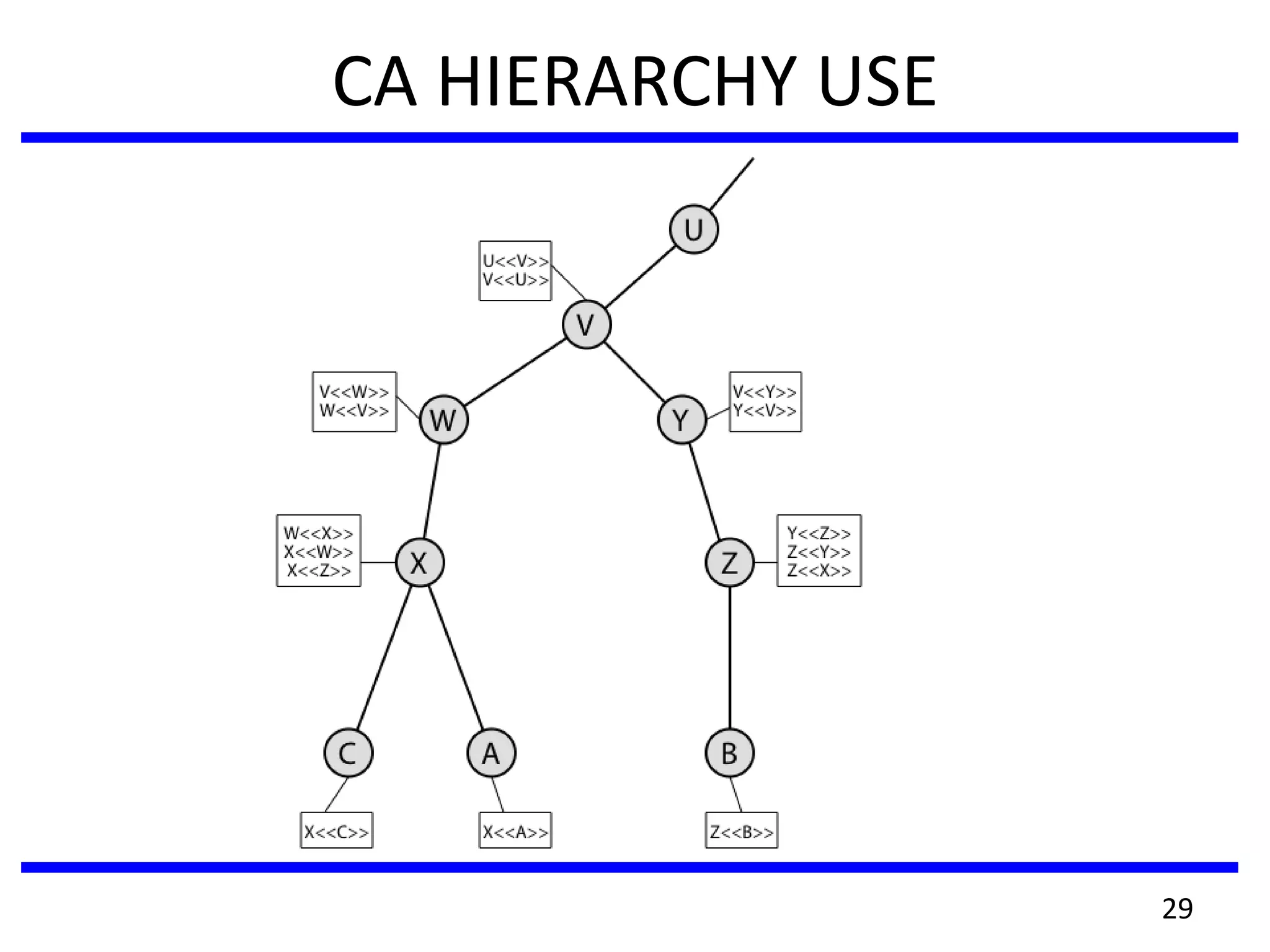
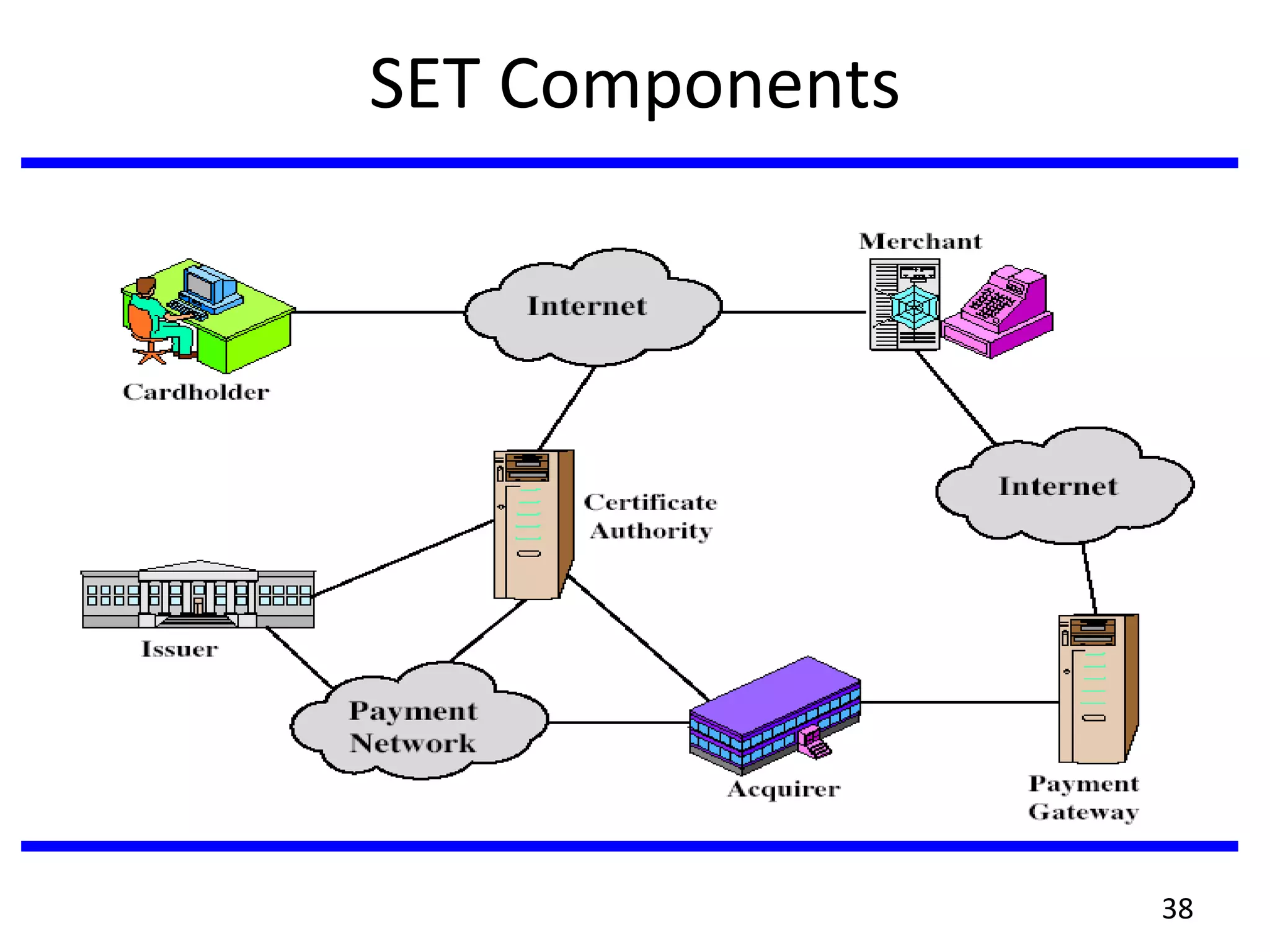
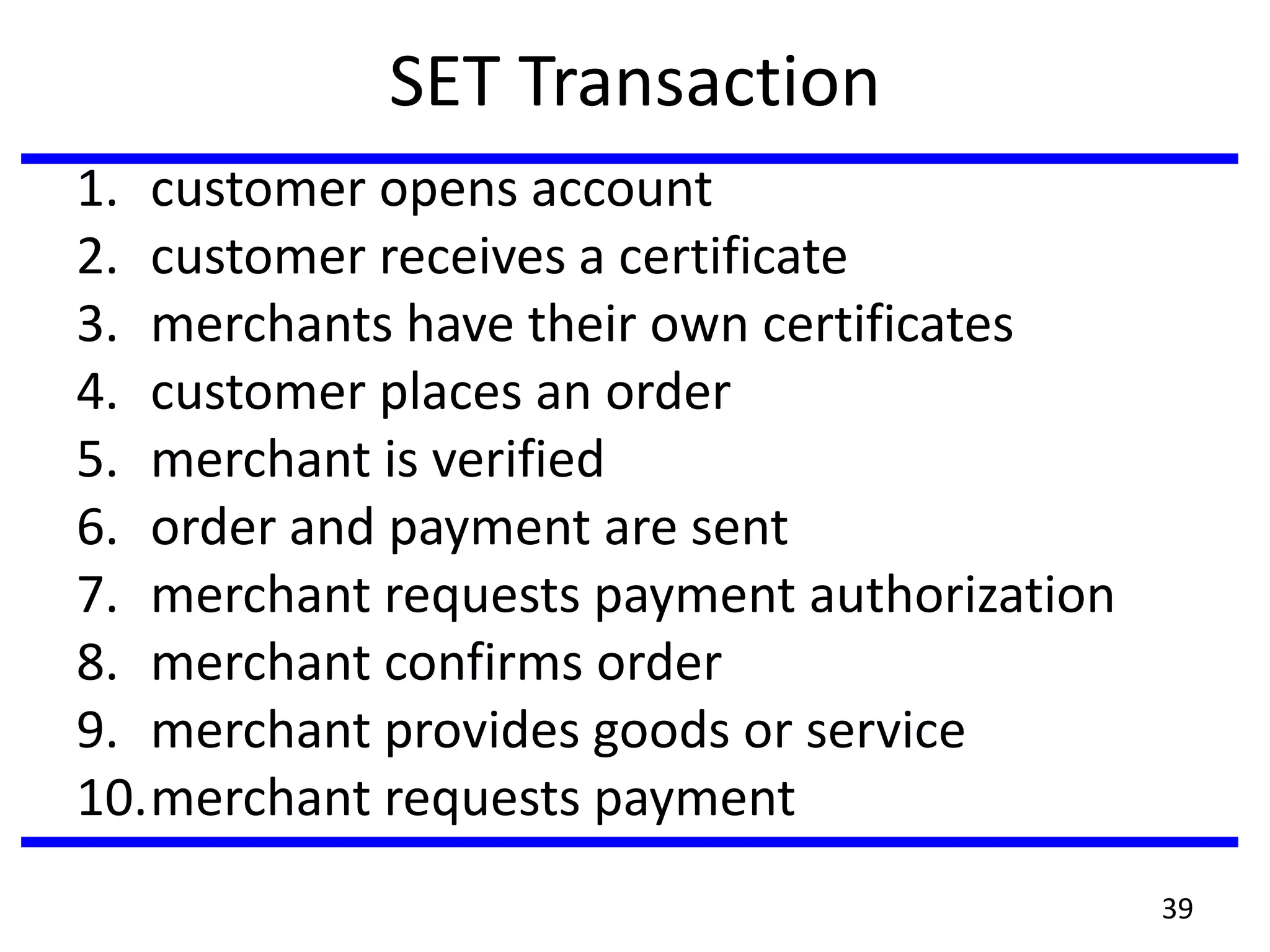
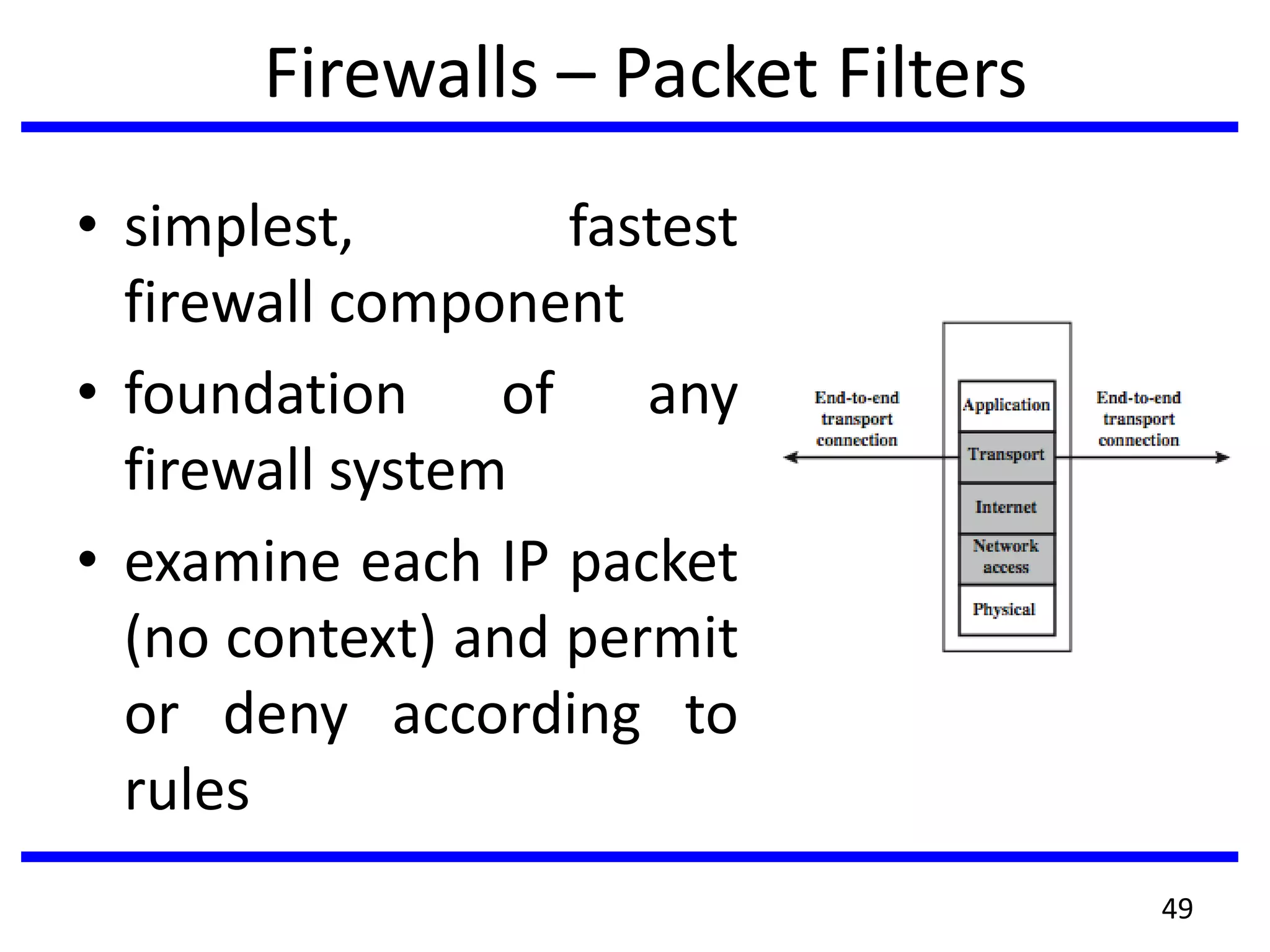
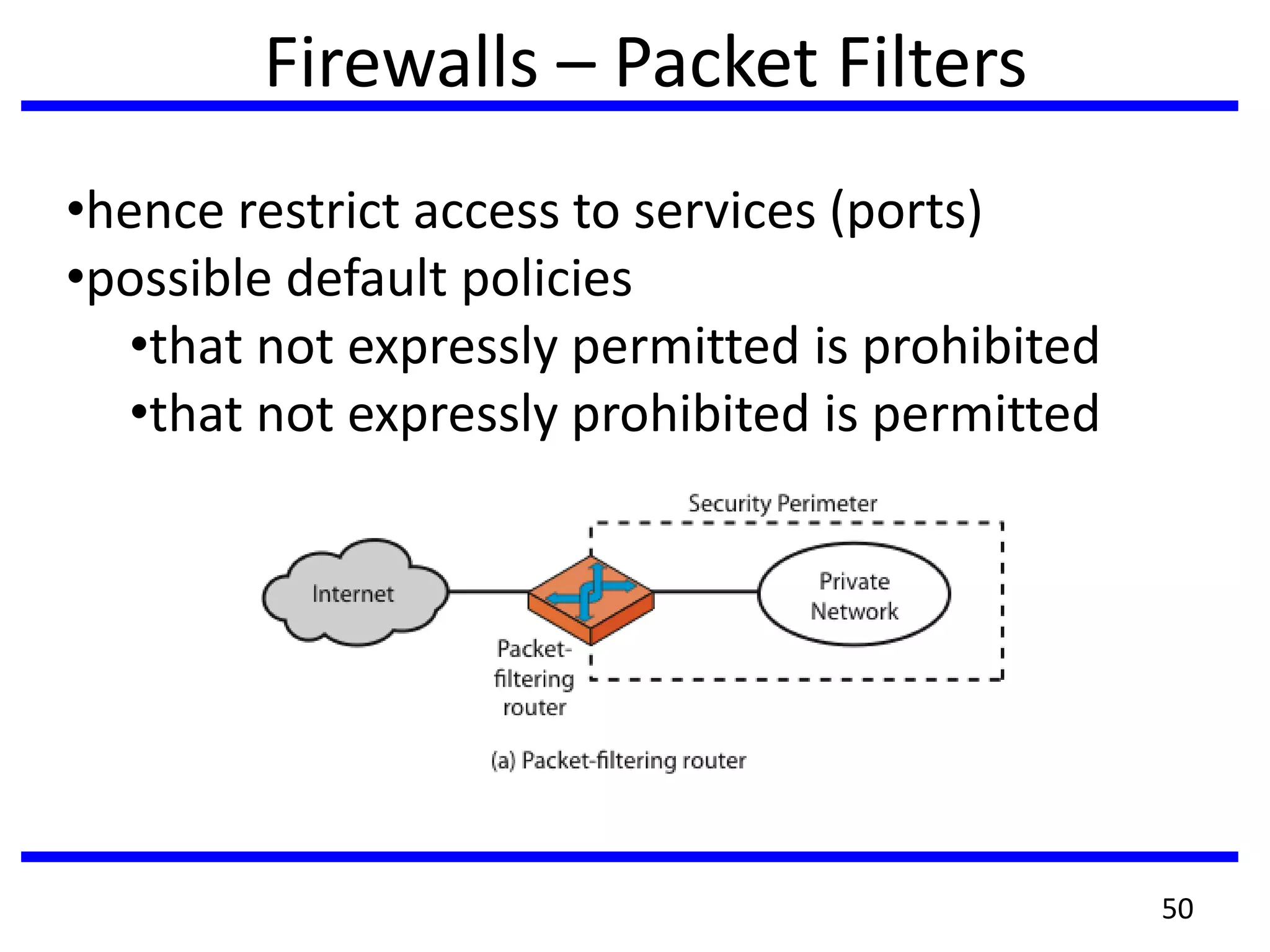
