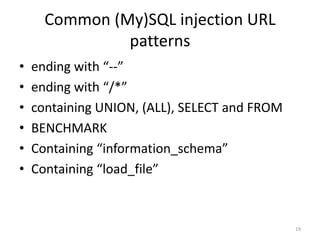
SQL injection is a critical security vulnerability that allows attackers to execute unintended SQL queries in a database, potentially leading to data theft or loss. To mitigate the risk, it is essential to escape and validate all user input, use prepared statements, and apply the principle of least privilege to database accounts. Additionally, guidelines for safe URL practices and awareness of common SQL injection patterns can help prevent these attacks.




![Actual use case
$sql = “SELECT * FROM ARTICLES WHERE id = “ . $_GET[“id”];
//executed query - SELECT * FROM ARTICLES WHERE ID = 1234
$result = mysql_query($sql);
5](https://image.slidesharecdn.com/sqlinjection-120704012741-phpapp02/85/Sql-Injection-attacks-and-prevention-5-320.jpg)
![SQL injected input
$sql = “SELECT * FROM ARTICLES WHERE id = “ . $_GET[“id”];
//executed query - SELECT * FROM ARTICLES WHERE ID = 1234; DROP
TABLE ARTICLES
$result = mysql_query($sql);
6](https://image.slidesharecdn.com/sqlinjection-120704012741-phpapp02/85/Sql-Injection-attacks-and-prevention-6-320.jpg)


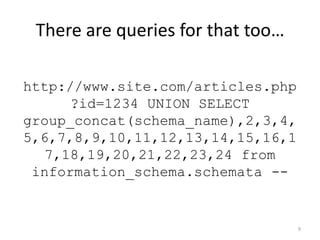
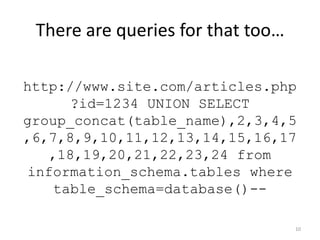




![Escape & Validate input
• Escape all input
– Whether supplied via the URL or via POST data
– Even for internal APIs
– Anything that goes to the DB is escaped
• Validate all input - Validating a Free Form Text Field for
allowed chars (numbers, letters, whitespace, .-_)
– ^[a-zA-Z0-9s._-]+$ (Any number of characters)
– ^[a-zA-Z0-9s._-]{1-100}$ (This is better, since it limits this
field to 1 to 100 characters)
• source https://www.owasp.org/index.php/Input_Validation_Cheat_Sheet
15](https://image.slidesharecdn.com/sqlinjection-120704012741-phpapp02/85/Sql-Injection-attacks-and-prevention-15-320.jpg)