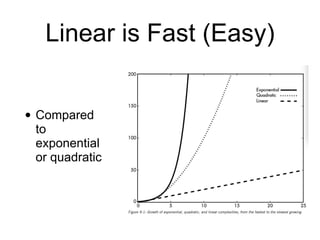
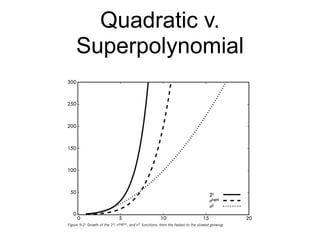
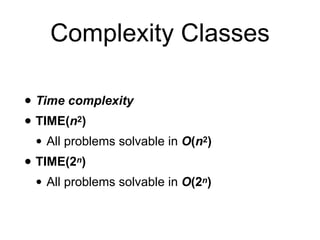
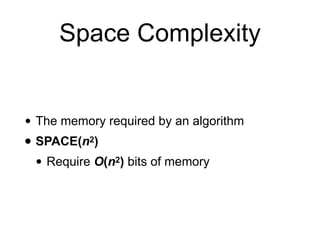
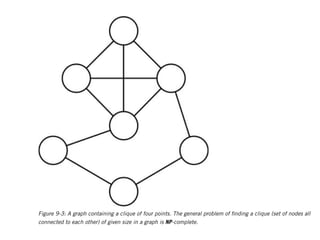
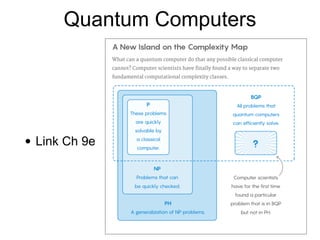
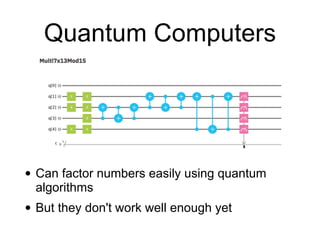
This document discusses computational hardness and complexity classes related to cryptography. It covers the computational complexity of problems like factoring large numbers and the discrete logarithm problem. These problems are assumed to be hard, even for quantum computers, and form the basis for cryptographic techniques. The document also discusses how cryptography could be broken if faster algorithms were found for these problems or if the key sizes used were too small.




![Measuring Running Time
• Search an array of n elements to find x
• Loop goes from 1 to n
• Expected value: n/2
• Complexity is linear in n
• Doubling n doubles running time
search(x, array, n)
:
for i from 1 to n
if (array[i] == x) return i
;
return 0;](https://image.slidesharecdn.com/141-ch9-221102193232-7544adf0/85/9-Hard-Problems-5-320.jpg)