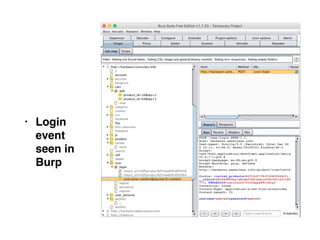
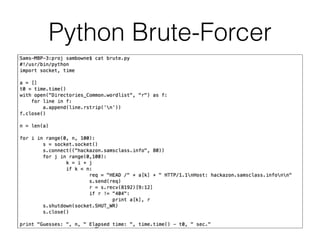
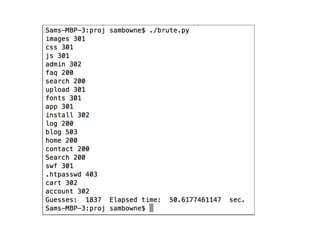
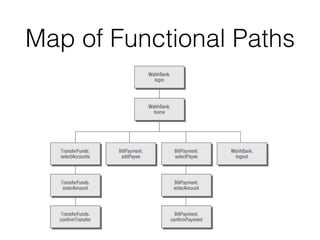
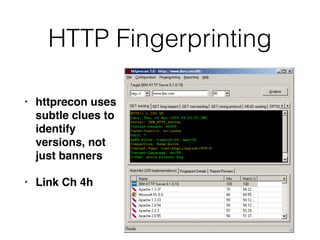
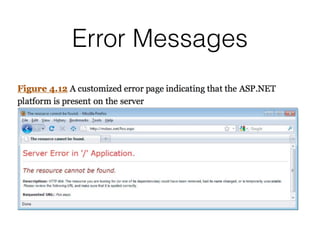
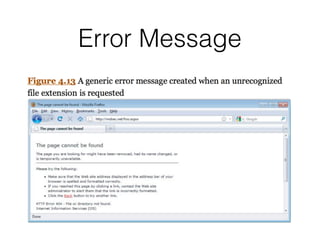
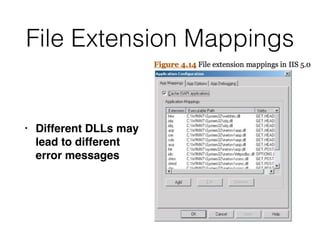
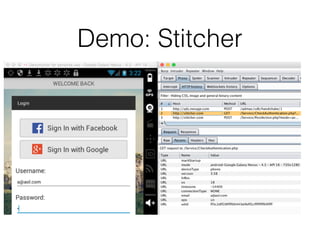
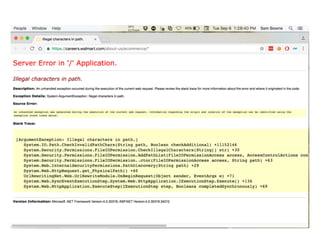
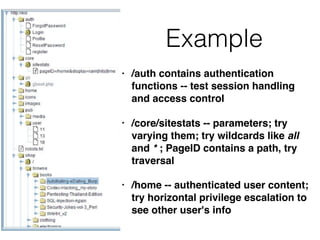
Chapter 4 of CNIT 129s discusses mapping web applications to secure them by enumerating content, functionality, and vulnerabilities using both automated and user-directed spidering techniques. It highlights the limitations of automatic spidering, such as difficulty handling complex navigation and authentication issues, while emphasizing the benefits of user-directed approaches. The chapter also covers various methods for discovering hidden content, analyzing server-side technologies, and identifying entry points for user input, with a focus on understanding application behavior to effectively map the attack surface.