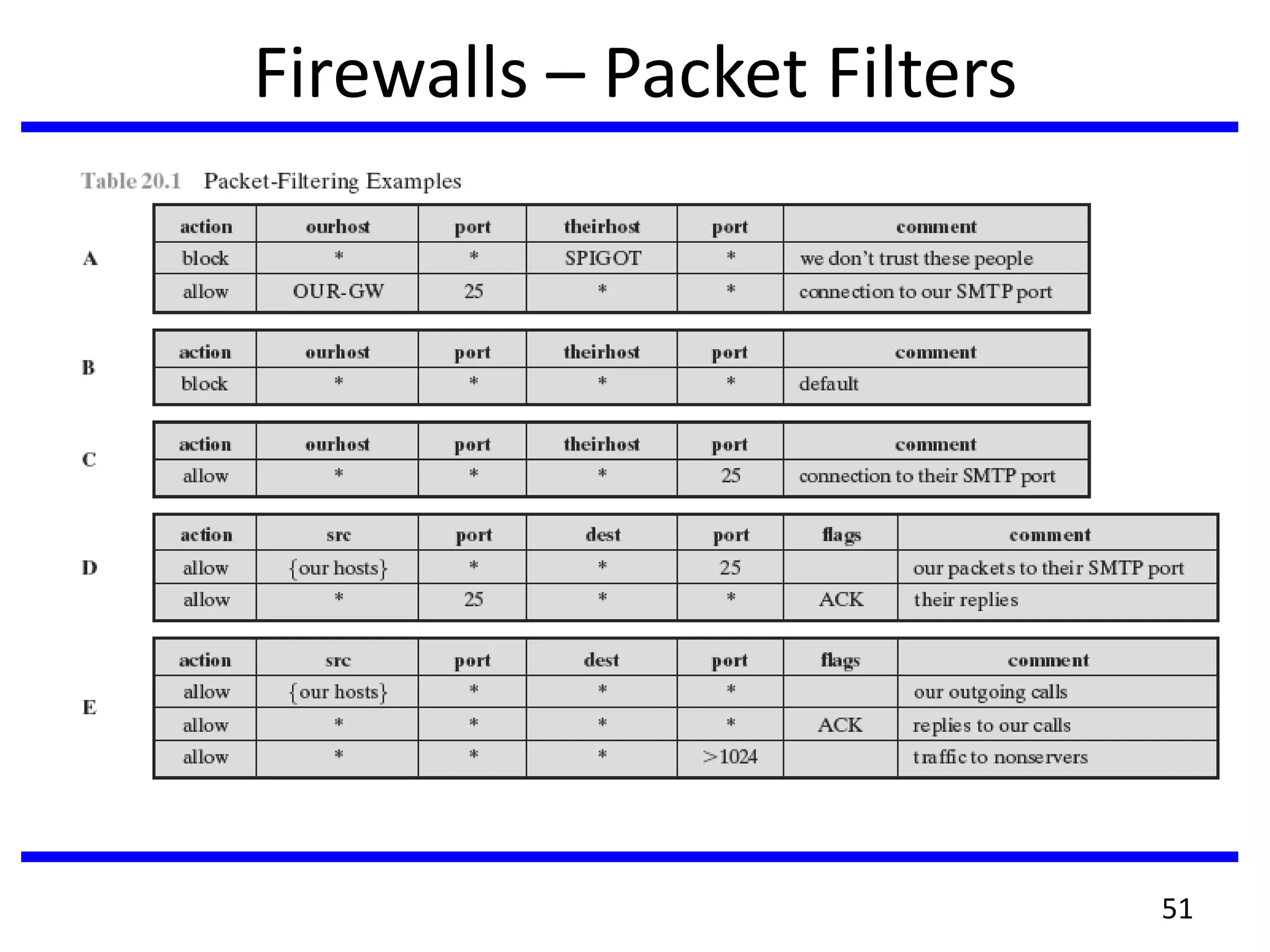
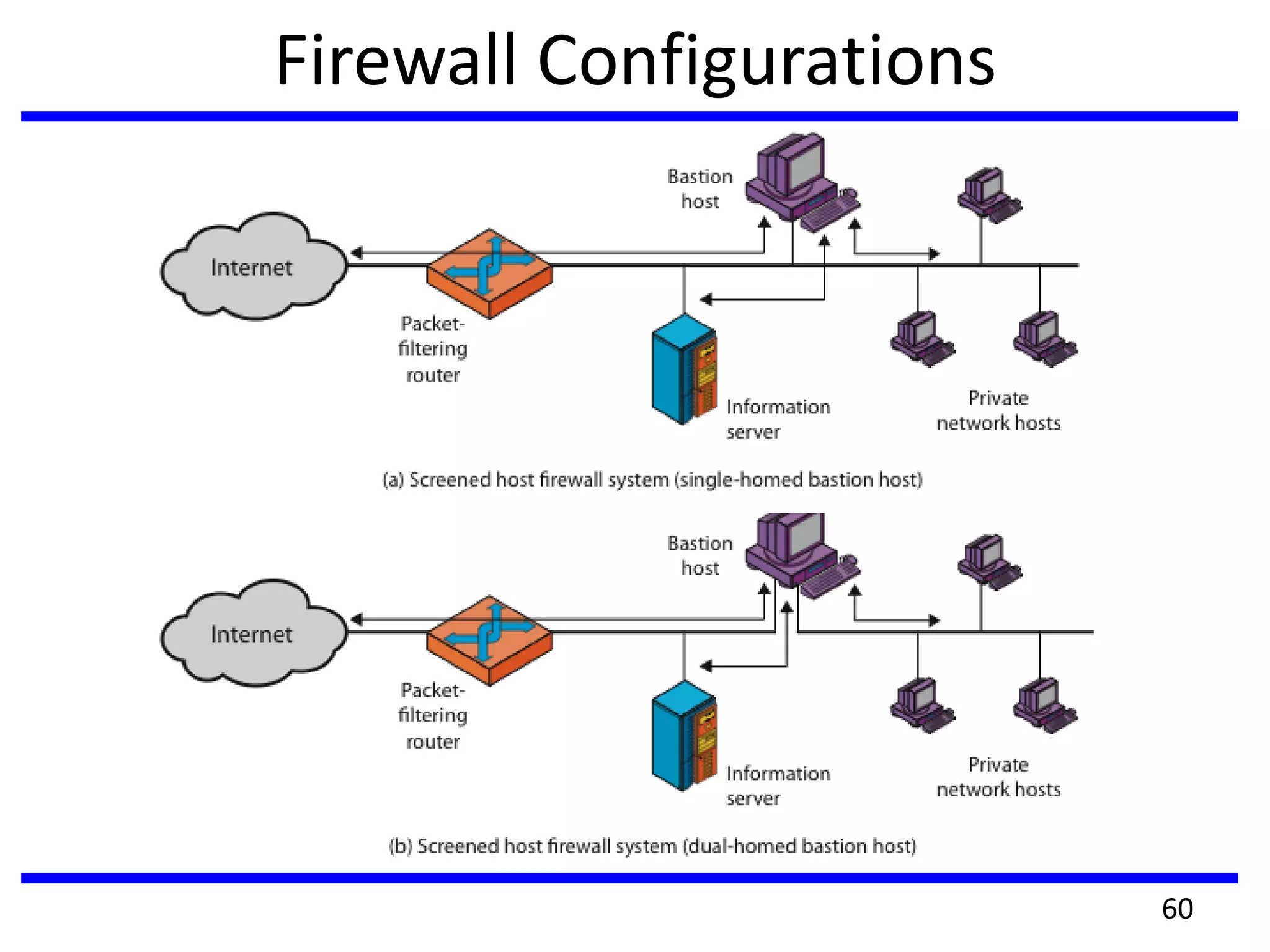
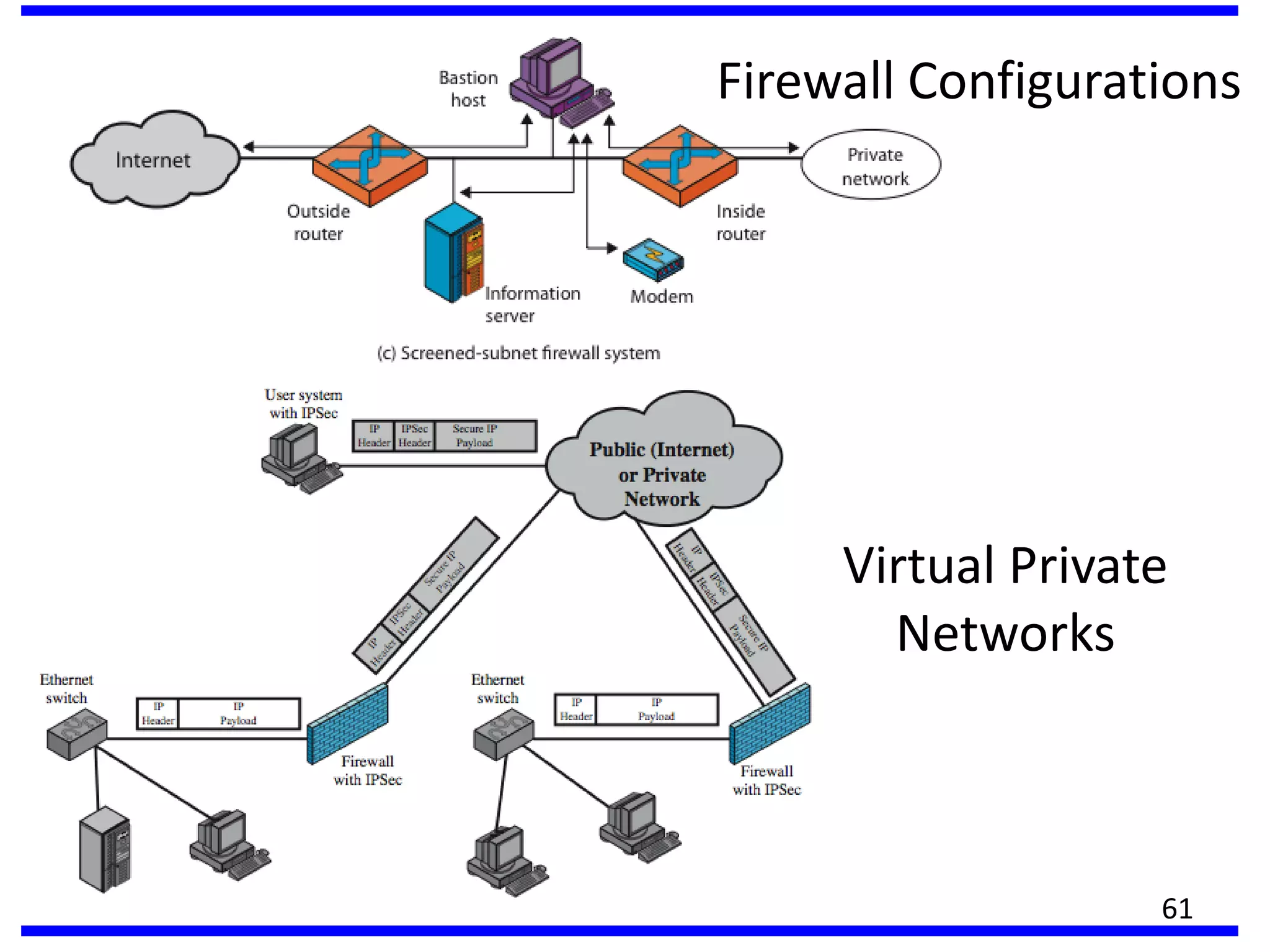
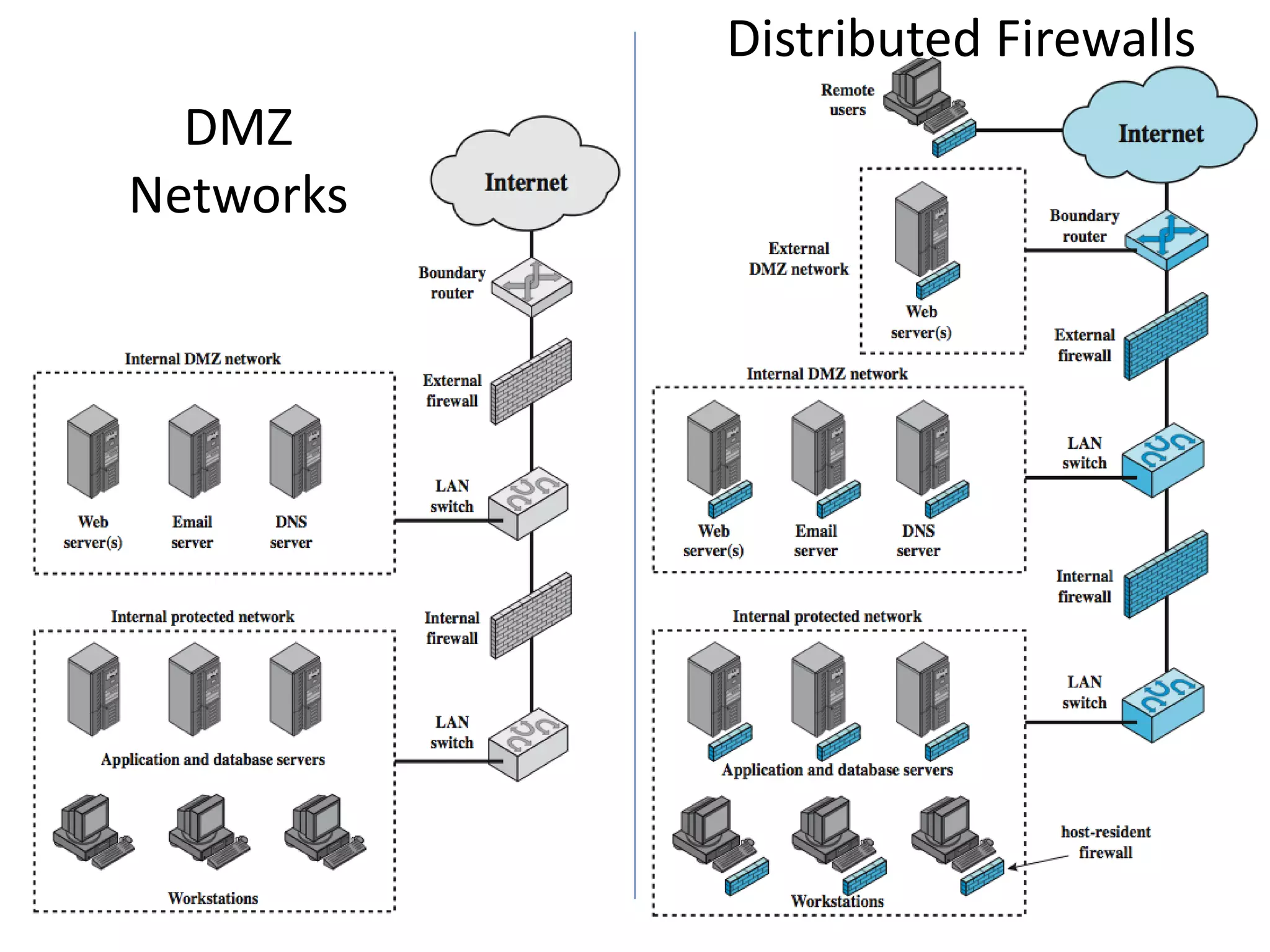
