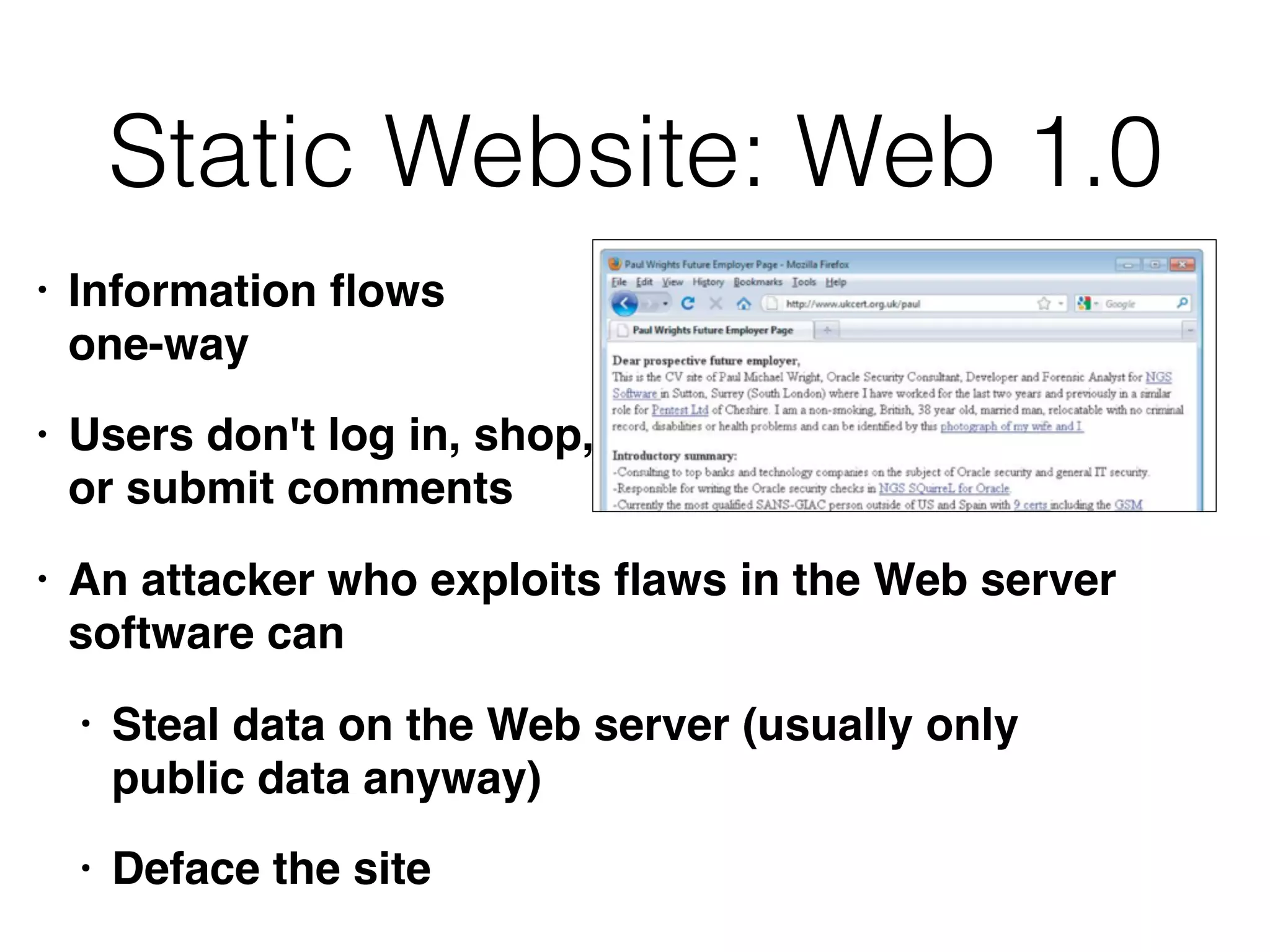
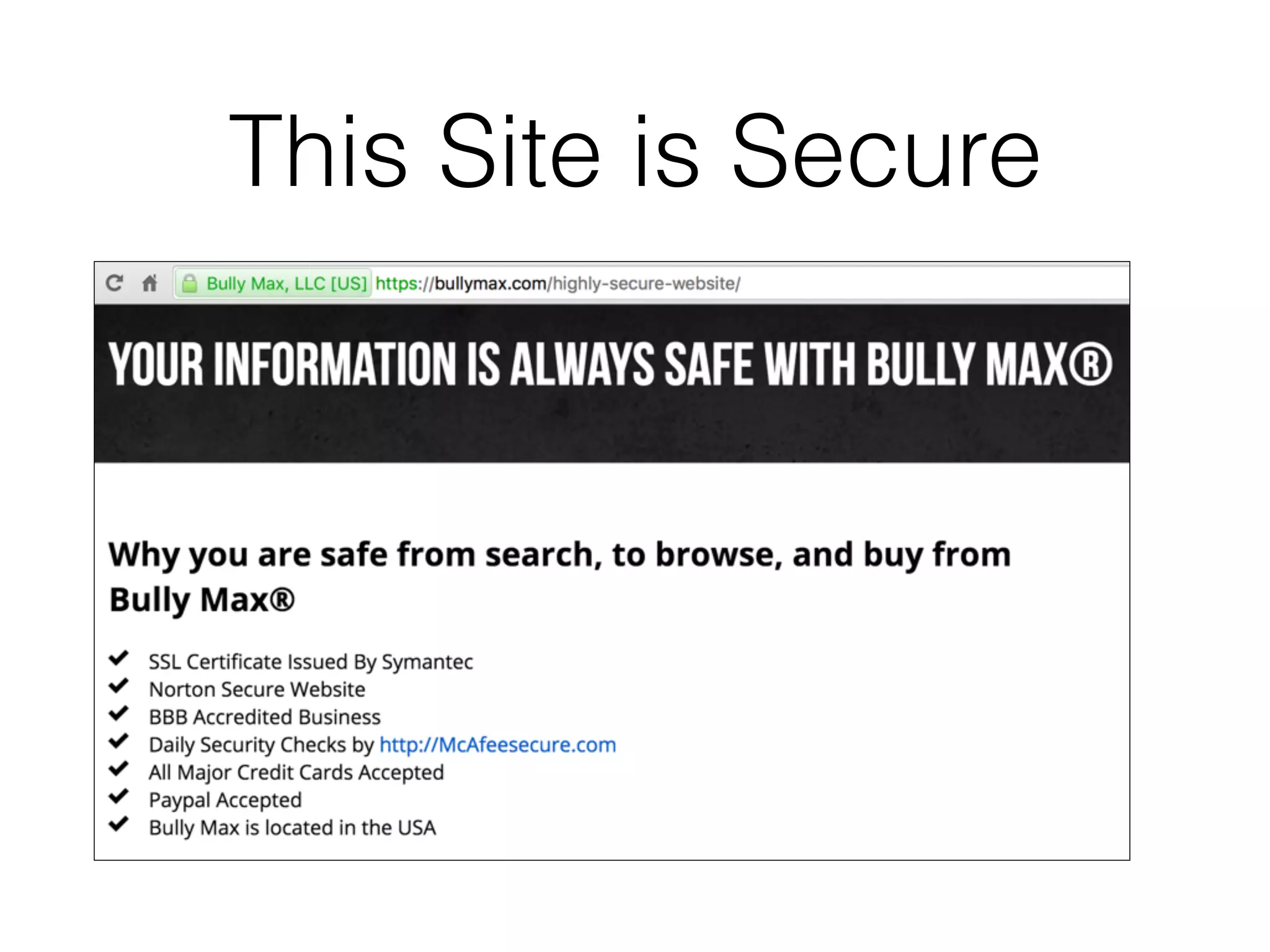
