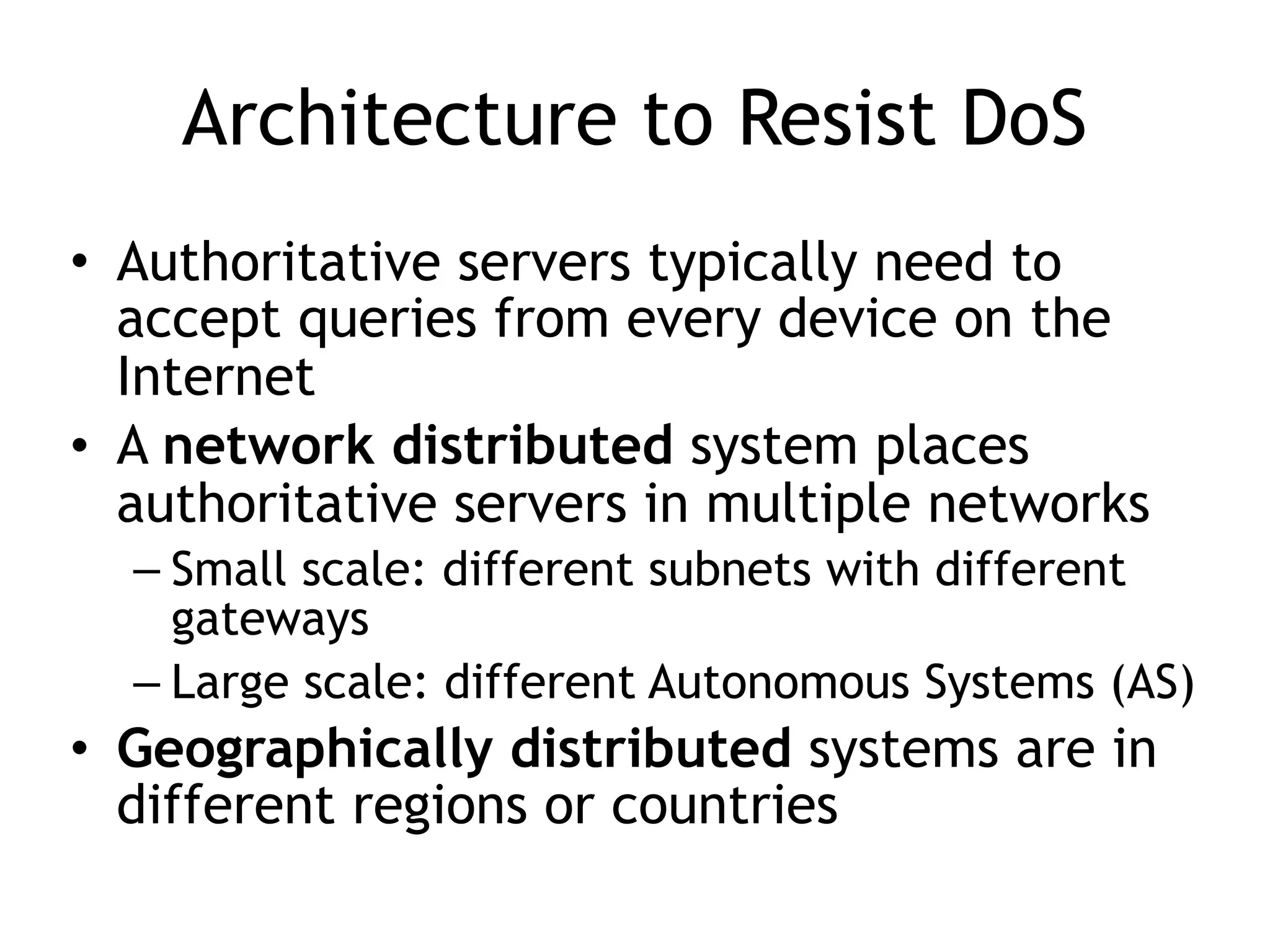
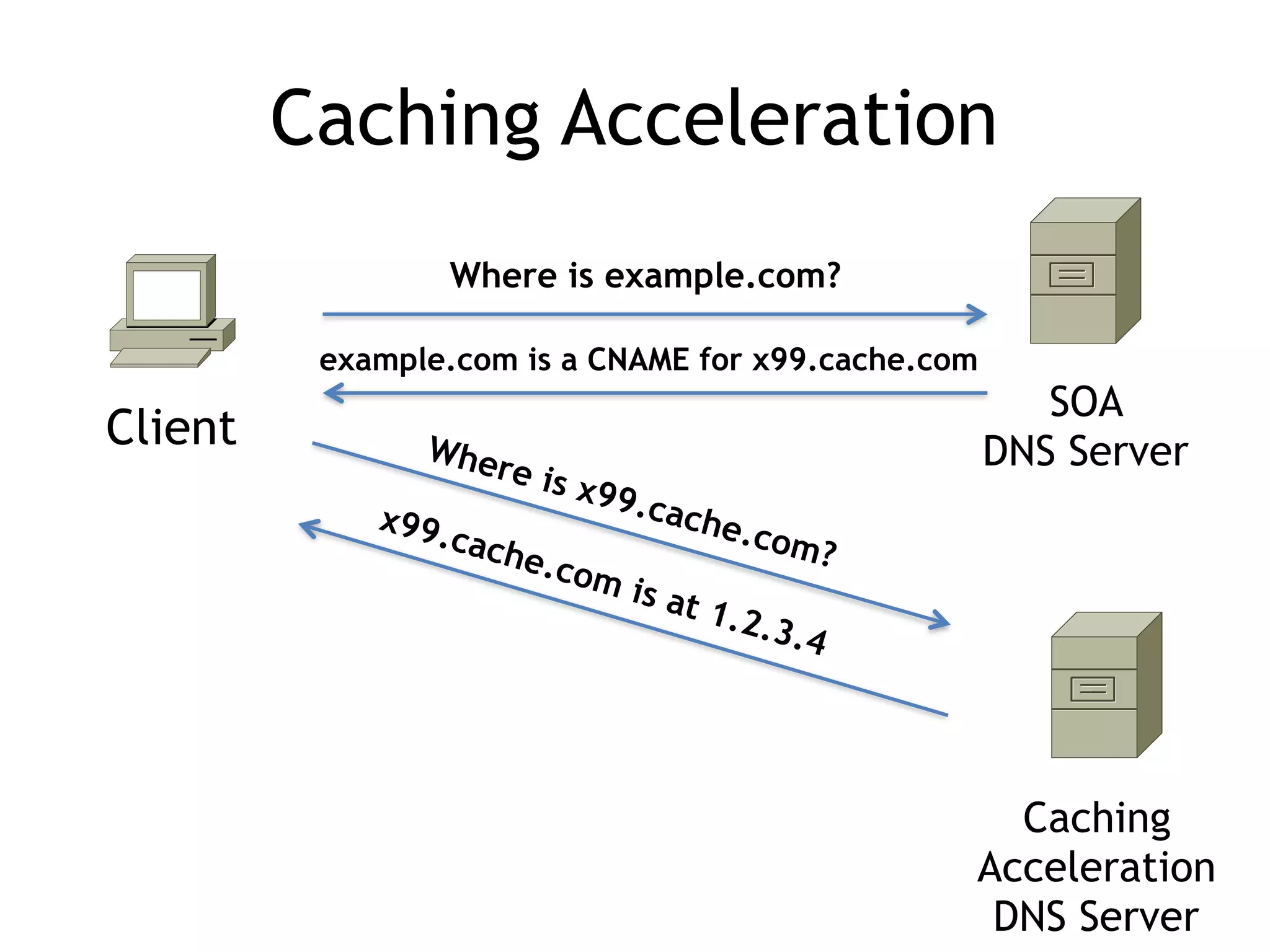
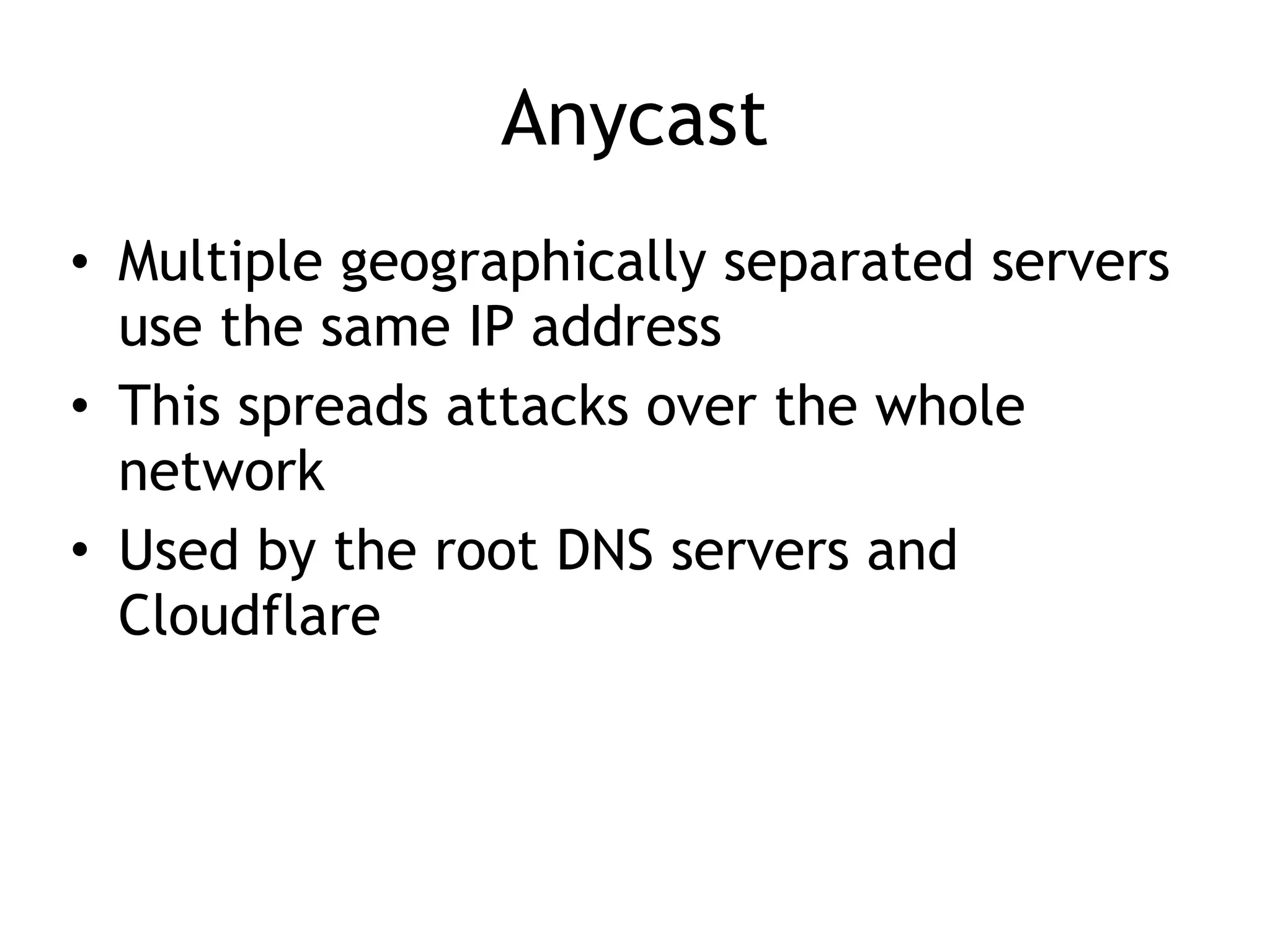
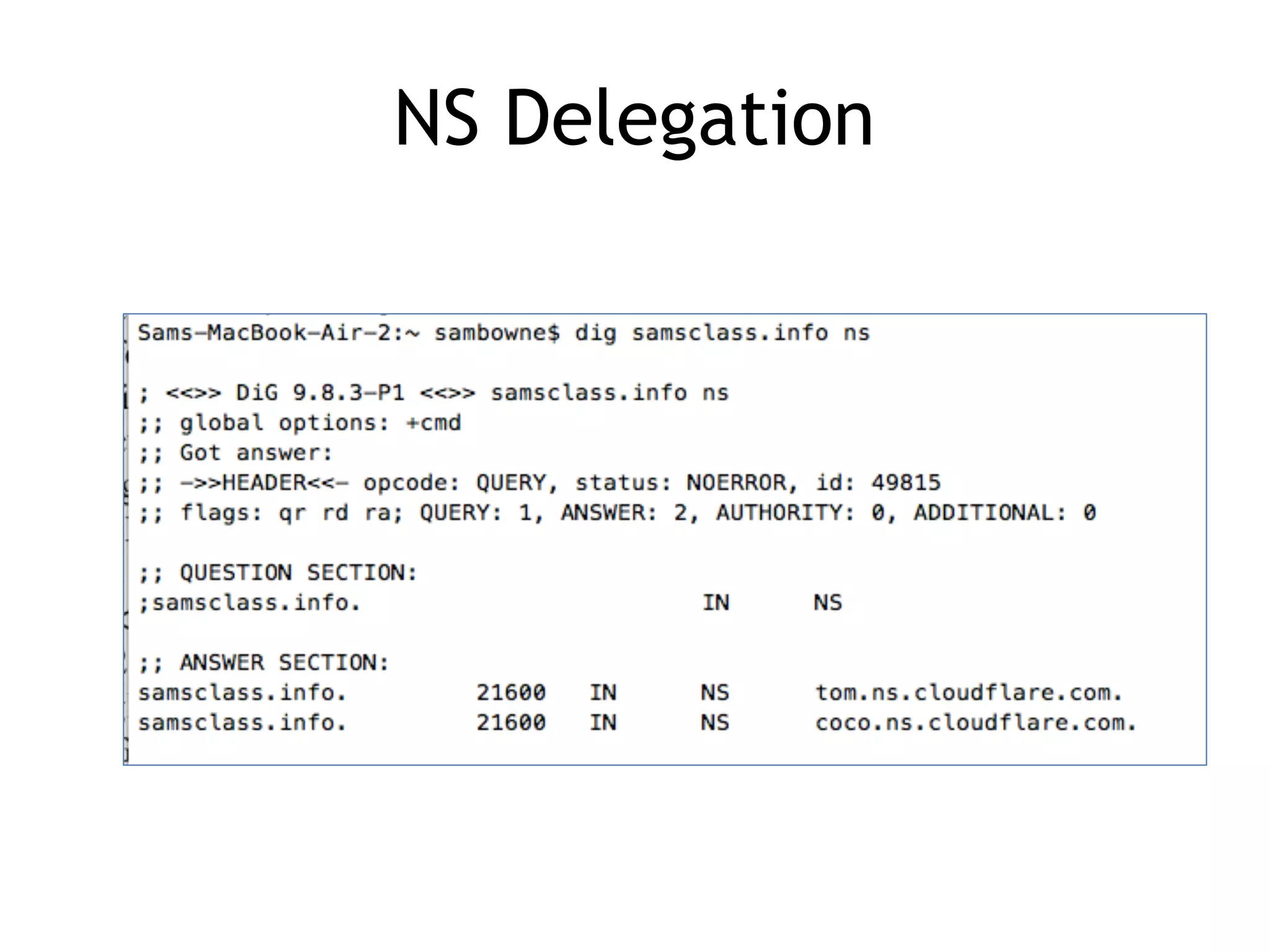
