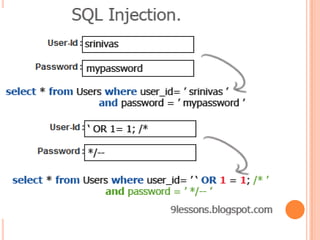
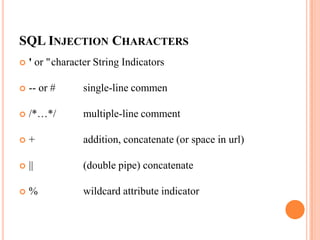
This document discusses SQL injection, which is a security vulnerability that allows attackers to interfere with how a database operates. SQL injection occurs when user input is not sanitized and is used directly in SQL queries, allowing attackers to alter the structure and meaning of queries. The document provides an example of how an attacker could log in without a password by adding SQL code to the username field. It also lists some common SQL injection techniques like using comments, concatenation, and wildcards. Finally, it points to additional online resources for learning more about SQL injection and database security.