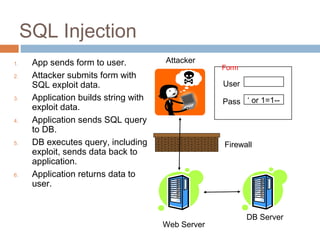
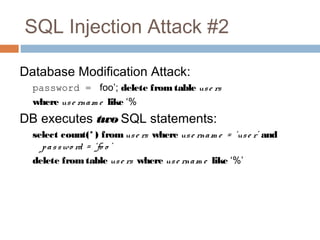
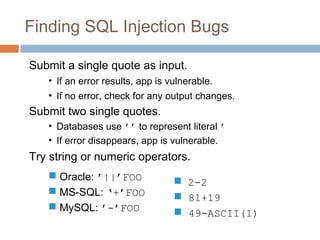
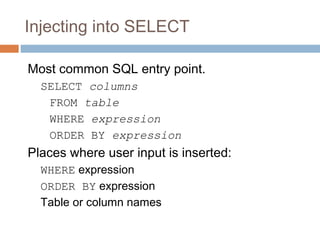
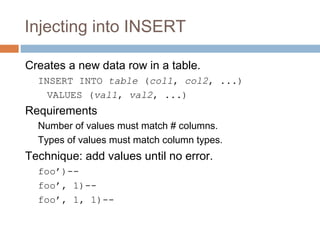
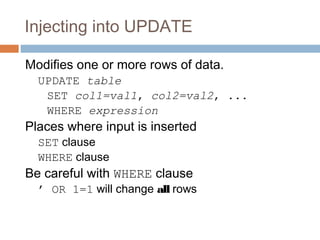
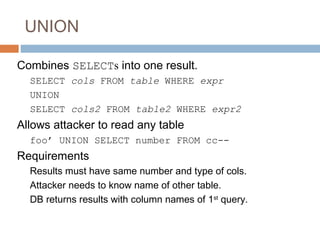
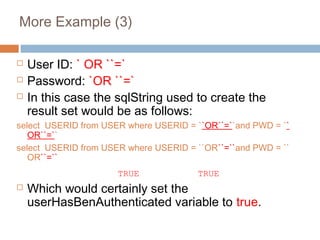
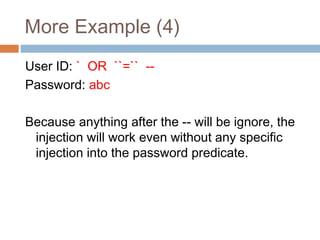
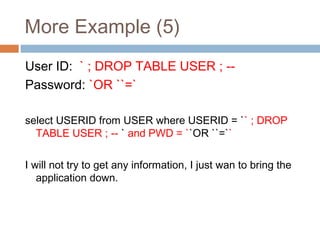
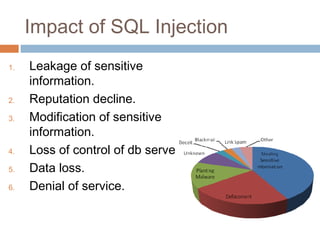
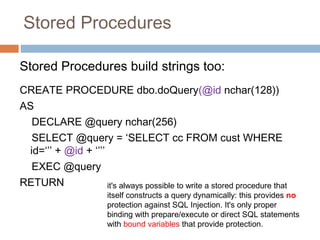
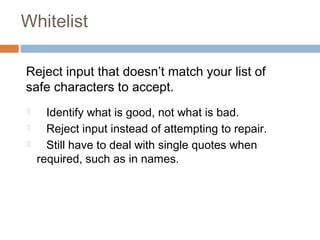
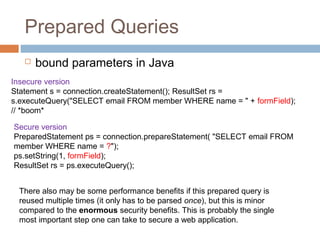
The document discusses SQL injection attacks. It explains that SQL injection works by tricking web applications into treating malicious user input as SQL code rather than data. This allows attackers to view sensitive data from the database or make changes by having the application execute unintended SQL commands. The key to preventing SQL injection is using prepared statements with bound parameters rather than concatenating user input into SQL queries. Other types of injection attacks on different interpreters are also discussed.