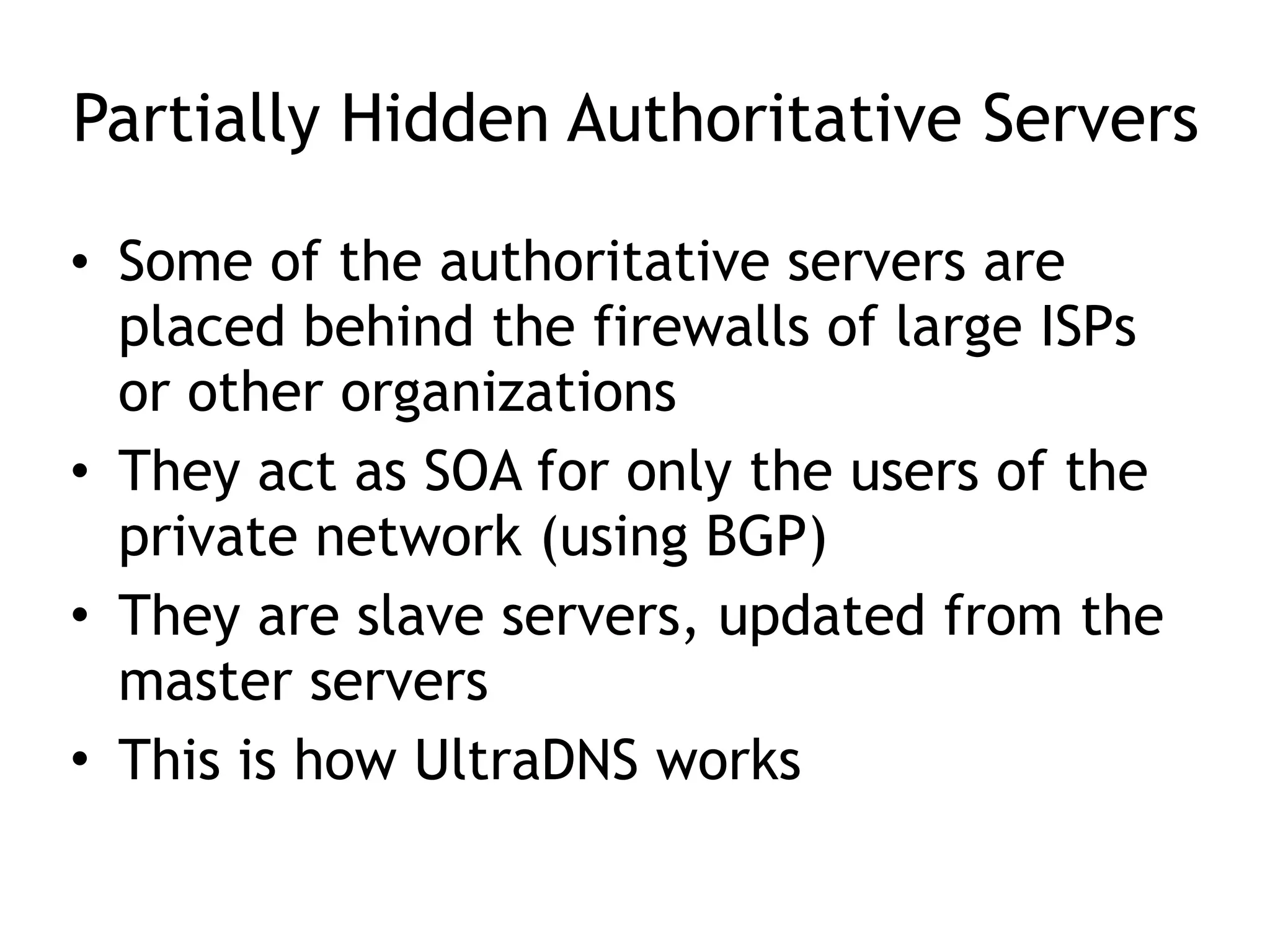
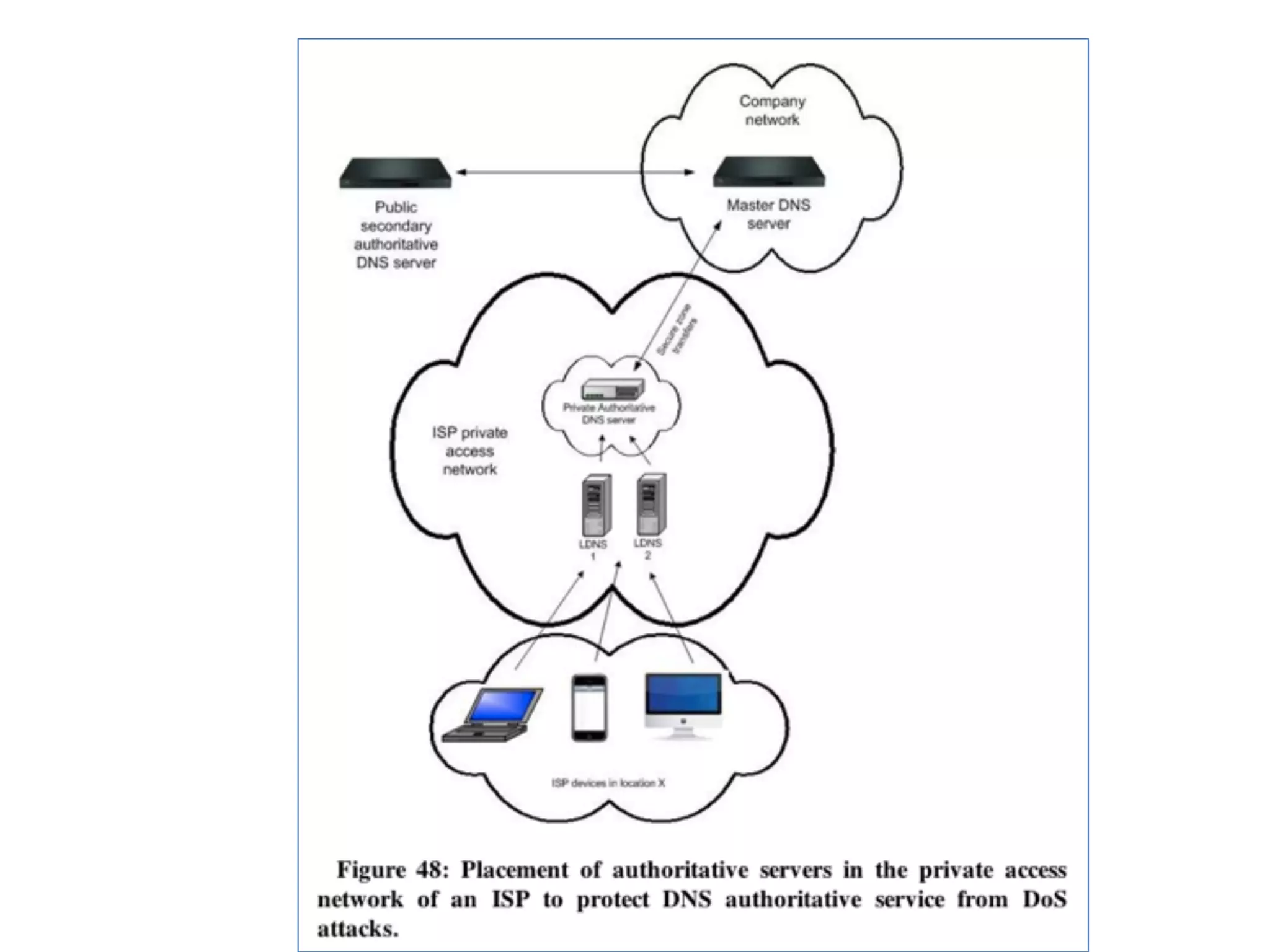
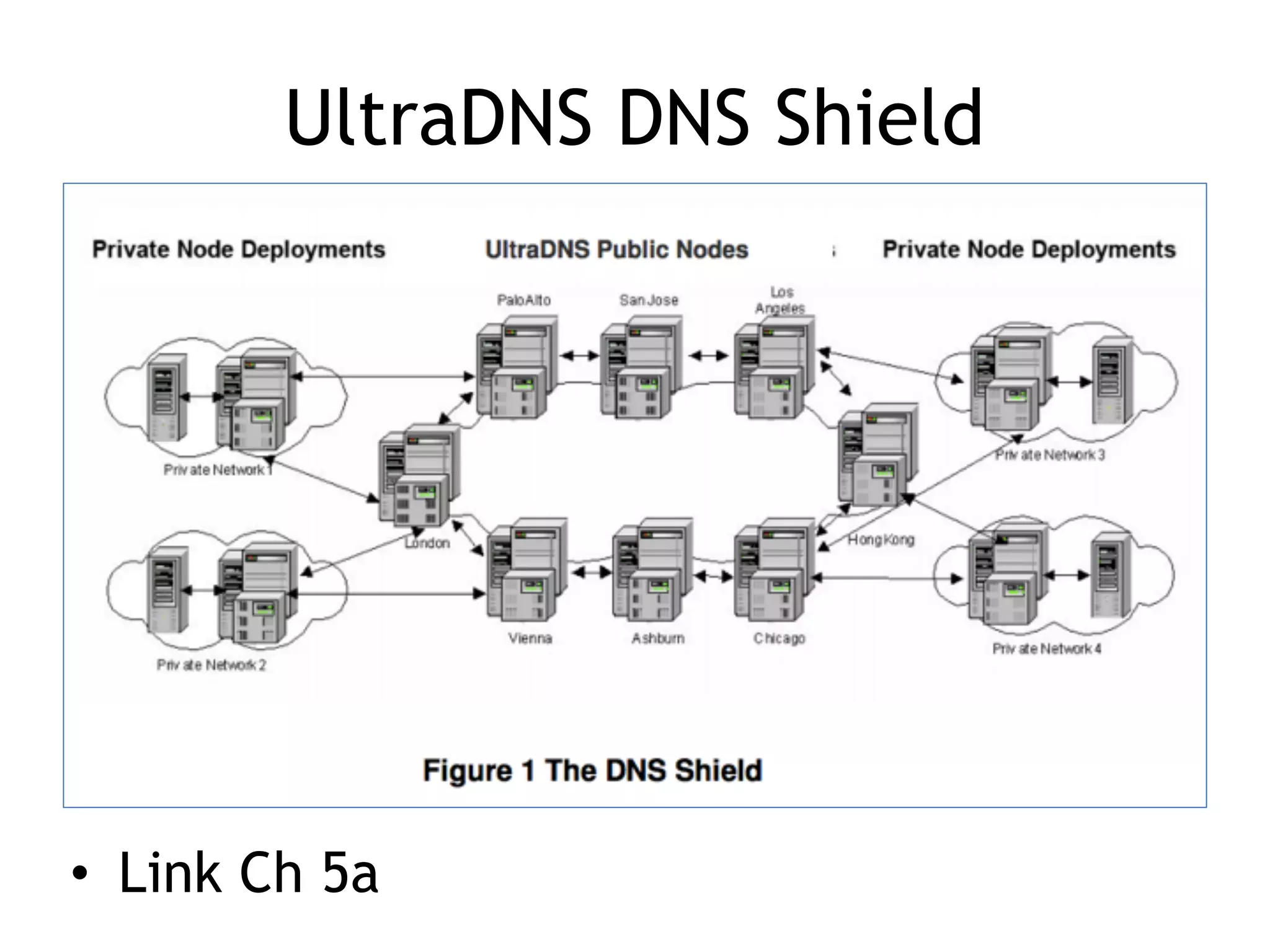
