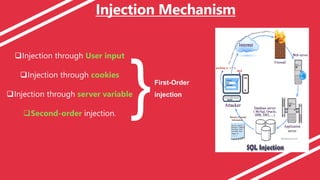
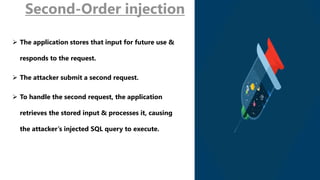
SQL injection is a code injection technique that attacks data-driven applications. It involves inserting malicious SQL statements into entry fields that are then executed by the database. There are different types of SQL injection attacks, including directly injecting code to immediately execute or injecting into persistent storage to be triggered later. Injection can occur through user input, cookies, or server variables. Prevention techniques aim to stop these types of attacks from harming databases.