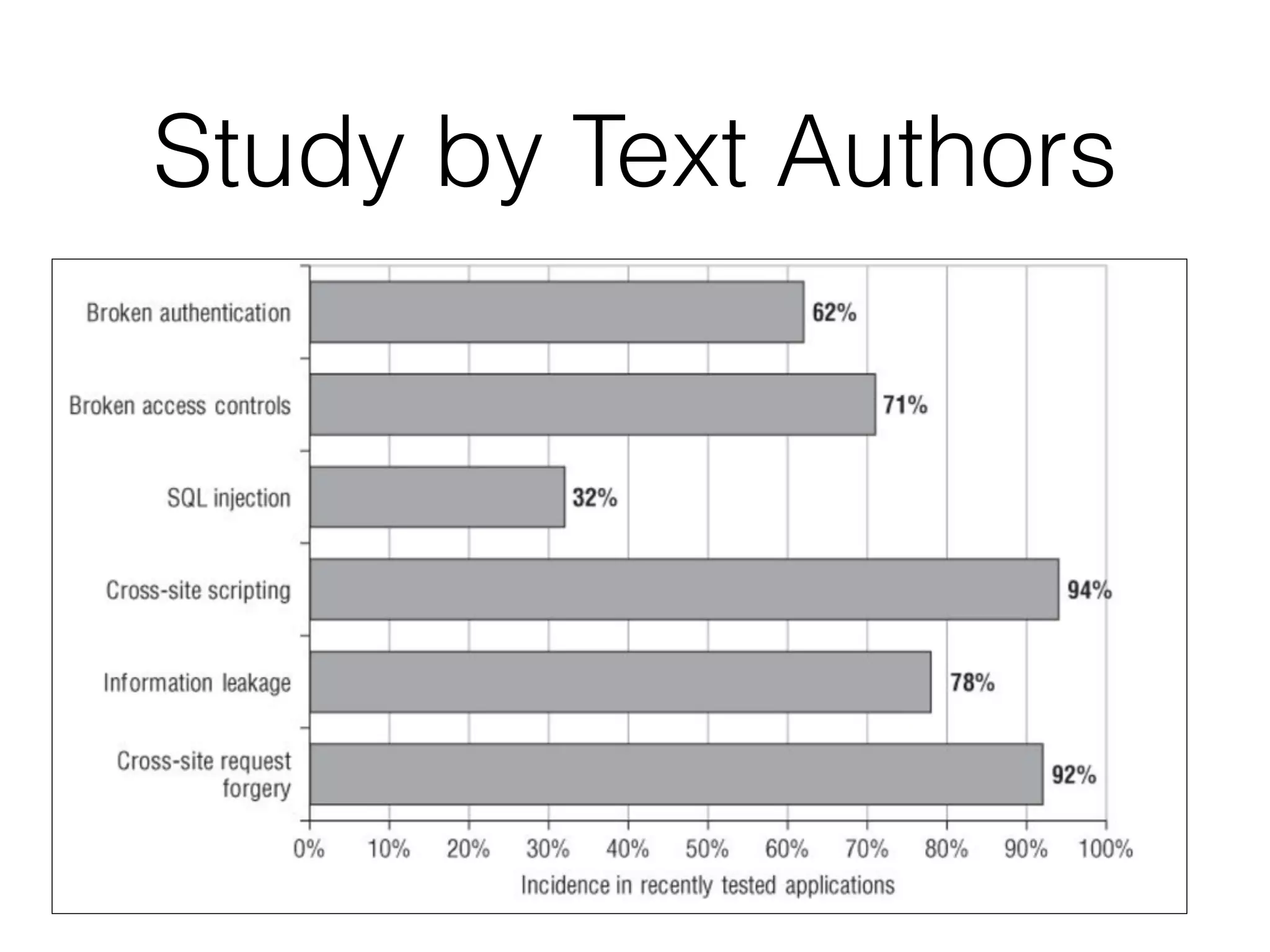
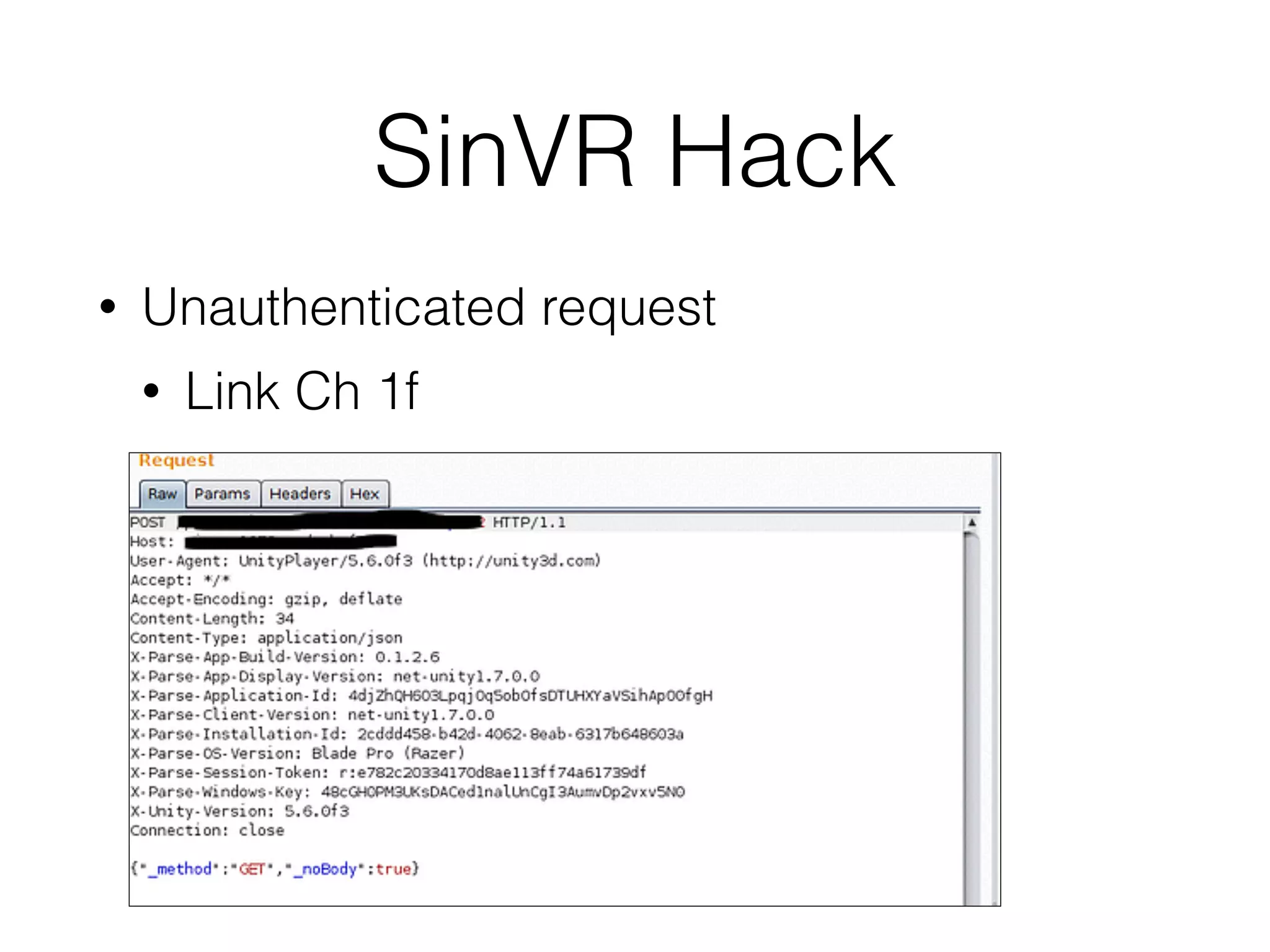