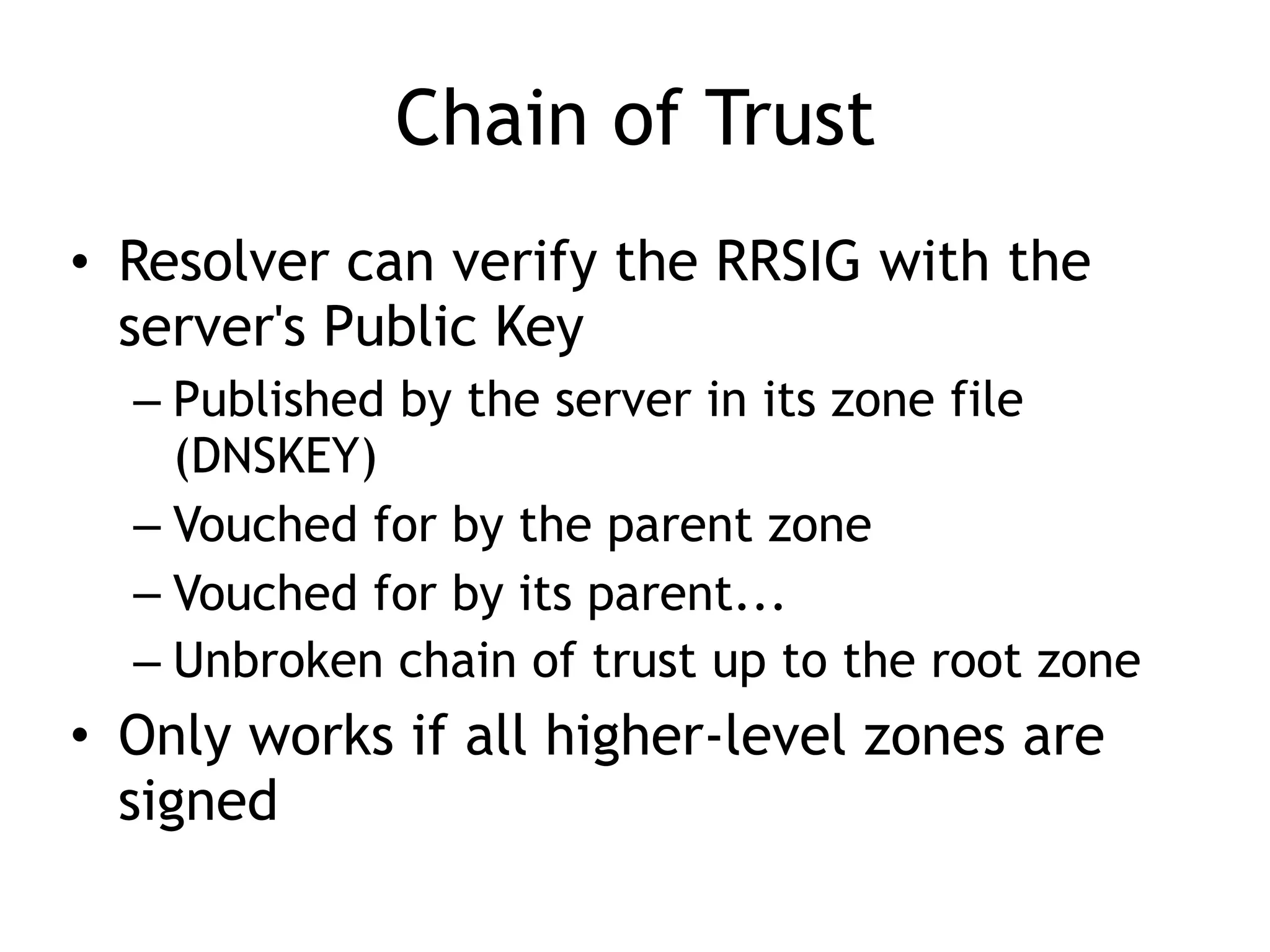
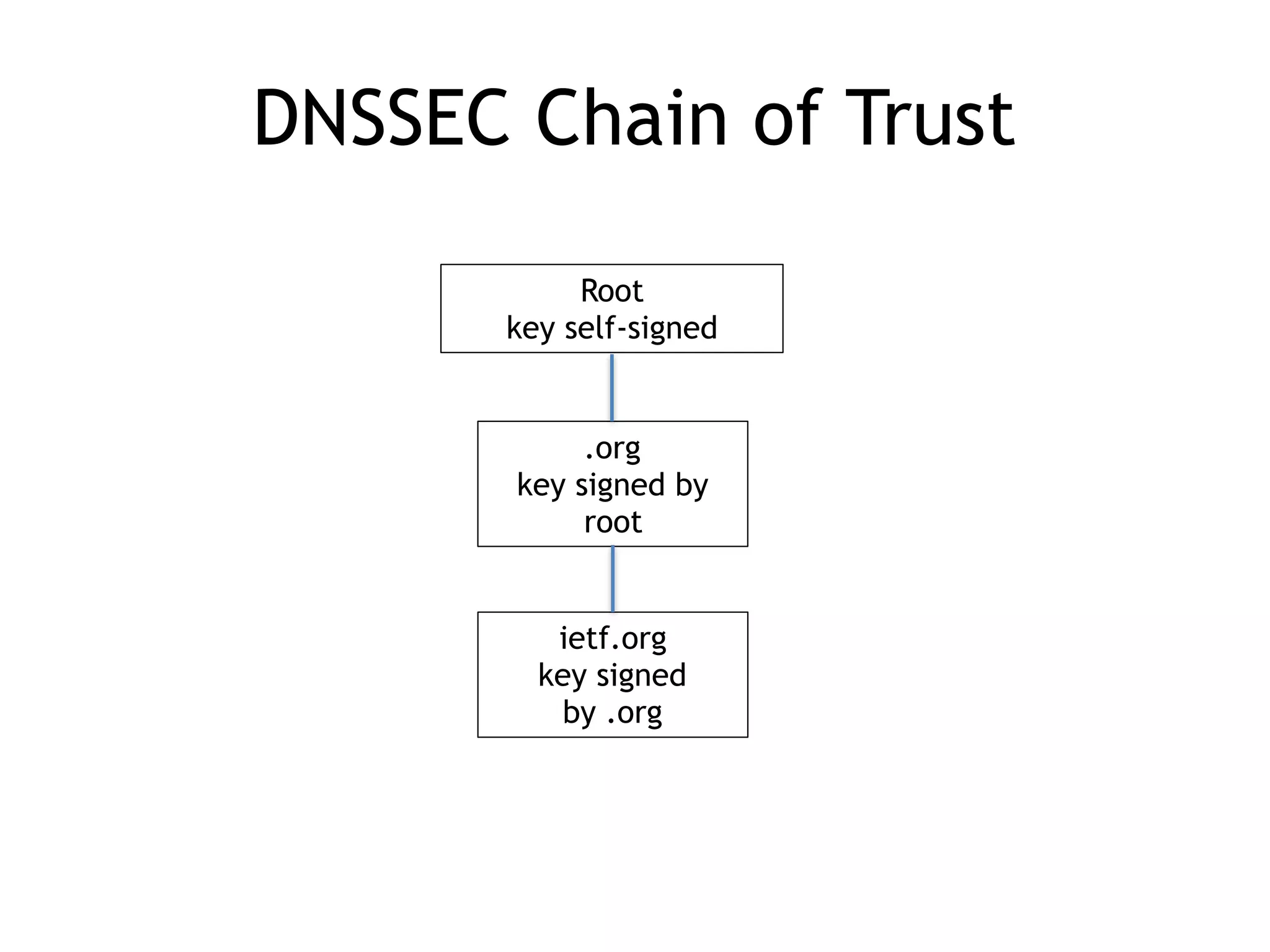
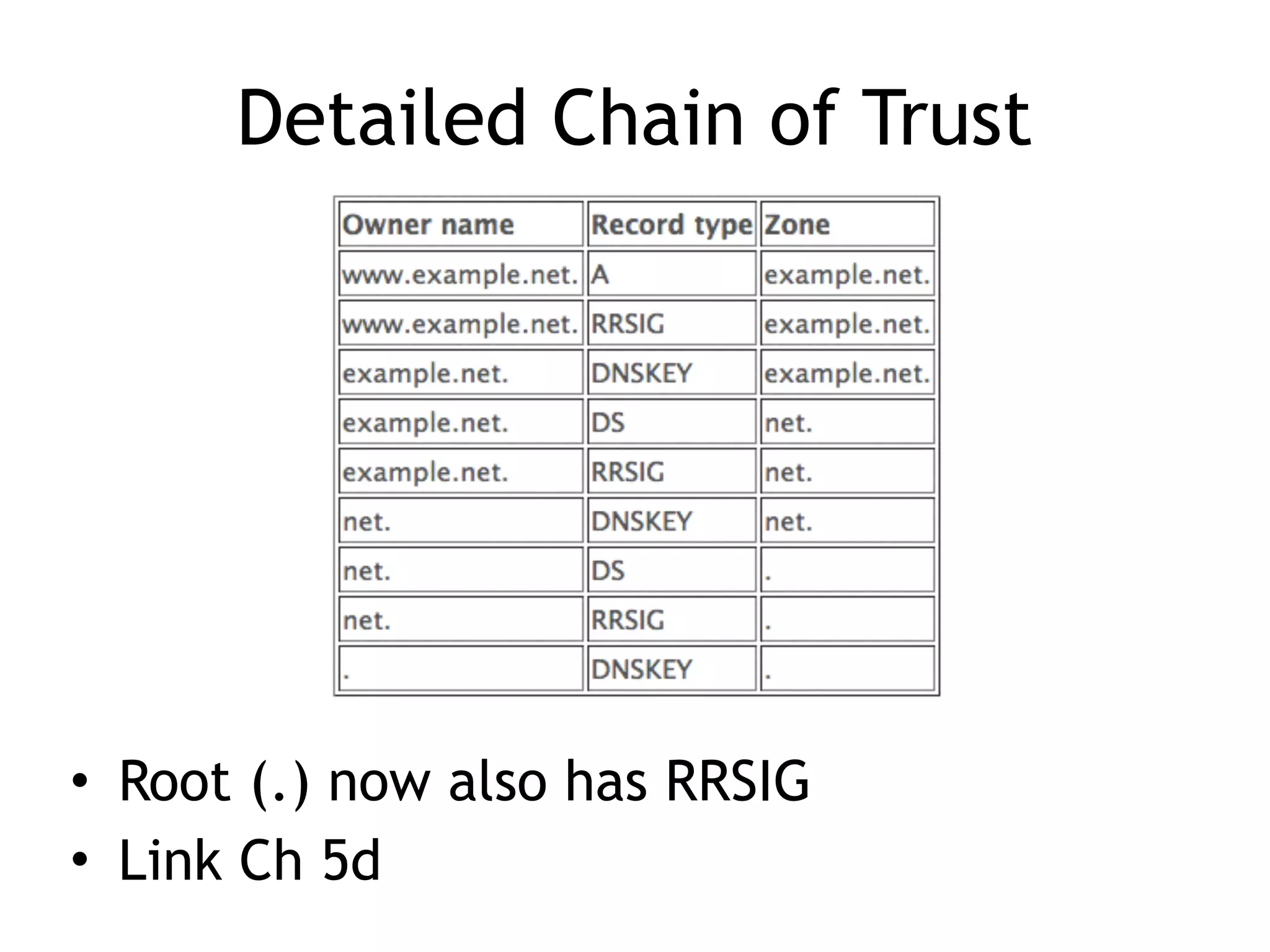
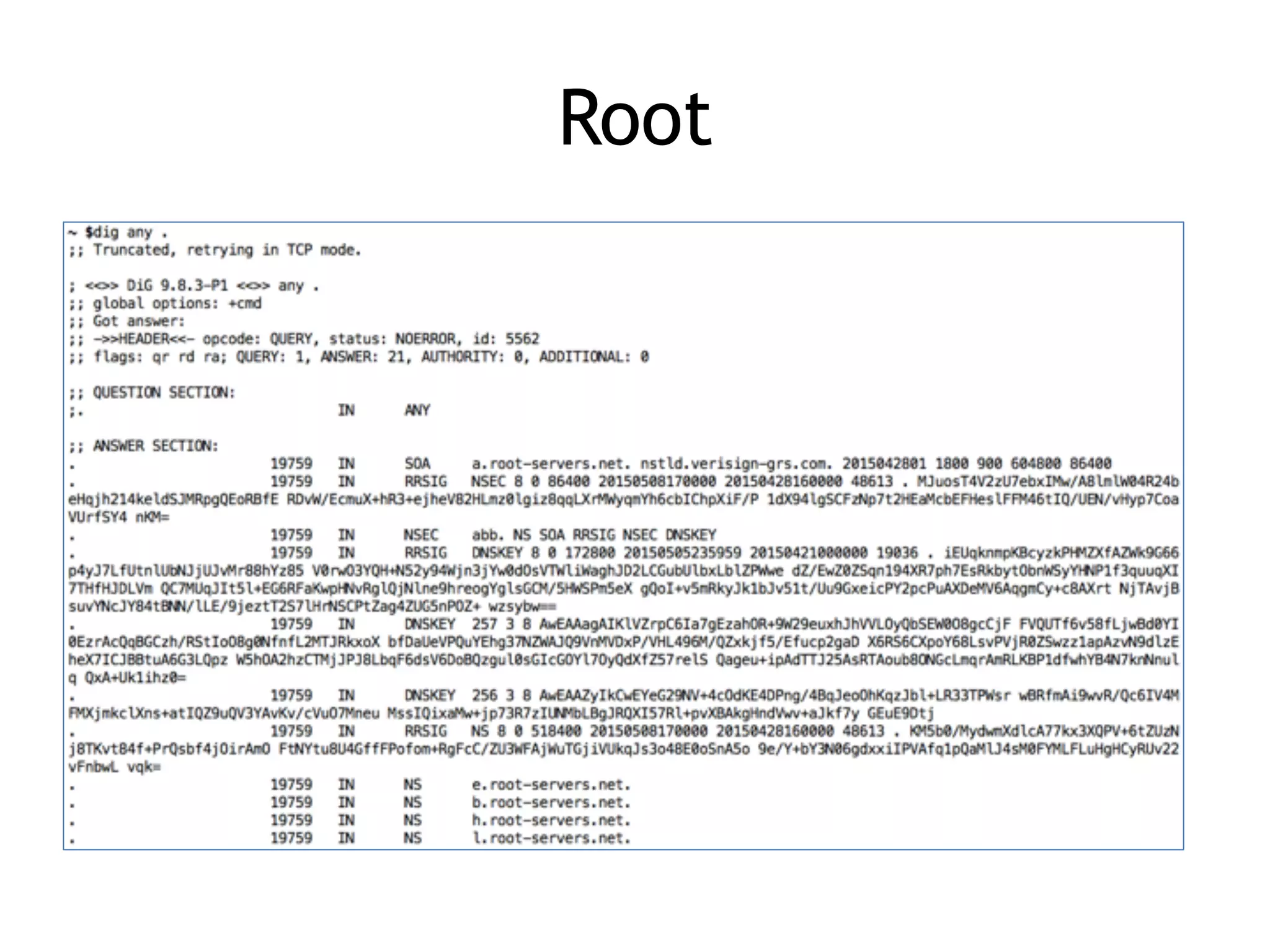
