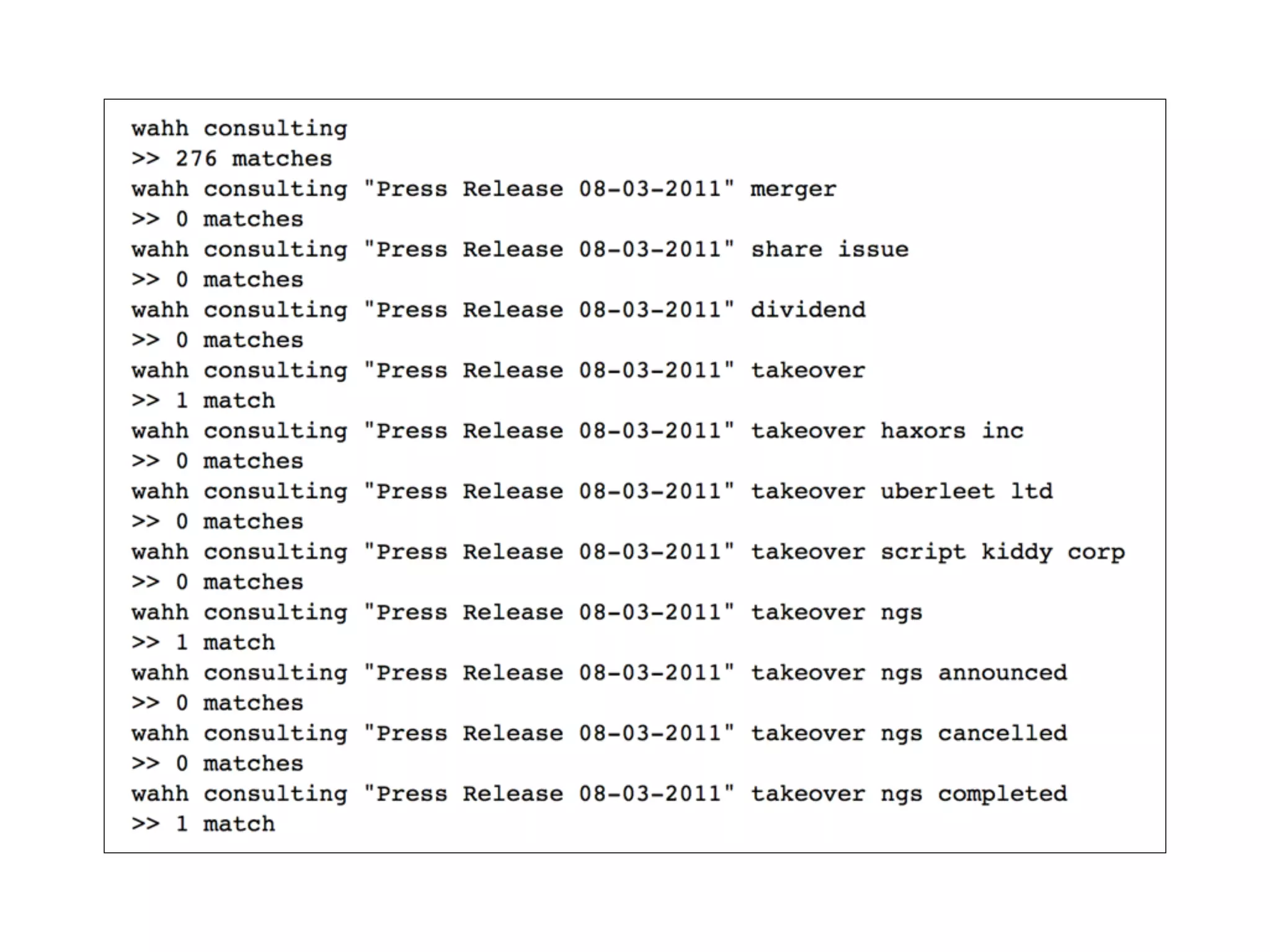
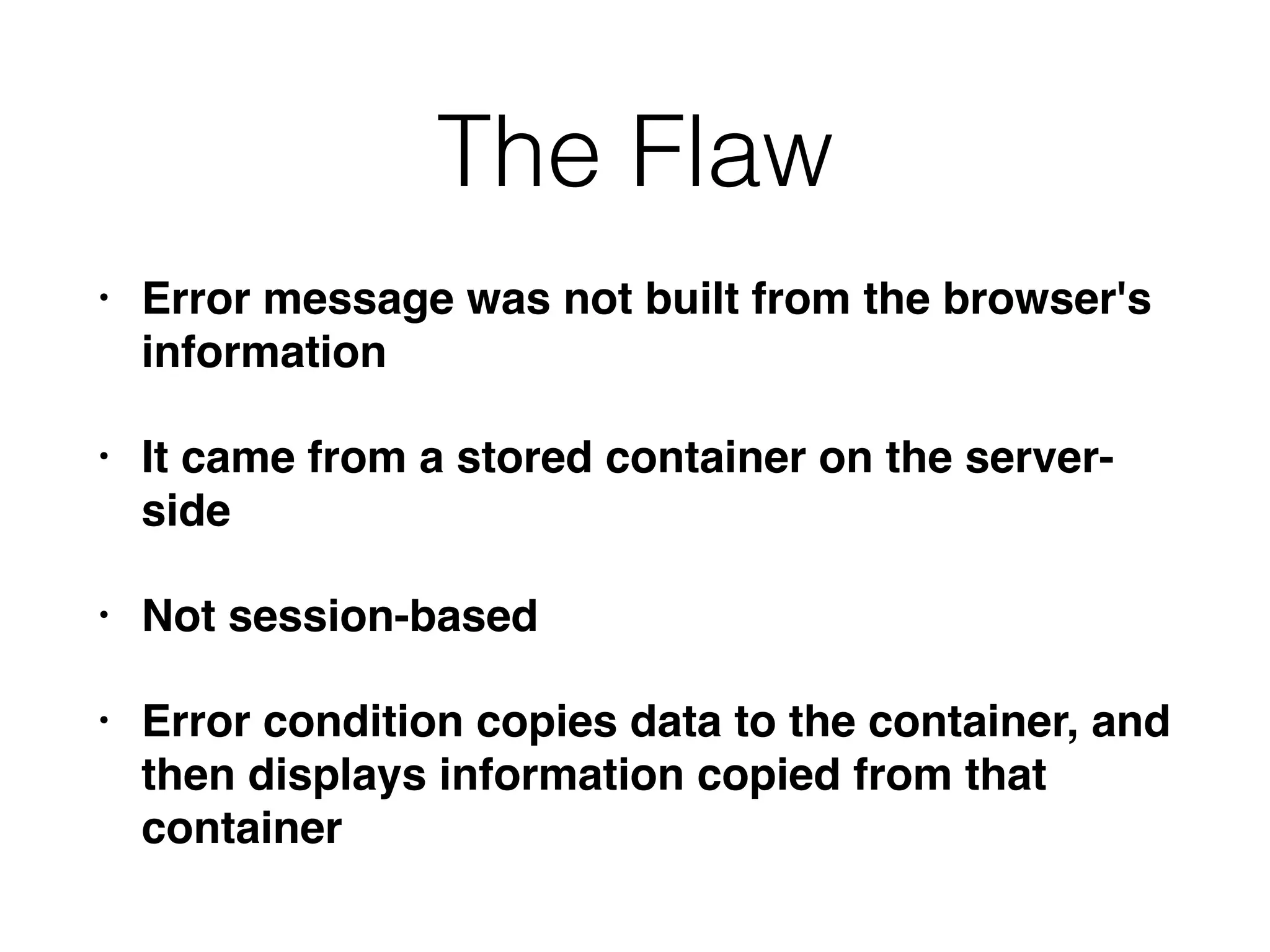
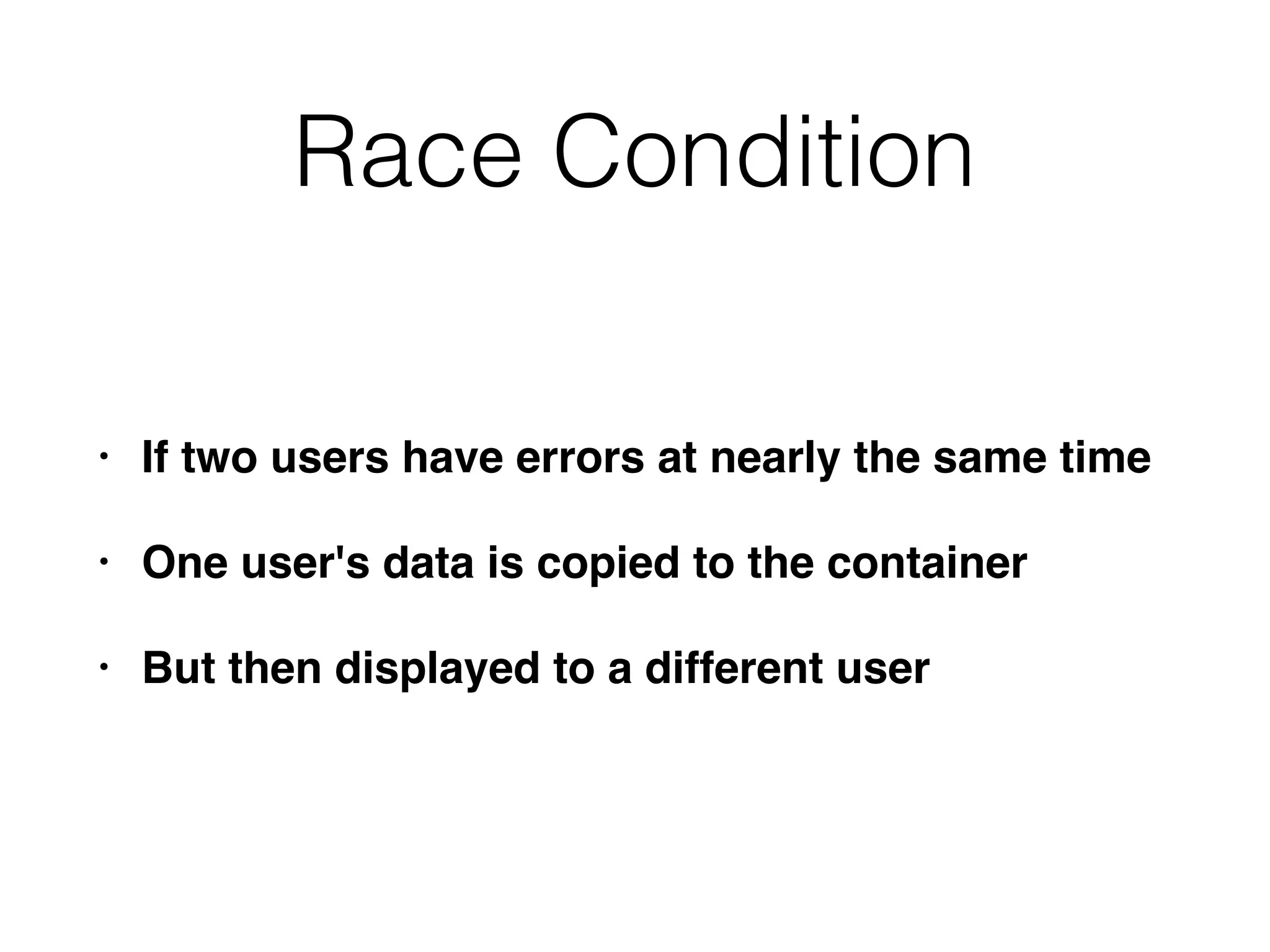
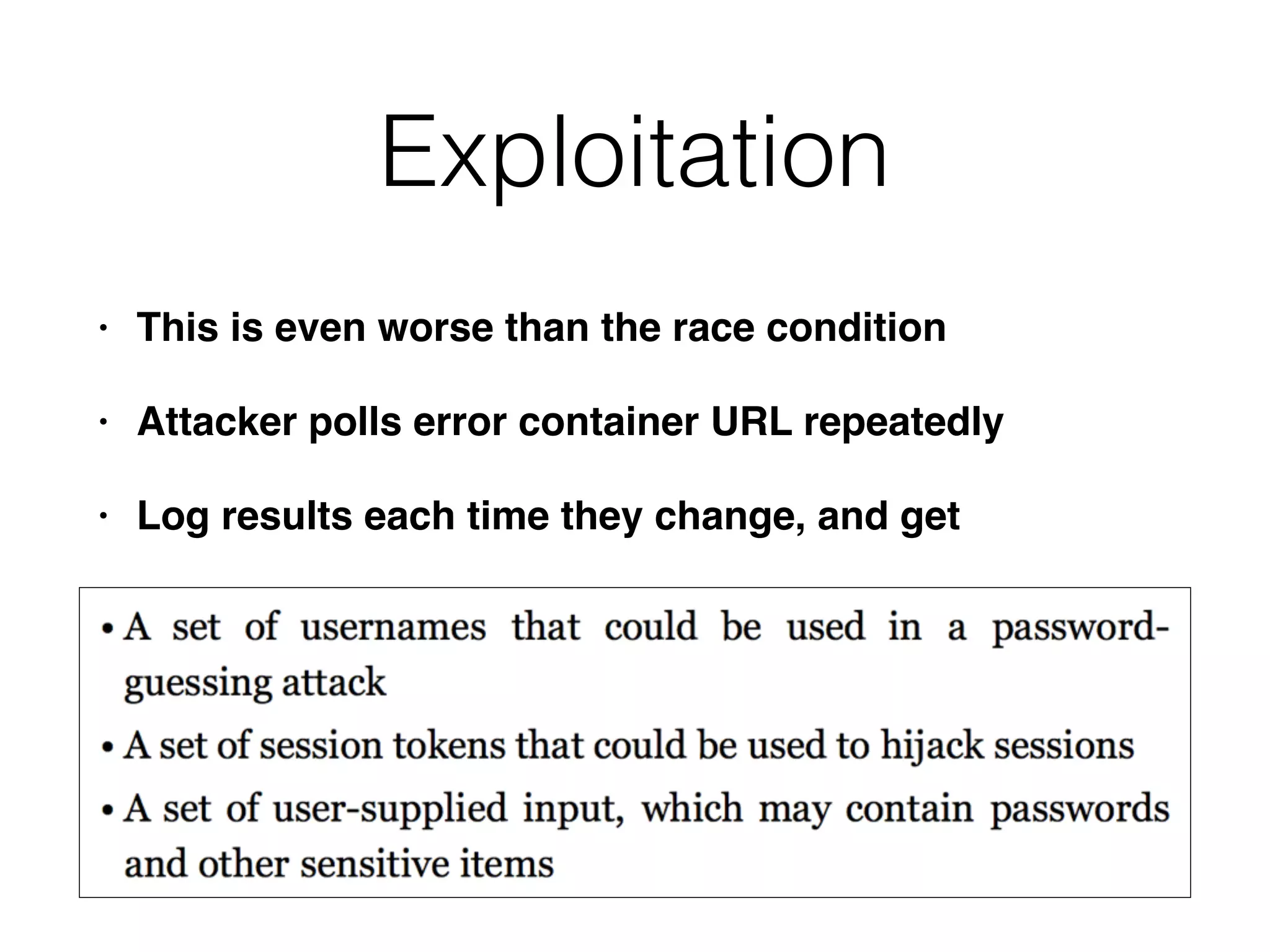
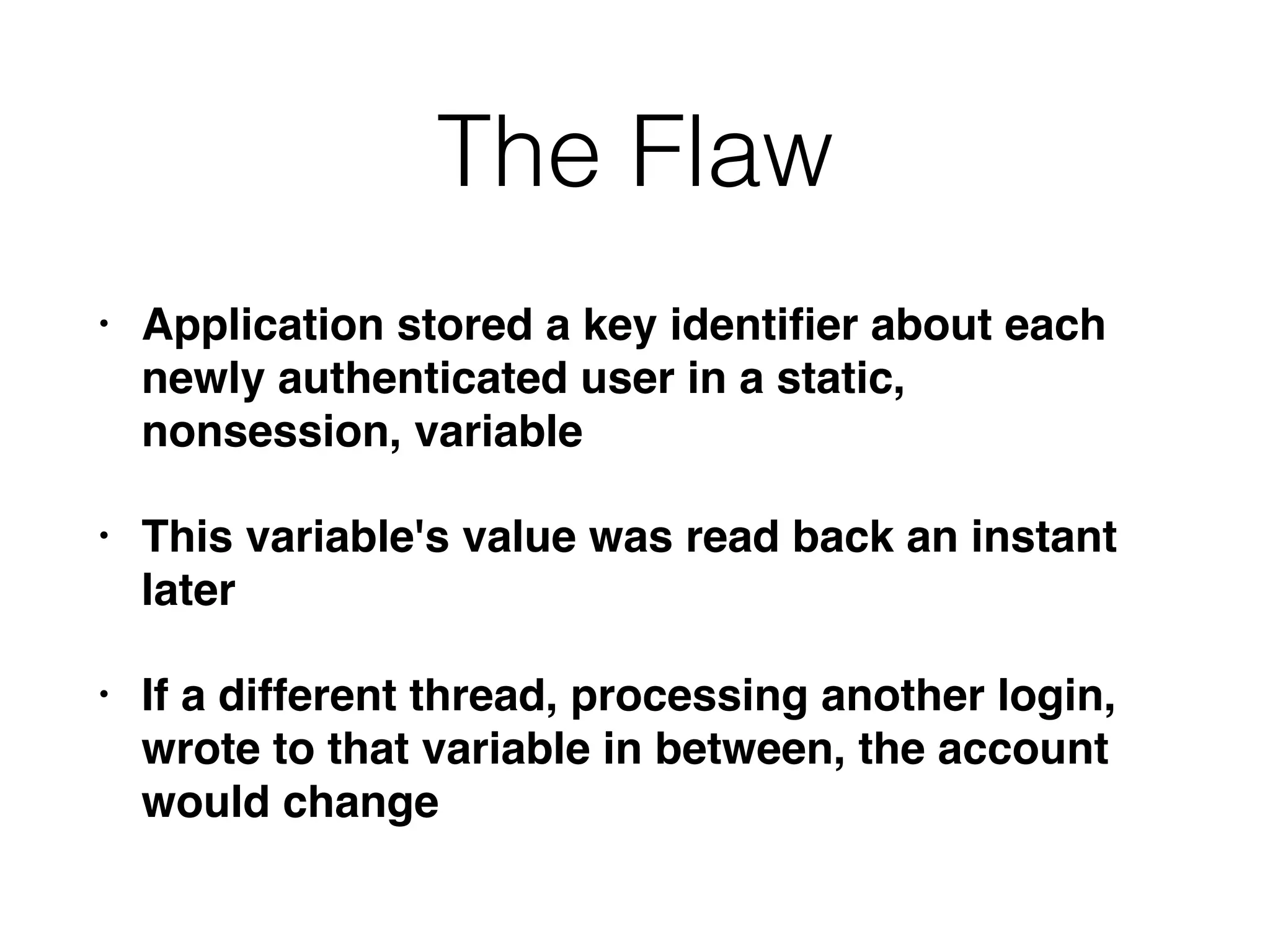
