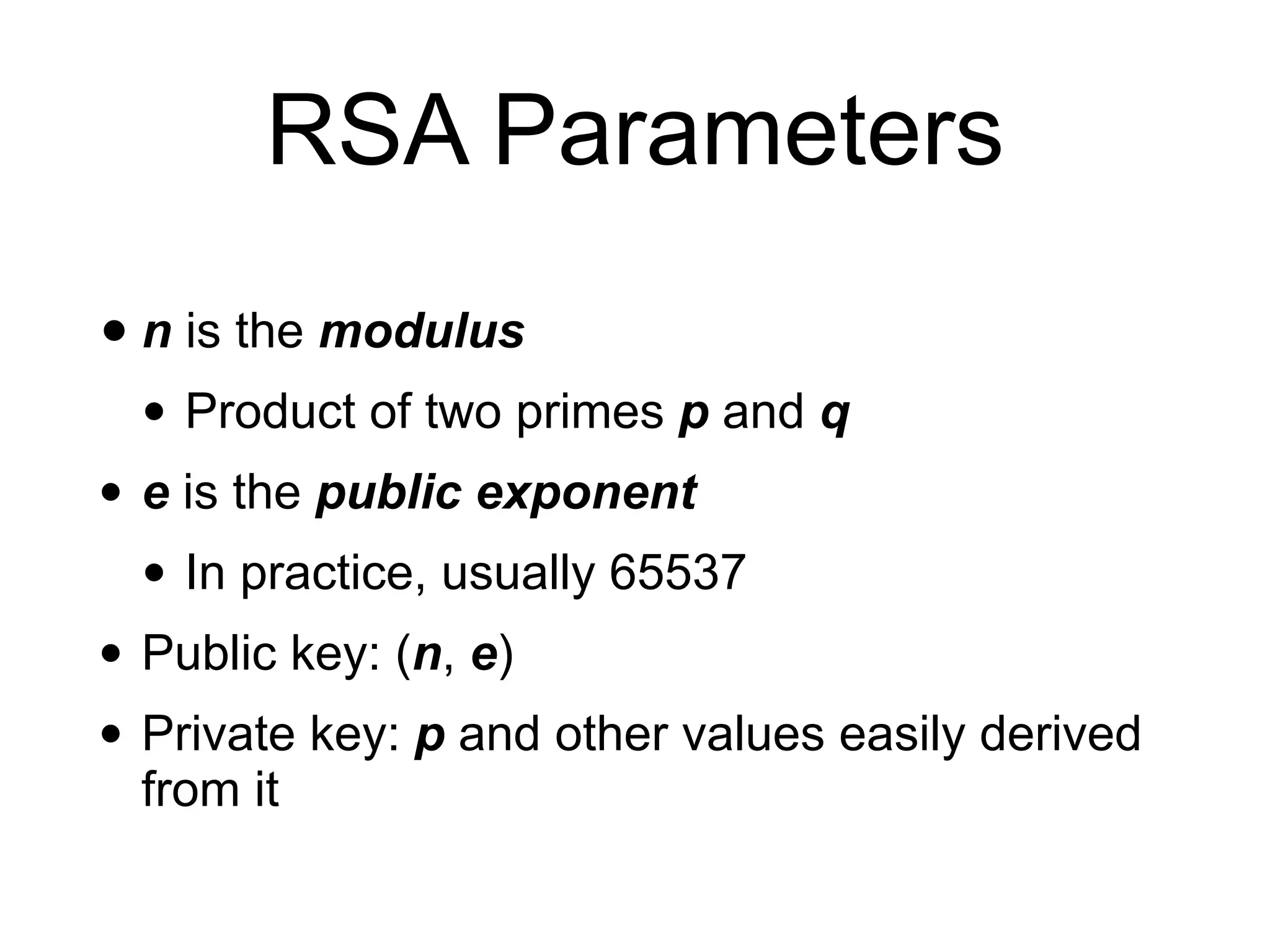
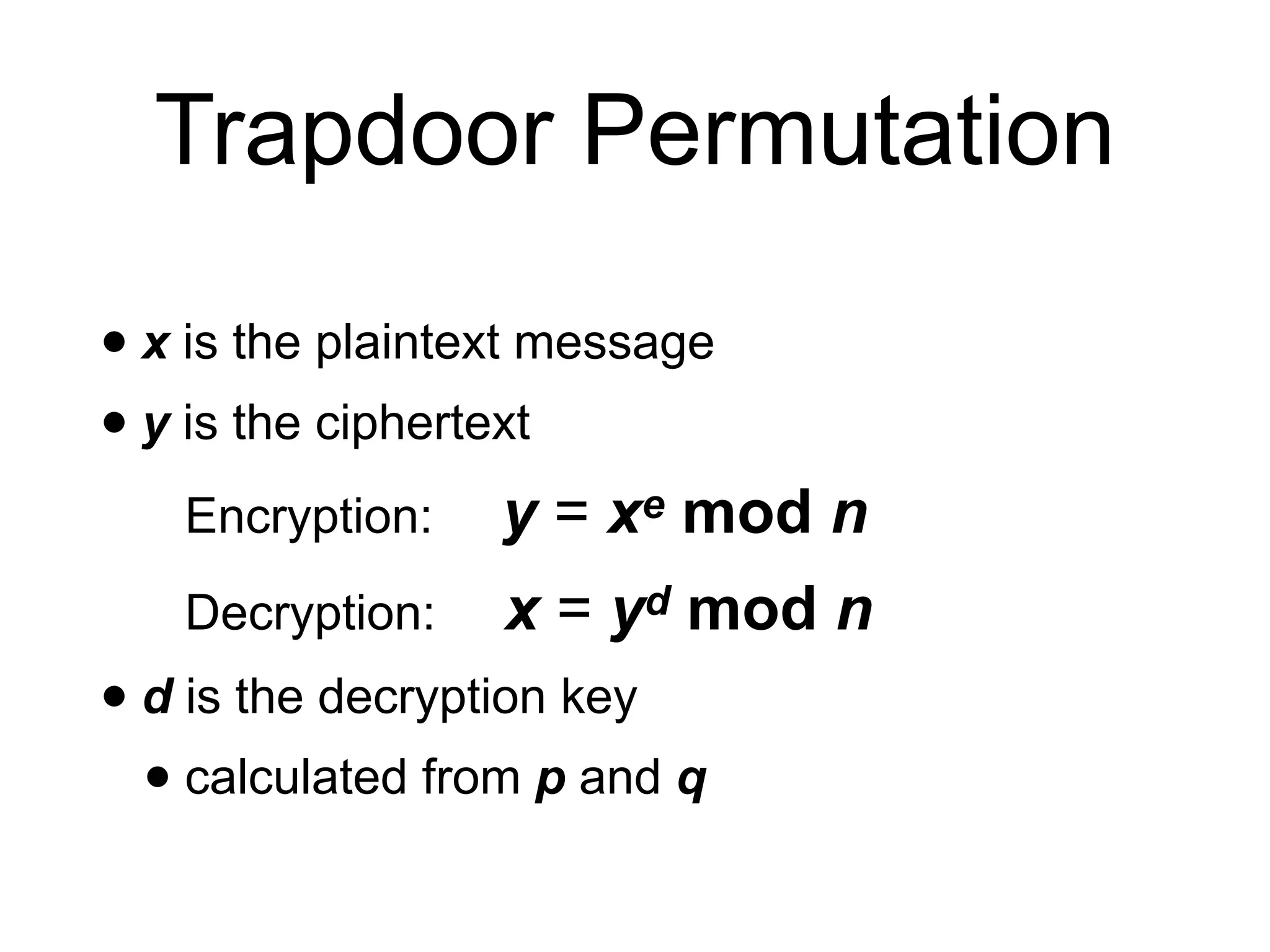
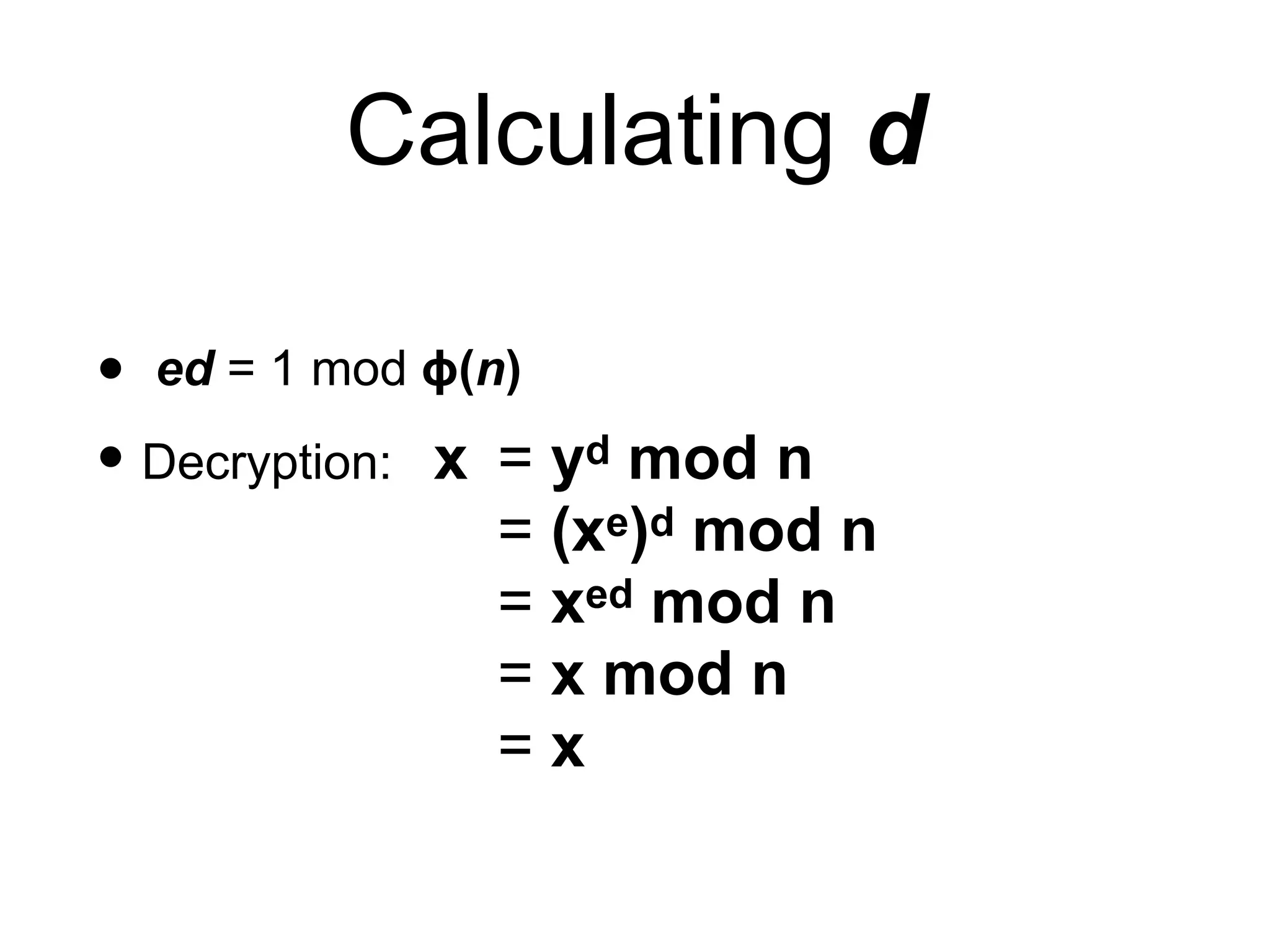
