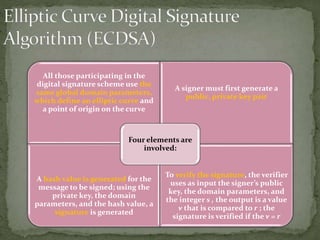
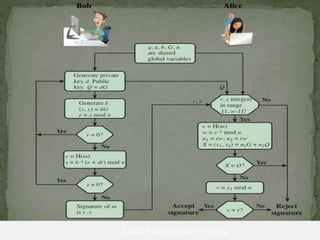
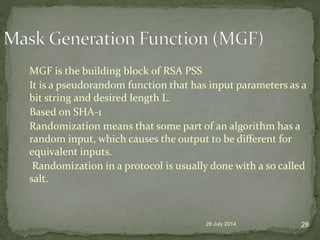
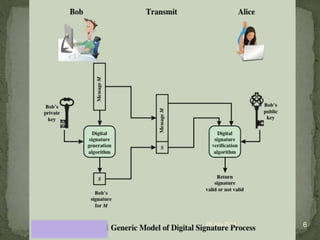
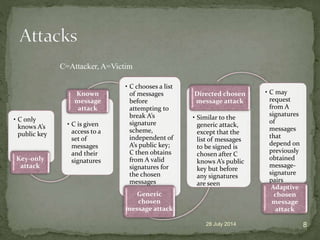
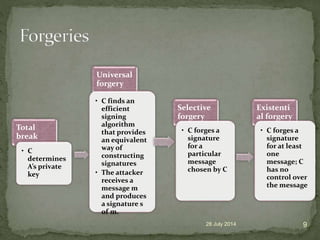
A digital signature allows one to verify the identity of the sender of a message and that the message content has not been altered. It involves a key generation algorithm that produces a private key and public key pair. The signing algorithm uses the private key to generate a signature for a message. The signature verification algorithm uses the public key to verify the signature and authenticity of the message. Digital signatures provide security as long as the private key remains confidential to the owner.















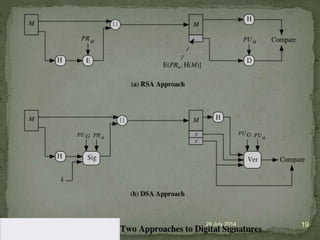

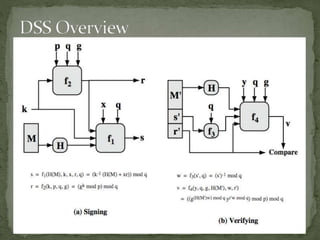
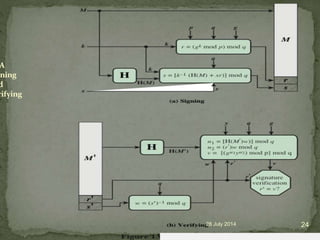
![ to sign a message M the sender:
generates a random signature key k, k<q
k must be random, be destroyed after use, and never be
reused
then computes signature pair:
r = (gk mod p)mod q
s = [k-1(H(M)+ xr)] mod q
sends signature (r,s) with message M](https://image.slidesharecdn.com/digitalsignature-140728072105-phpapp02/85/Digital-signature-21-320.jpg)
![having received M & signature (r,s)
to verify a signature, recipient computes:
w = s-1 mod q
u1= [H(M)w ]mod q
u2= (rw)mod q
v = [(gu1 yu2)mod p ]mod q
if v=r then signature is verified.](https://image.slidesharecdn.com/digitalsignature-140728072105-phpapp02/85/Digital-signature-22-320.jpg)