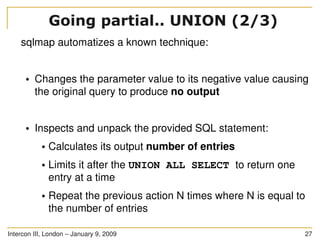
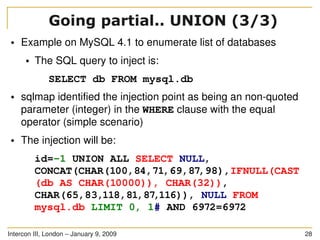
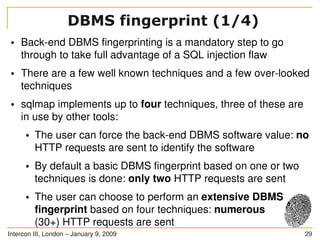
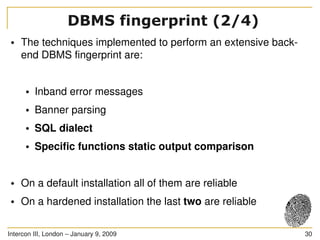
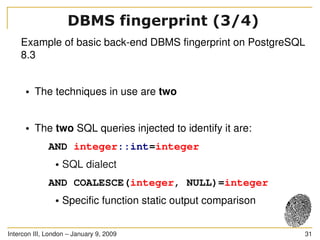
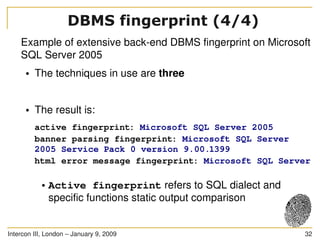
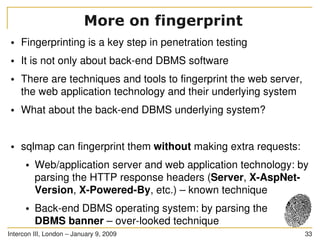
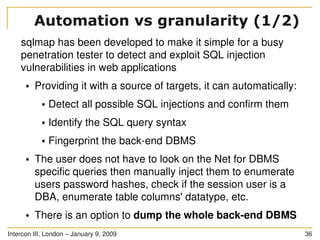
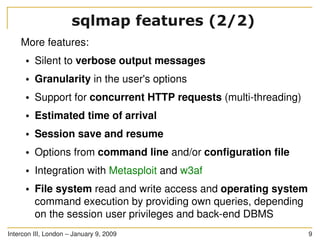
The document discusses SQL injection, a significant web application security flaw, and provides insights into exploiting such vulnerabilities using the automated tool sqlmap. It outlines the key features of sqlmap, including support for various databases and SQL injection techniques, as well as the importance of database management system fingerprinting. The presenter shares practical examples and limitations of sqlmap while encouraging contributions from the community.






![Intercon III, London – January 9, 2009 13
Python library helped to solve this problem: for each HTTP
response sqlmap calls a function that compares the returned
page content with the untouched original page content:
● Return a measure of the page contents' similarity as a float
in the range [0, 1] with a radio of 3.
● It works also when the original page is stable, but the
injected query with a valid condition (True) differs
If the automatic comparison fails, the user can provide a
string or a regular expression to match on both original and
True page contents and to not match on False page contents
Dealing with advertisements (3/3)](https://image.slidesharecdn.com/sqlinjectioninternals-1231599956953984-2/85/SQL-injection-exploitation-internals-13-320.jpg)
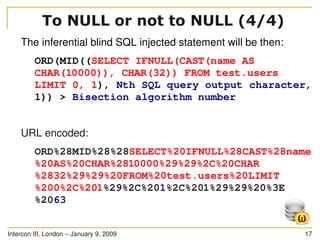
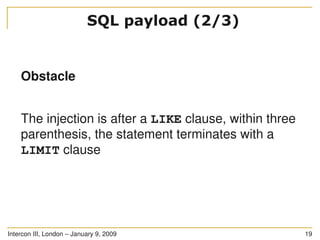
![Intercon III, London – January 9, 2009 18
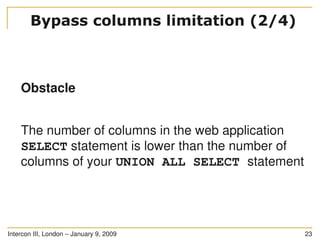
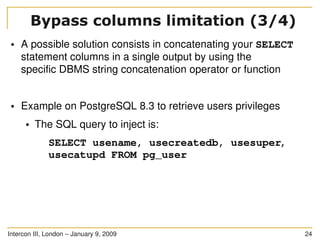
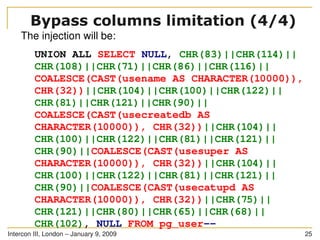
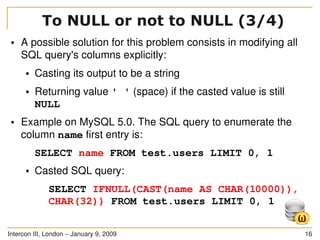
You have got an injection point
The injection point is in a SQL statement as follows:
SELECT * FROM users WHERE id LIKE ((('%" .
$_GET['id'] . "%'))) LIMIT 0, 1
SQL payload (1/3)](https://image.slidesharecdn.com/sqlinjectioninternals-1231599956953984-2/85/SQL-injection-exploitation-internals-18-320.jpg)