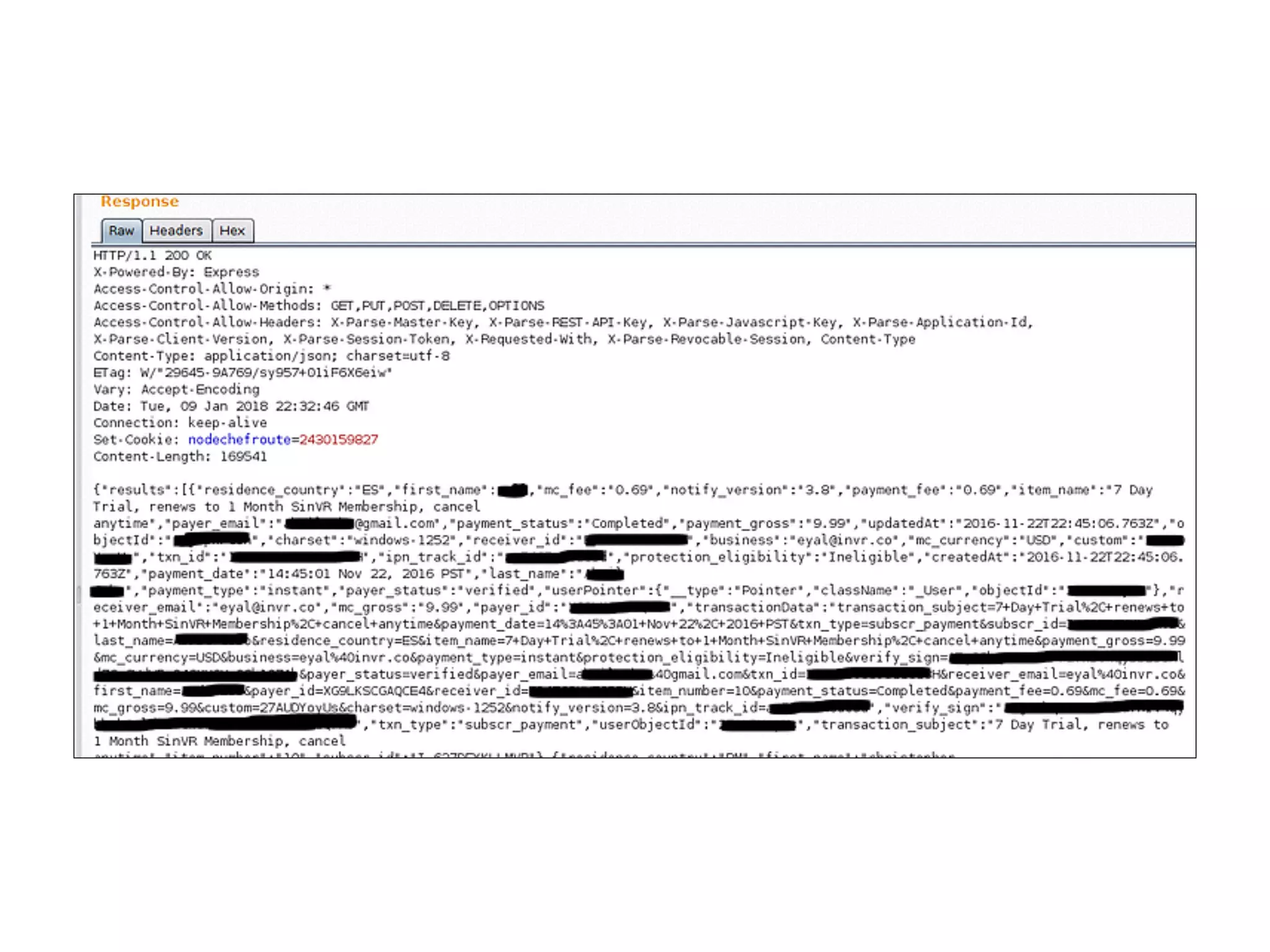
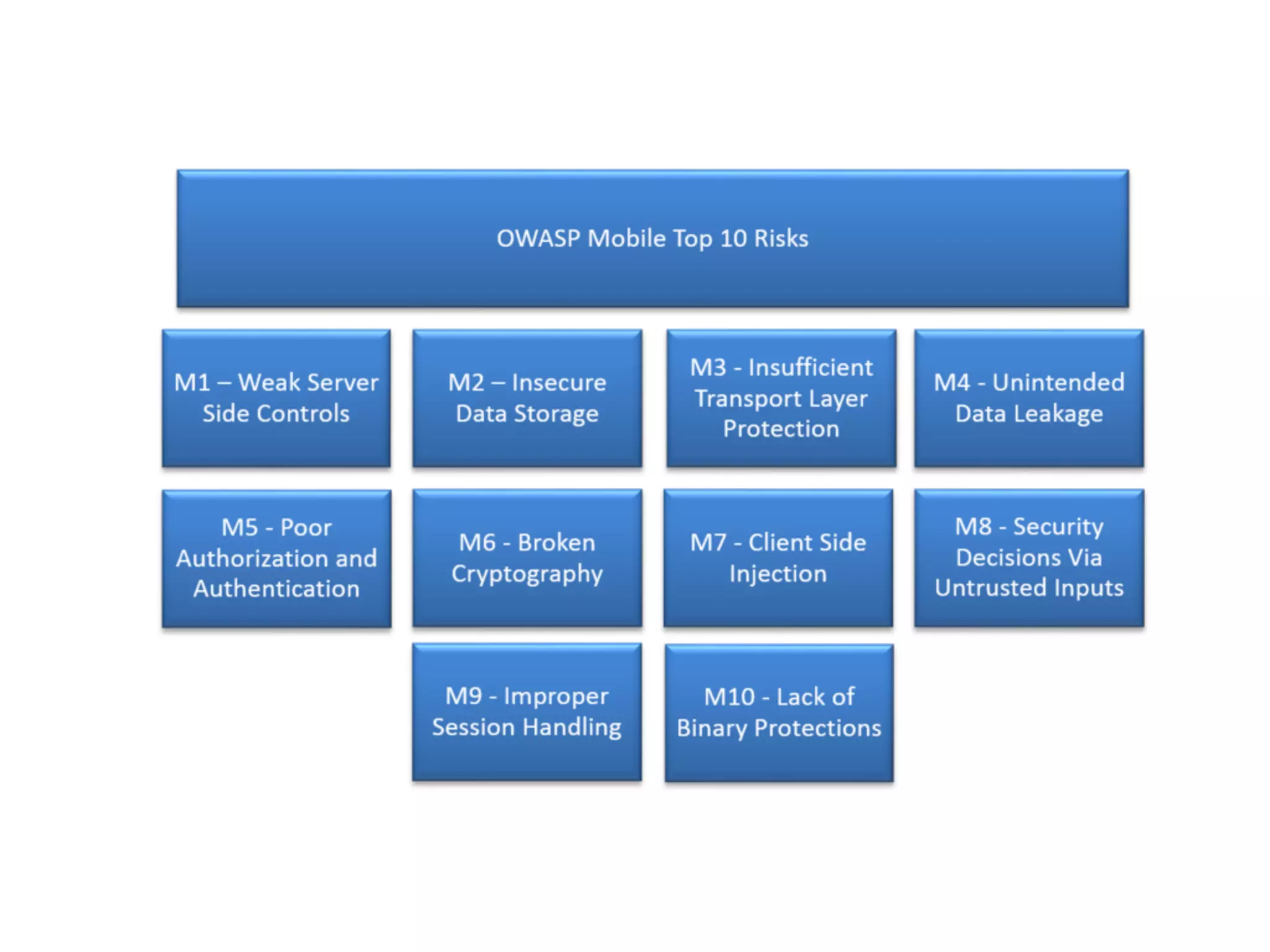
