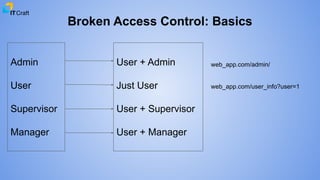
This document discusses security issues related to broken access control and security misconfiguration. It provides examples of broken access control including modifying URL parameters to access restricted resources, restricting folder access, and using malicious URLs as parameters. Recommendations are given to implement access controls consistently, limit account data changes to account holders, and log access control failures. Examples of security misconfiguration include using default credentials and configurations, having an overly informative error handling, and leaving unnecessary features enabled. Recommendations include removing unused features, sending secure headers, not using default configurations, and properly configuring robots.txt files. Links to additional resources on these topics are also provided.