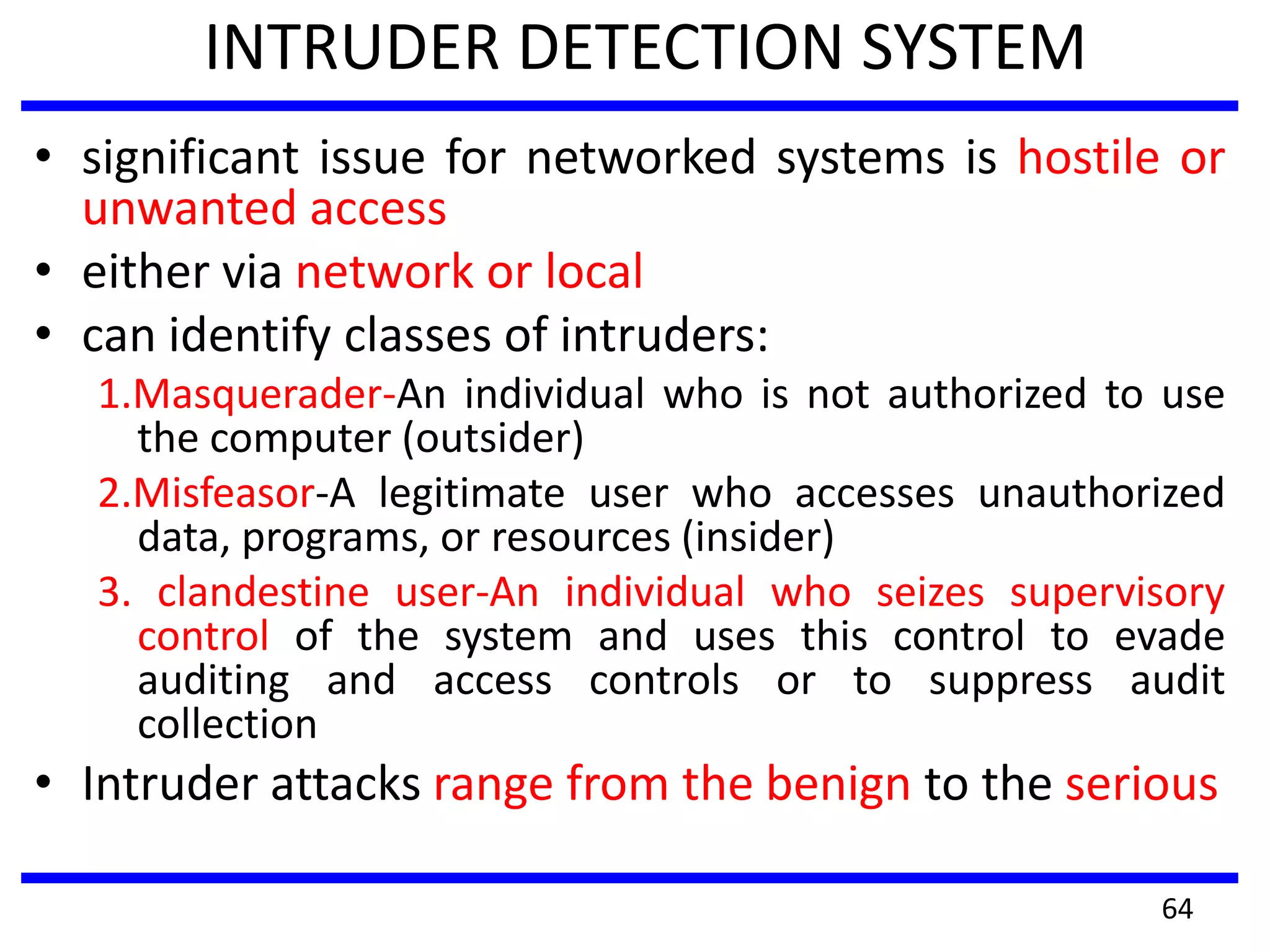
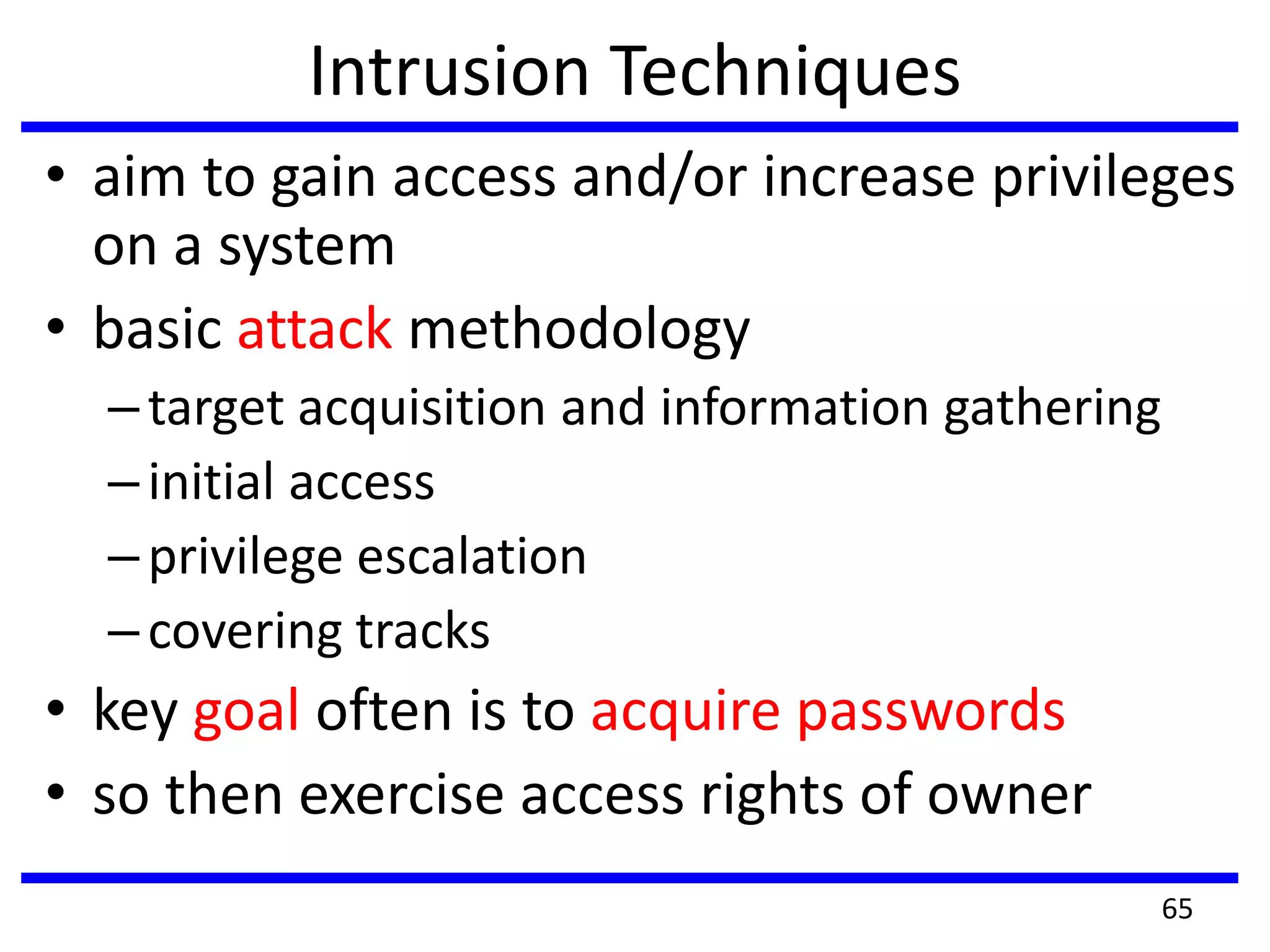
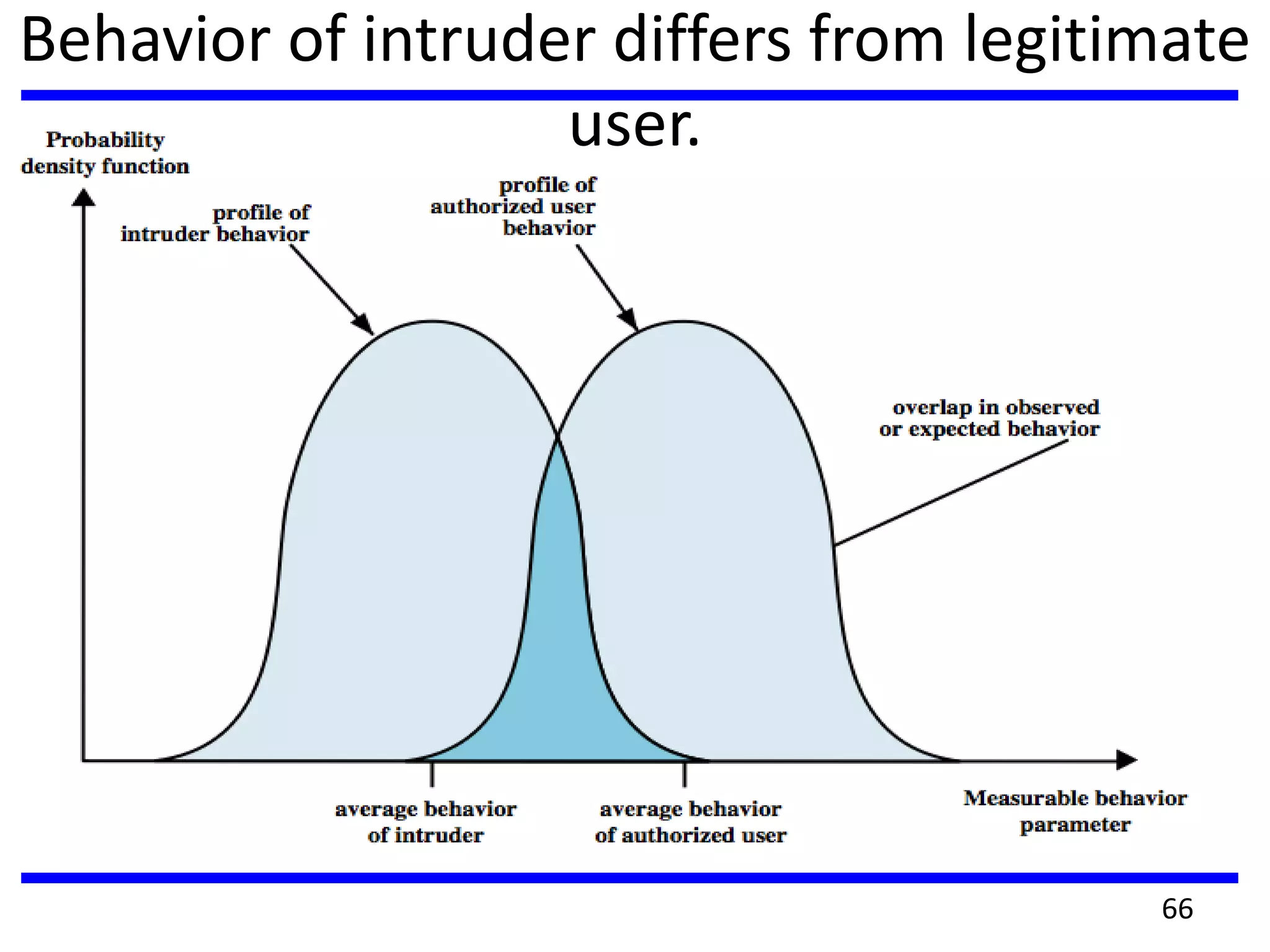
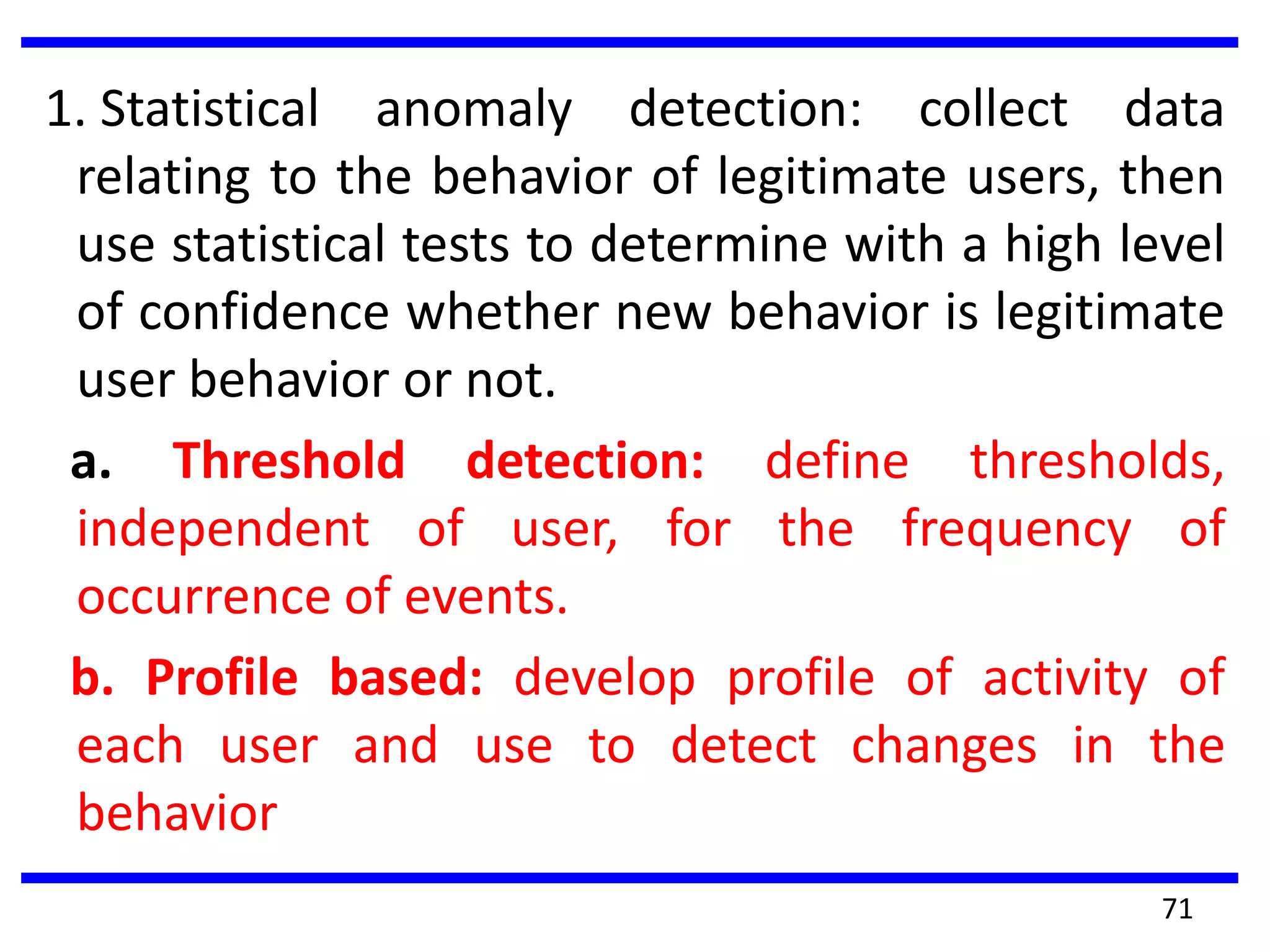
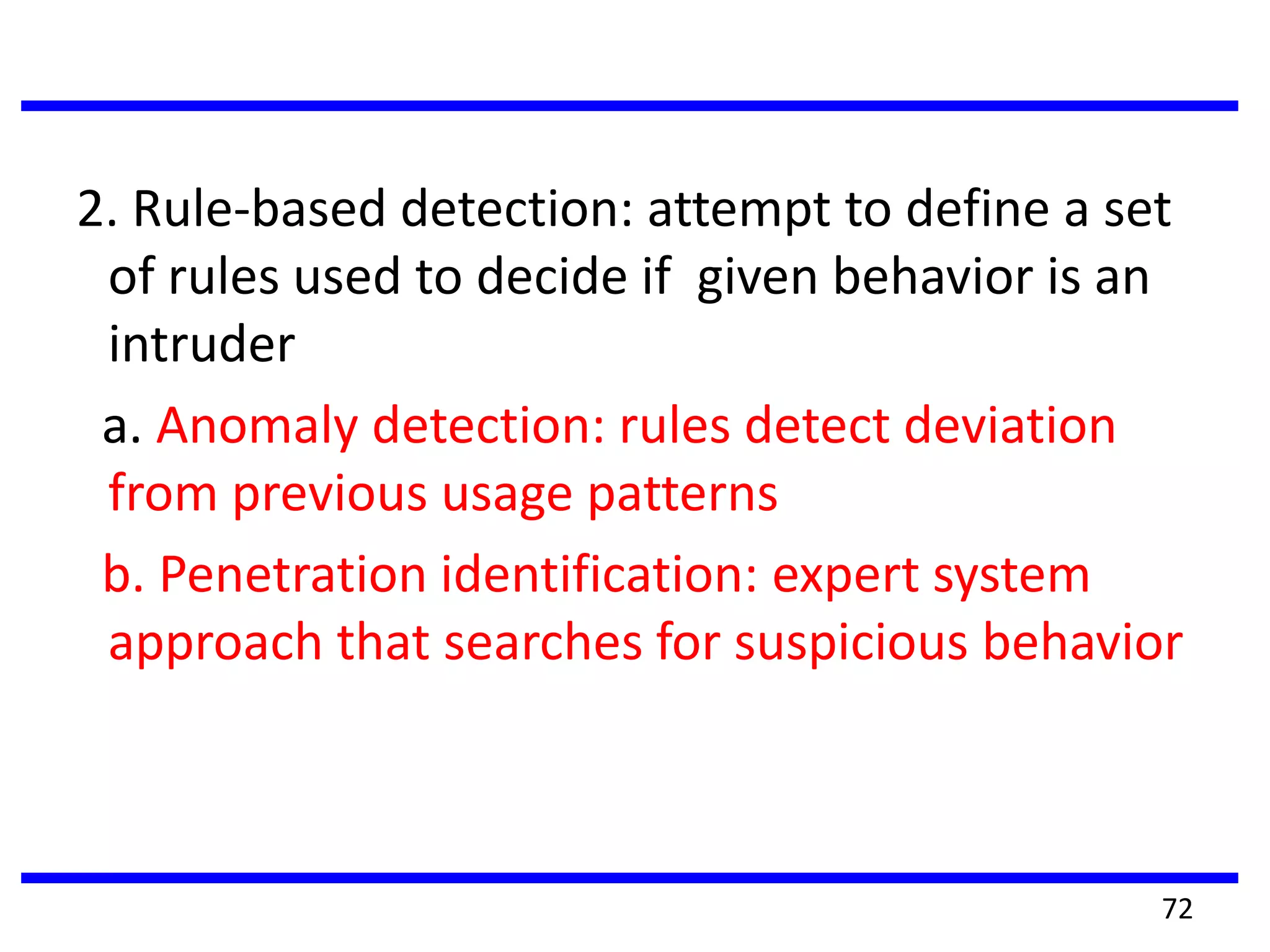