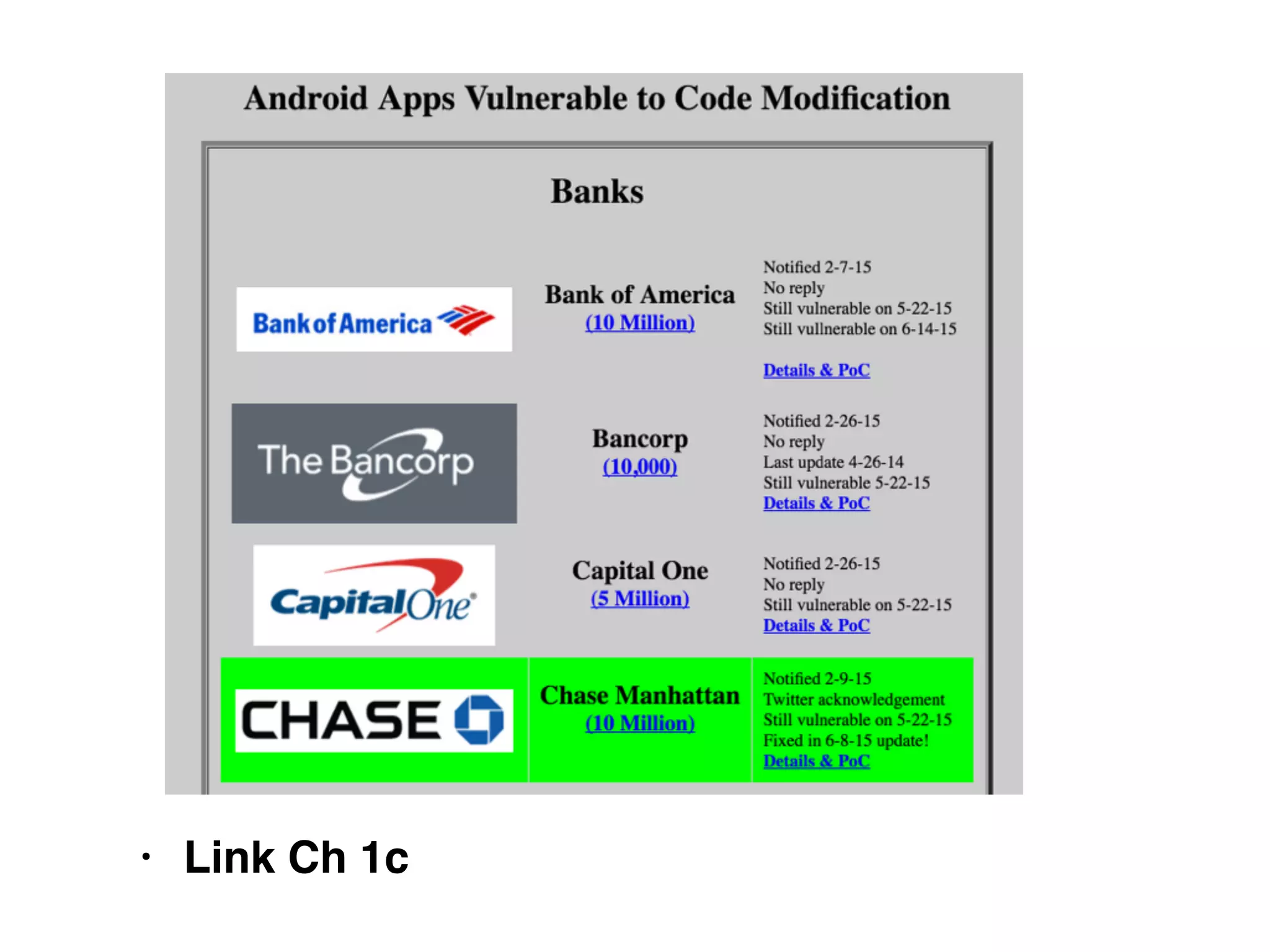
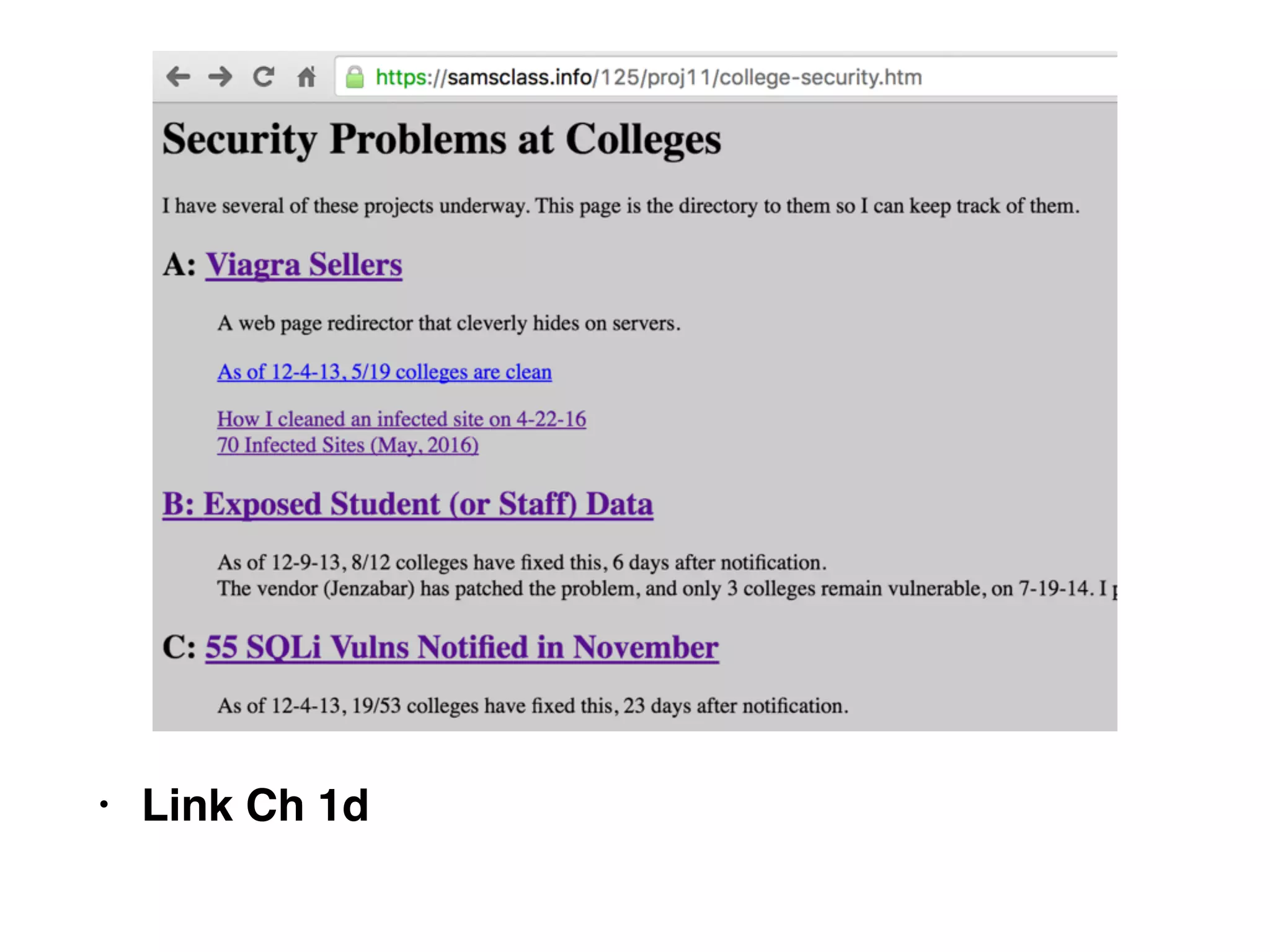
