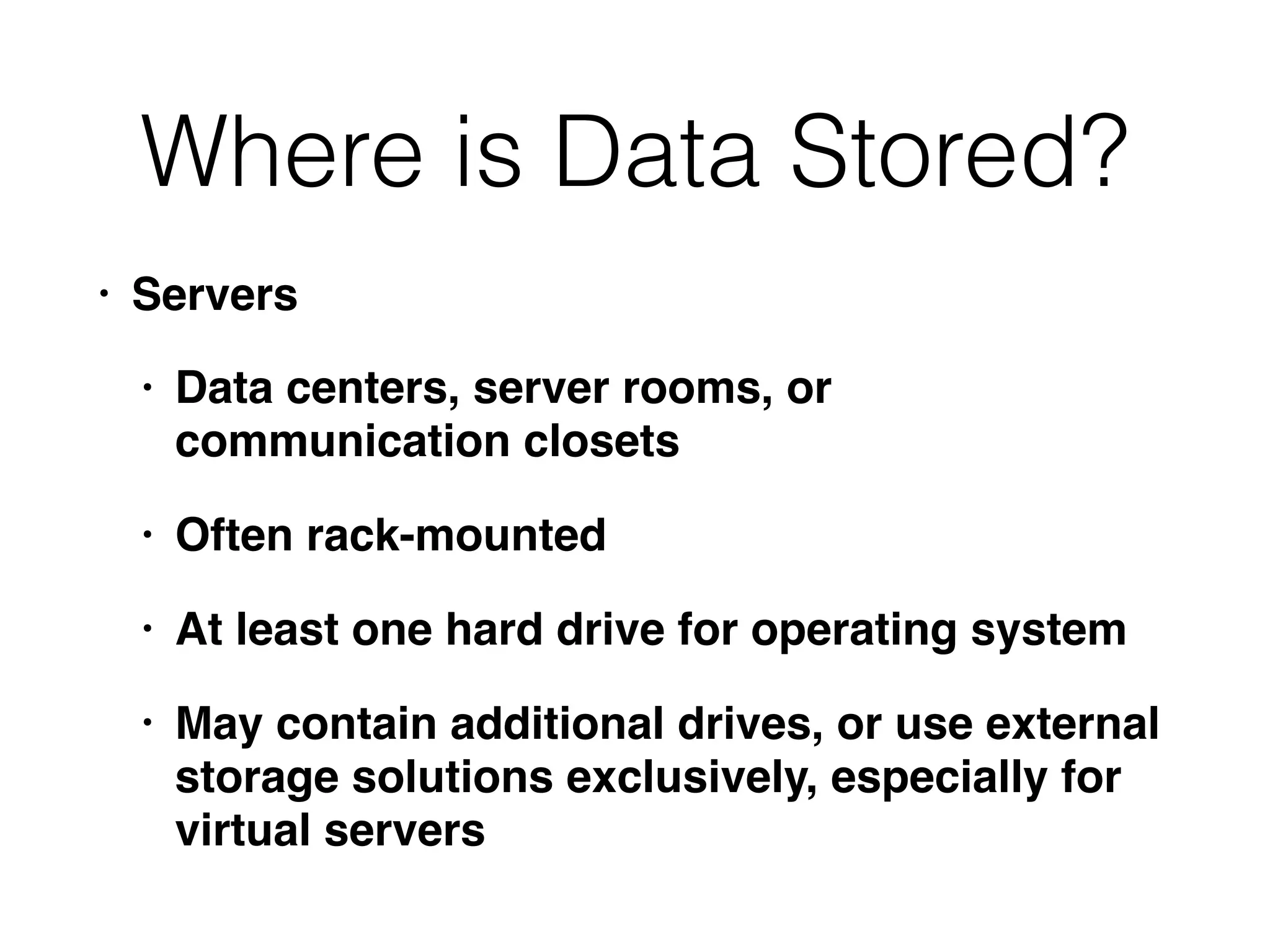
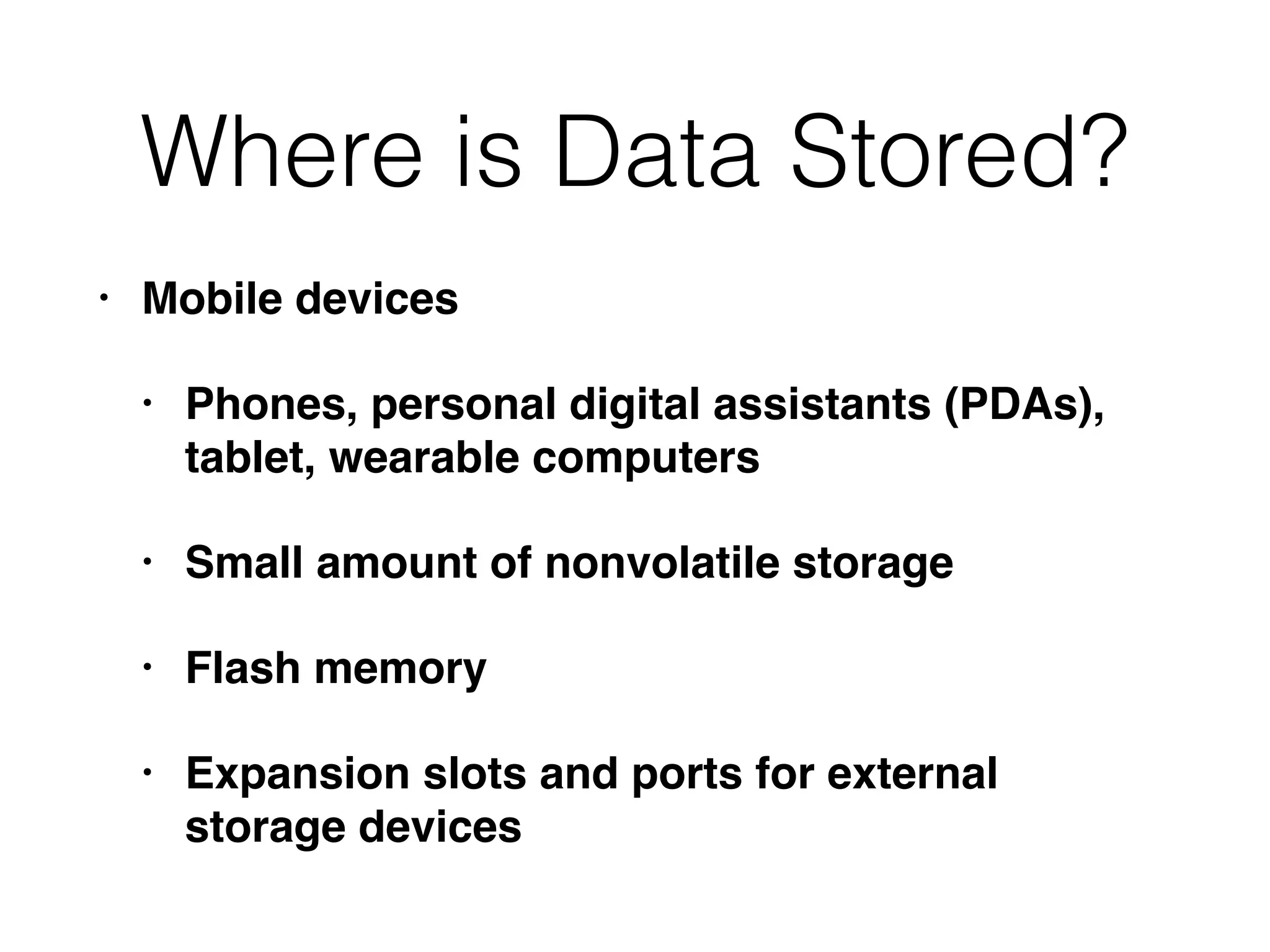
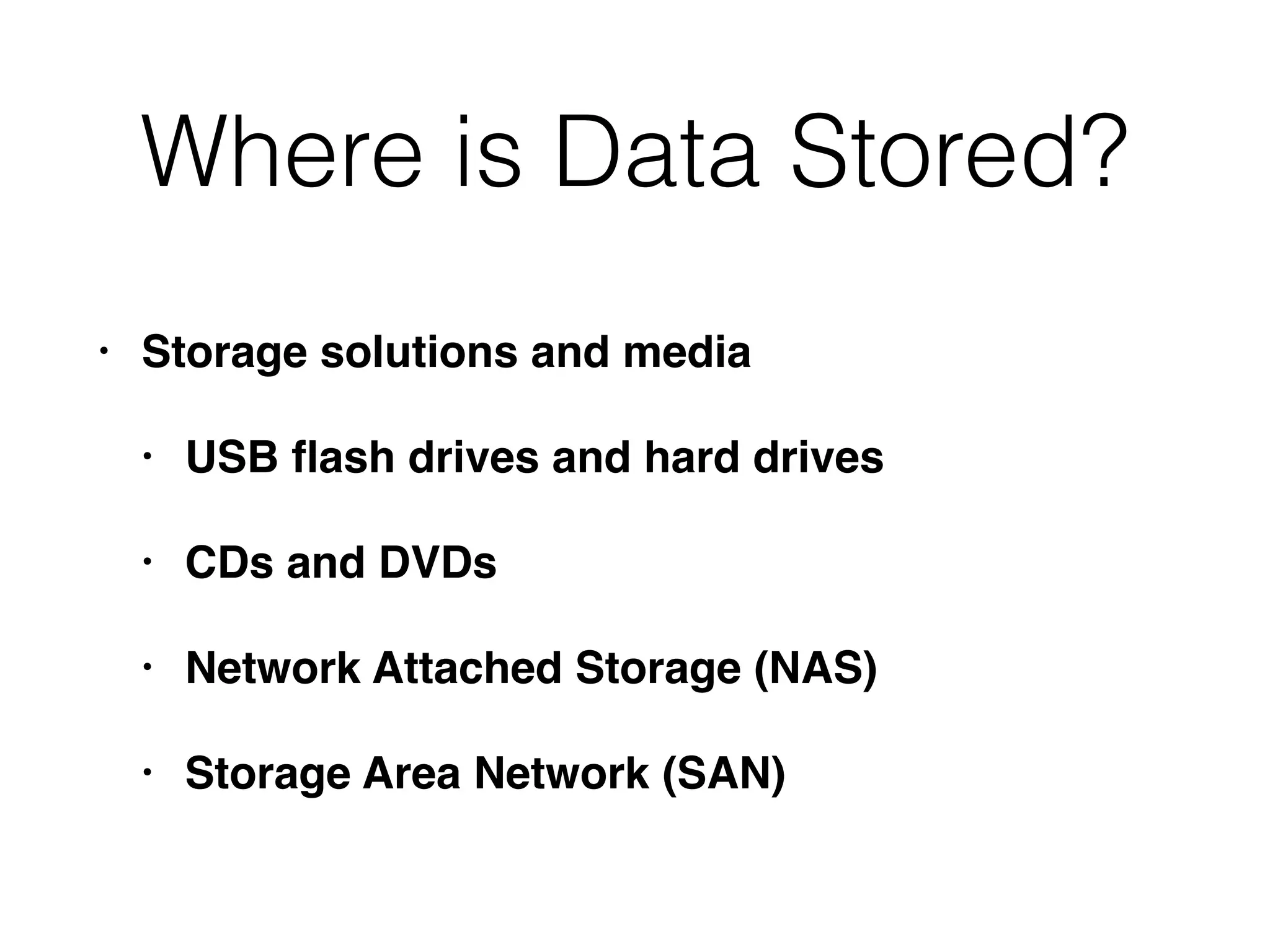
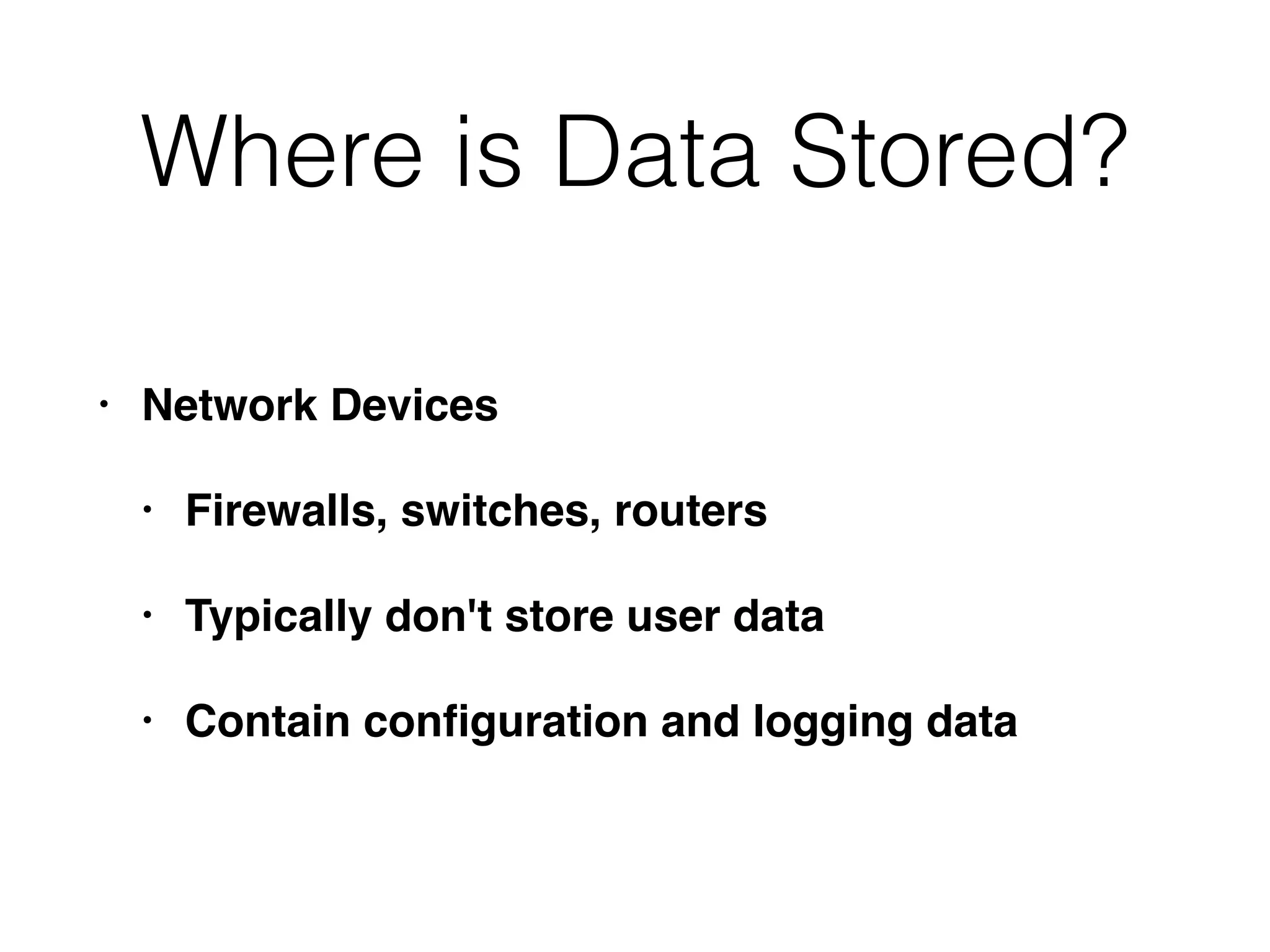
The document outlines a methodology for conducting computer forensics investigations, emphasizing the importance of defining objectives, understanding data storage locations, and identifying relevant evidence types. It discusses various aspects of data analysis, including methods for examining operating systems, applications, and network services, as well as strategies for data minimization and statistical analysis. Additionally, it highlights the need for effective communication within the investigative team and the importance of verifying findings to ensure accurate results.