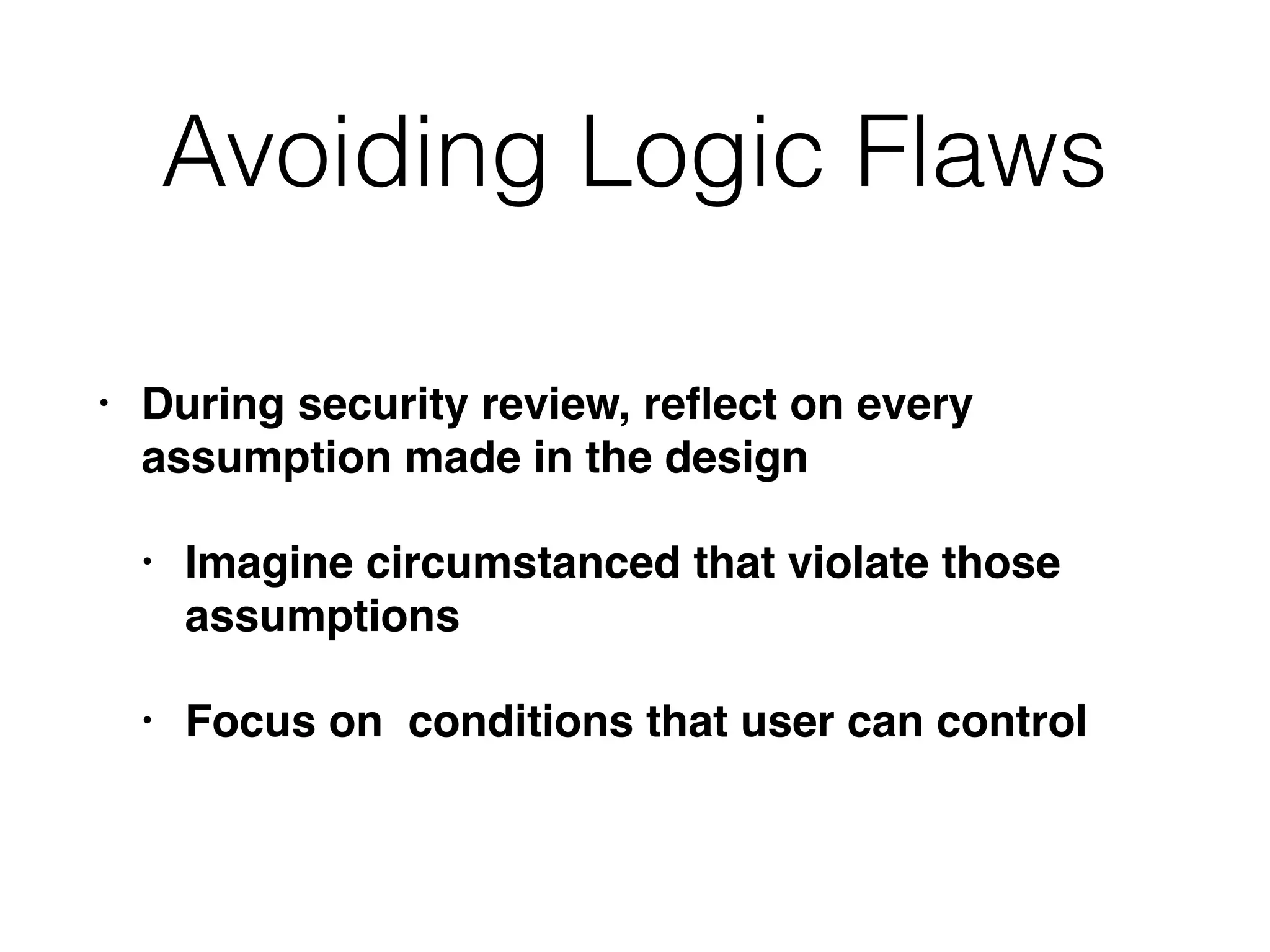
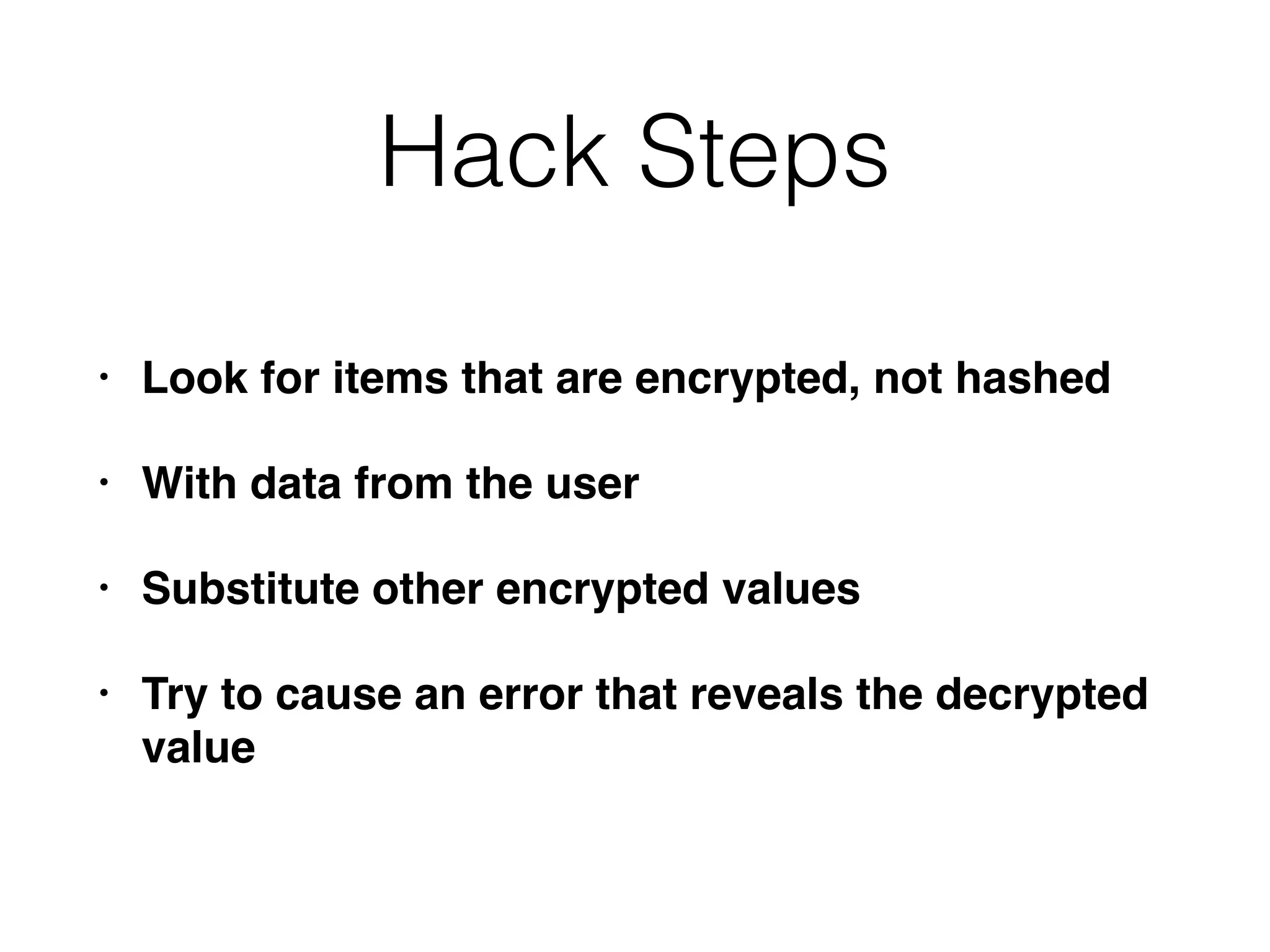
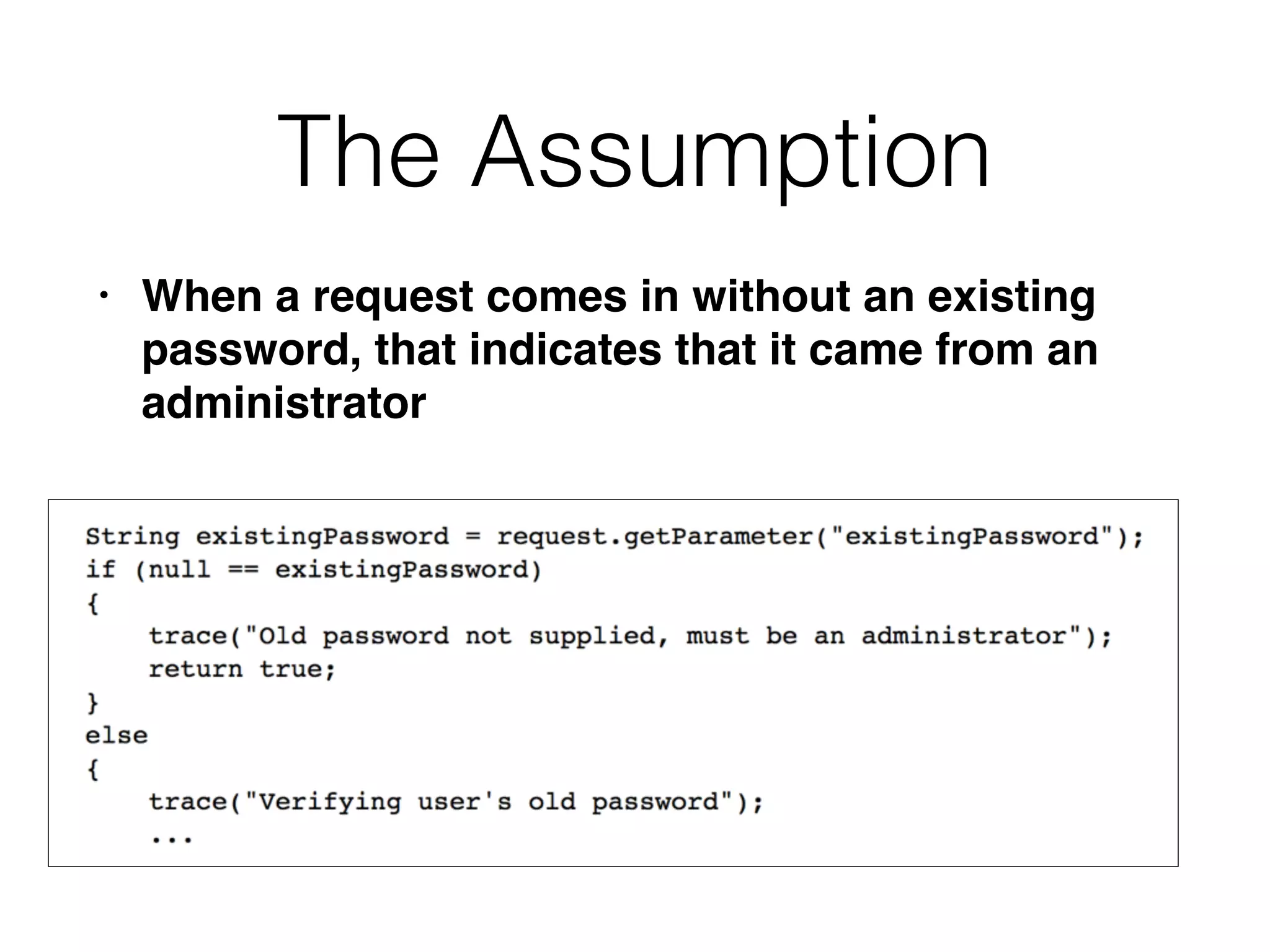
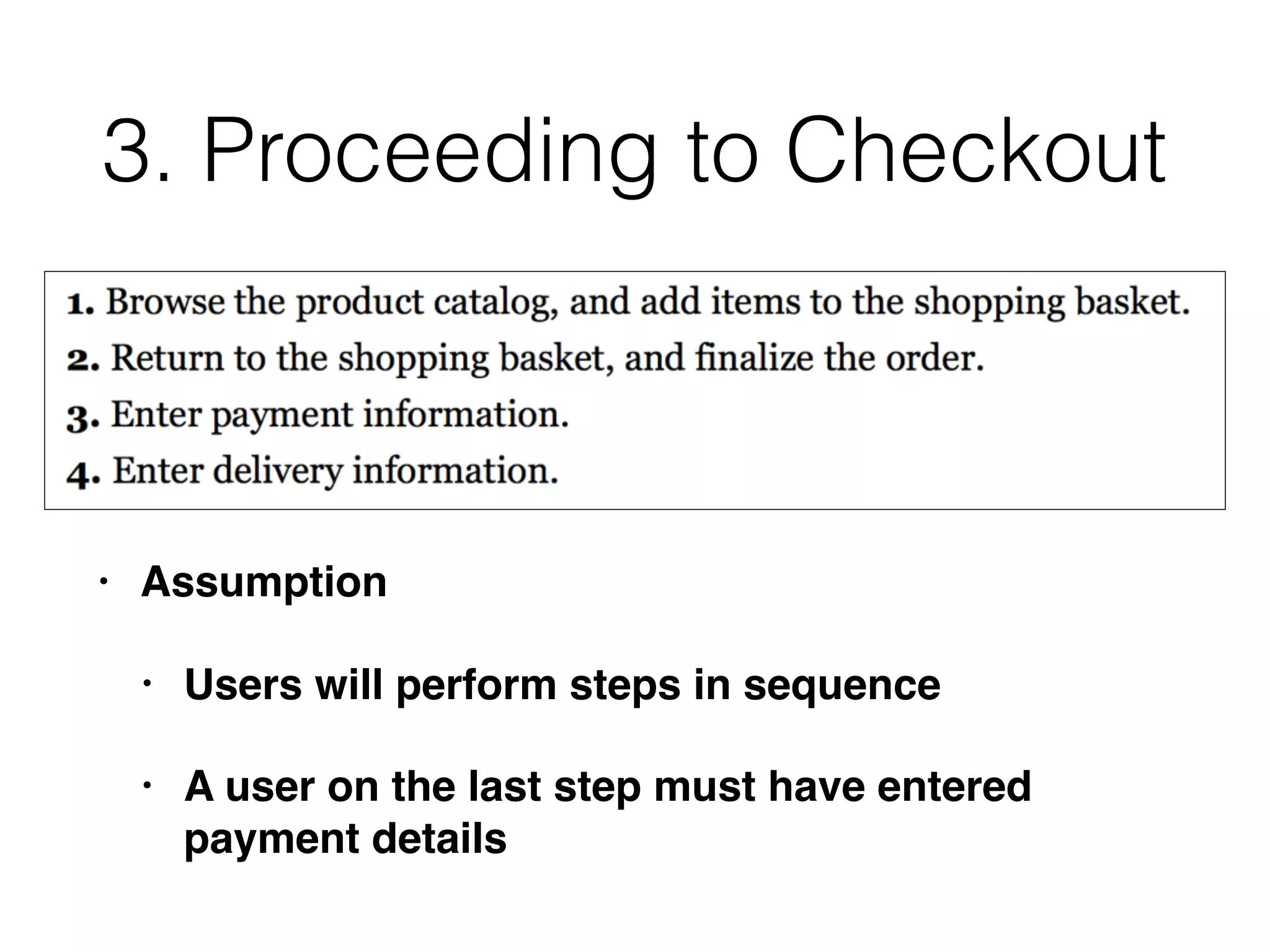