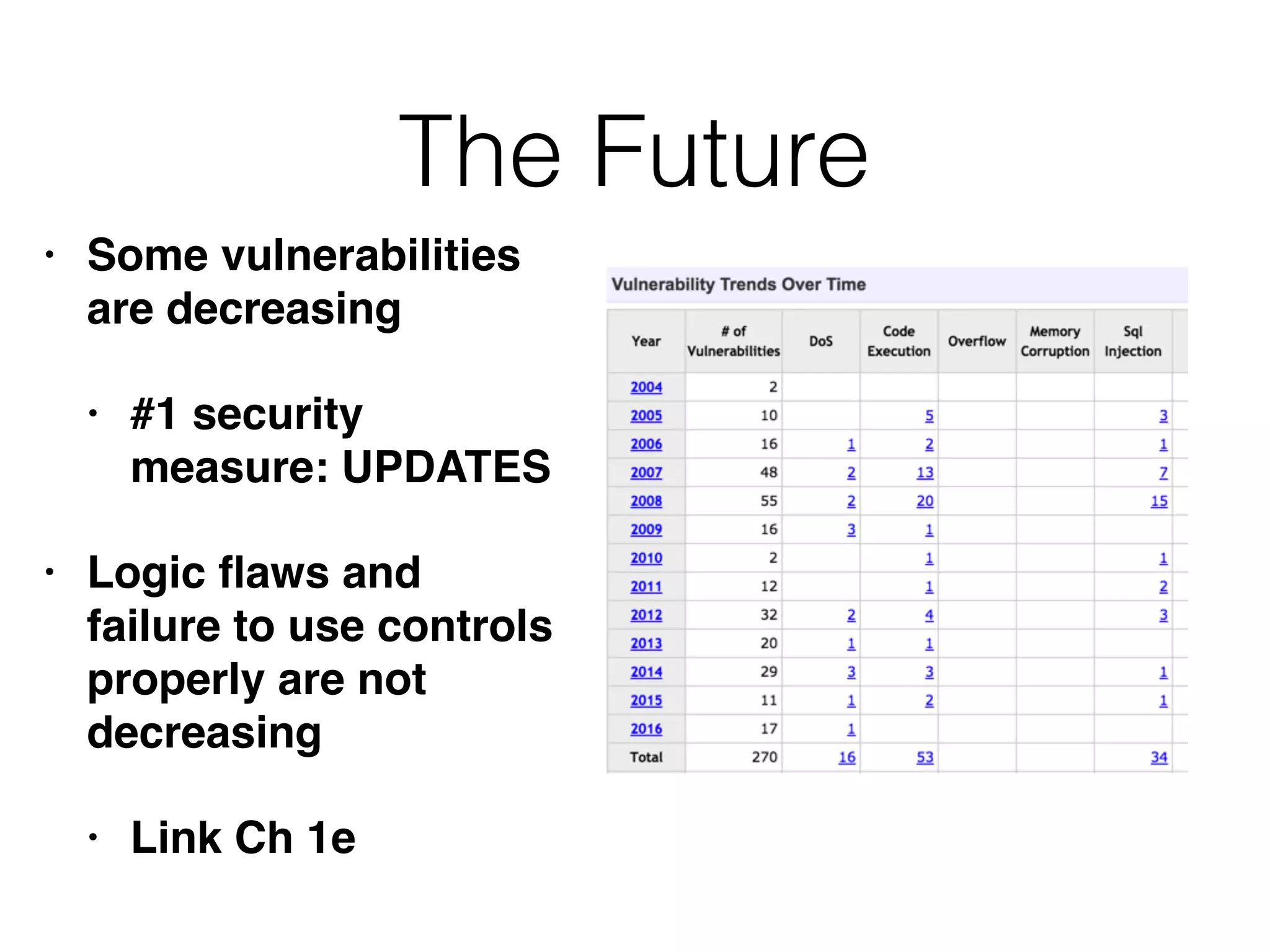
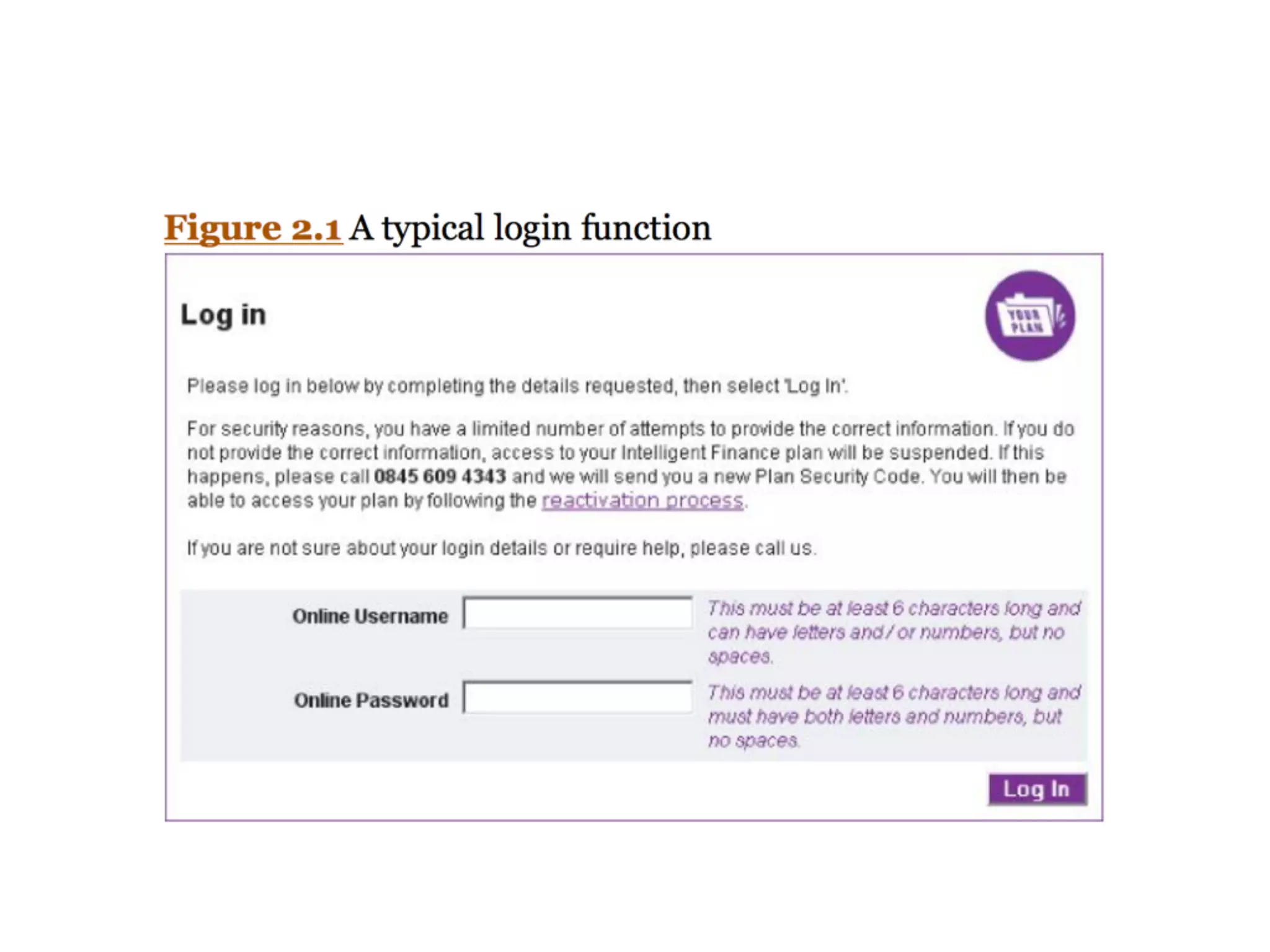
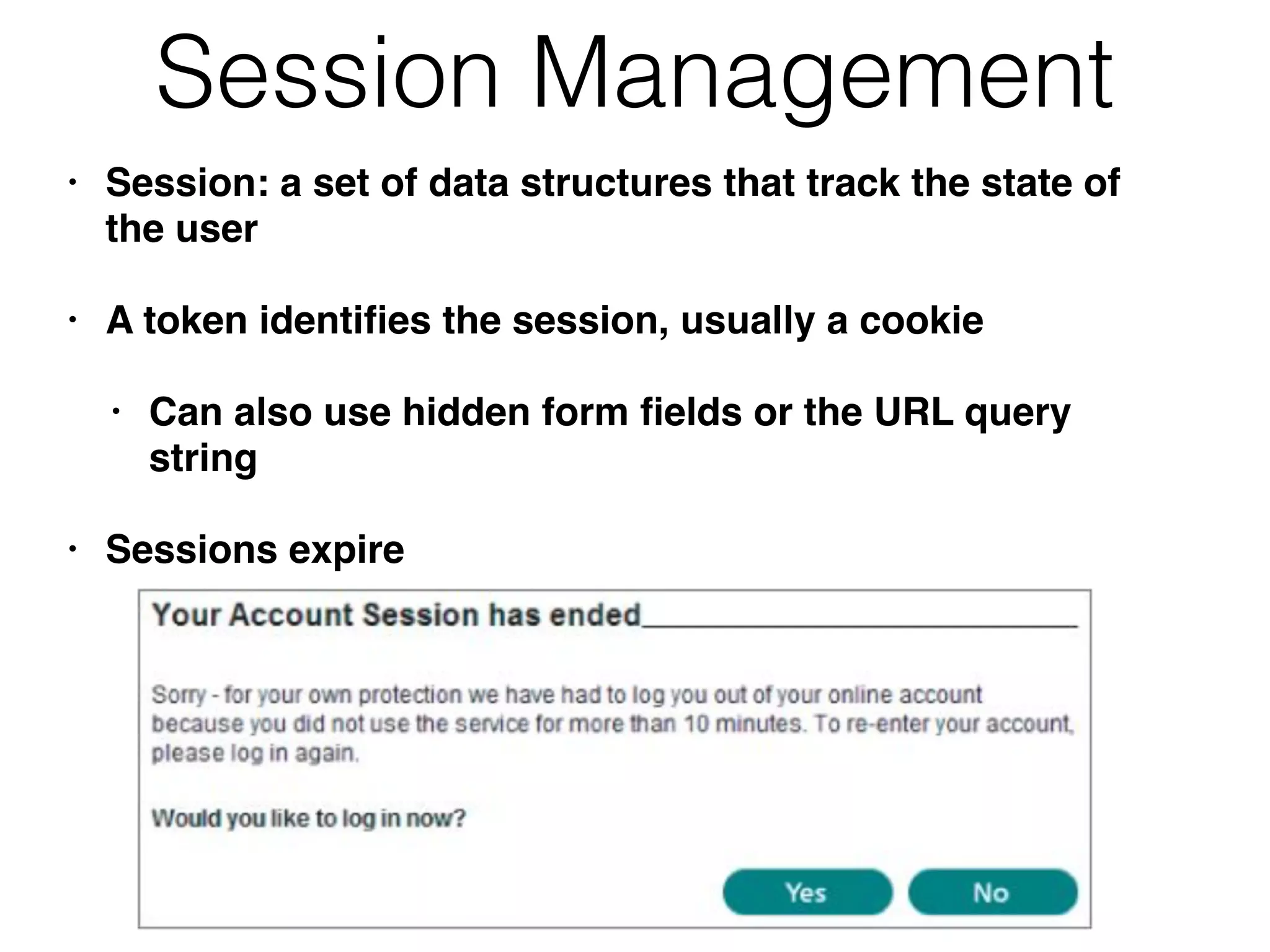
