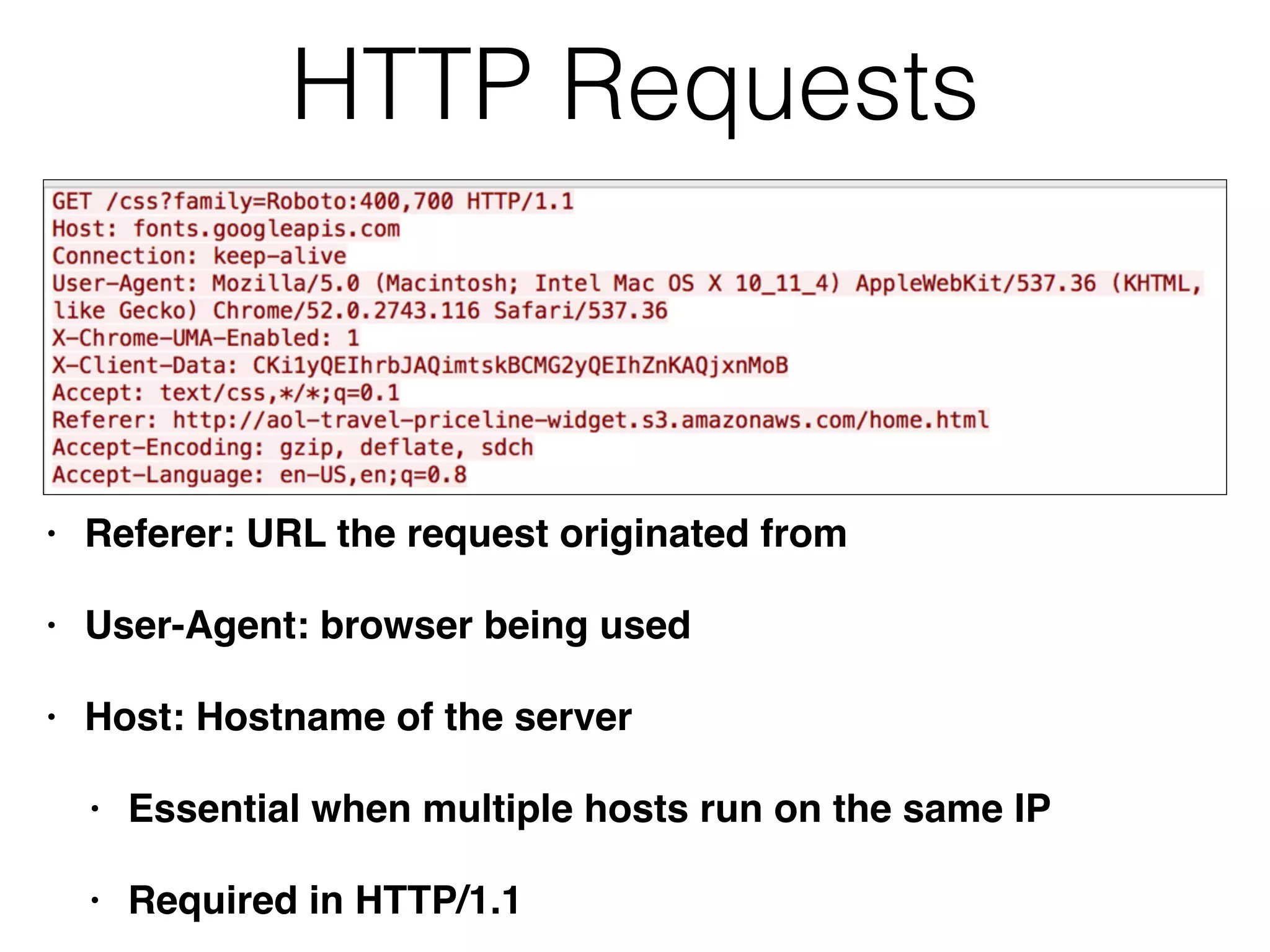
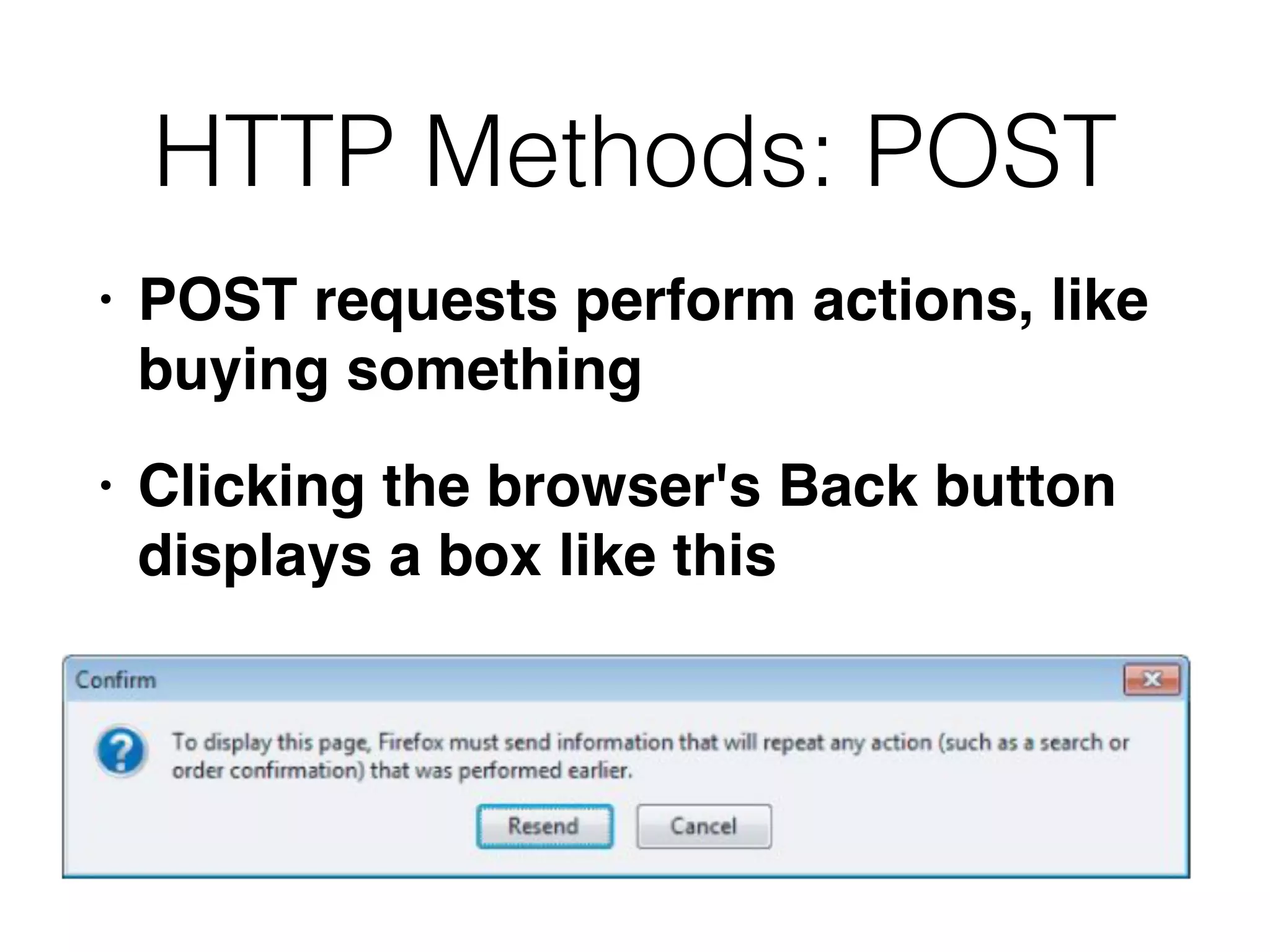
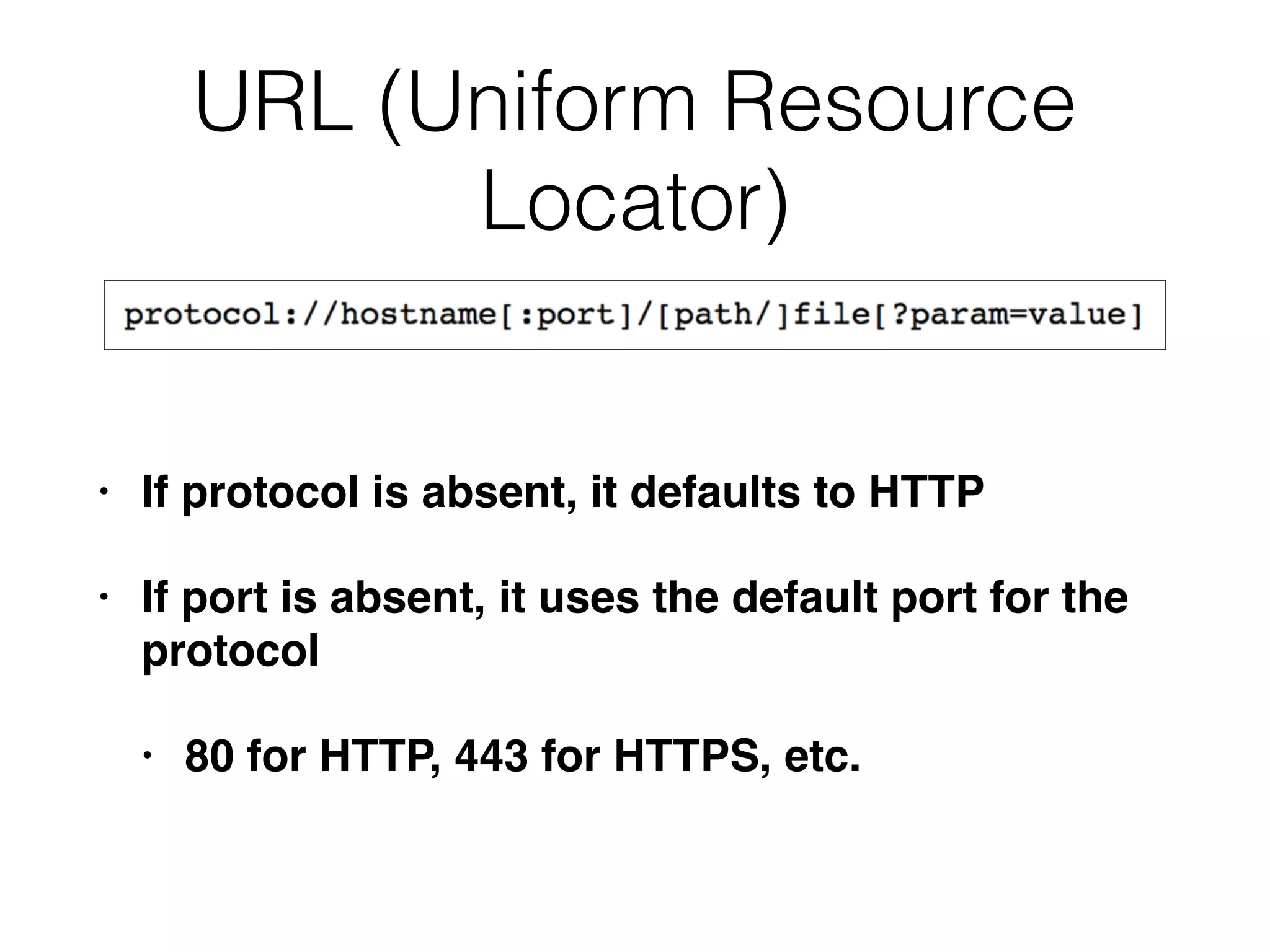