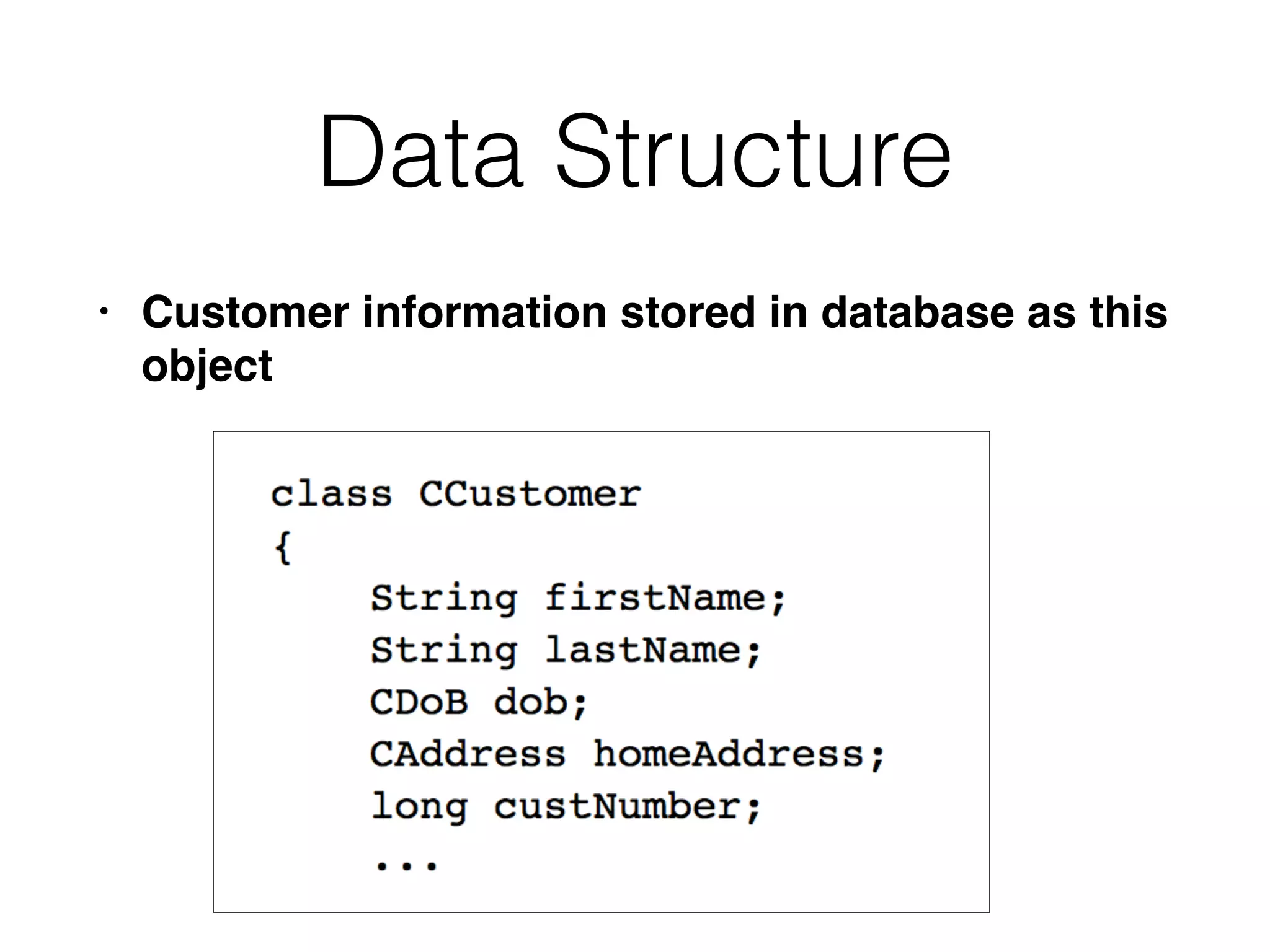
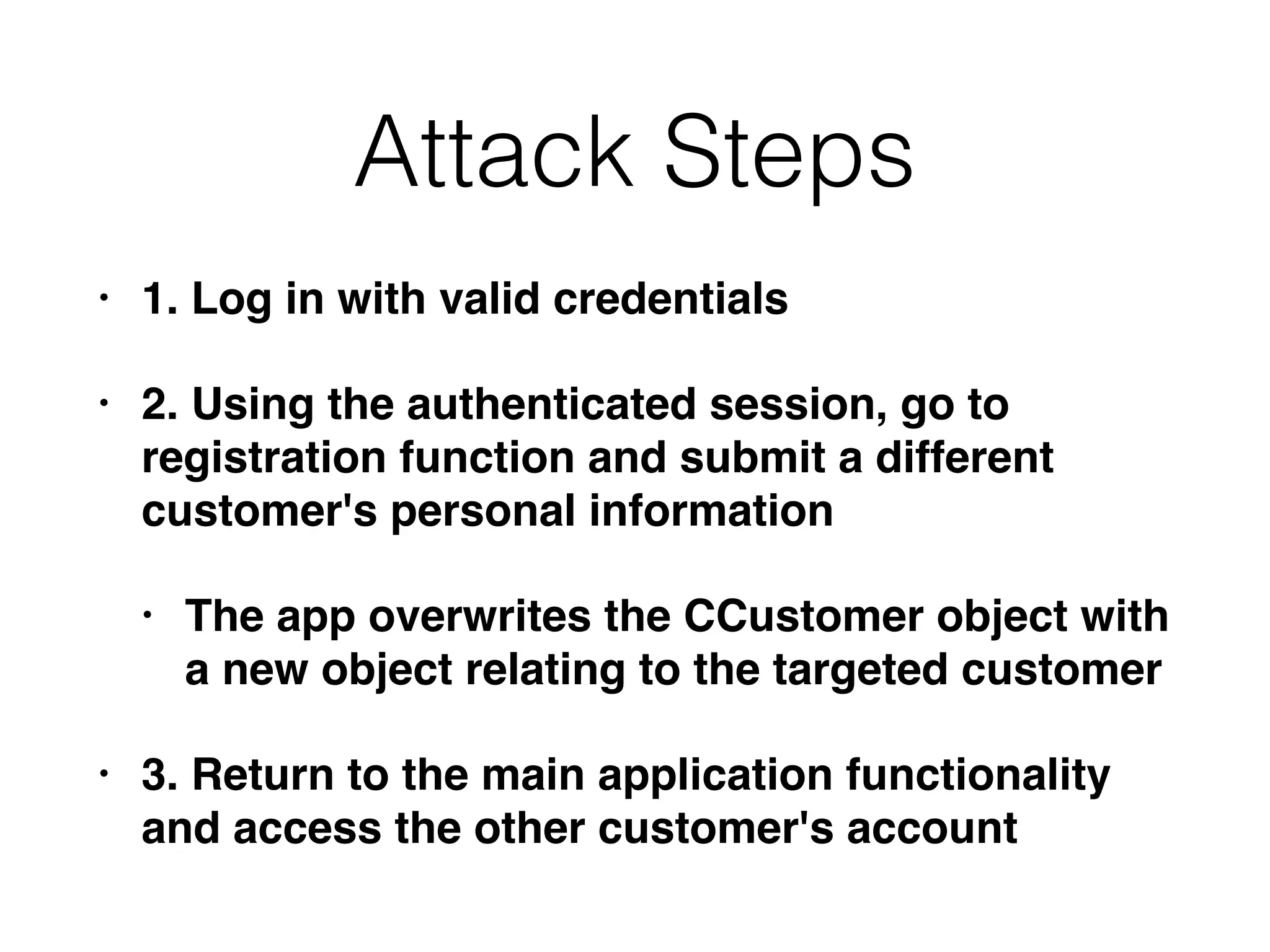
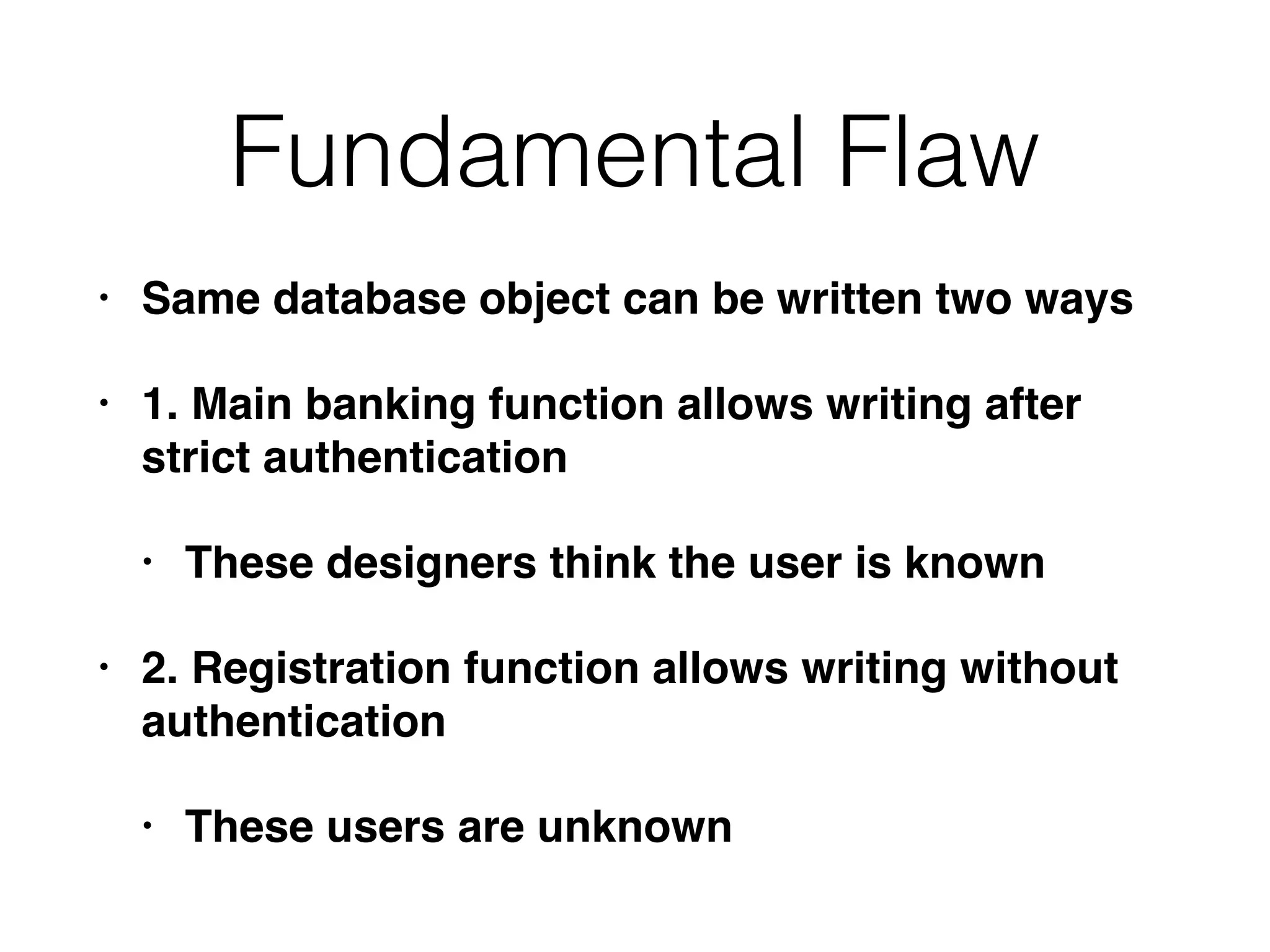
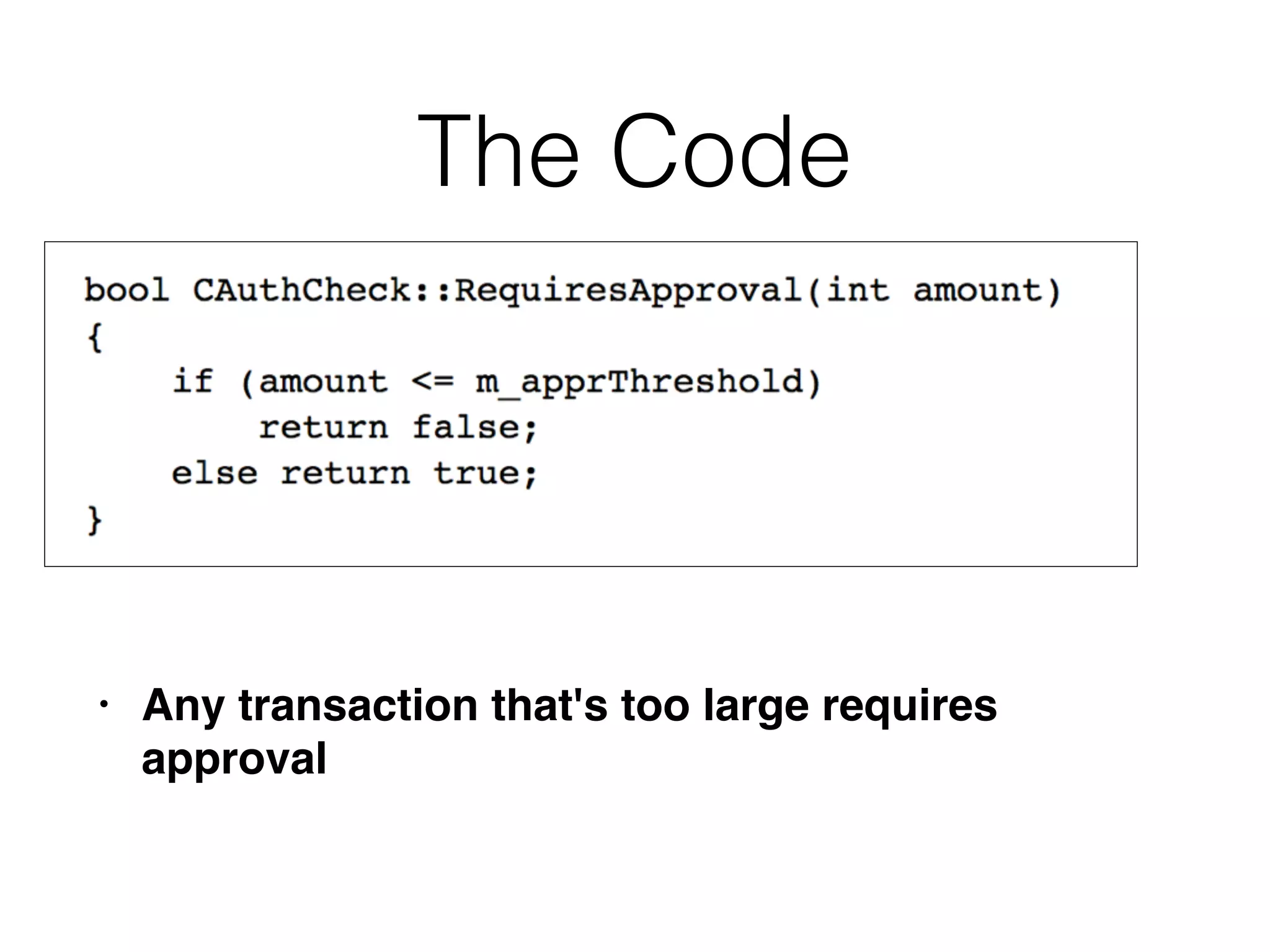
The document outlines various attacks on web application logic flaws that developers commonly overlook, such as relying on user input assumptions, inadequate validation, and flawed session management. It details multiple attack methods, including cookie manipulation, unauthorized password changes, and bypassing payment controls, illustrating how attackers can exploit seemingly secure systems. The document emphasizes the importance of thoroughly documenting design assumptions and considering unexpected user behavior during security reviews to mitigate these vulnerabilities.