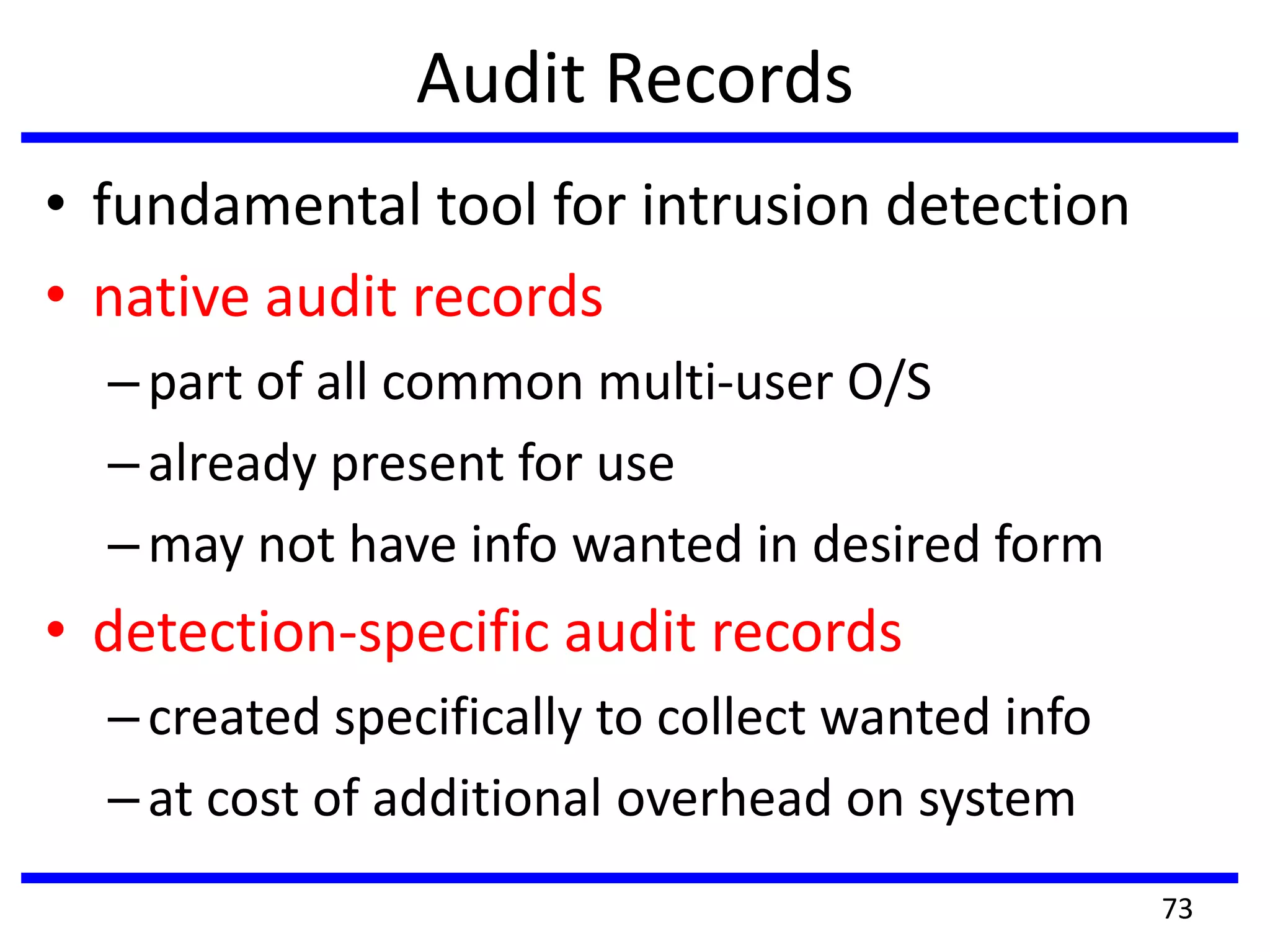
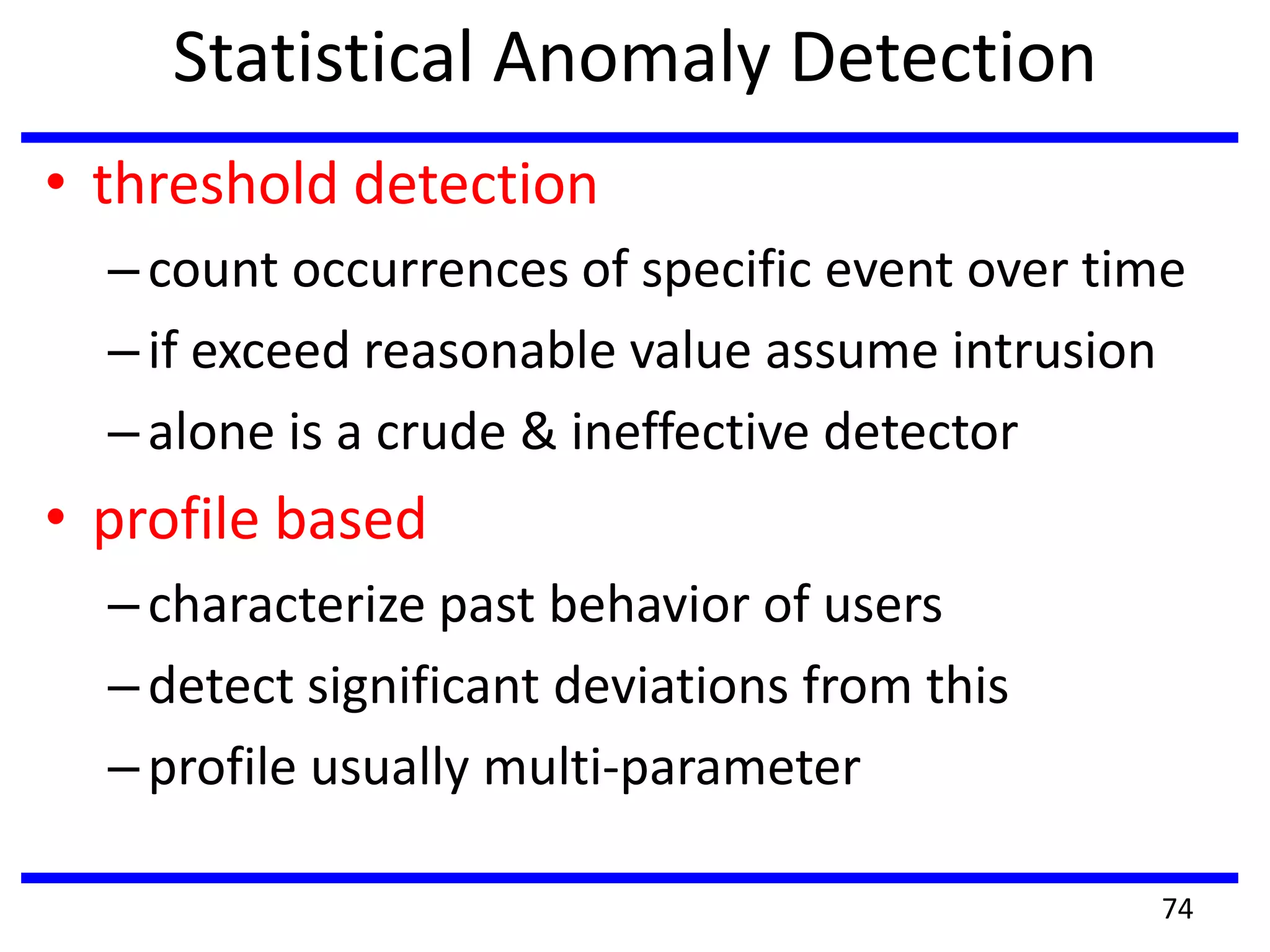
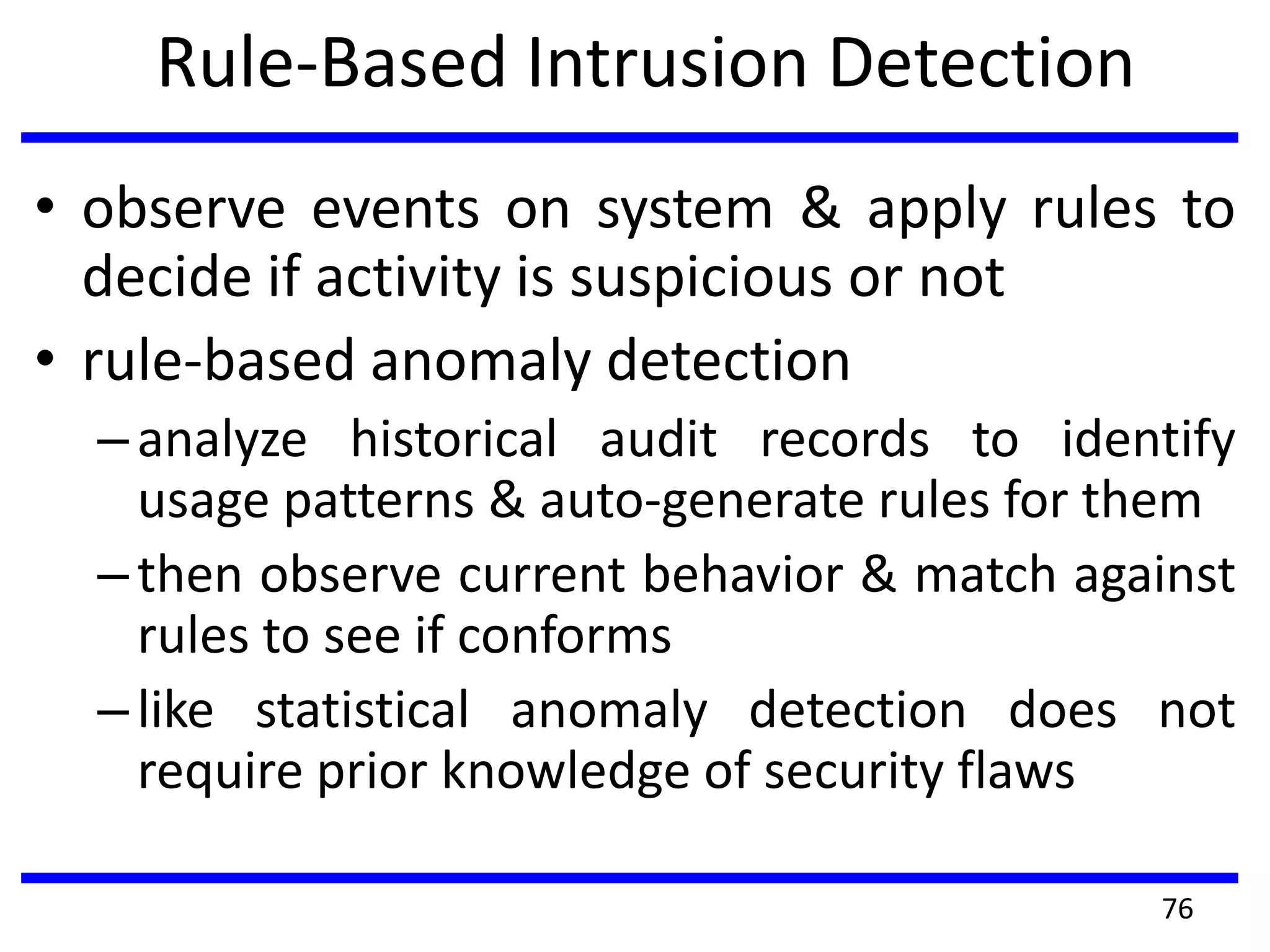
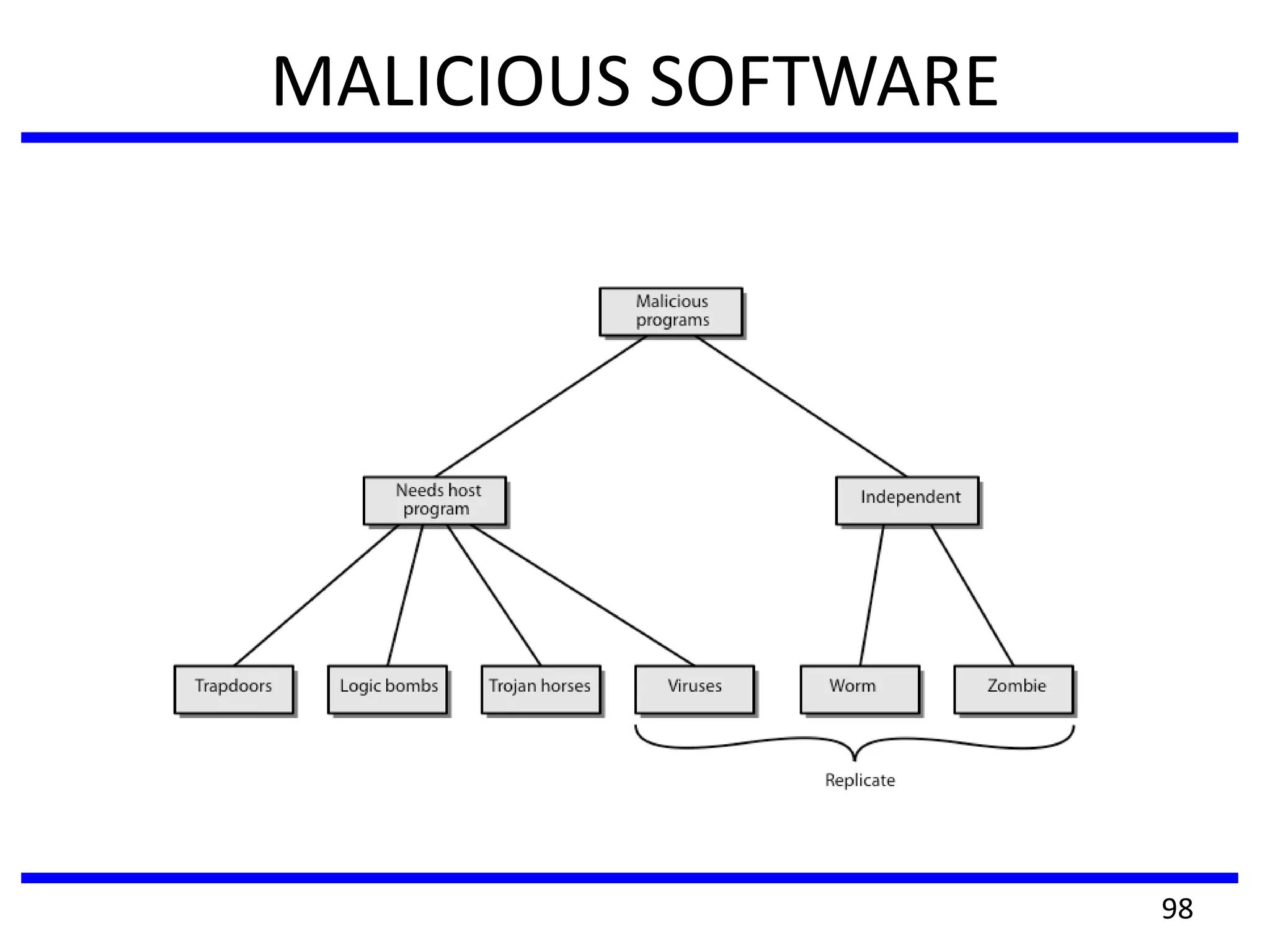
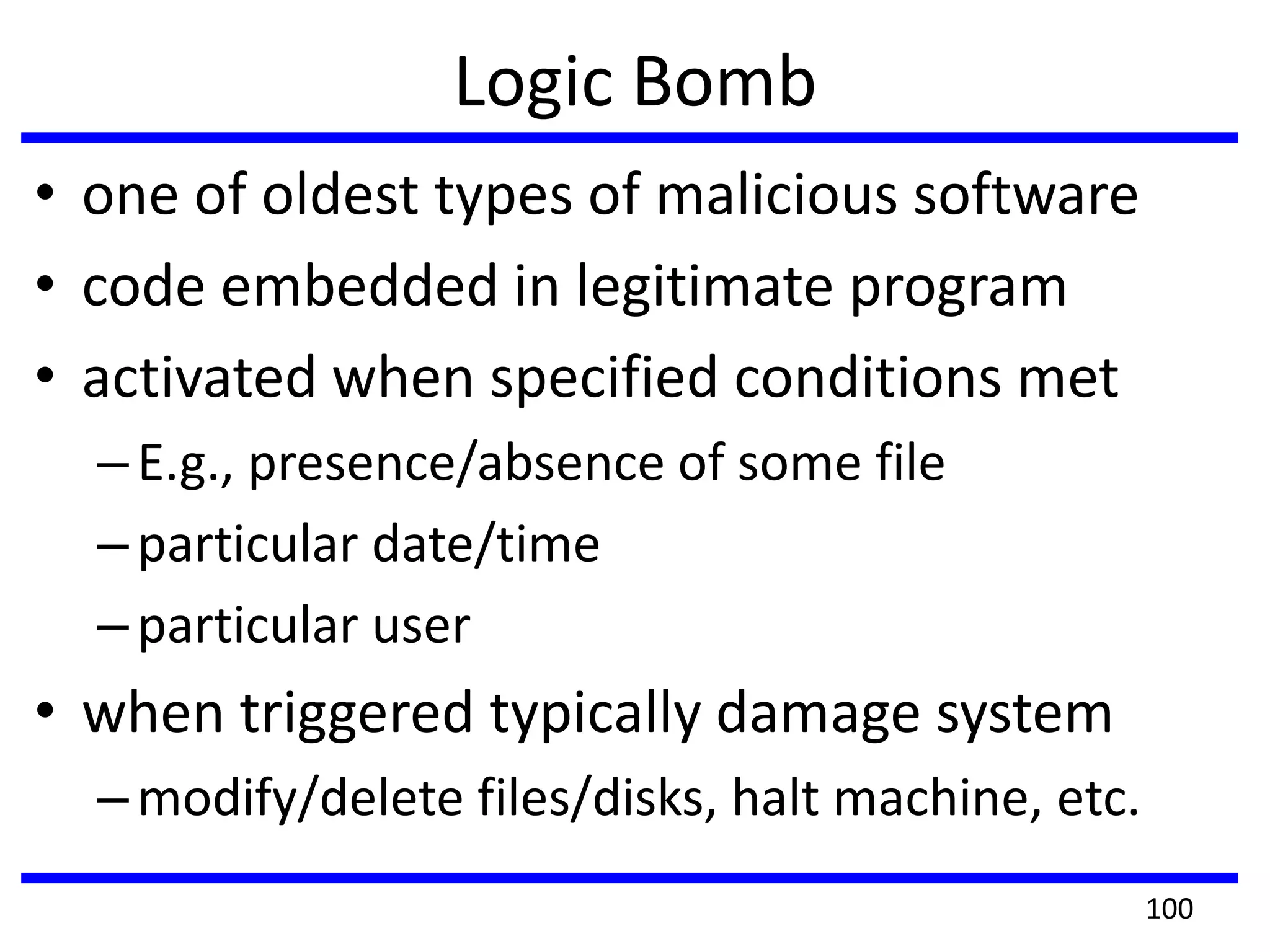
