This document discusses server-side template injection (SSTI), including an introduction to template engines, examples of commonly used template engines like Twig and Jinja2, how SSTI works by allowing user input to be embedded in templates in an unsafe manner, ways to detect and identify SSTI vulnerabilities, exploiting SSTI to read files or execute code, automated tools like Tplmap that can assist in SSTI exploitation, mitigations like input sanitization, and references and case studies.



![Template Injection -
■ User input is embedded in unsafe manner.
■ Confused by XSS.
Marketing application with email greeting
$output = $twig->render(“Dear, $_GET[‘name’]”, array("first_name" => $user.first_name) );
Name =Tester Name = {{7*7}}
> Dear,Tester > Dear, 49
Name = {{self}}
> Dear, Object of class __TwigTemplate_7ae62e582f8a35e5ea6cc639800ecf15b96c0d6f78db3538221c1145580ca4a5 could not
be converted to string](https://image.slidesharecdn.com/sstippt-190224160034/85/Server-side-template-injection-Slides-6-320.jpg)
![■ Detect –
Plain Text Context
- Can be confused with XSS
- {var} {{var}} ${var} <%var%> [% var %]
- Results in execution or error message.
- a{{var}}b
> Expect : ab or Error message
- a{{7*7}}b
> Expect : a49b
smarty=Hello {user.name}
> Hello user1](https://image.slidesharecdn.com/sstippt-190224160034/85/Server-side-template-injection-Slides-7-320.jpg)

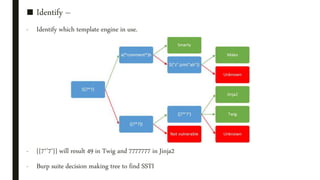








![■ Input Sanitization –
- PHP
- JAVA
- ASP.NET
str_replace( array( ''', '"', ',' , ';', '<', '>','{','}', ), '', $name);
preg_replace('/[^a-zA-Z0-9_ -]/s','',$value);
Text = text.replaceAll ("[^a-zA-Z0-9]", "");
Regex.Replace(Your String, @"[^0-9a-zA-Z:,]+", "")](https://image.slidesharecdn.com/sstippt-190224160034/85/Server-side-template-injection-Slides-19-320.jpg)