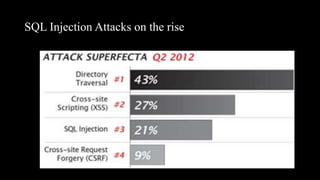
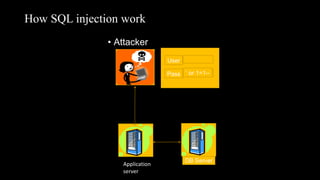
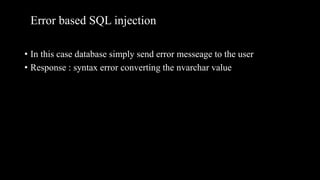
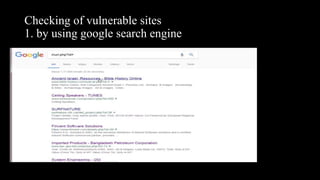
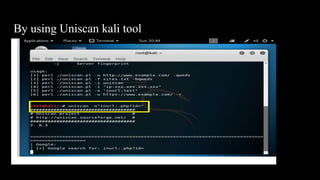
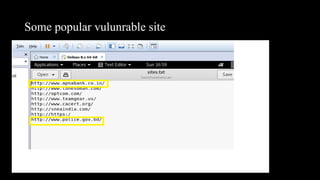
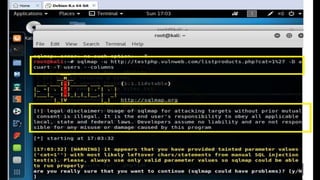
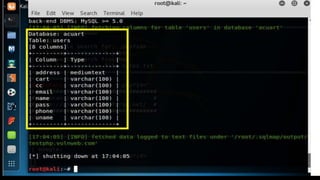
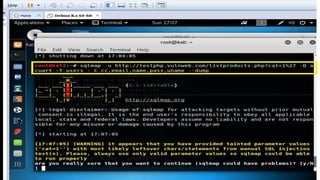
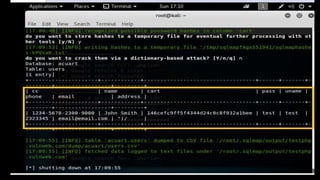
This document discusses SQL injection, including what it is, how it works, and its impacts. It defines SQL injection as a dangerous web attack that leverages vulnerabilities in web applications to bypass authentication and modify or delete database data. The summary explains that SQL injection works by manipulating SQL queries passed to a backend database, such as by appending additional SQL statements or modifying the structure of the original query. Some impacts of successful SQL injection attacks mentioned are leakage of sensitive information, reputation decline, data loss, and denial of service. Tools for finding SQL injection vulnerabilities like sqlmap and uniscan are also briefly described.