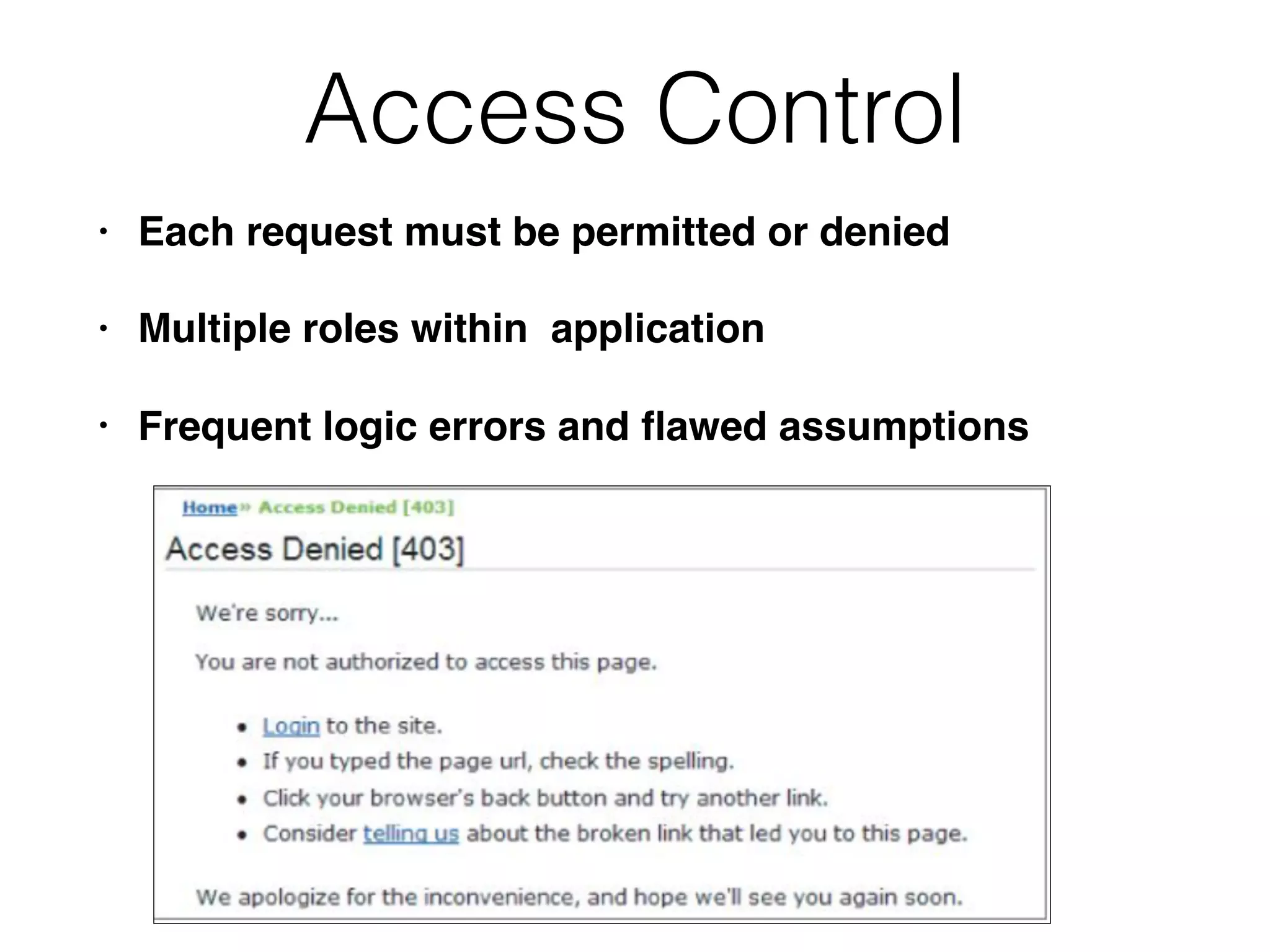
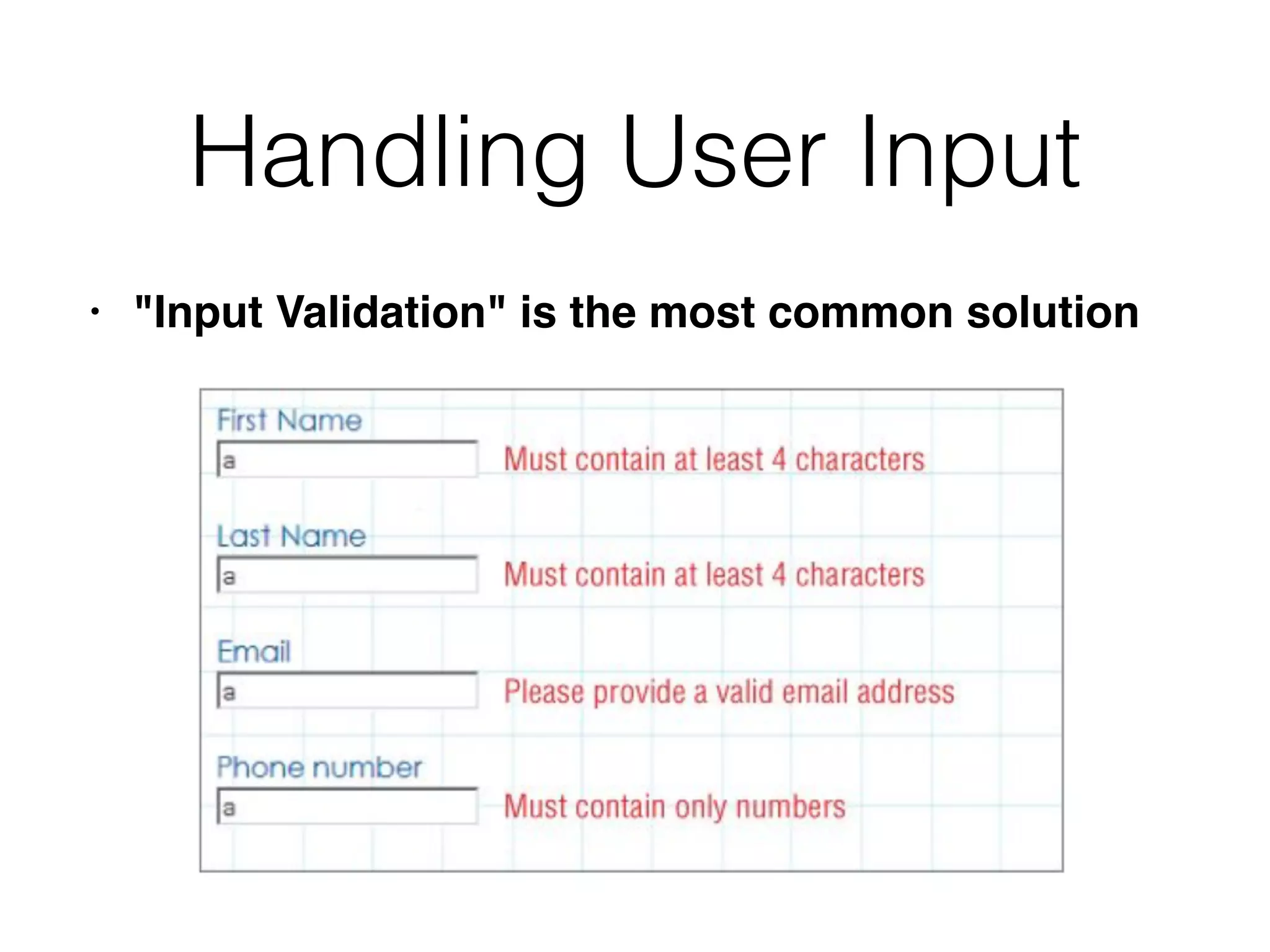
