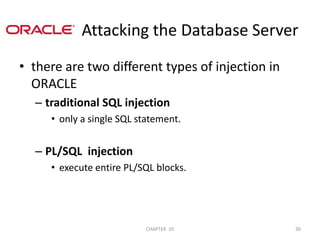
This document provides an extensive overview of Structured Query Language (SQL), focusing on SQL injection techniques, common queries, and methods to exploit vulnerabilities. It discusses the historical development of SQL, various types of SQL statements, and detailed strategies for identifying and attacking different database platforms. The document also includes cheat sheets for SQL injections and references to various tools and resources related to SQL security and exploitation.



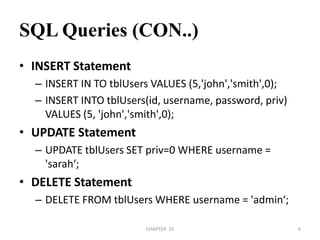


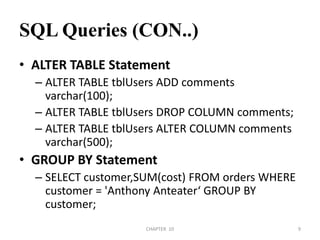



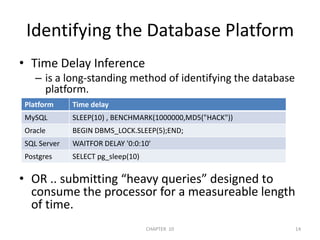









![Quote Filters (con…)#!/usr/bin/perlprint "Enter SQL query to encode:";$teststr=<STDIN>;chomp $teststr;$hardcoded_sql ='declare @q varchar(8000) '.'select @q=0x*** '.'exec(@q)';$prepared = encode_sql($teststr);$hardcoded_sql =∼s/\*\*\*/$prepared/g;print "\n[*]-Encoded SQL:\n\n";print $hardcoded_sql ."\n";sub encode_sql{@subvar=@_;my $sqlstr =$subvar[0];@ASCII = unpack("C*", $sqlstr);foreach $line (@ASCII) {$encoded = sprintf('%lx',$line);$encoded_command .= $encoded;}return $encoded_command;}CHAPTER 10392/04/2011](https://image.slidesharecdn.com/references-110404133442-phpapp02/85/References-sql-injection-39-320.jpg)