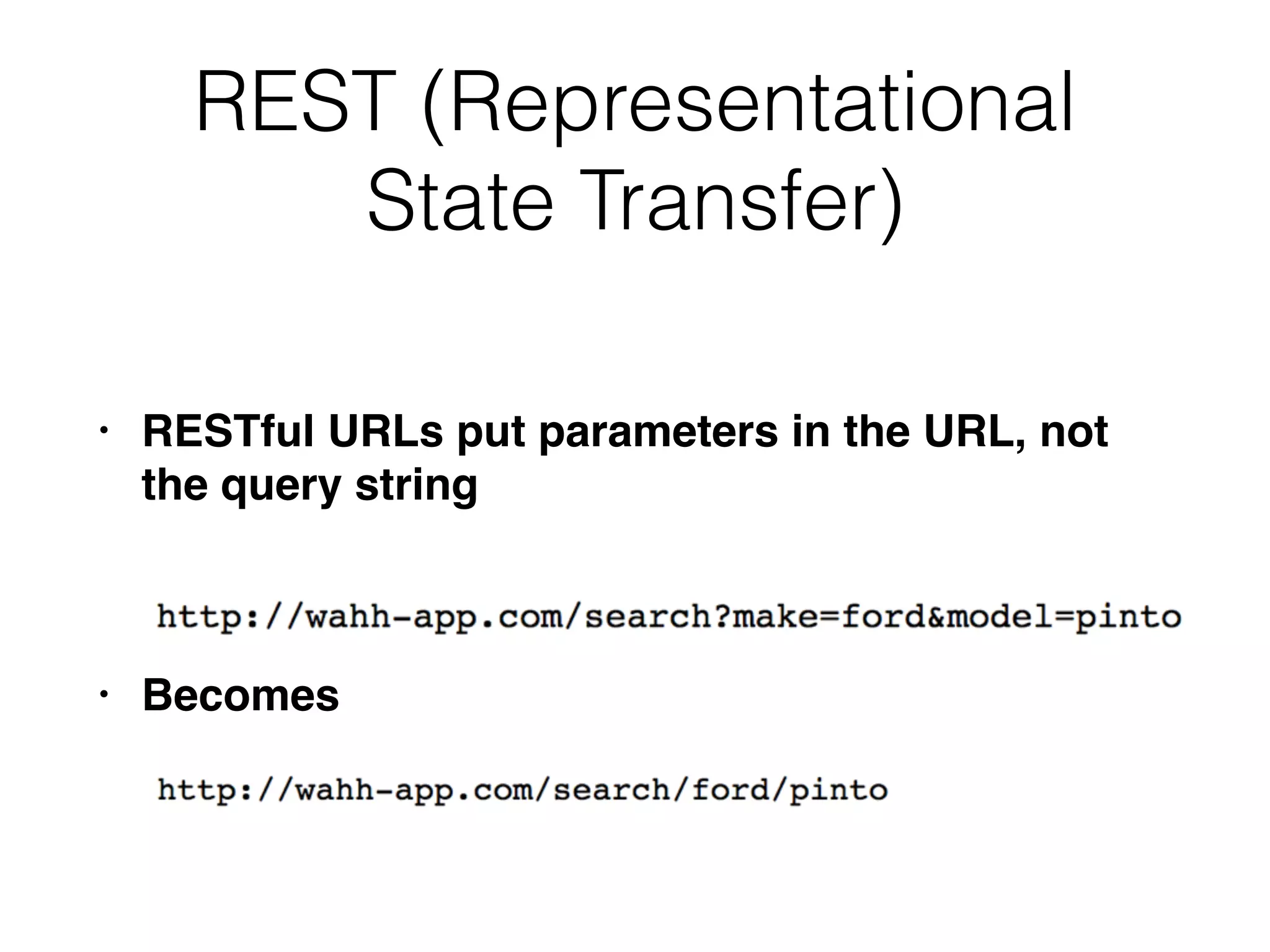
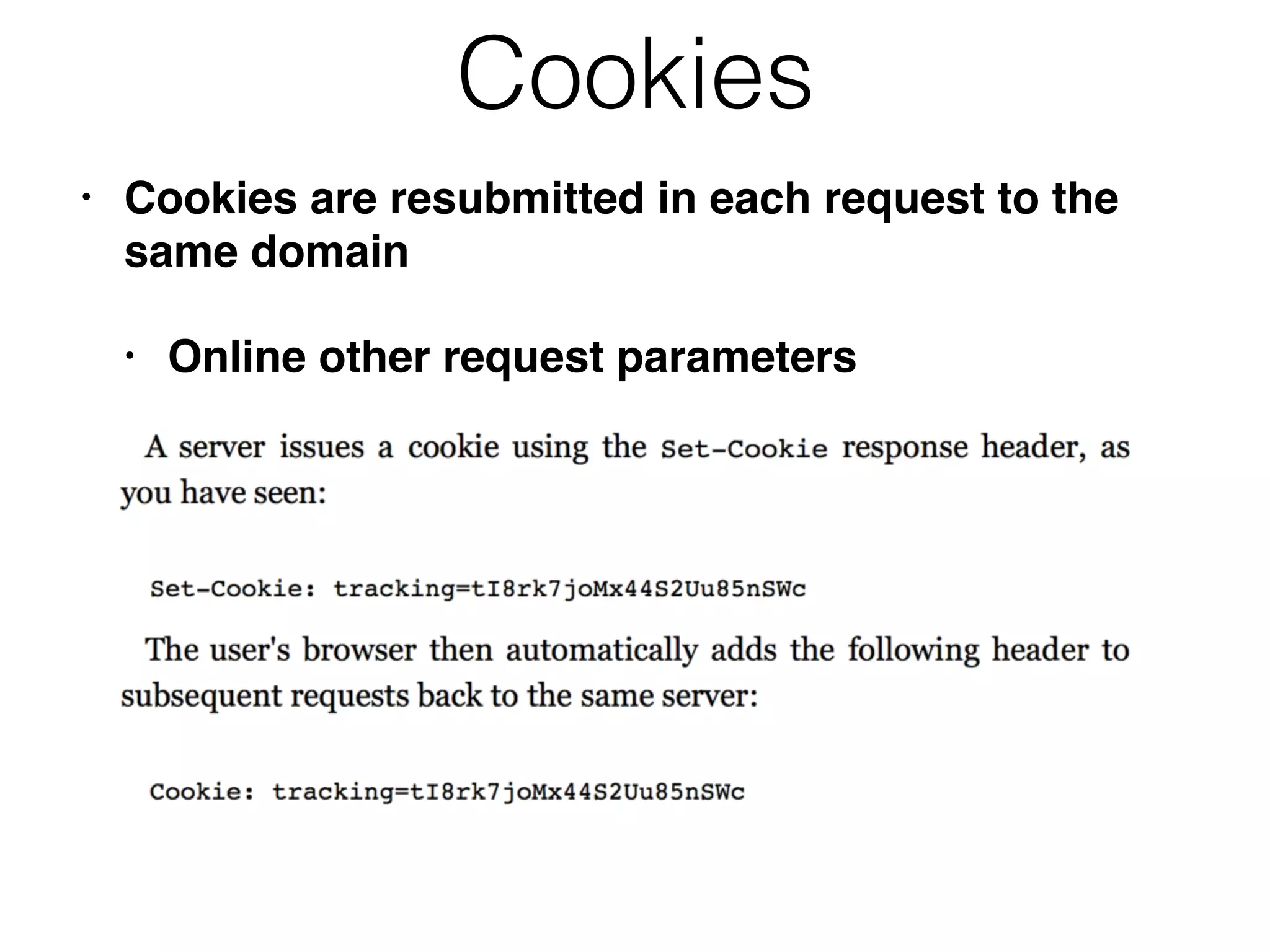
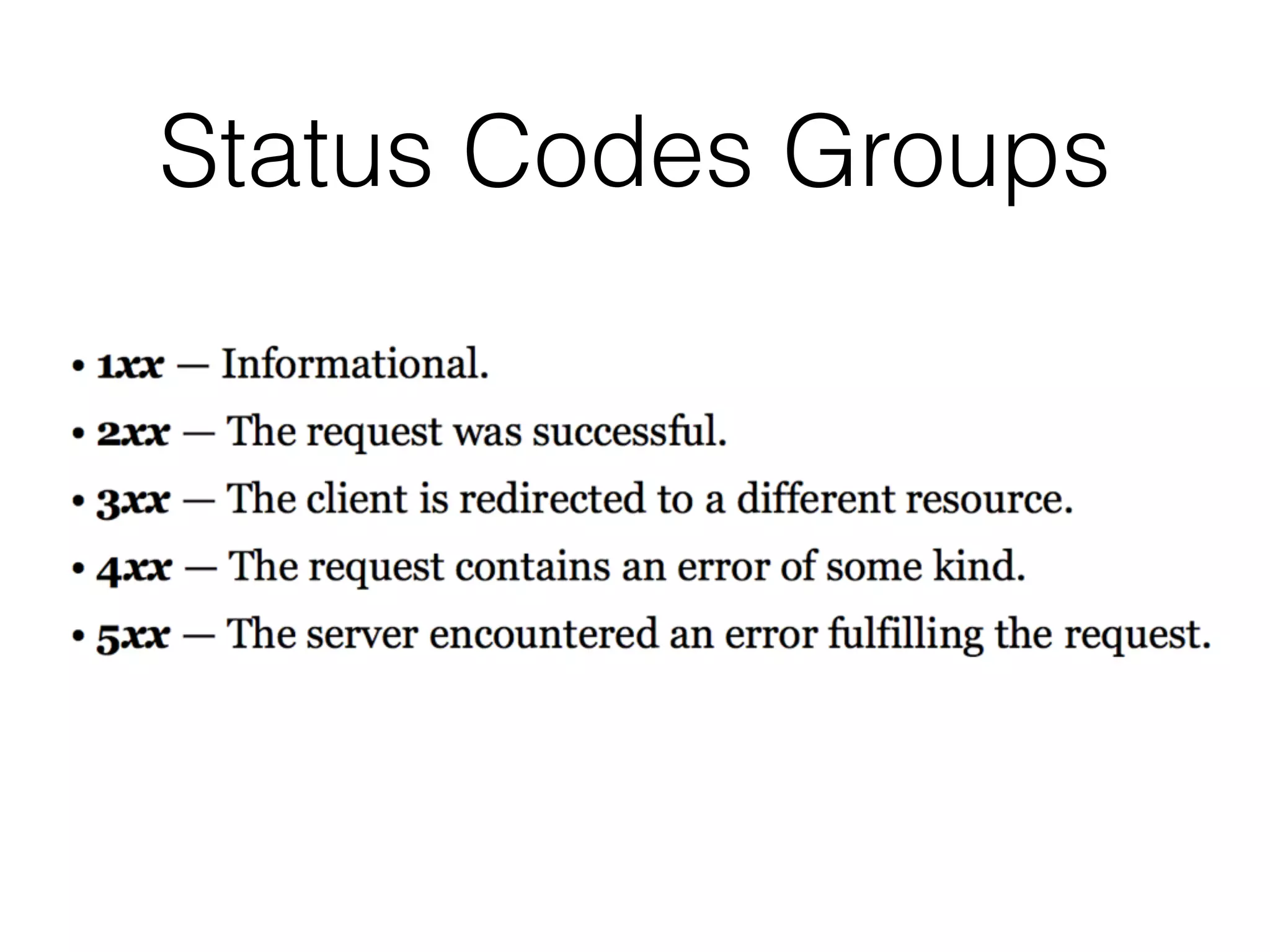