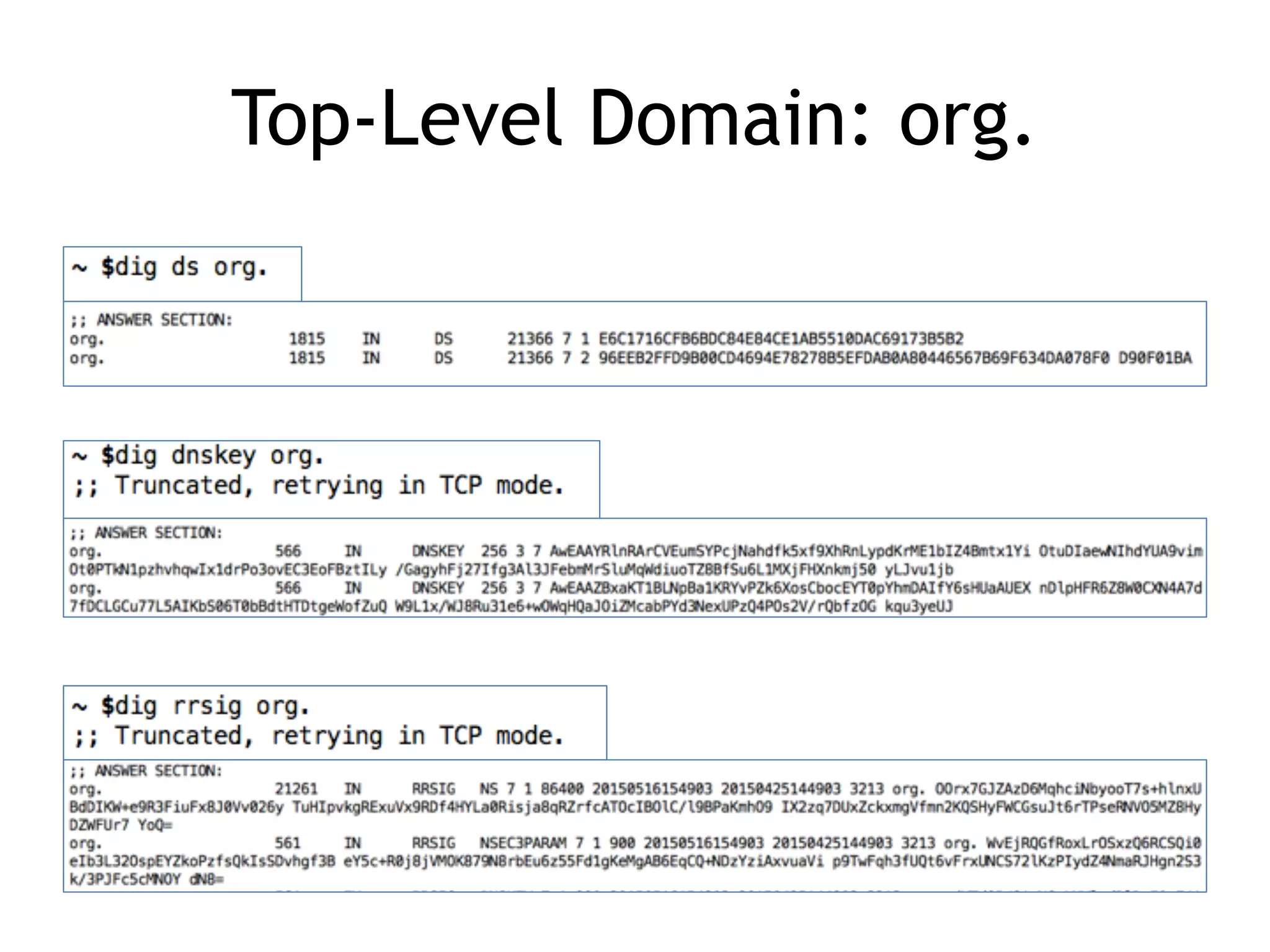
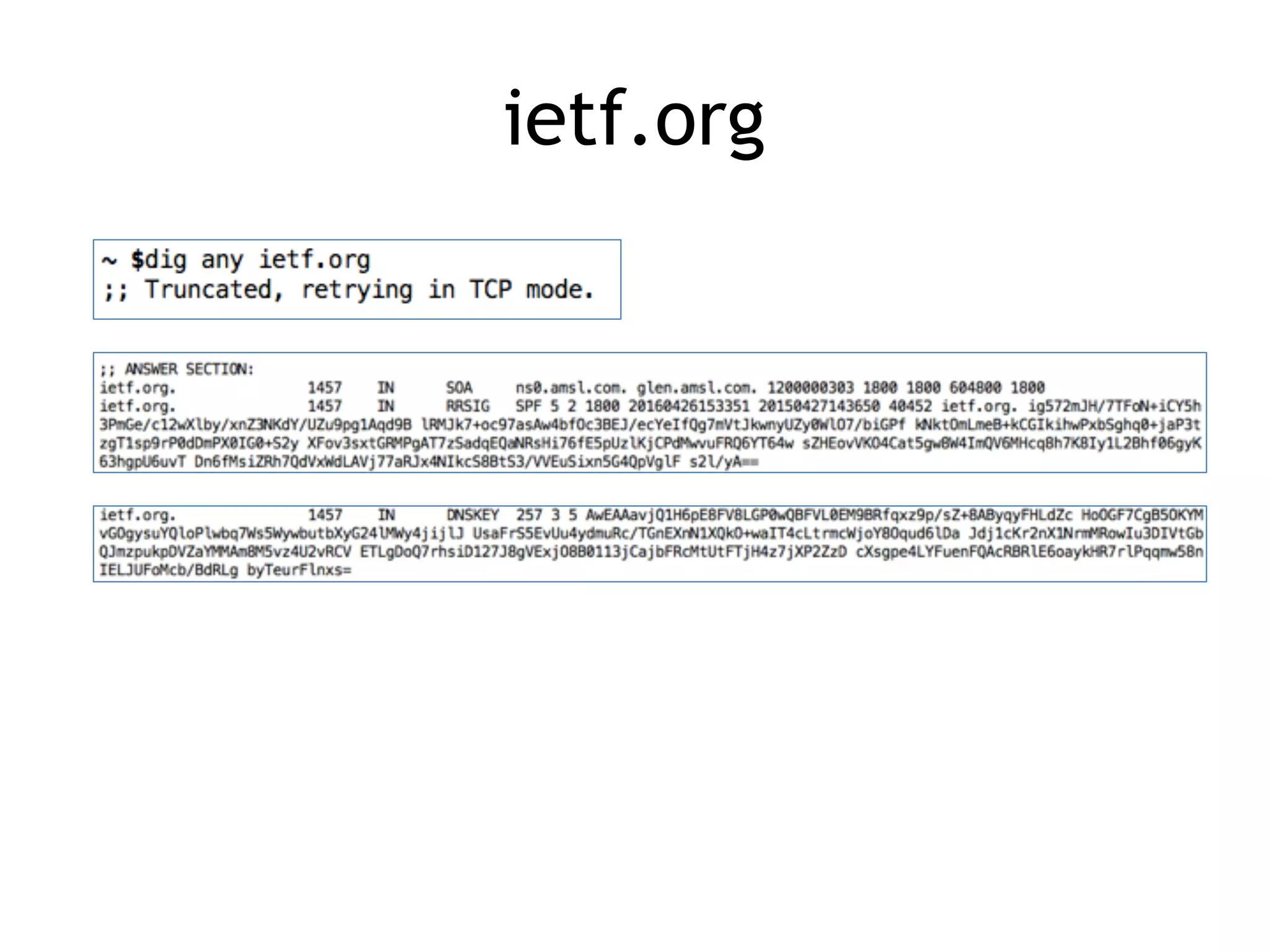
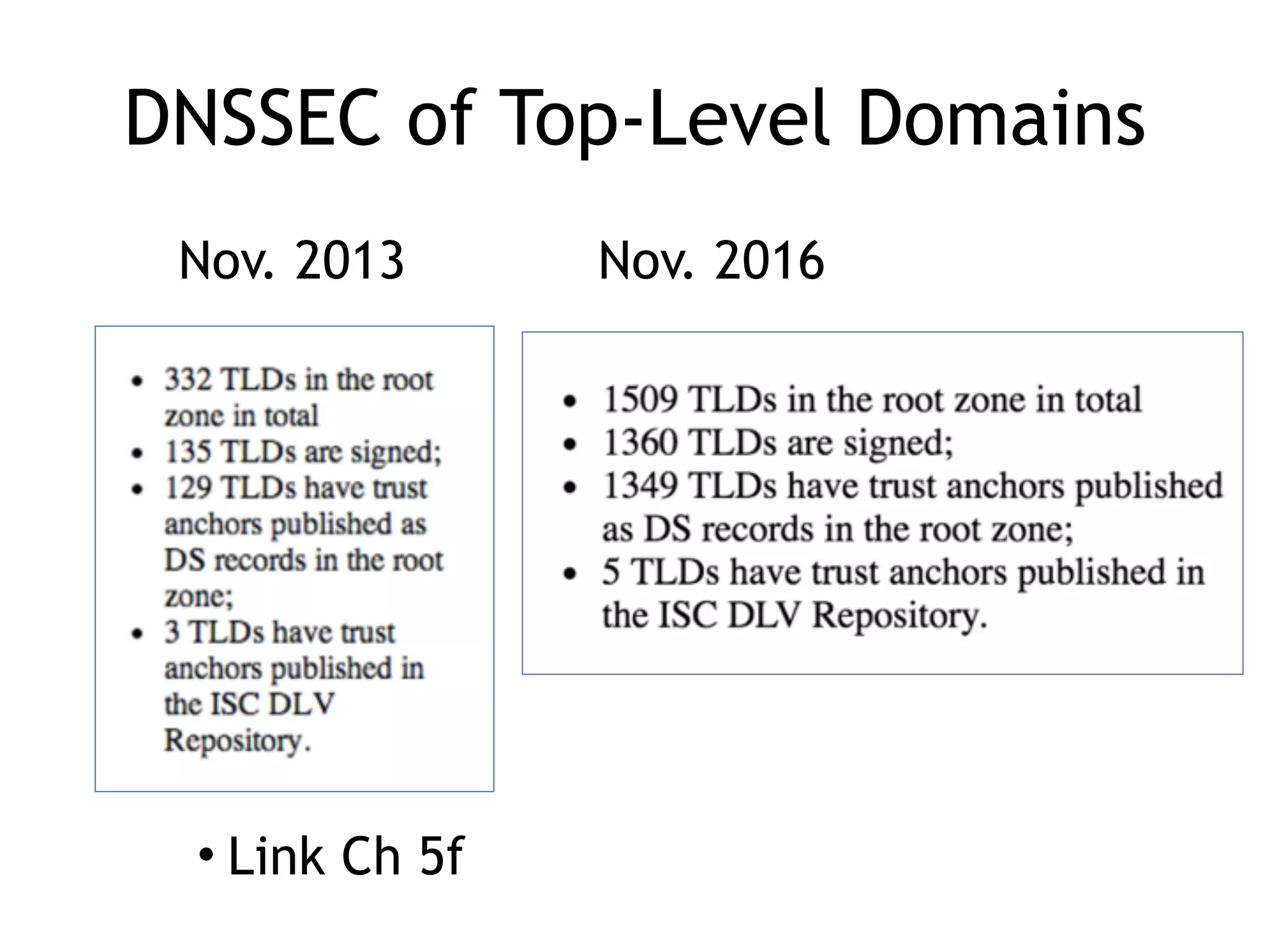
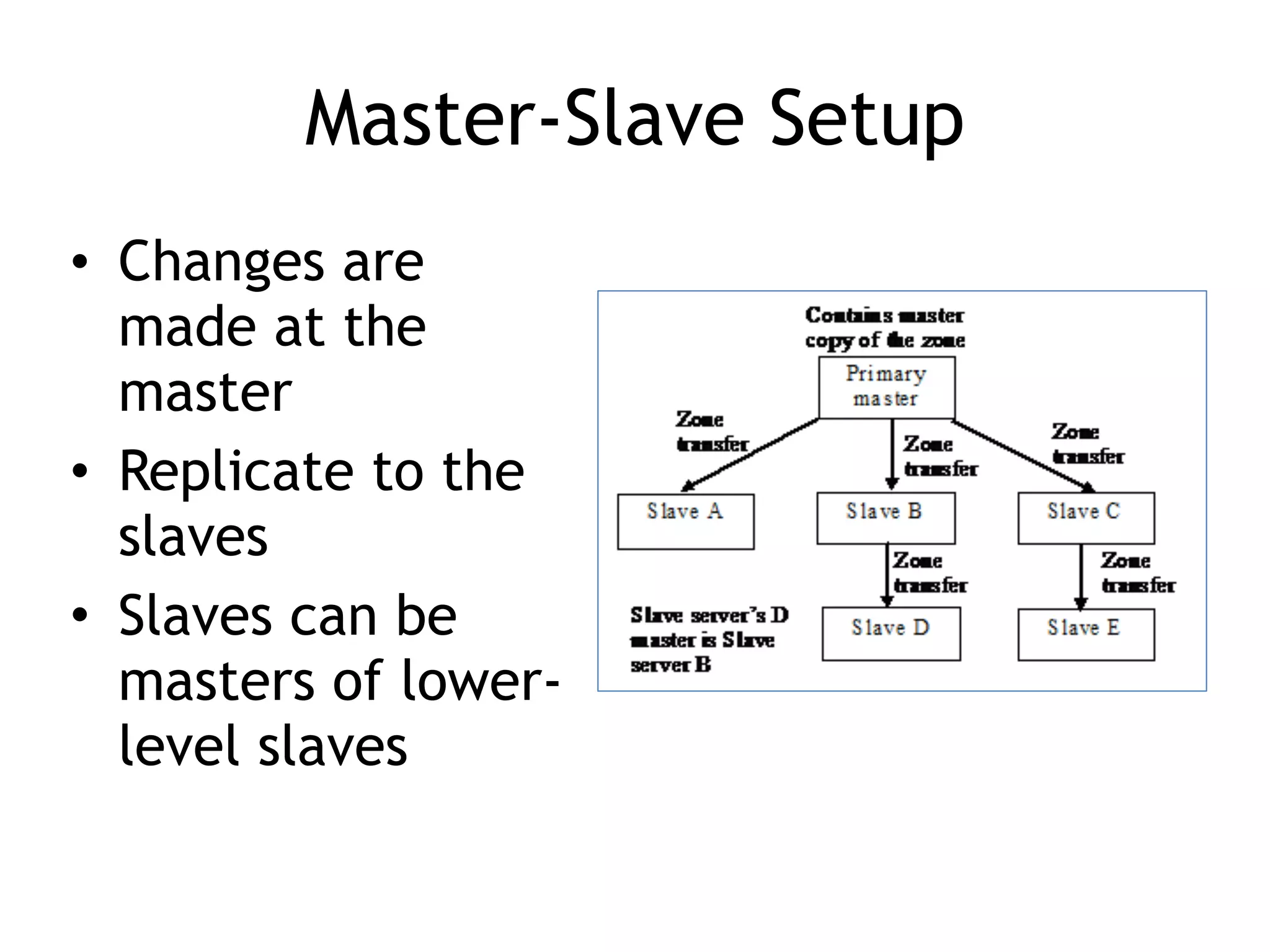