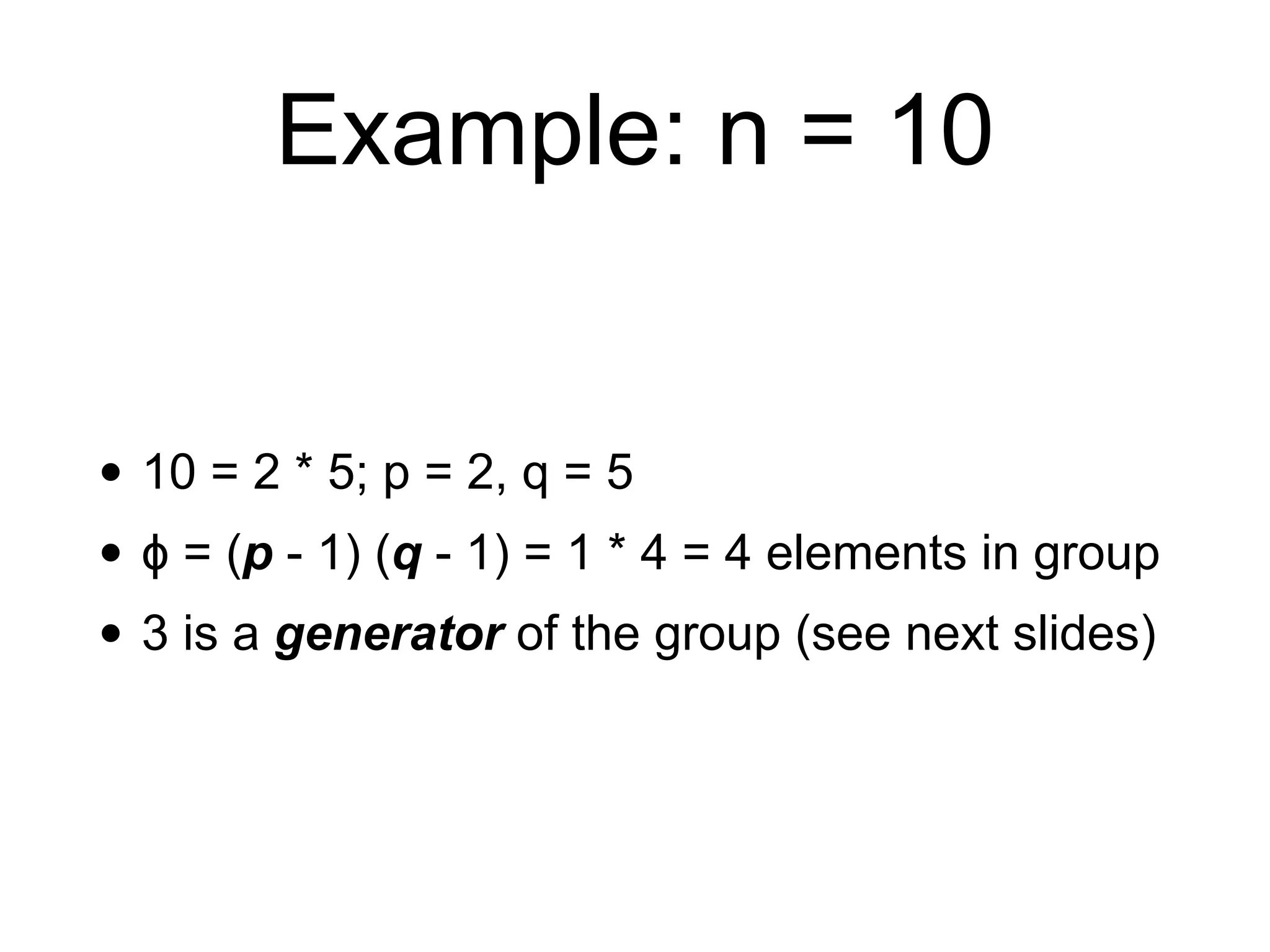
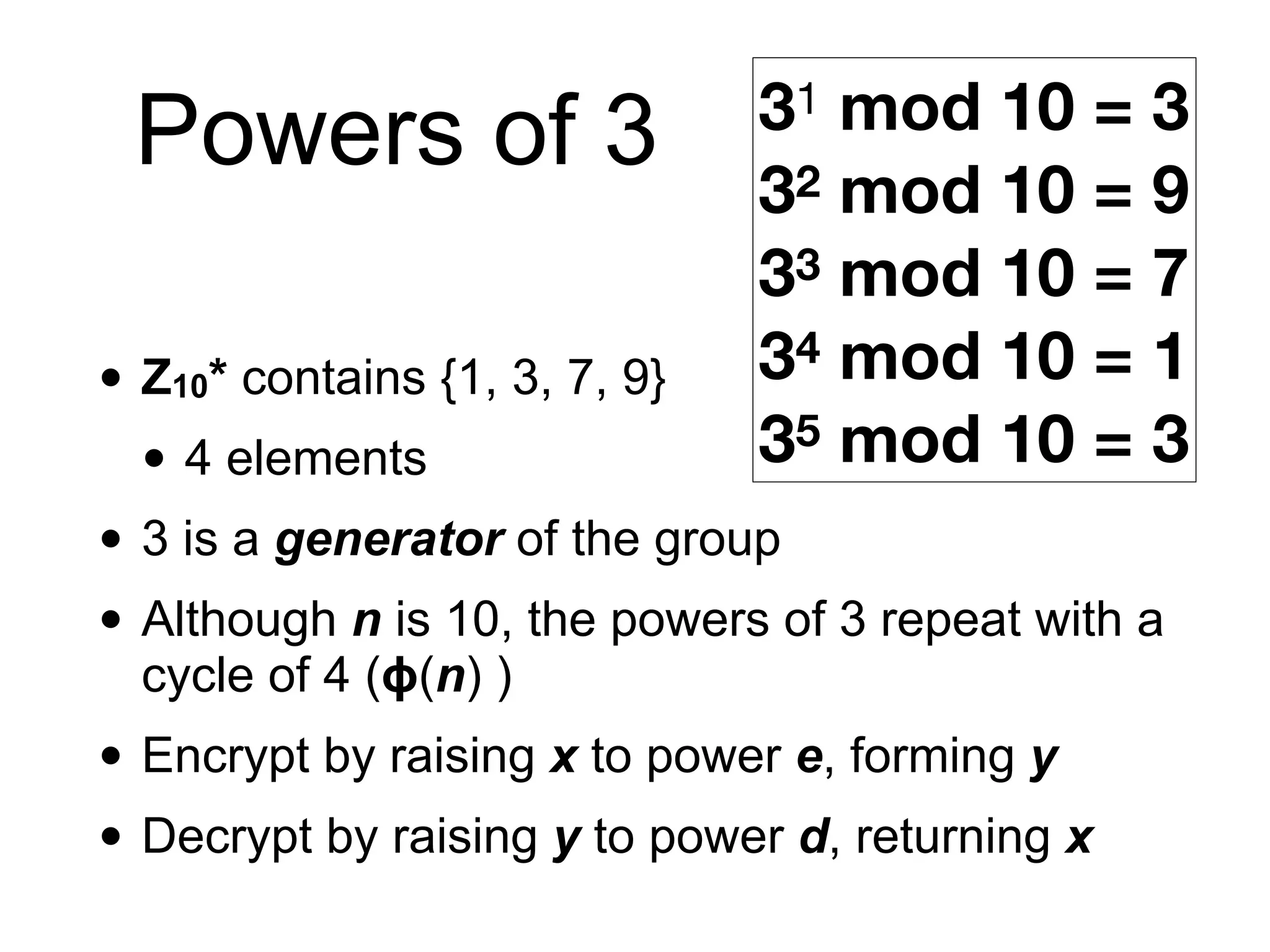
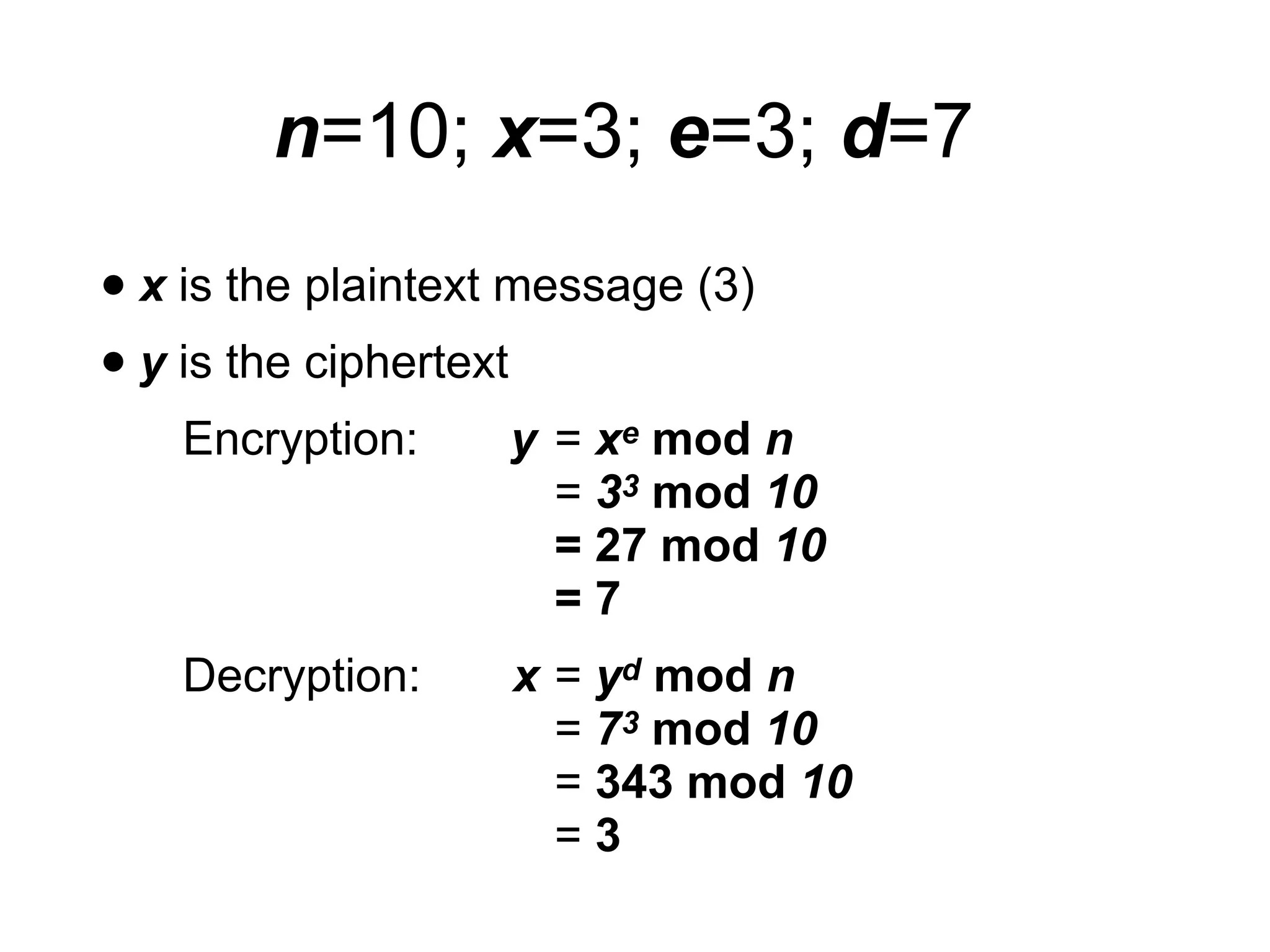
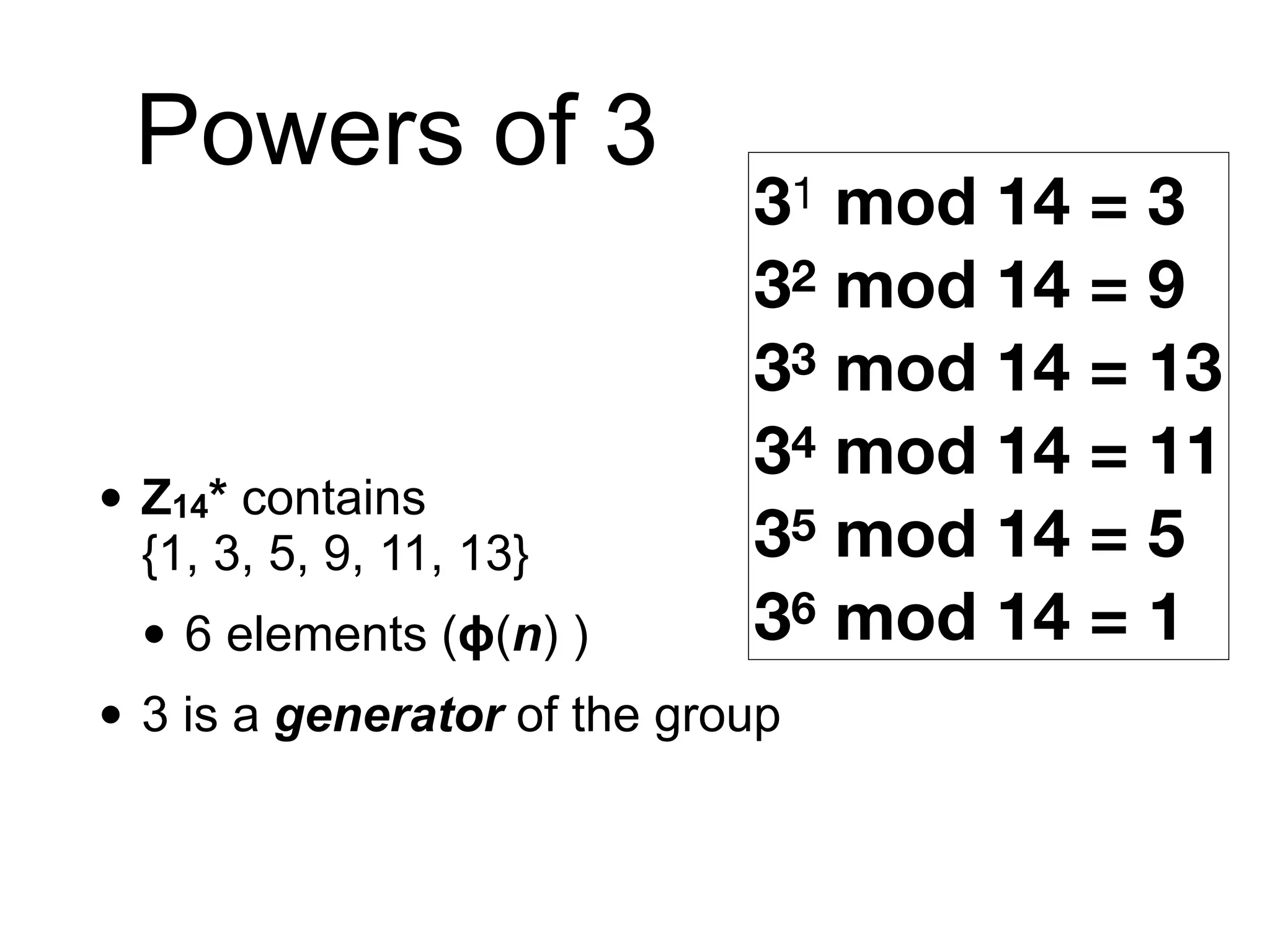