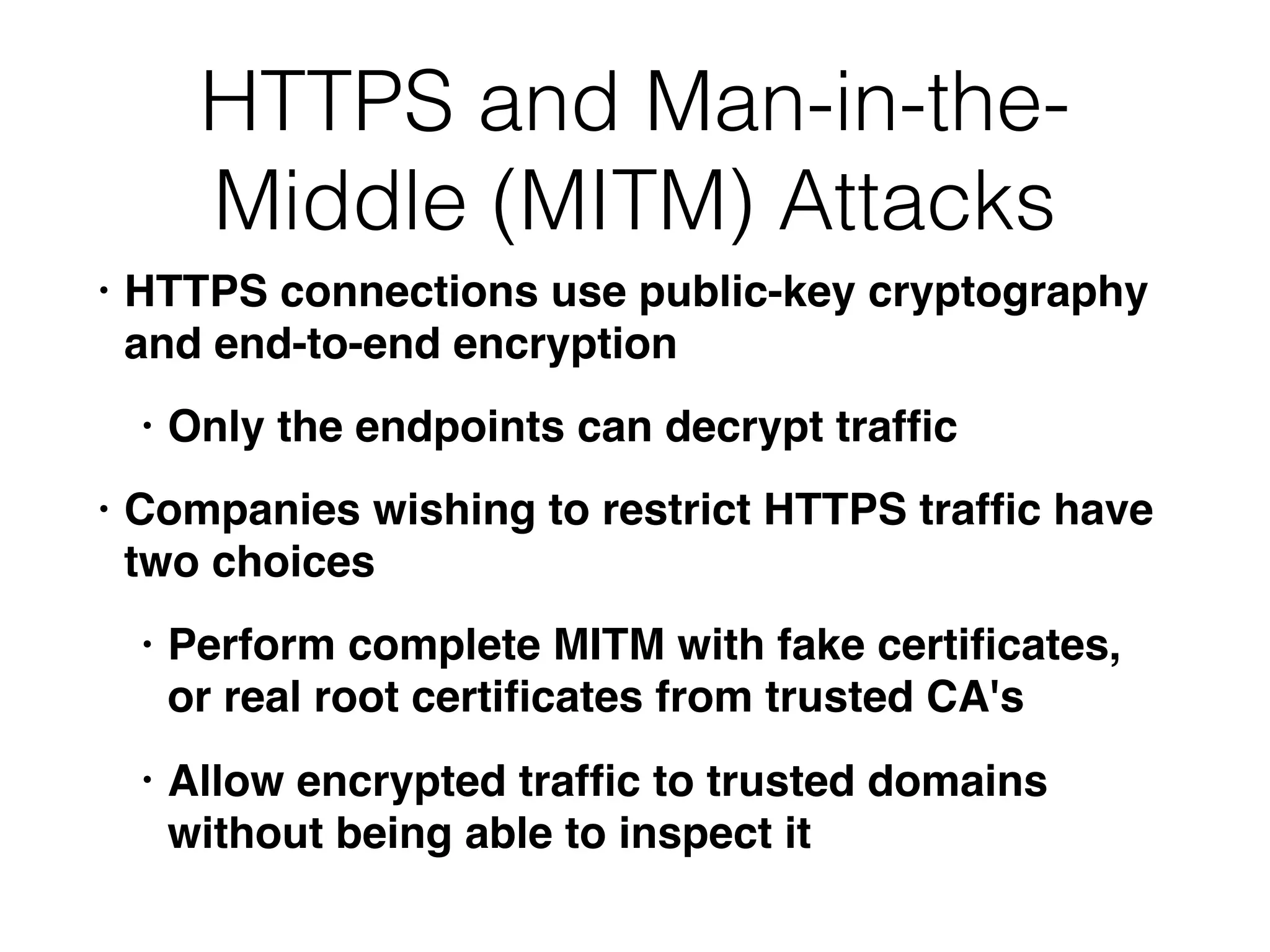
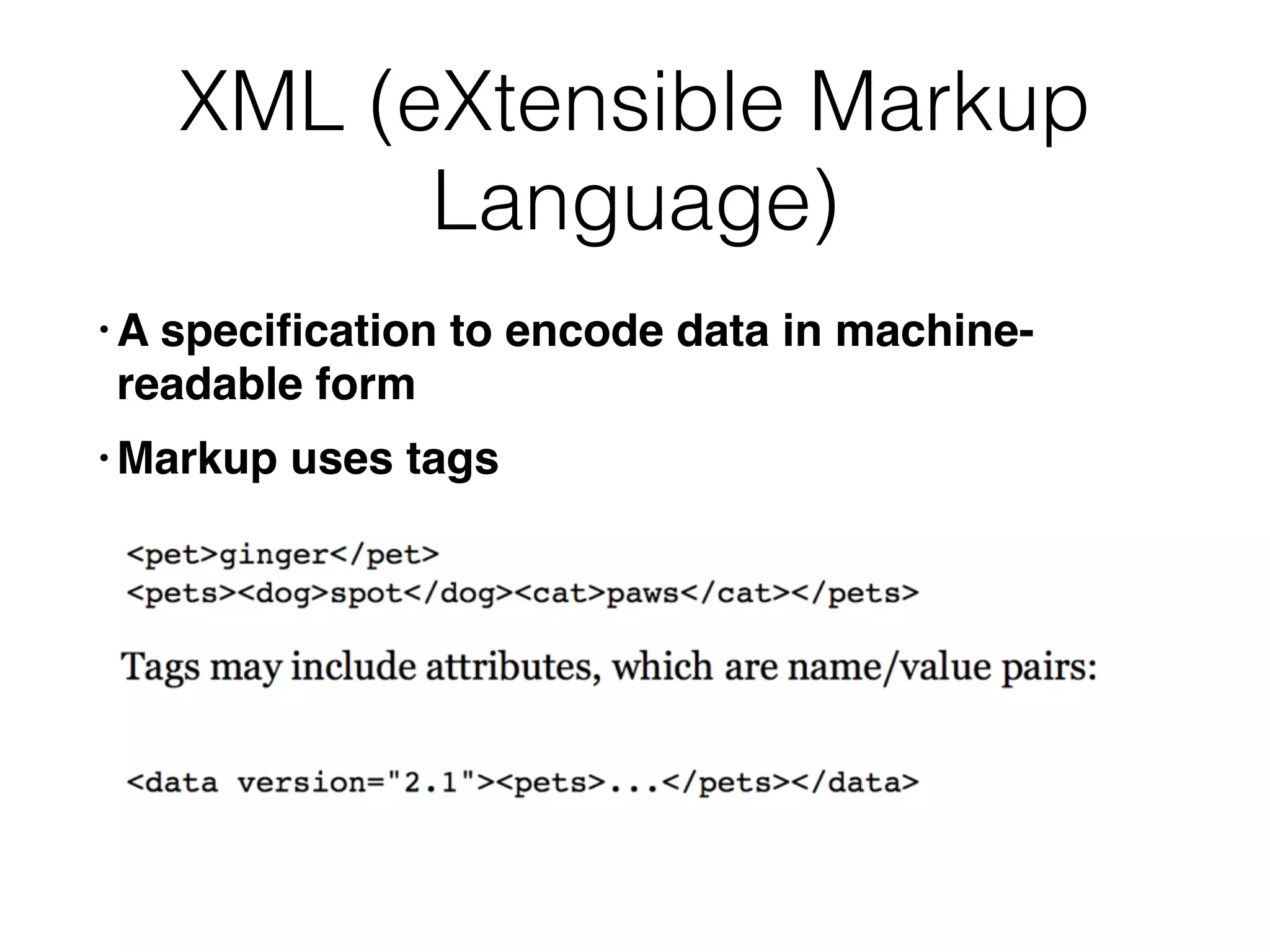
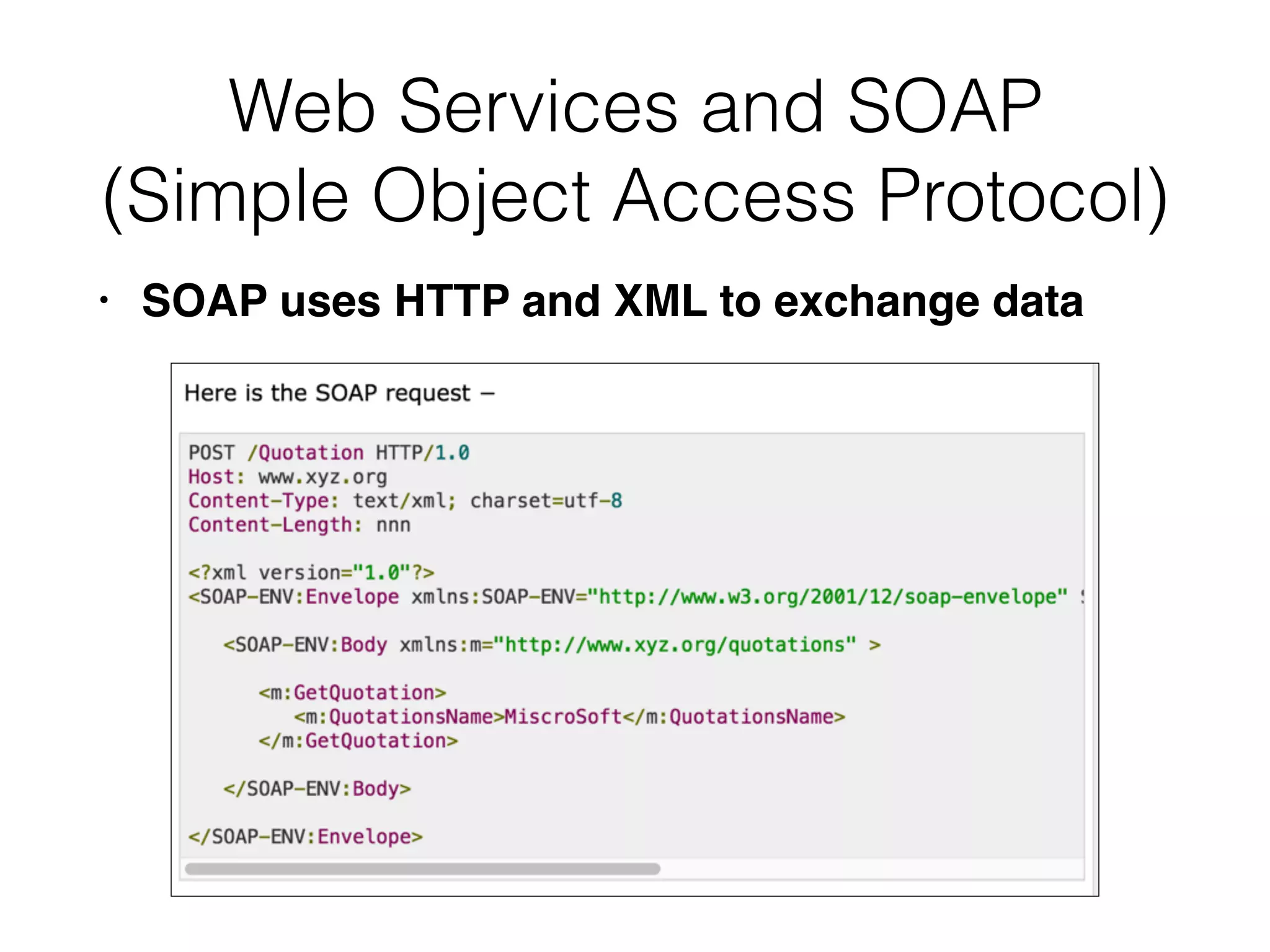
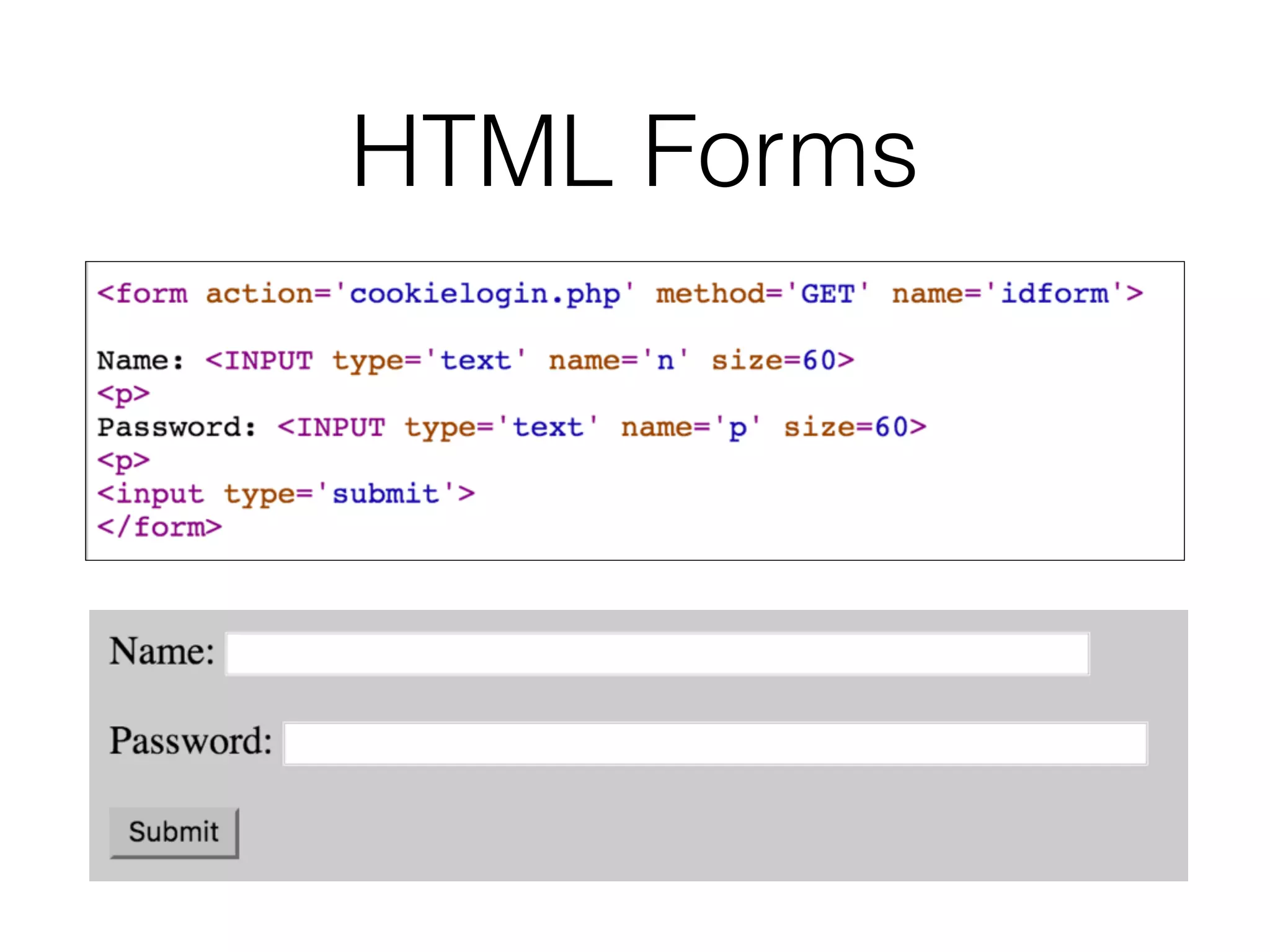