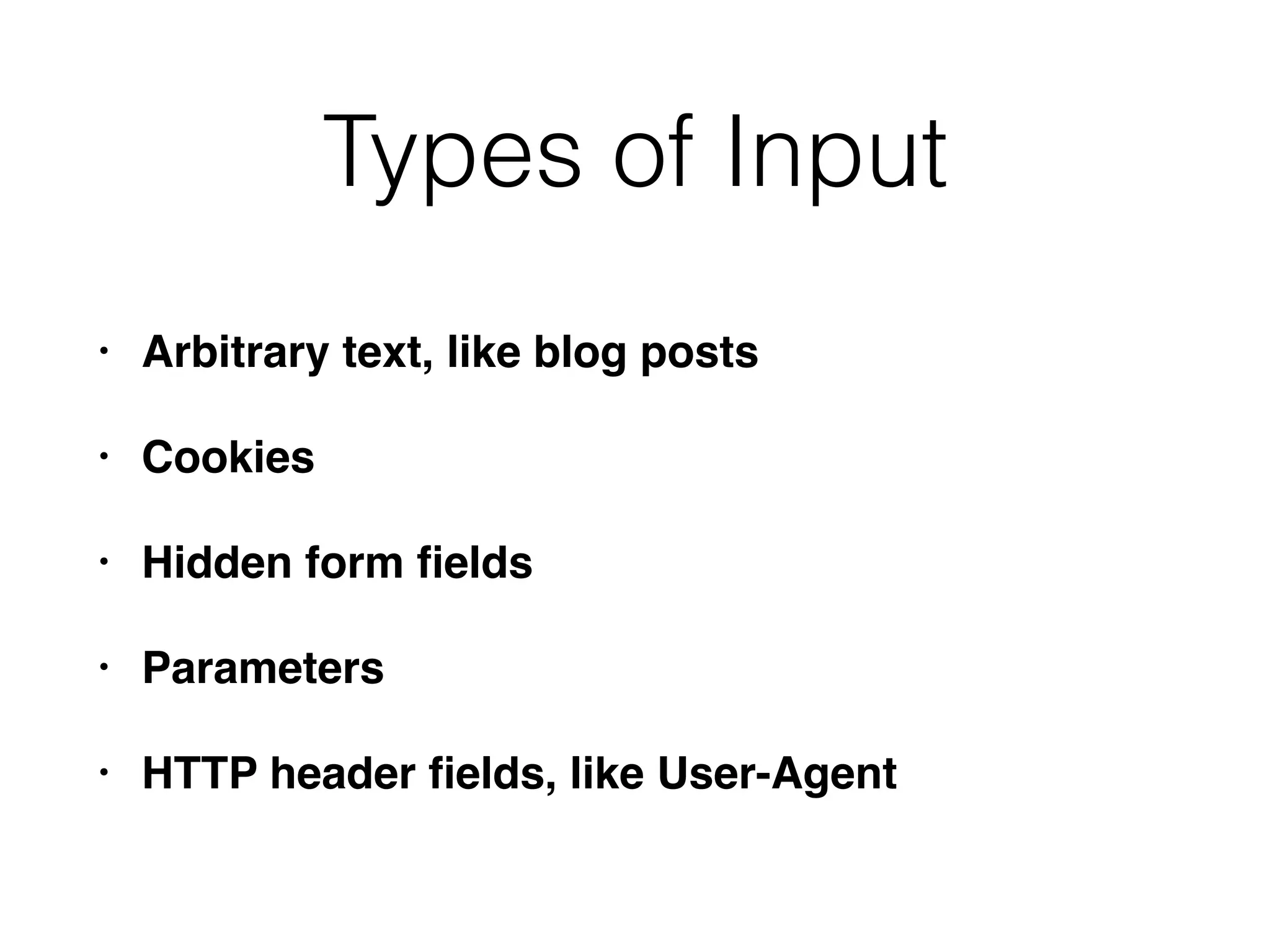
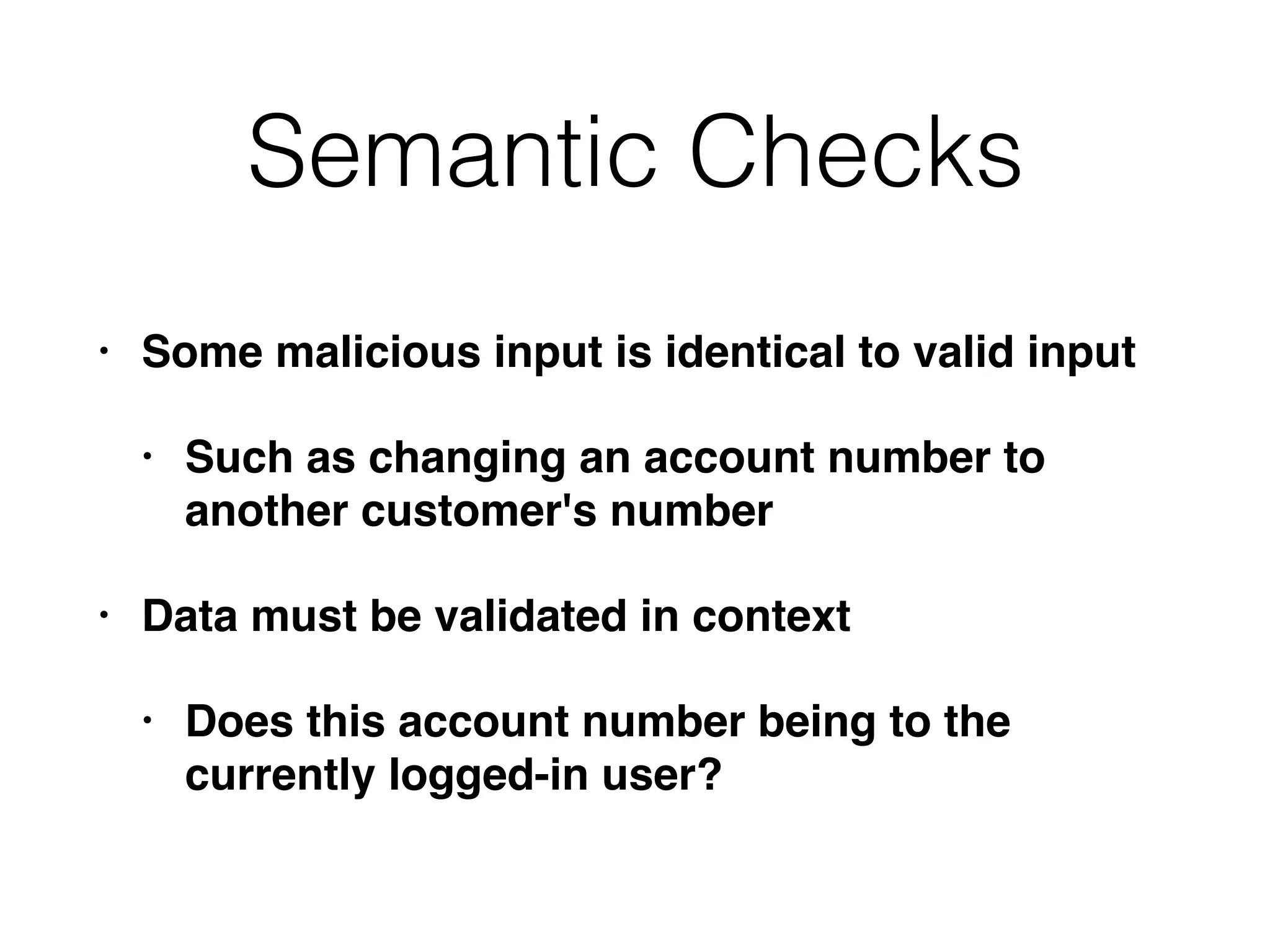