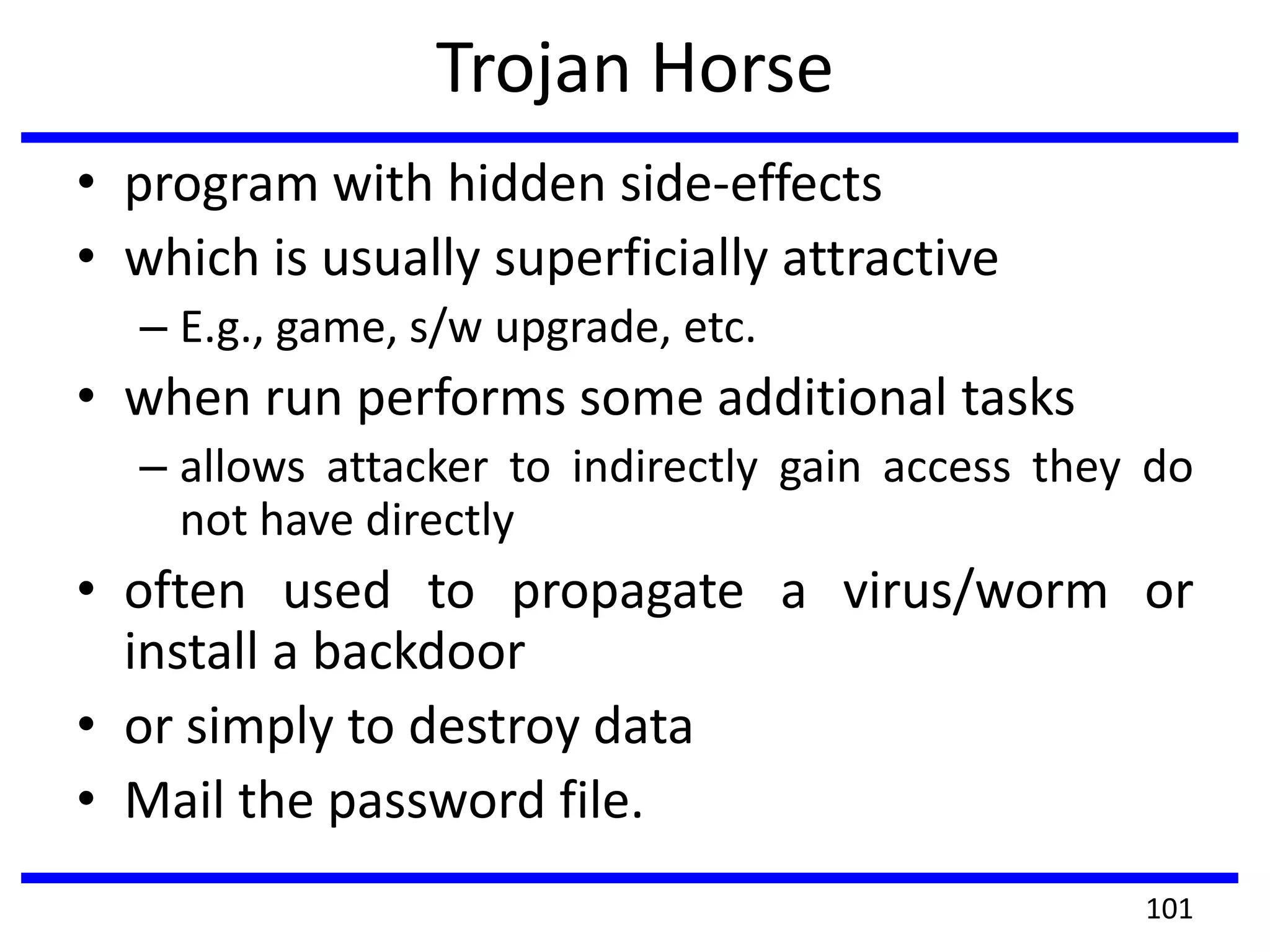
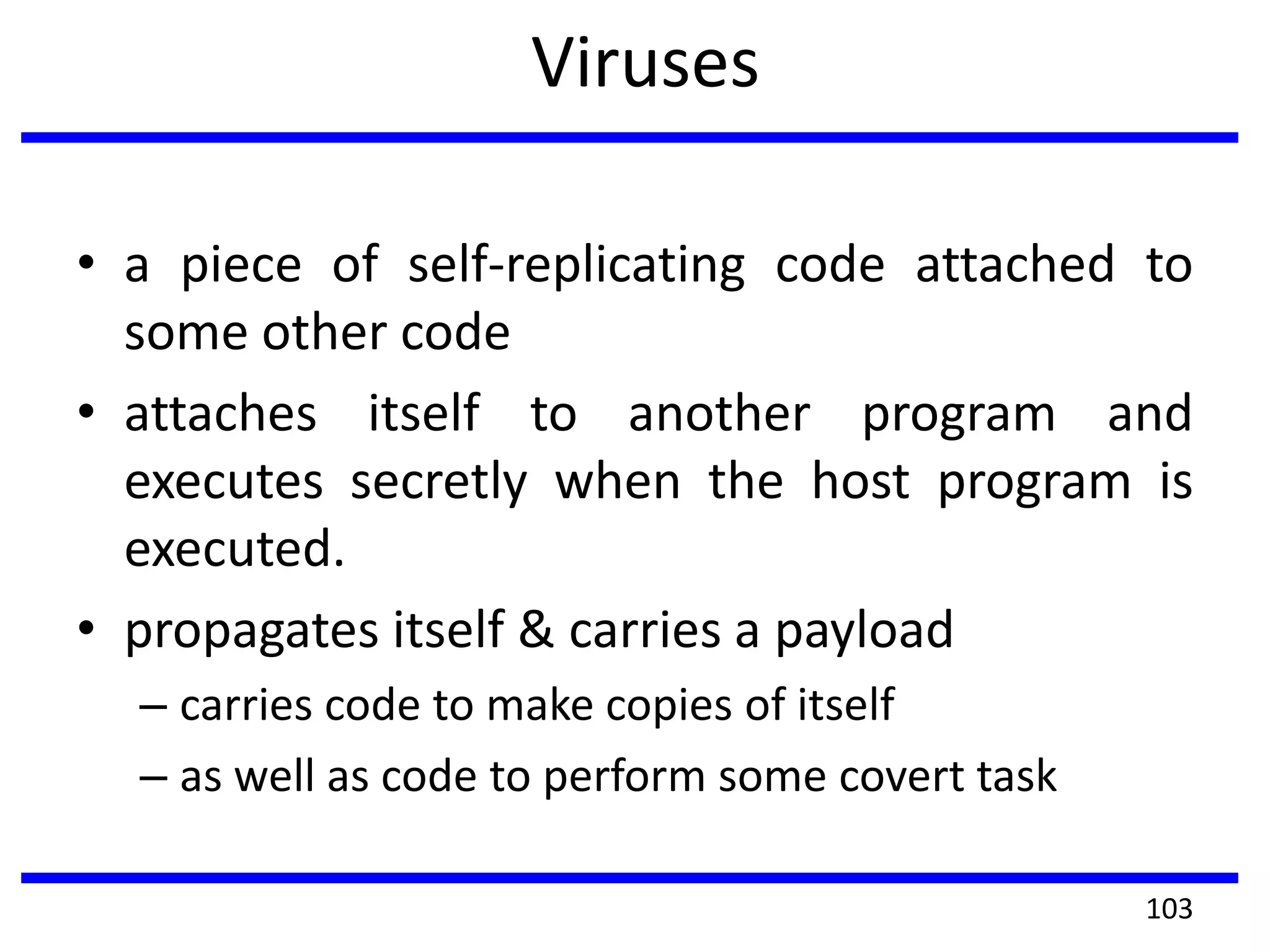
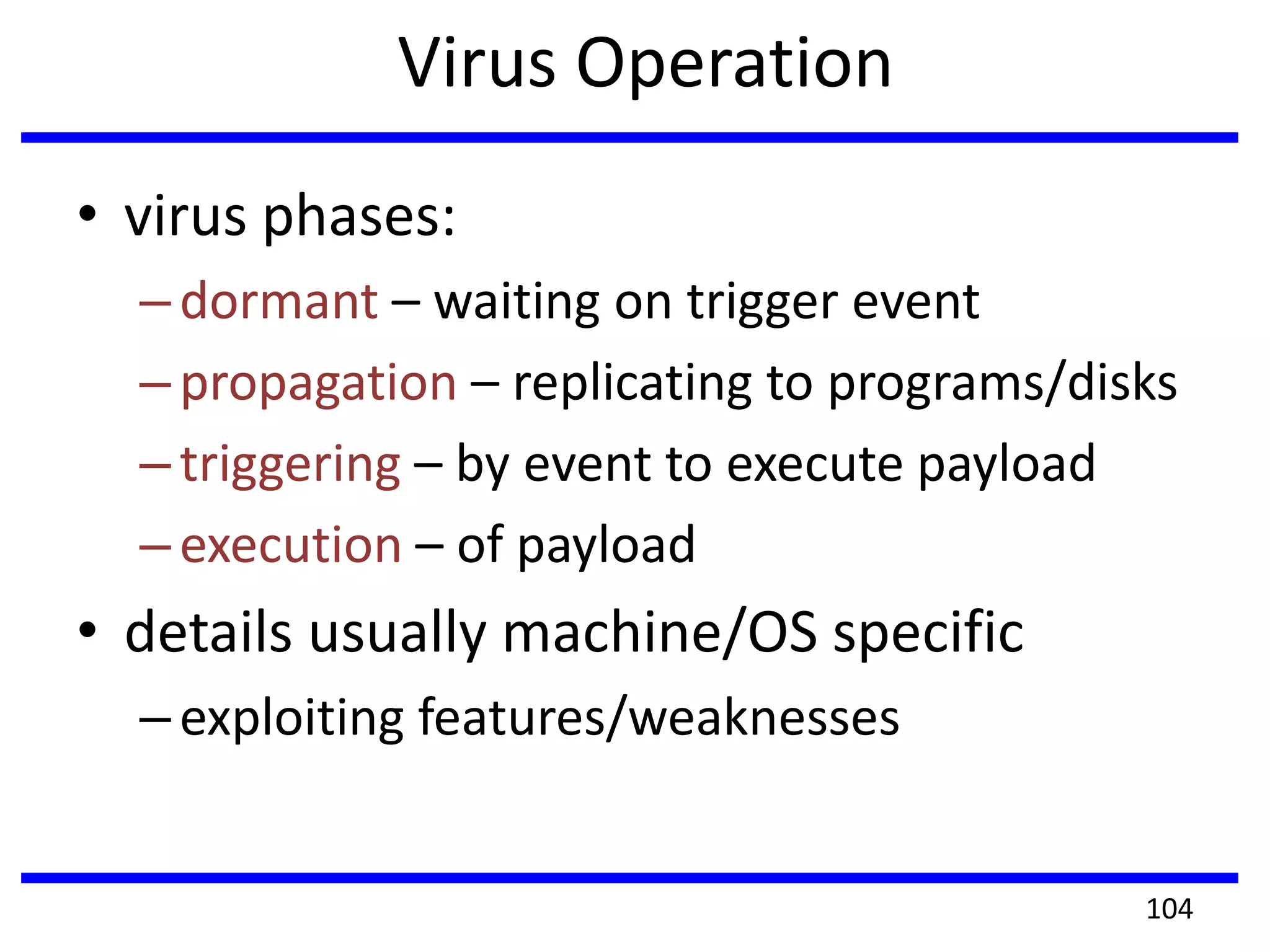
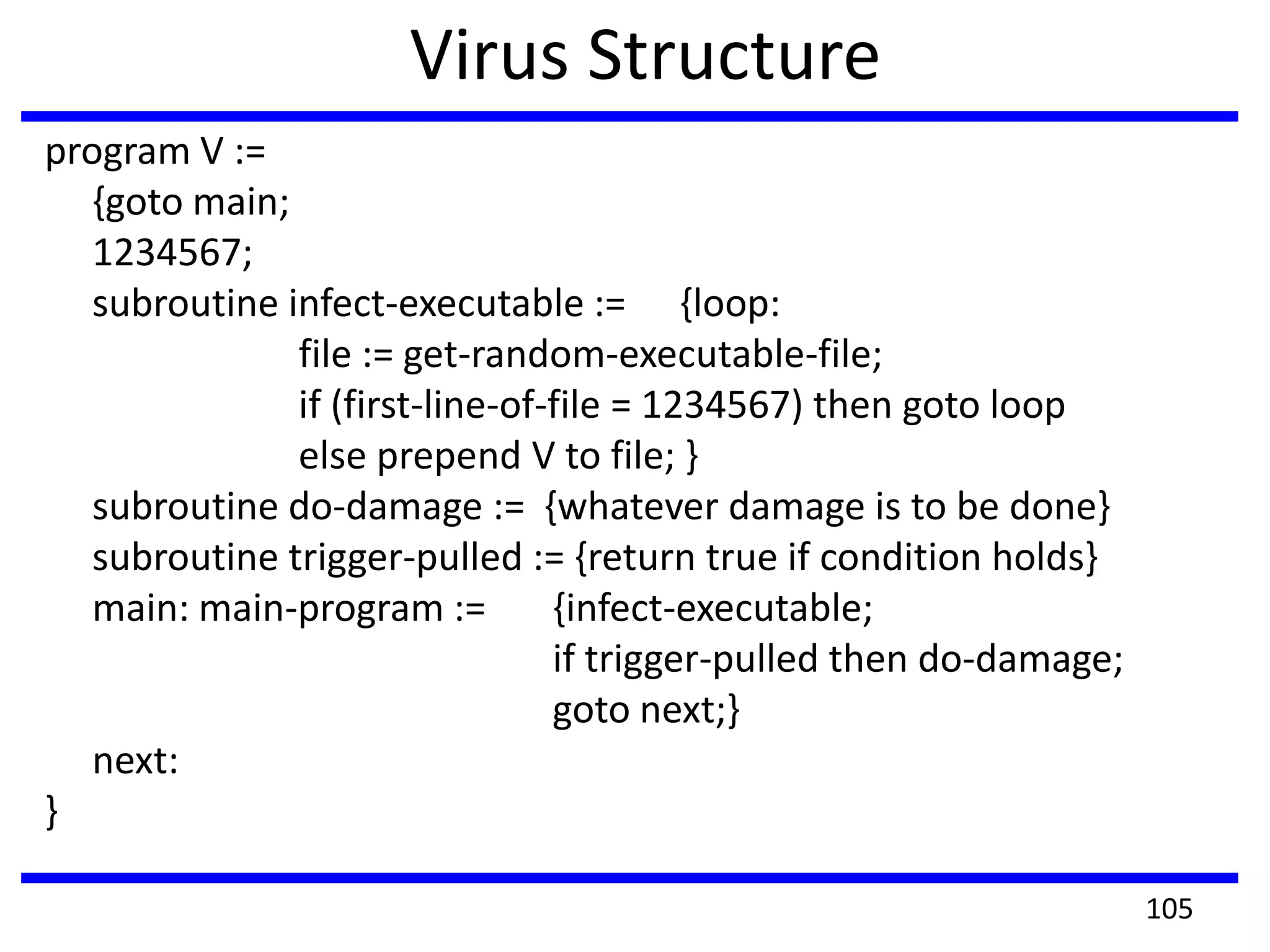
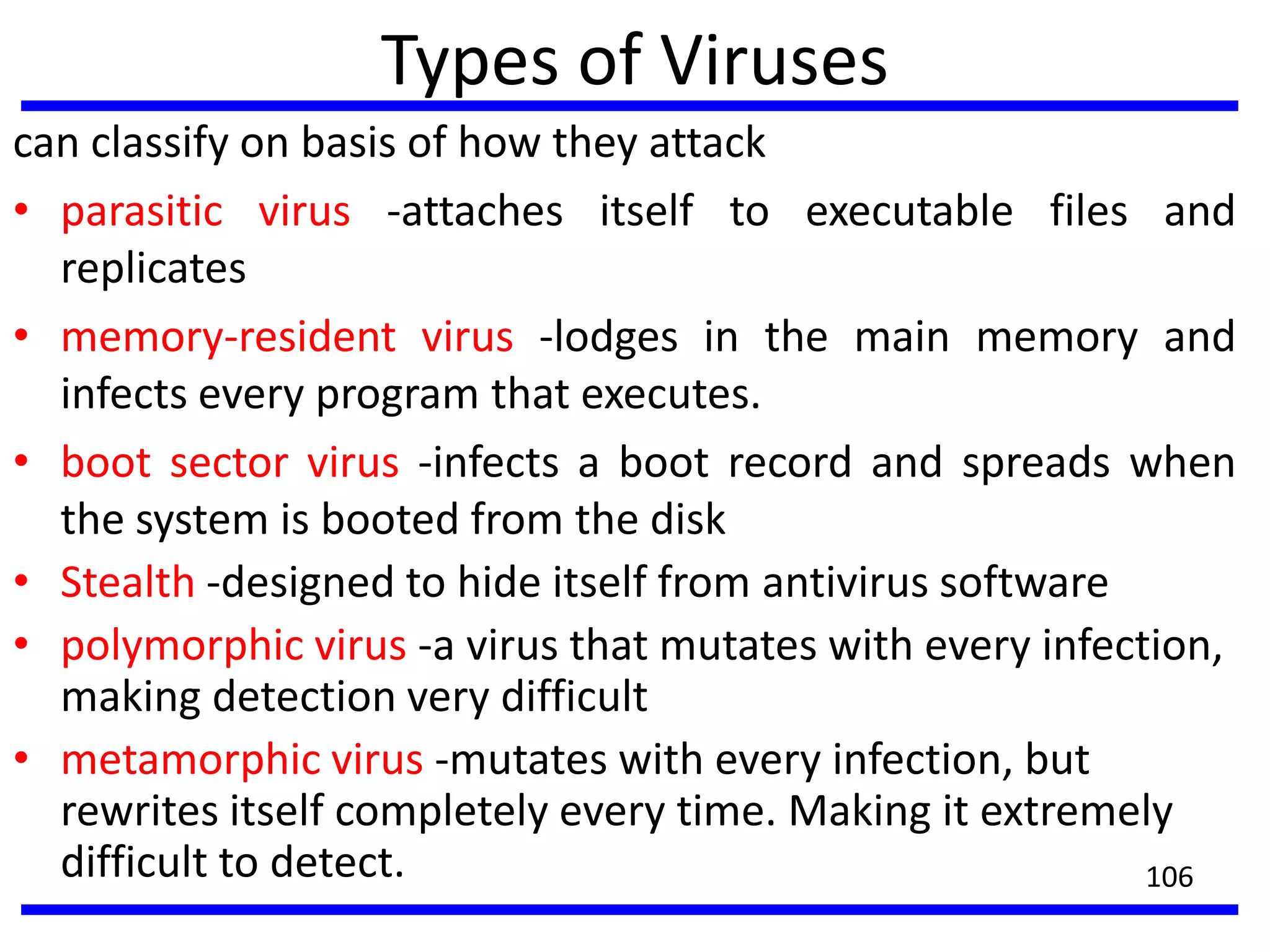