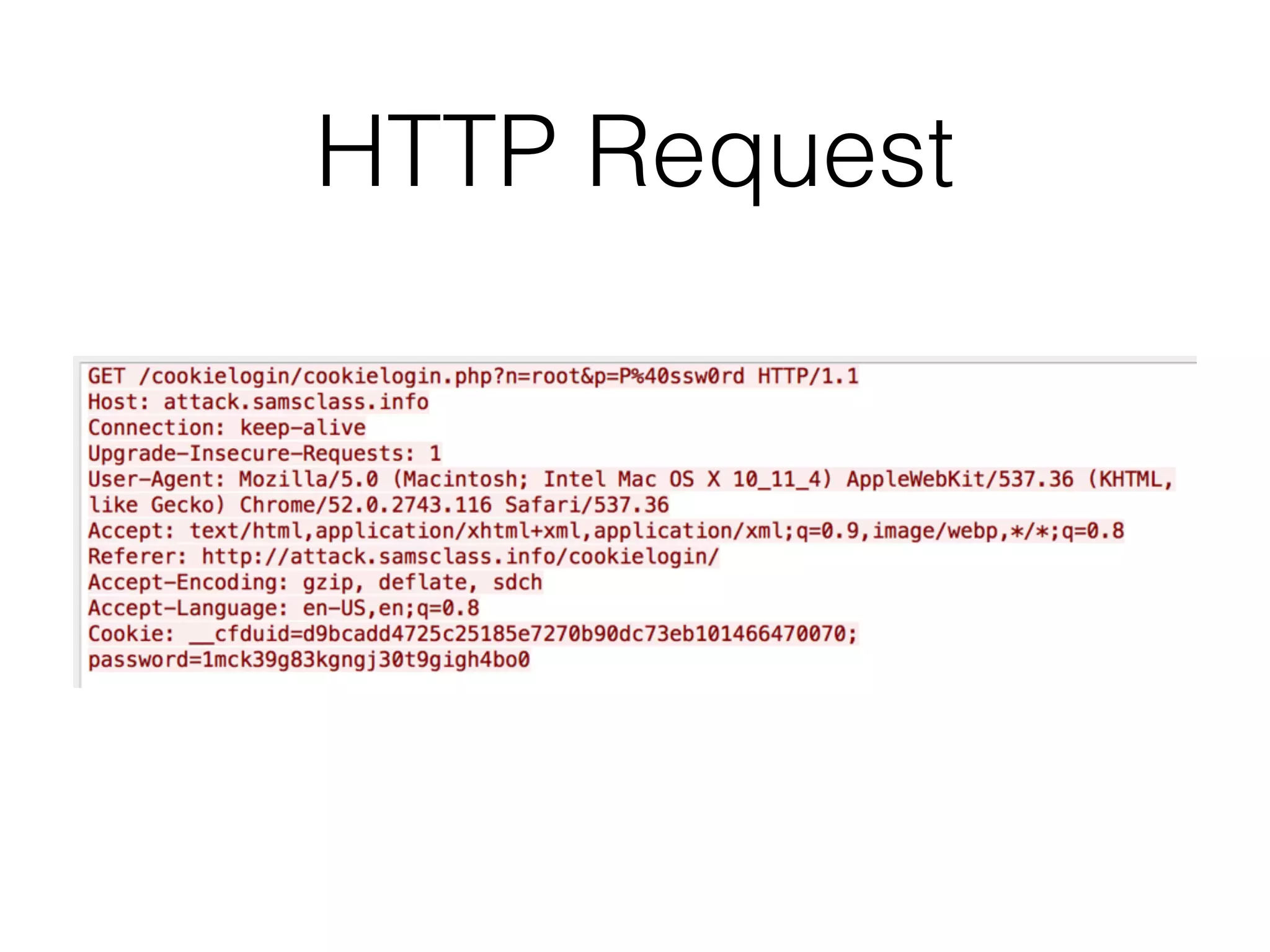
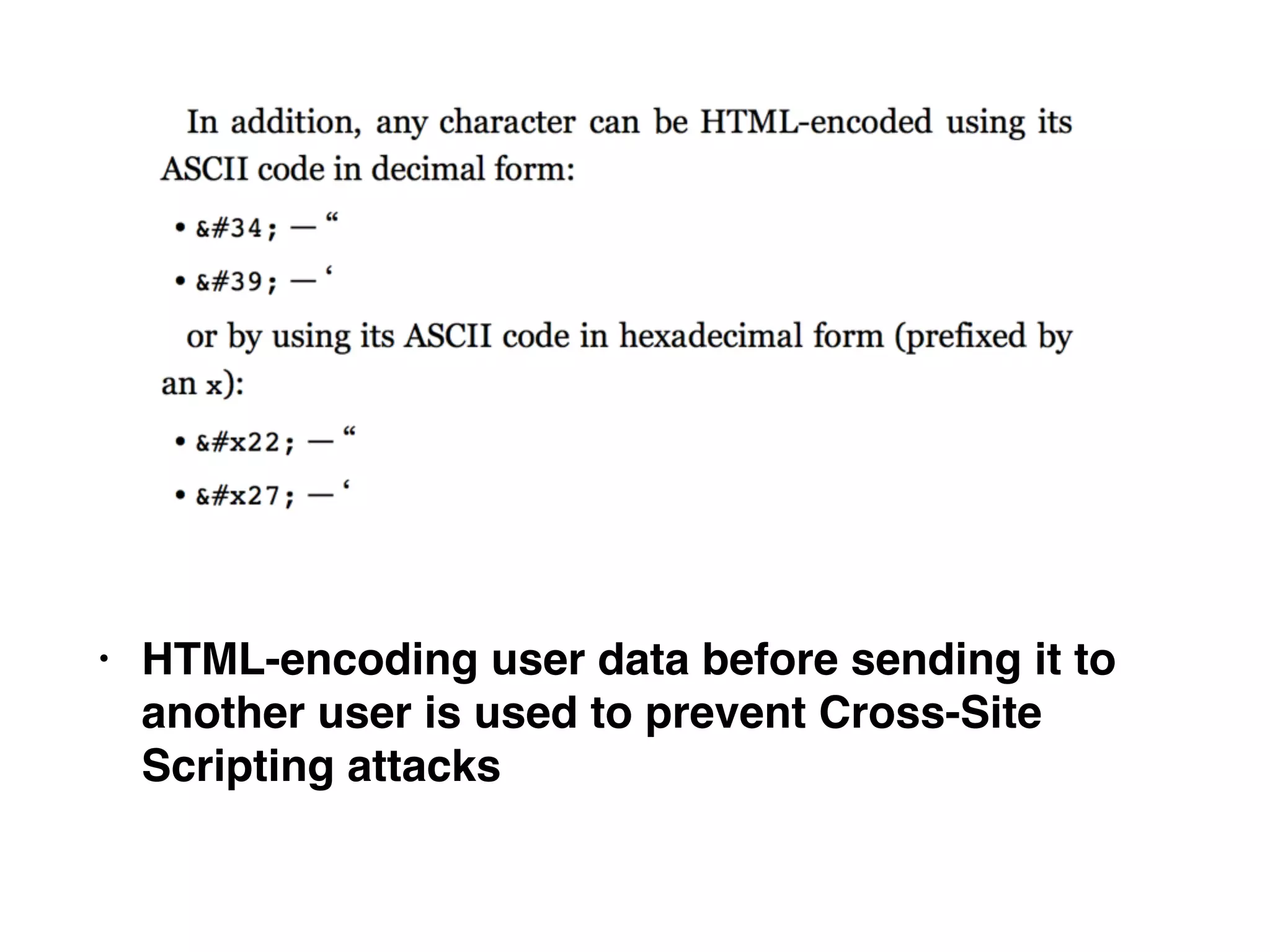
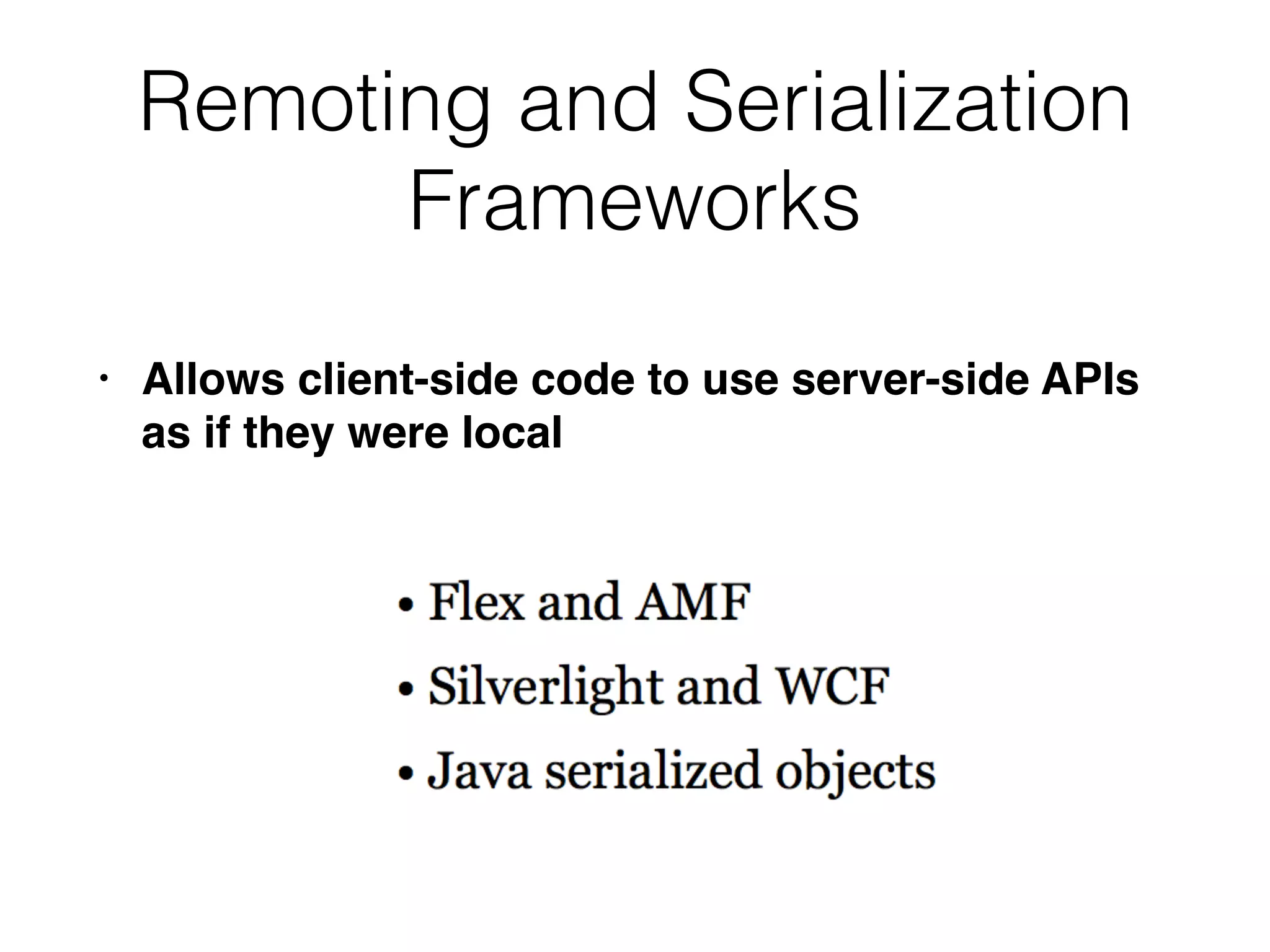
Chapter 3 covers essential web application technologies, focusing on HTTP and how it operates as a connectionless protocol with various request methods like GET and POST. It discusses the structure of HTTP requests and responses, including status codes, cookies, and security measures through HTTPS and proxies. Additionally, it introduces server-side and client-side functionalities, touching on technologies such as Java, ASP.NET, PHP, and AJAX, along with encoding schemes used to ensure safe data transmission.