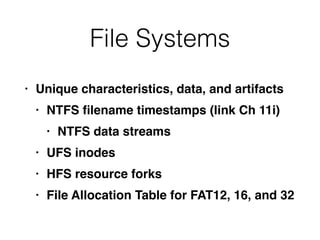
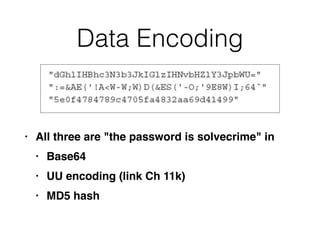
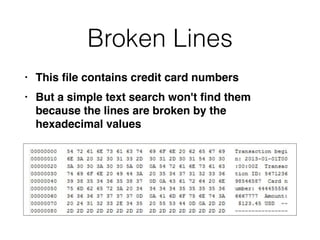
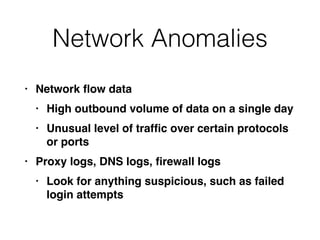
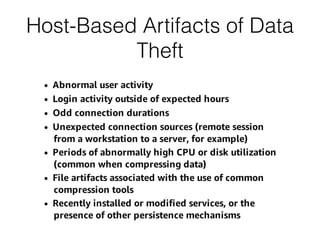
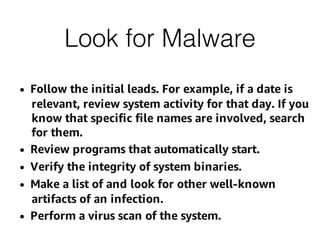
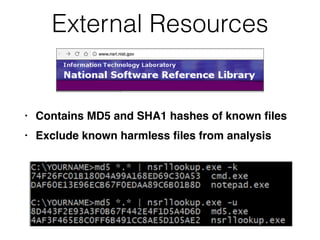
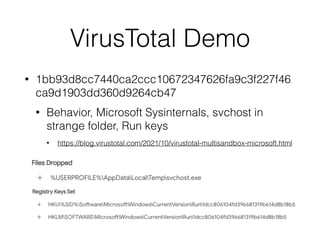
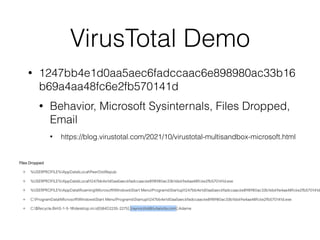
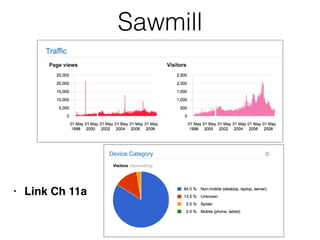
This document provides an overview of the incident response analysis methodology process. It discusses defining objectives, understanding the situation and available resources, identifying leadership, avoiding impossible tasks like proving a negative, asking why to define scope, knowing where data is stored, accessing raw data, selecting analysis methods like searching for malware or using tools like VirusTotal, manual review, filtering data, statistical analysis using tools like Sawmill, string searching, analyzing unallocated space, and file carving. It stresses periodically evaluating results to ensure progress and only making definitive statements if supported by evidence.