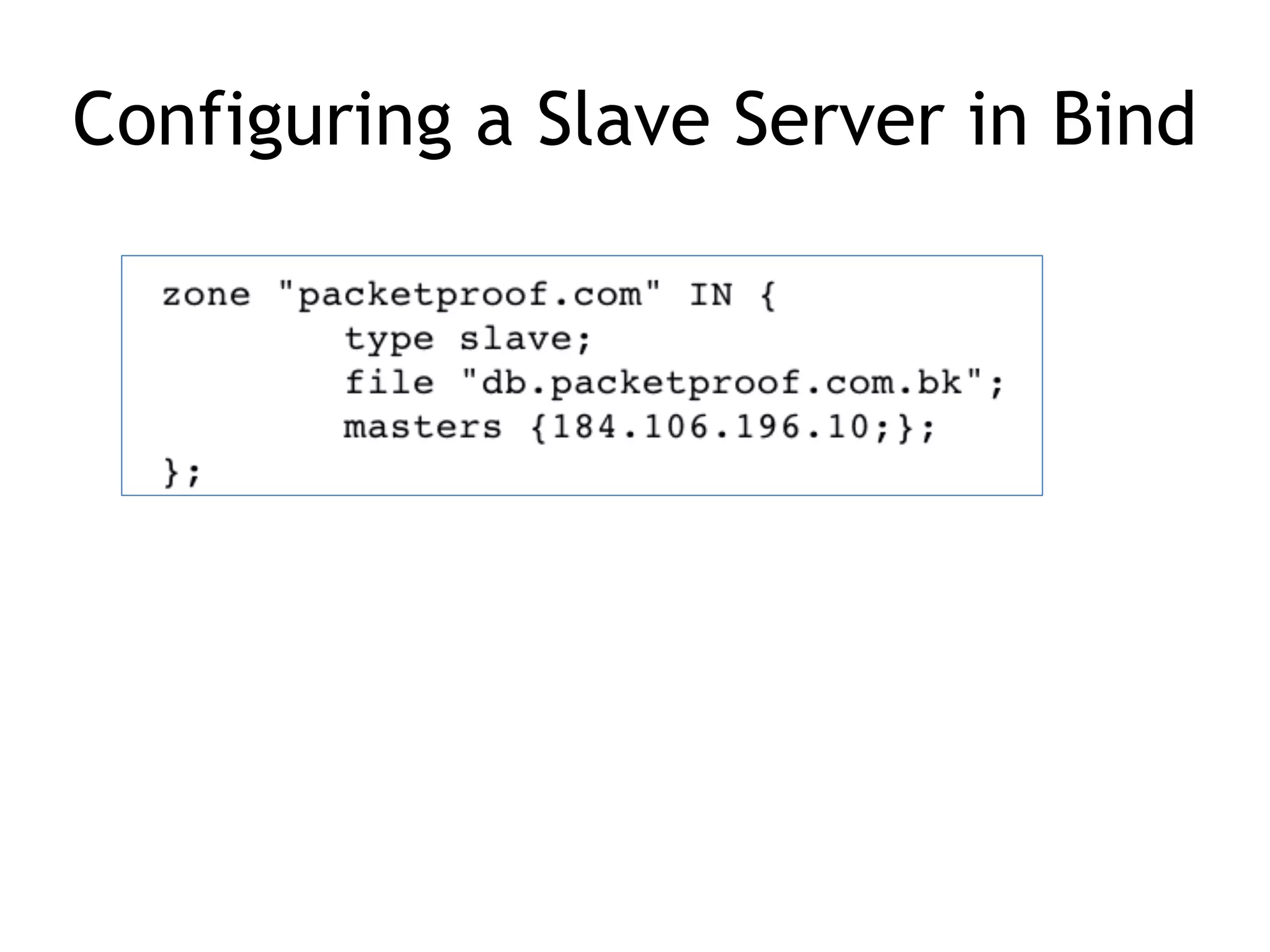
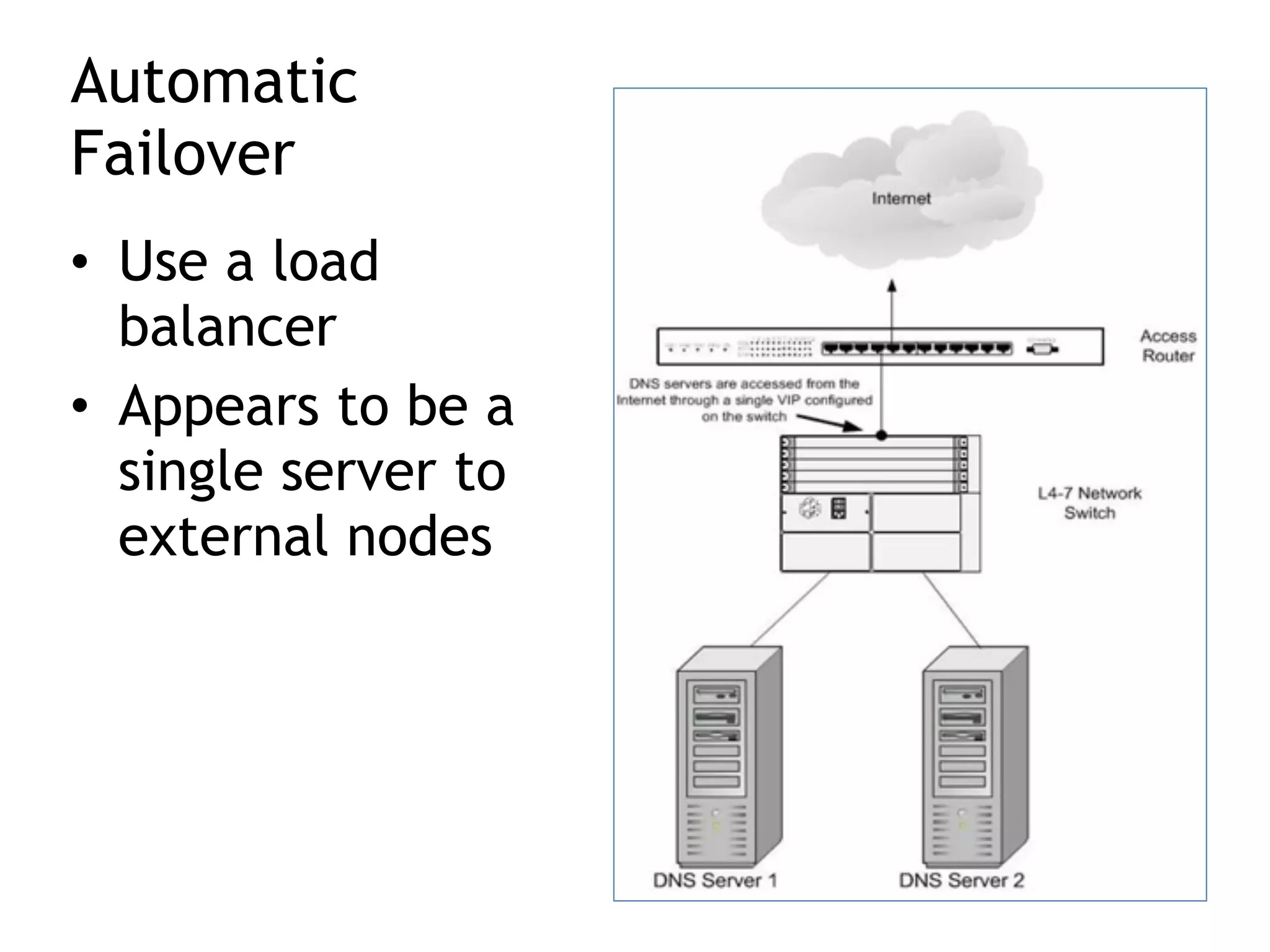
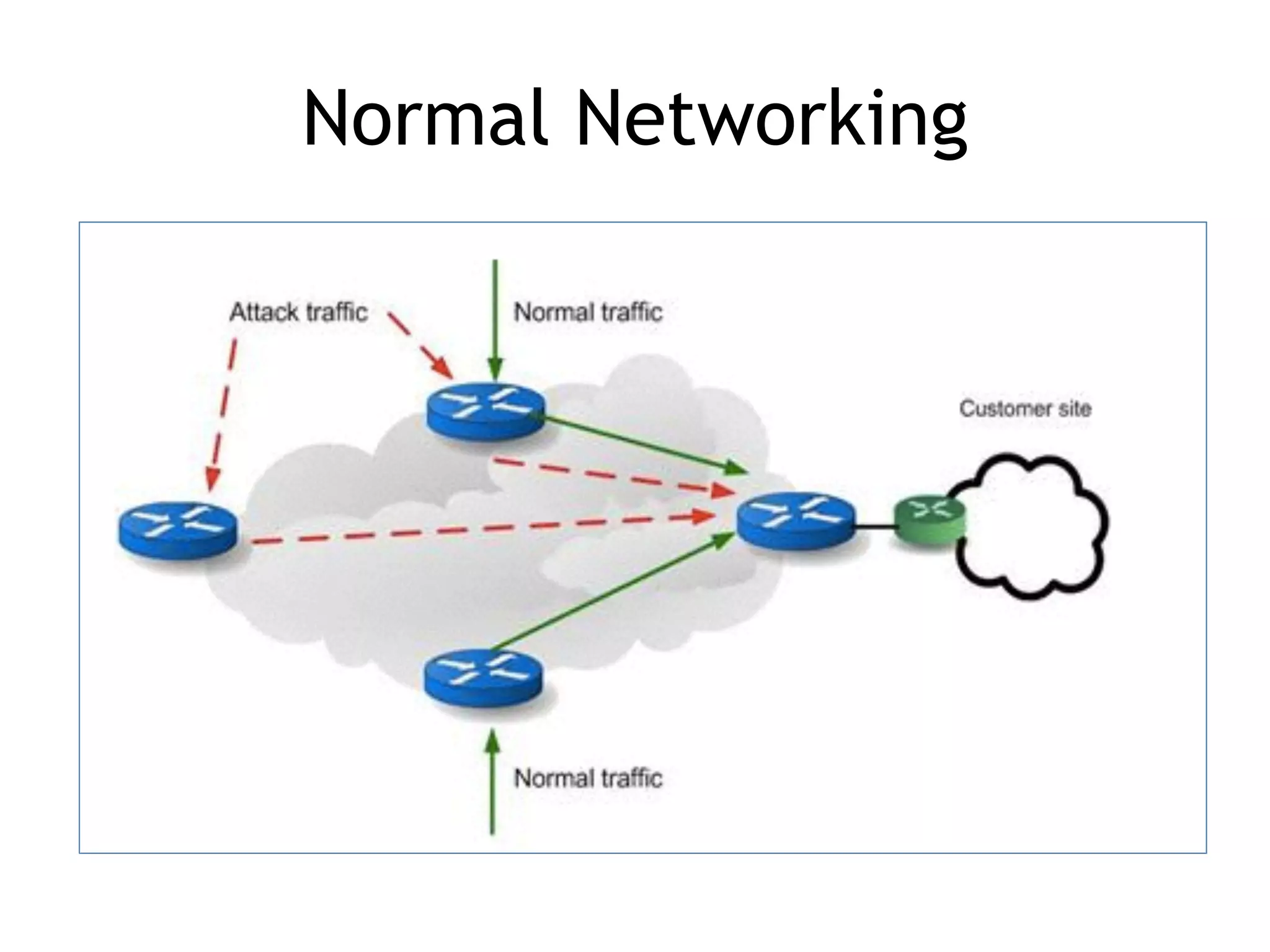
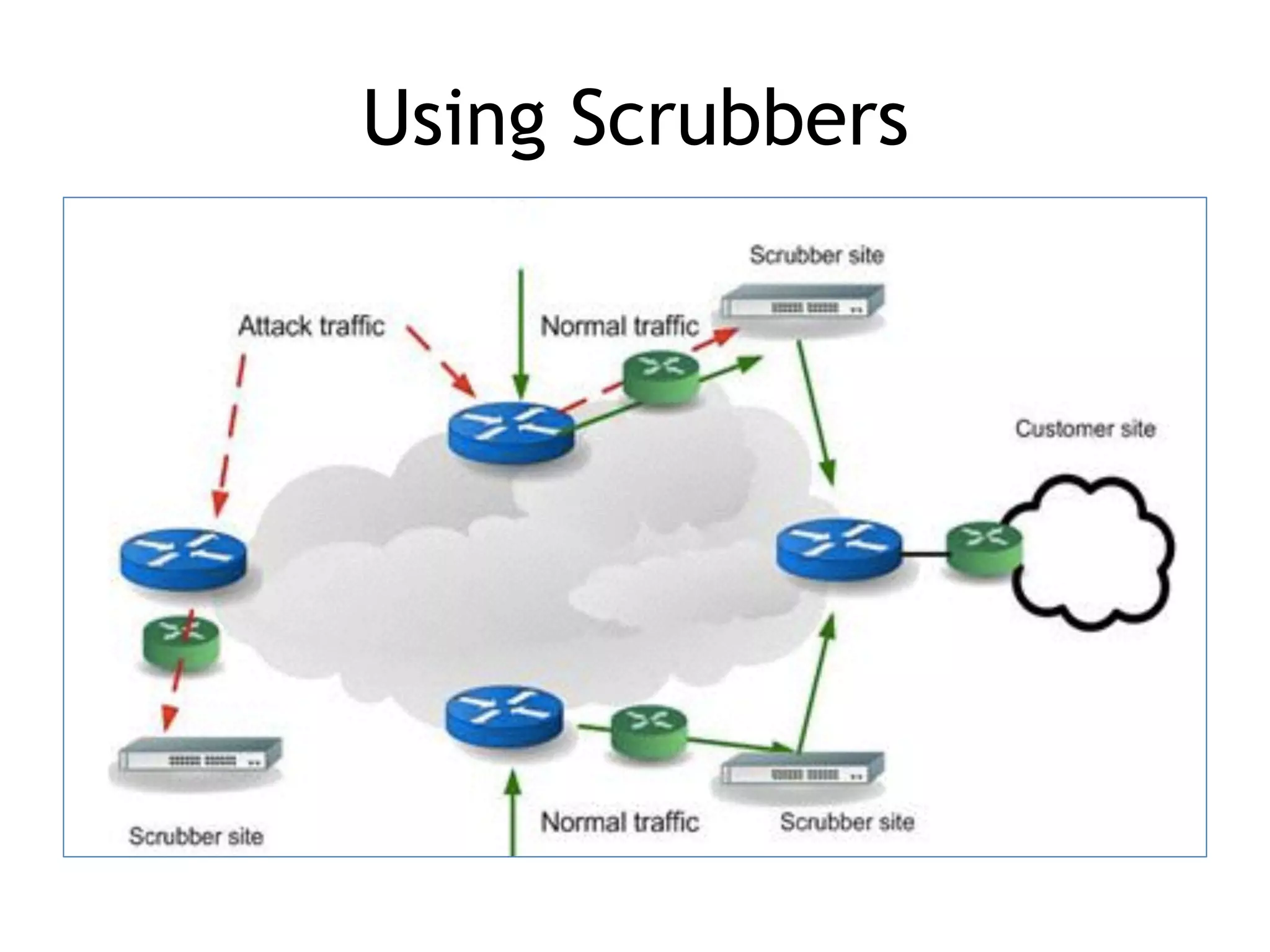
Chapter 5 discusses strategies for preventing DNS service disruptions, emphasizing the architecture of distributed systems and various types of DoS protection. It covers DNS security measures, including DNSSEC for data integrity and authenticity, and techniques for managing server failover and monitoring. The chapter also highlights the importance of regular backups and the use of firewalls and scrubbers to protect against attacks.