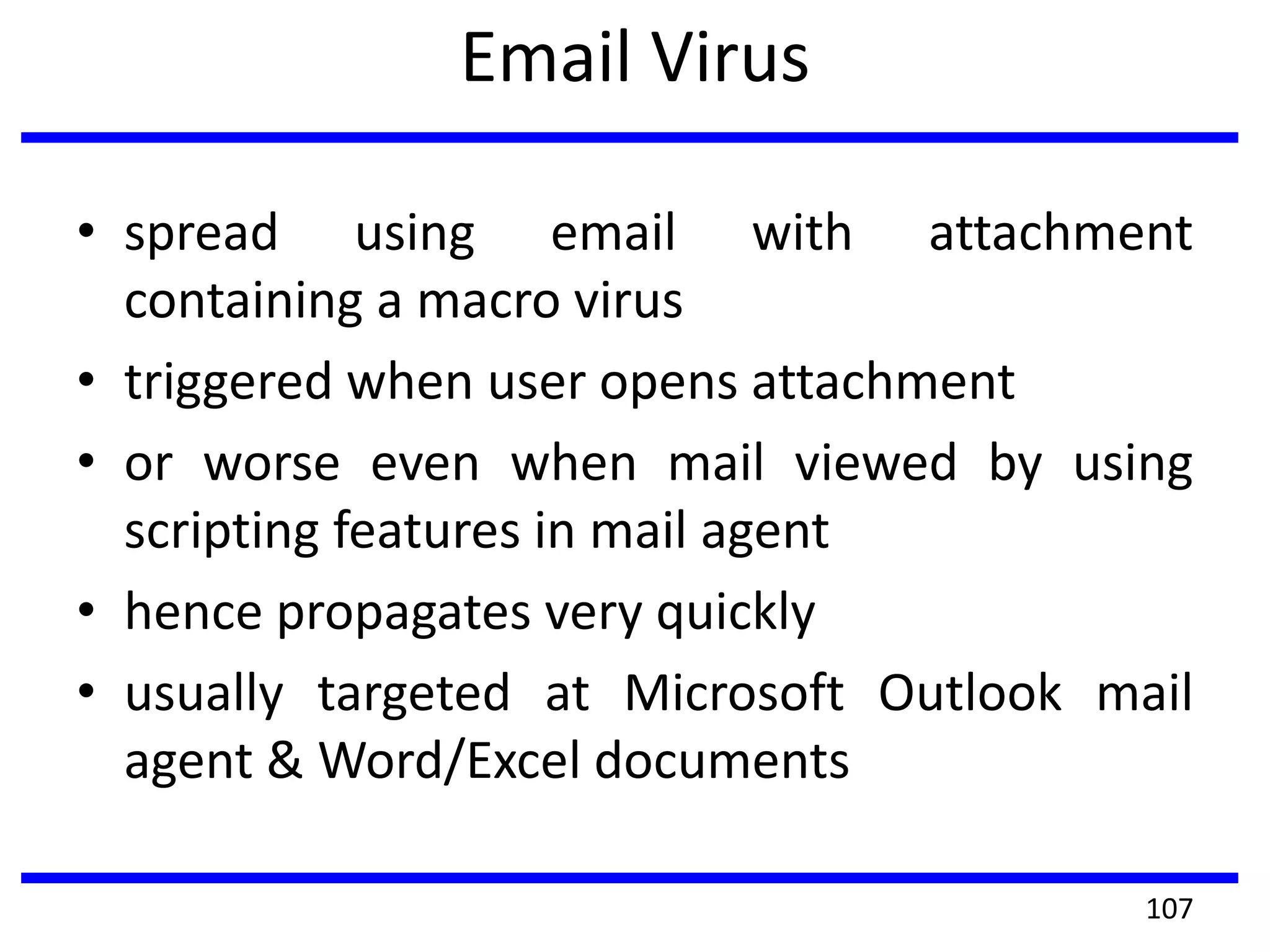
This document discusses advanced security practices in cryptography and networking, focusing on authentication methods like Kerberos and X.509 services, as well as the roles and types of firewalls. It details the mechanisms of user authentication, ticket granting, and session management in Kerberos, along with the implementation of secure electronic transactions (SET) for credit card processing. The document also covers firewall limitations, configurations, and intrusion detection systems to enhance network security.