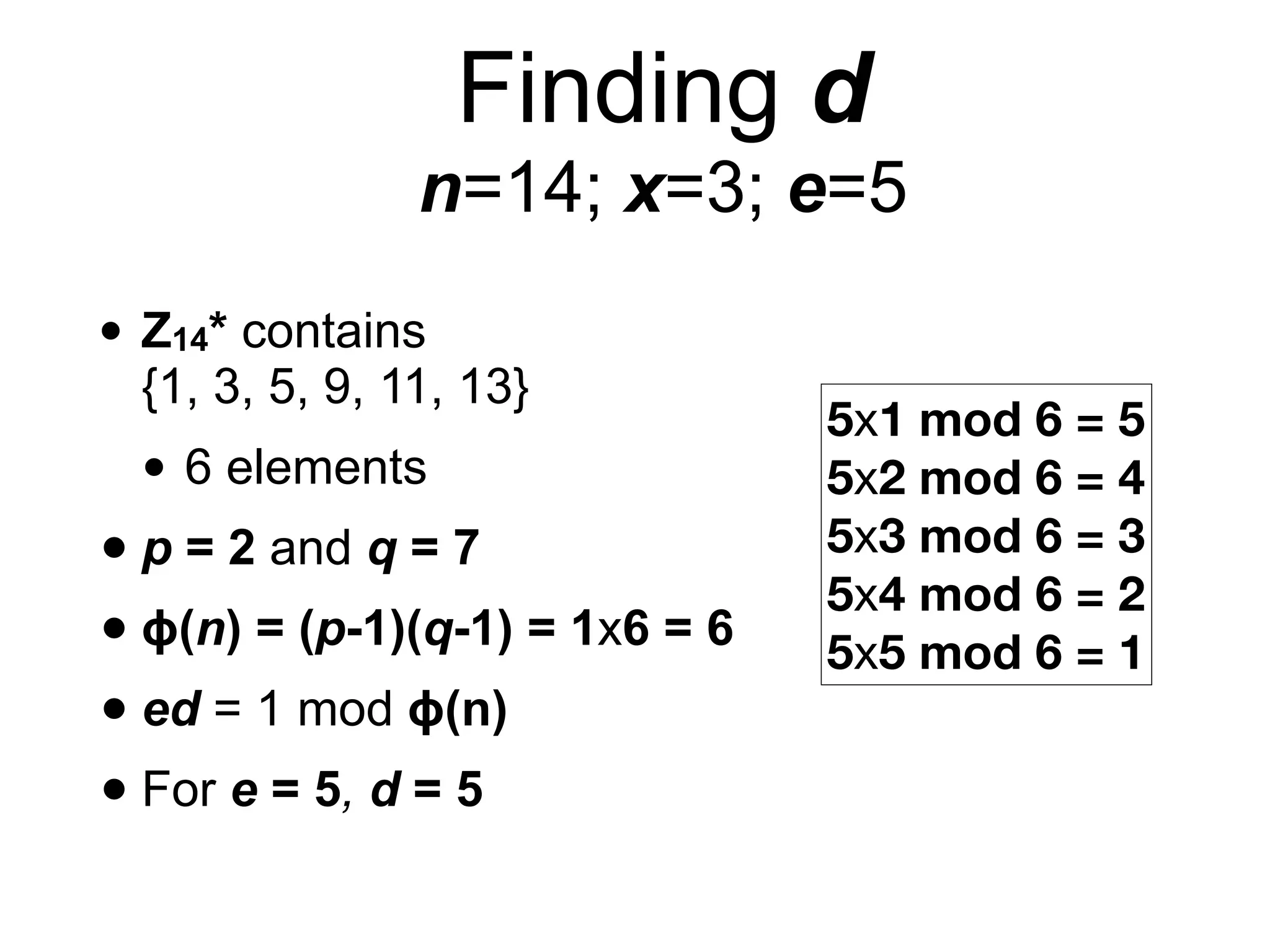
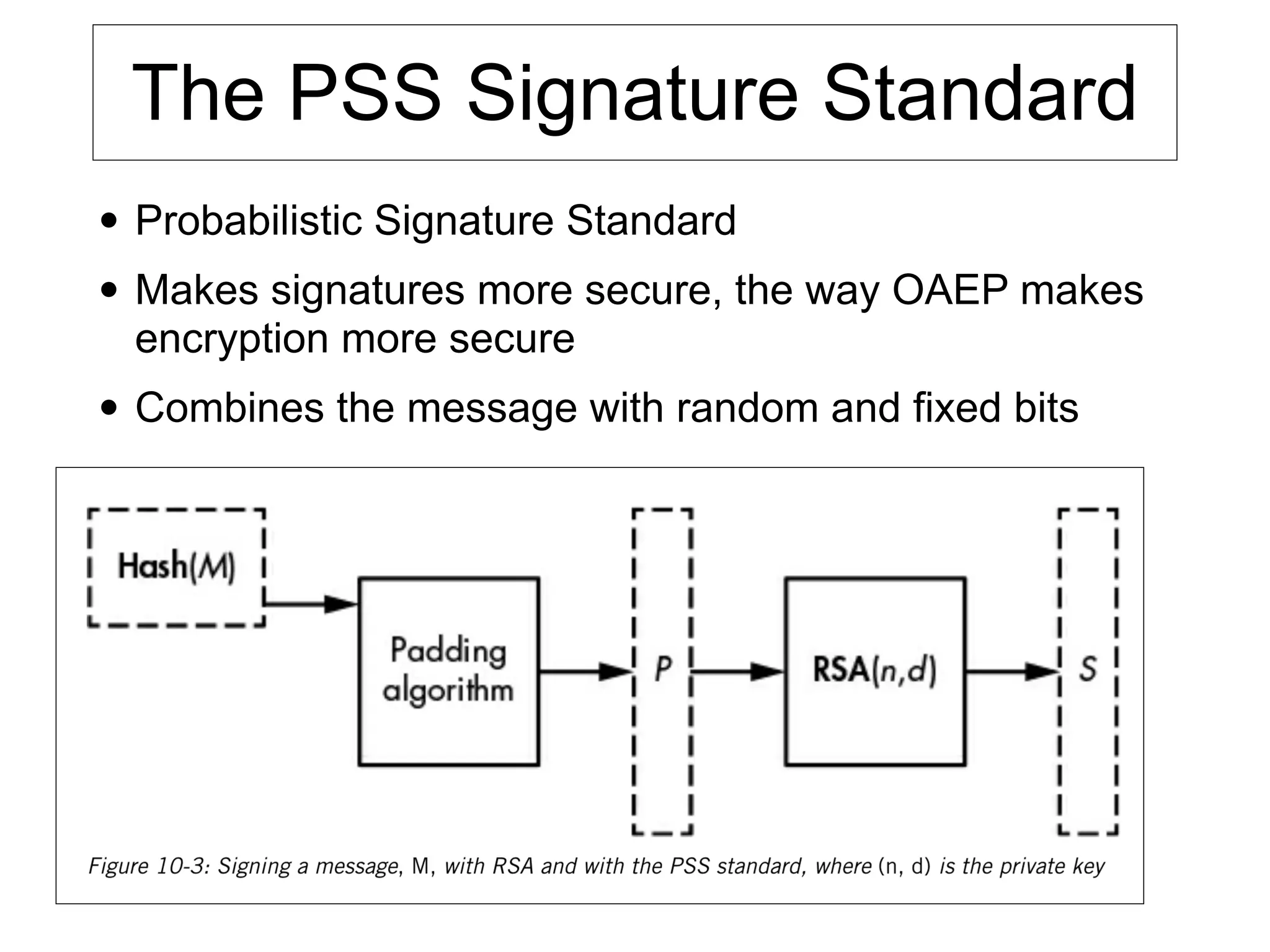
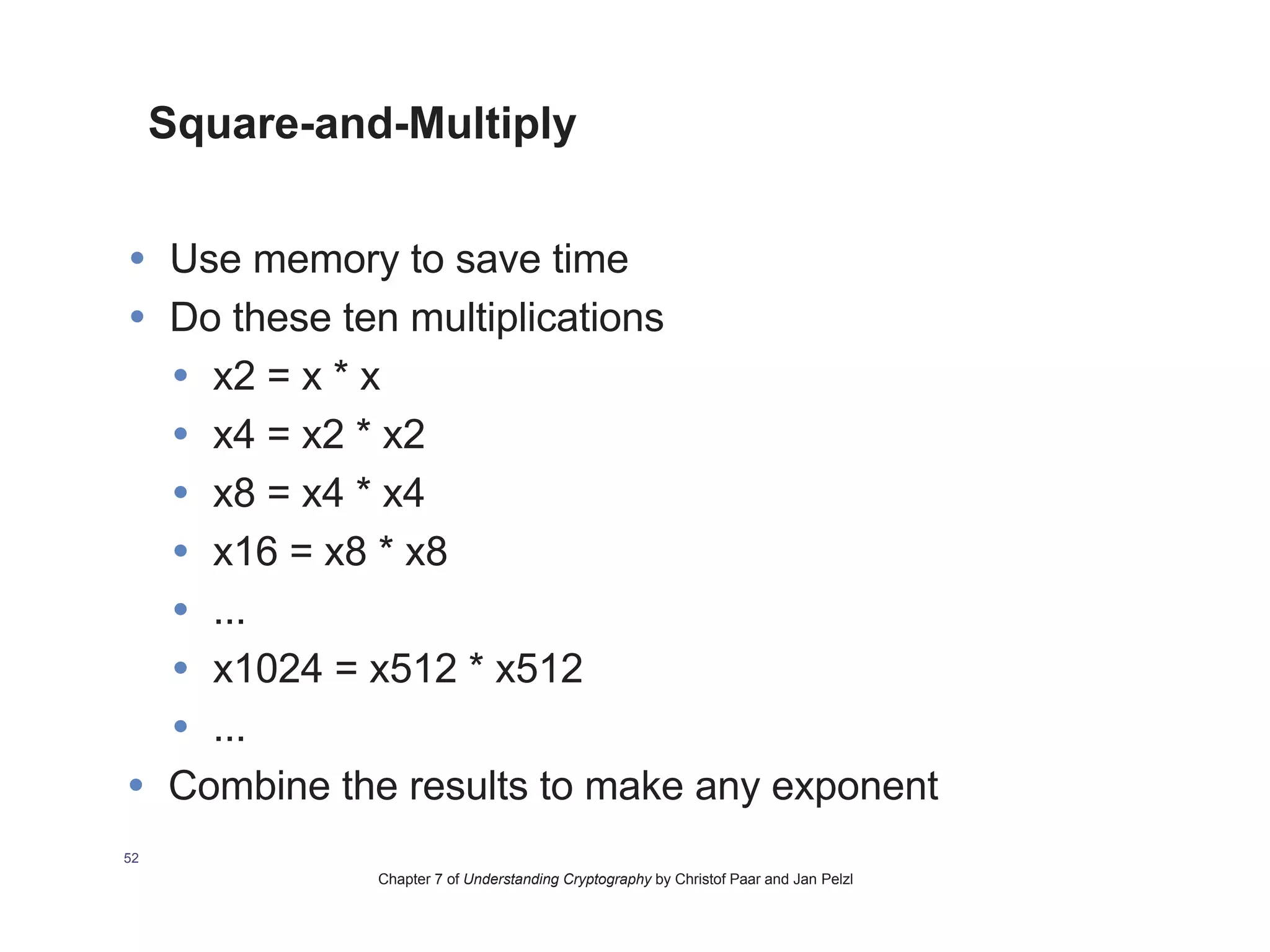