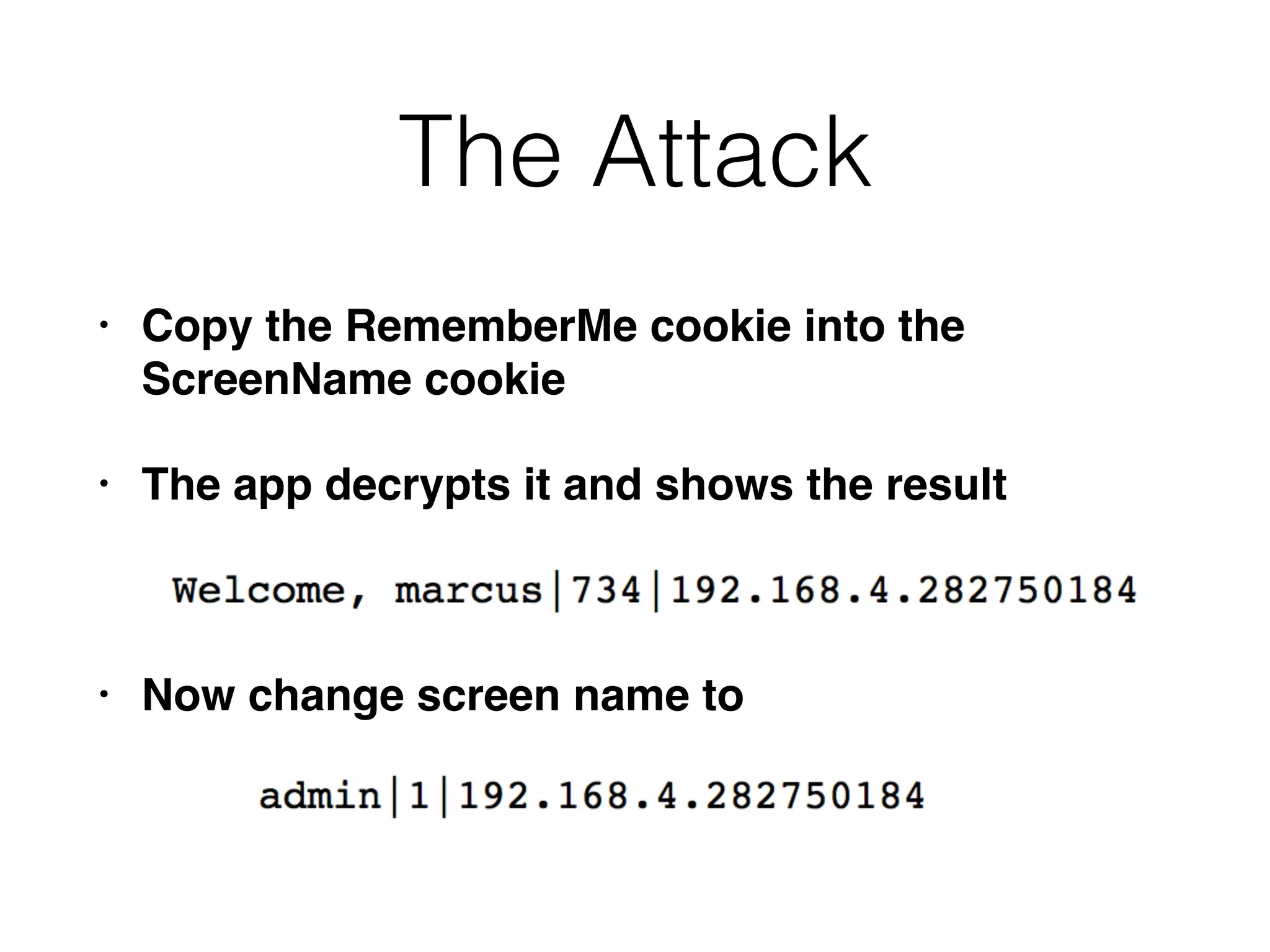






















![The Attack
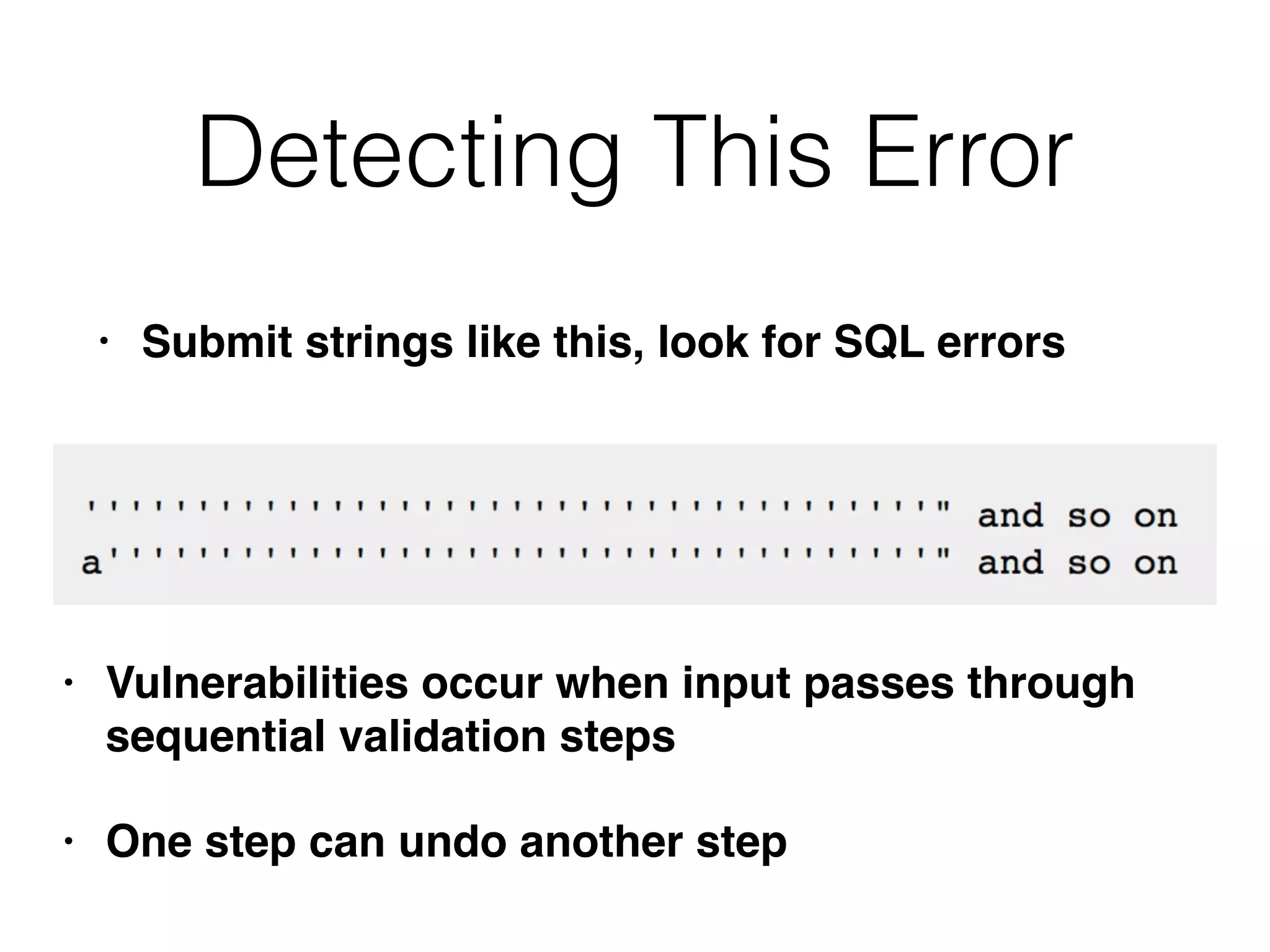
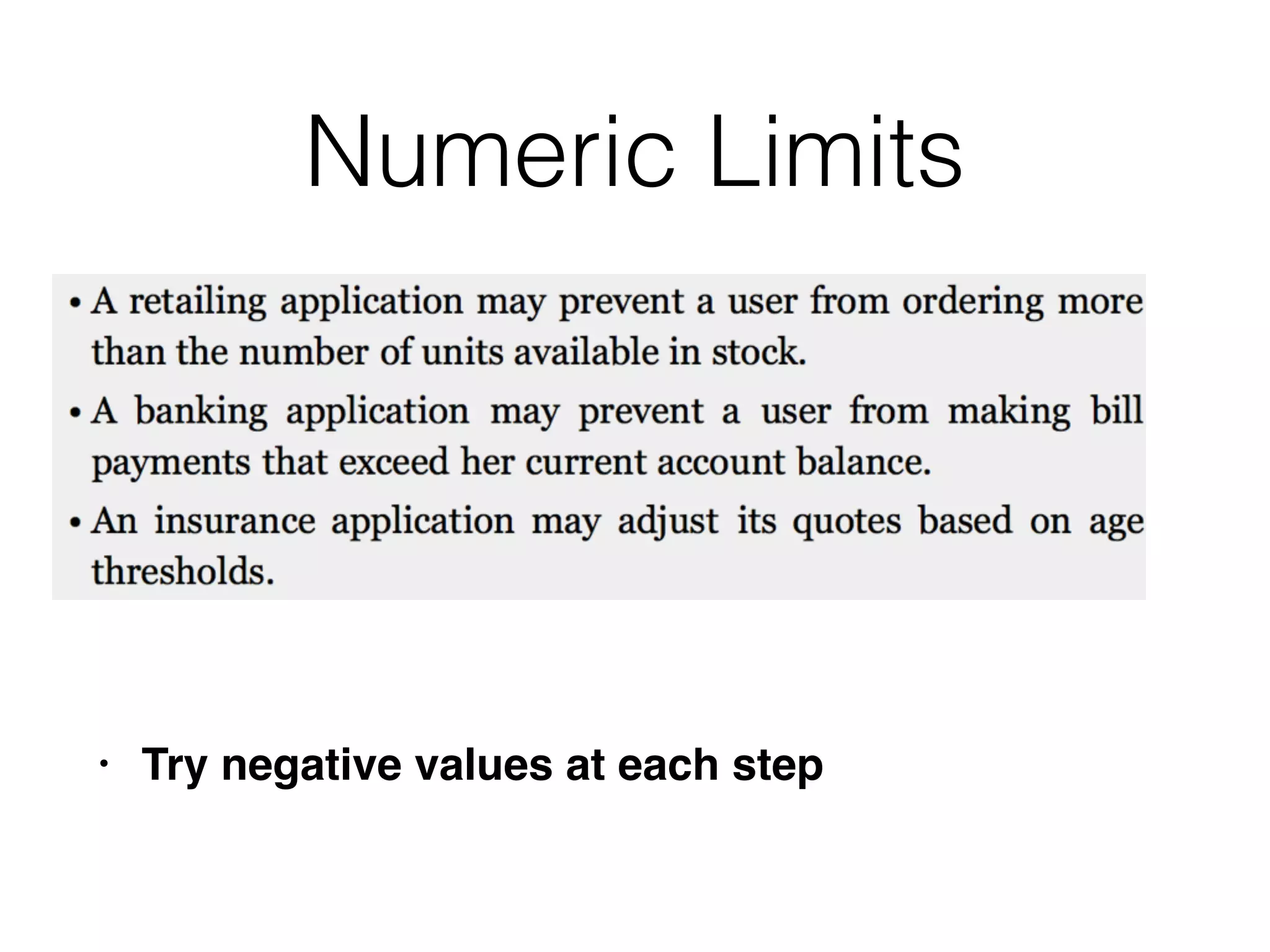
• Submit a username of 127 a's followed by a
single quotation mark, and password foo
• aaaaa[...]aaaaa'
• App adds another ', but the length limit removes
it
• This causes a SQL syntax error
• SELECT * FROM users WHERE username =
'aaaaa[..]aaaaa'' and password =
