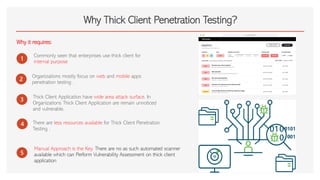
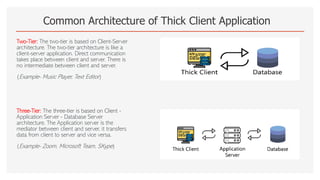
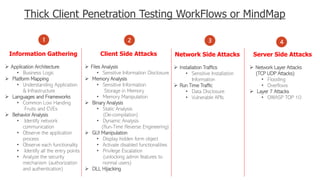
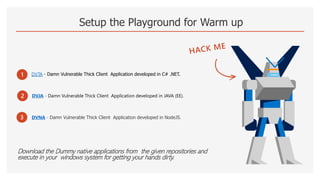
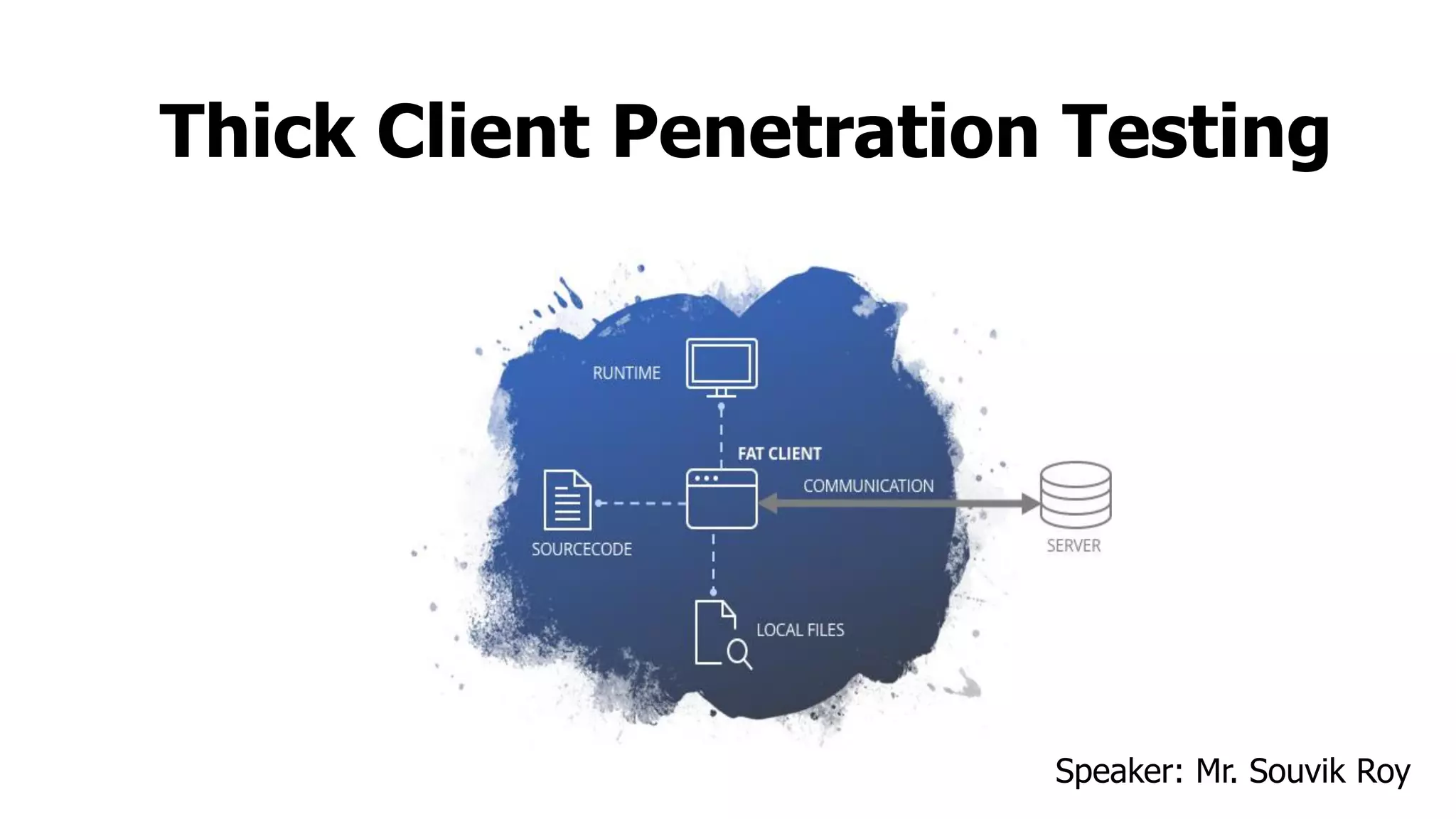
The document discusses thick client penetration testing, emphasizing the need for this type of testing due to vulnerabilities in thick client applications often overlooked in enterprise environments. It outlines the architecture of thick clients, common vulnerabilities, and workflows for testing, including client-side, network-side, and server-side attacks. Additionally, it provides details on tools and techniques for testing and practical applications, highlighting the importance of manual approaches in the absence of automated scanners.
![cat ~/.profile
# ~/.profile: executed by Bourne-compatible login shells.
if [ “ $IT Security Analyst " ]; then
if [ -f ~/.Application Security Engineer ]; then
. ~/.Web Application PenTester
. ~/.Source Code Reviewer
. ~/.Android Application PenTester
. ~/.Thick Client Application PenTester
fi
fi
mesg n 2> /OWASP/Kolkata_Lead || true.](https://image.slidesharecdn.com/thickclientpenetrationtesting-220827161917-0ab50495/85/Thick-Client-Penetration-Testing-pdf-2-320.jpg)