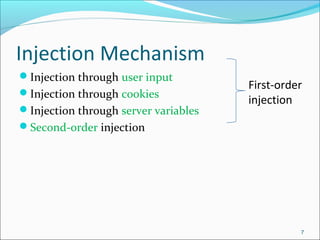
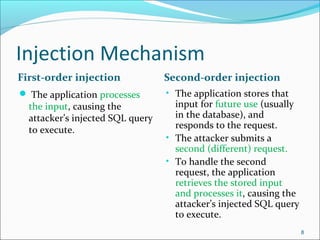
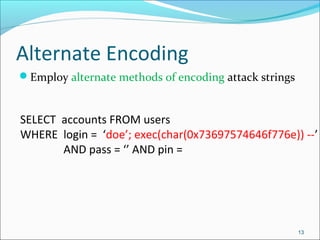
The document discusses SQL injection attacks, including what SQL injection is, types of SQL injection attacks such as first and second order attacks, mechanisms for injection through user input or cookies, and techniques for preventing SQL injection like defensive coding practices and input validation. SQL injection is a code injection technique where malicious SQL statements are inserted into an entry field for execution by the backend database, allowing attackers to view or manipulate restricted data in the database. The document provides examples of SQL injection and explores ways attackers can infer information and encode attacks despite prevention methods.