This document discusses database security and SQL injection attacks. It begins with an overview of access control in SQL and views before discussing SQL injection attacks in more detail. The key points are that SQL injection attacks involve inserting malicious SQL statements into user input fields to exploit applications that directly insert user input into SQL queries. Examples are given of how attacks can read or delete entire databases. The best defenses include using prepared statements with bound parameters and validating/sanitizing all user input.



![+ 5
Access Control in SQL
GRANT privileges ON object TO users
[WITH GRANT OPTIONS]
GRANT privileges ON object TO users
[WITH GRANT OPTIONS]
privileges = SELECT | INSERT | DELETE | . . .
object = table | attribute
REVOKE privileges ON object FROM users
[CASCADE ]
REVOKE privileges ON object FROM users
[CASCADE ]
[Griffith&Wade'76, Fagin'78]](https://image.slidesharecdn.com/sqlsecurity-140824110104-phpapp01/85/Sql-security-5-320.jpg)


![+
Views in MySQL
http://dev.mysql.com/doc/refman/5.0/en/create-view.html
CREATE [OR REPLACE]
[ALGORITHM = {UNDEFINED | MERGE | TEMPTABLE}]
[DEFINER = { user | CURRENT_USER }]
[SQL SECURITY { DEFINER | INVOKER }]
VIEW view_name [(column_list)]
AS select_statement
[WITH [CASCADED | LOCAL] CHECK OPTION]
The DEFINER and SQL SECURITY clauses determine which
MySQL account to use when checking access privileges for
the view when a statement is executed that references the
view.](https://image.slidesharecdn.com/sqlsecurity-140824110104-phpapp01/85/Sql-security-8-320.jpg)








![+
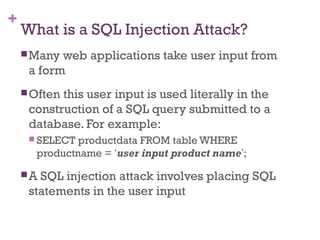
An Example SQL Injection Attack
Product Search:
This input is put directly into the SQL statement within the
Web application:
$query = “SELECT prodinfo FROM prodtable WHERE prodname =
‘” . $_POST[‘prod_search’] . “’”;
Creates the following SQL:
SELECT prodinfo FROM prodtable WHERE prodname = ‘blah‘ OR ‘x’ = ‘x’
Attacker has now successfully caused the entire database to be
returned.
blah‘ OR ‘x’ = ‘x](https://image.slidesharecdn.com/sqlsecurity-140824110104-phpapp01/85/Sql-security-18-320.jpg)