'foo'](https://image.slidesharecdn.com/ch11-161115001626/75/CNIT-129S-11-Attacking-Application-Logic-41-2048.jpg)
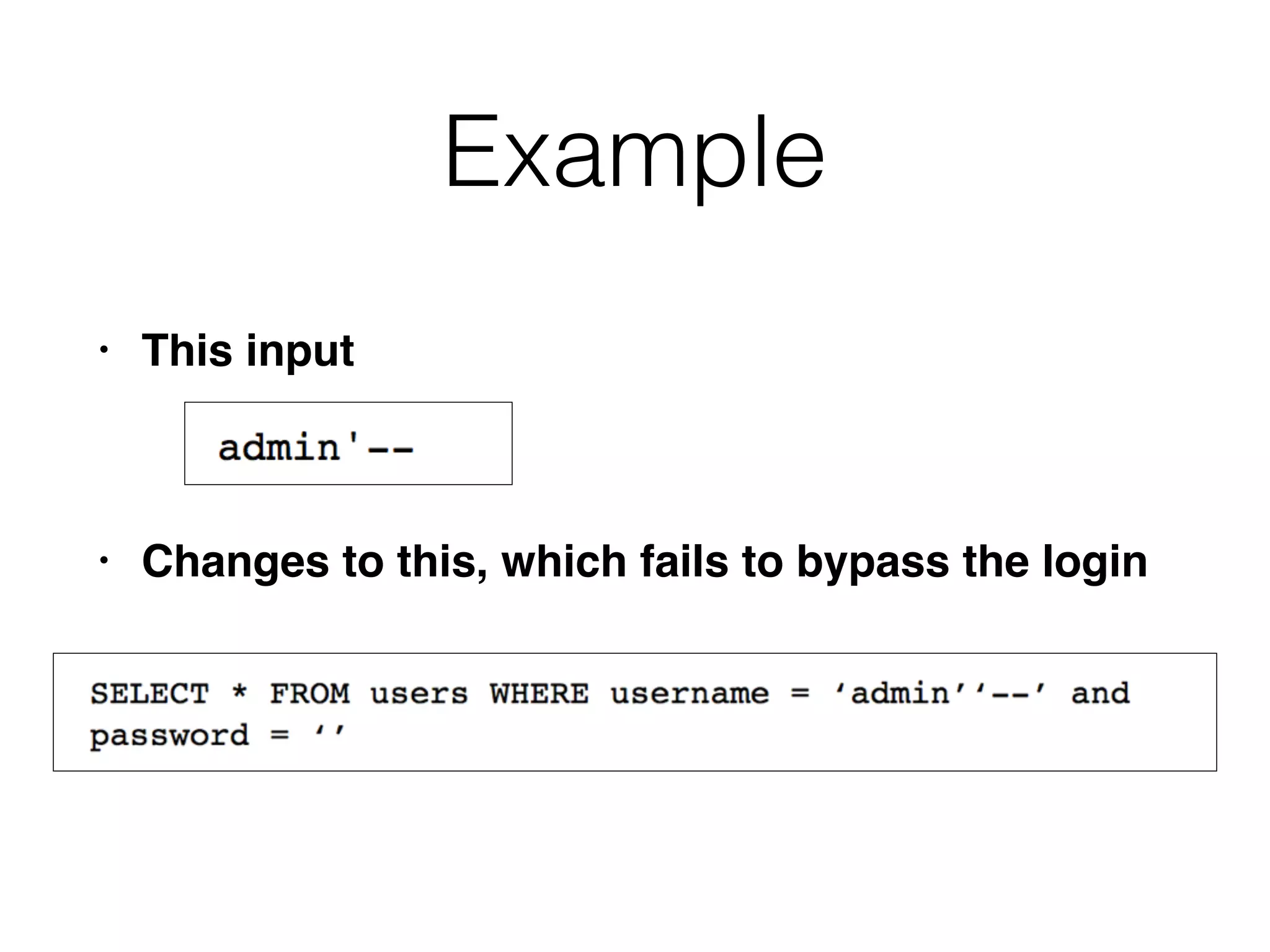
![The Attack
• Submit the same username, and a password of
• or 1=1--
• Query becomes this, bypassing the login
• SELECT * FROM users WHERE username =
'aaaaa[..]aaaaa'' and password = 'or
1=1--'
• '' is interpreted as a literal ', not a metacharacter](https://image.slidesharecdn.com/ch11-161115001626/75/CNIT-129S-11-Attacking-Application-Logic-42-2048.jpg)