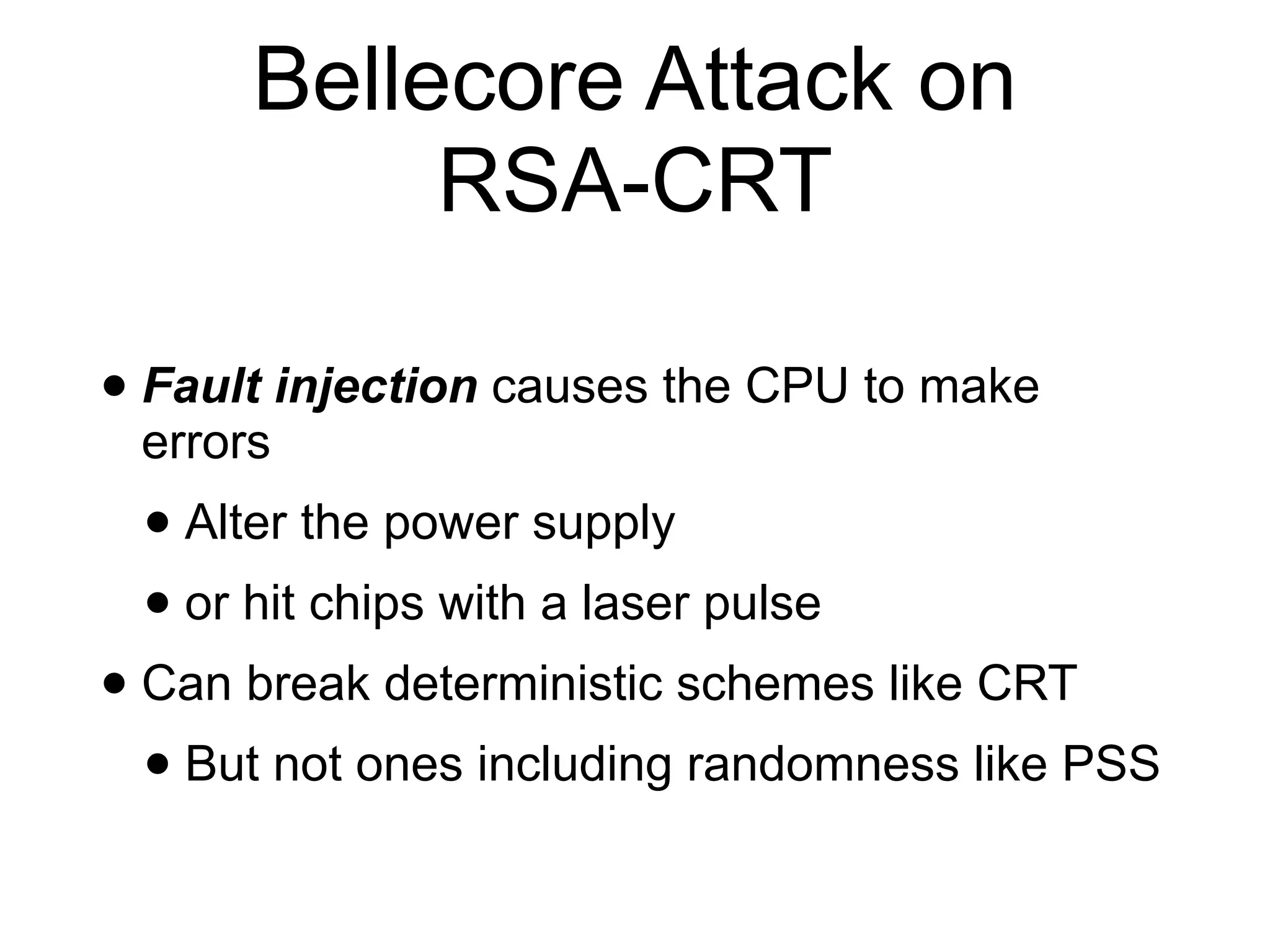
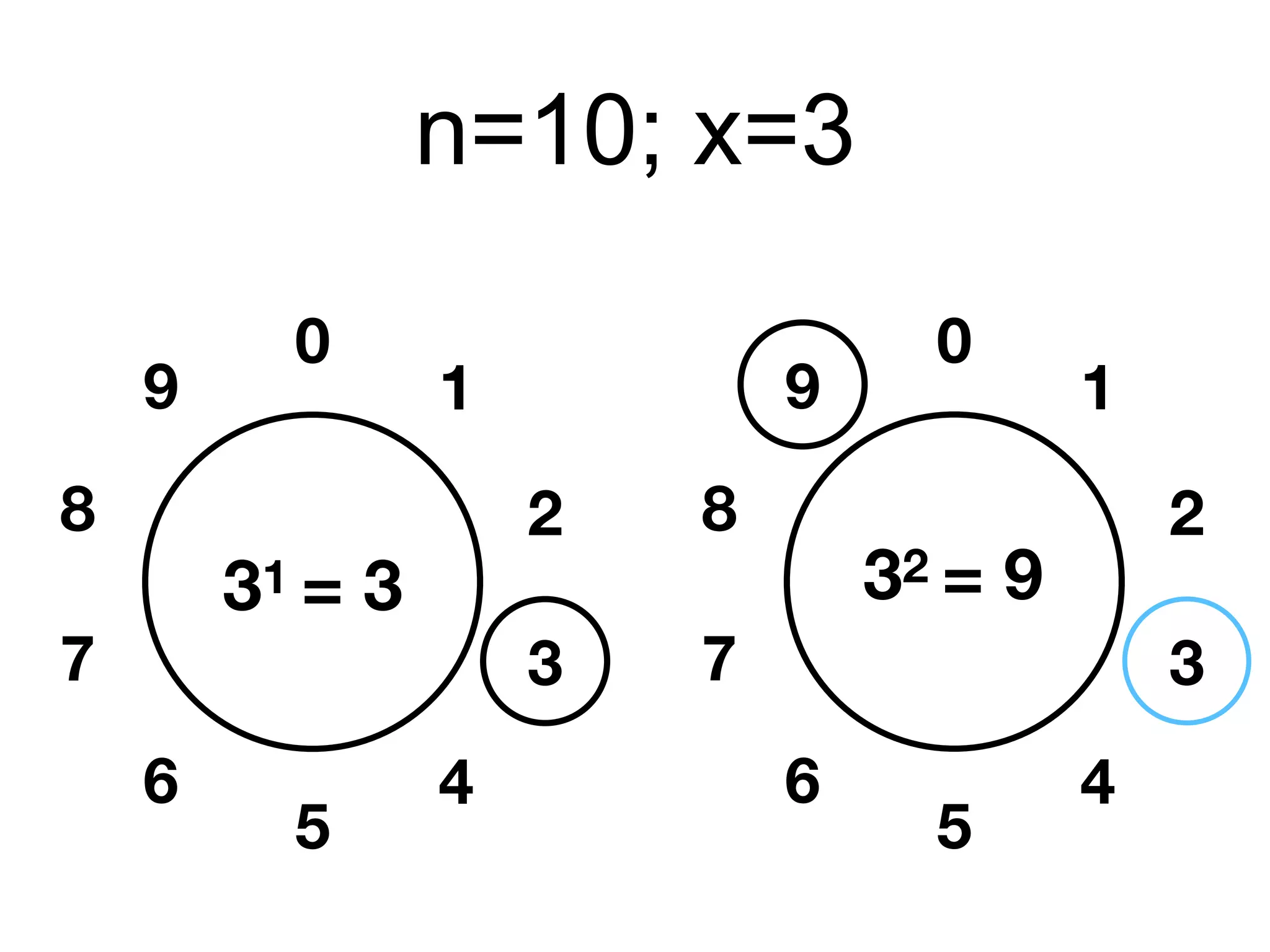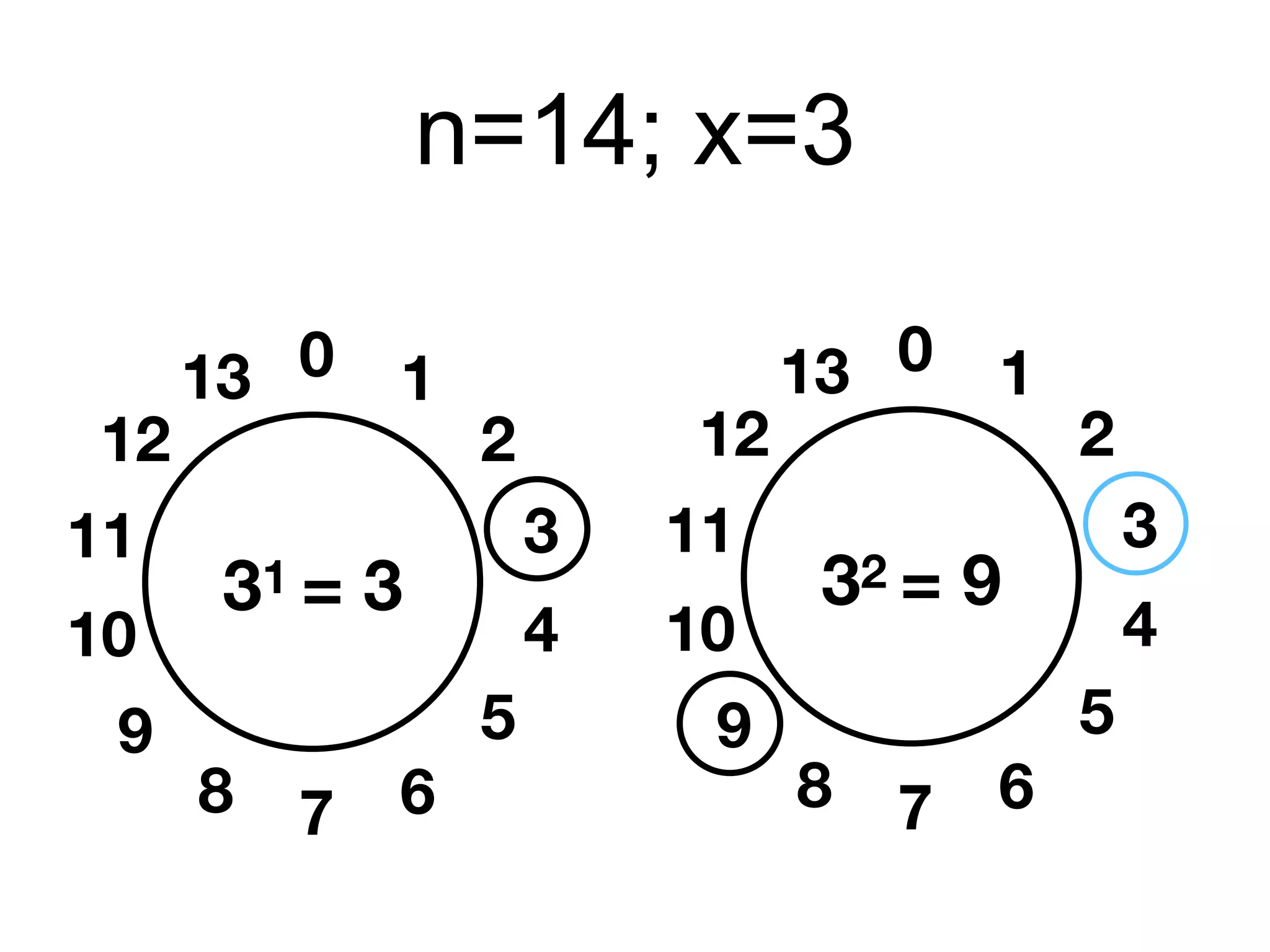This document provides an overview of the RSA cryptosystem. It begins with the mathematical foundations of RSA, including the group ZN* and Euler's totient function. It then covers the RSA trapdoor permutation using modular exponentiation and key generation. The document discusses encrypting and signing with RSA, as well as implementations using libraries and algorithms like square-and-multiply. It concludes with topics like side-channel attacks, optimizations for speed, and ways implementations can fail like the Bellcore attack on RSA-CRT.