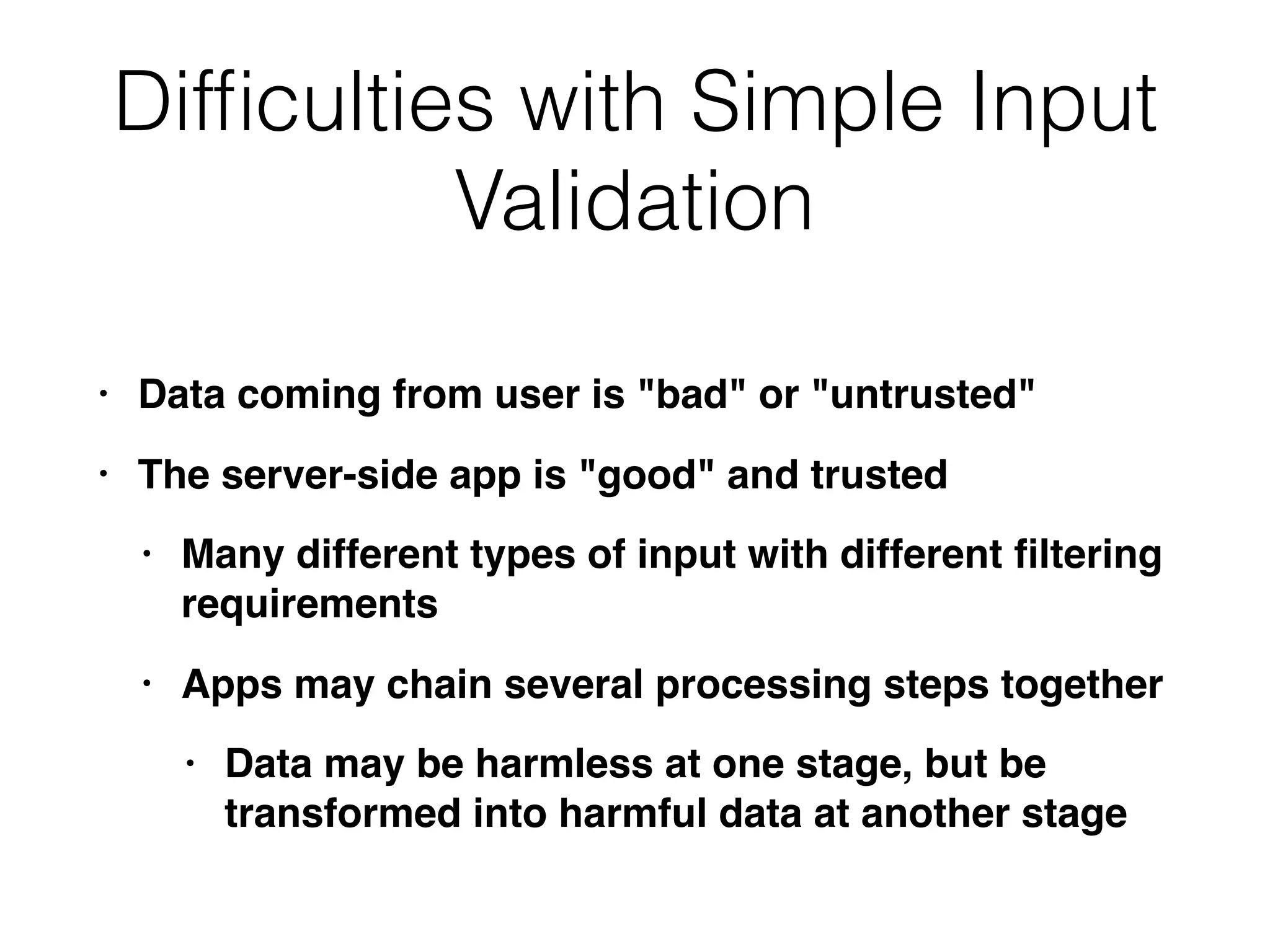
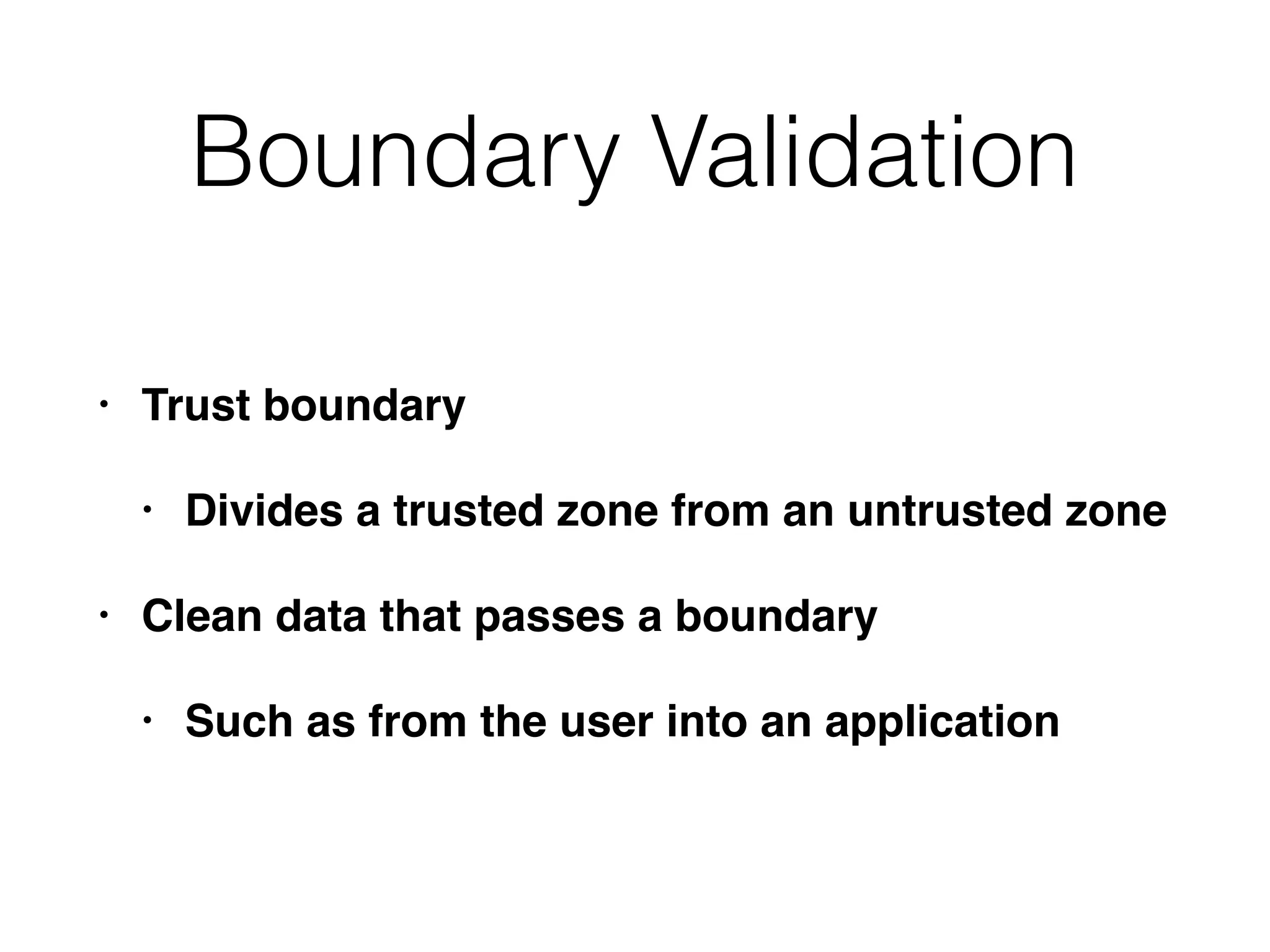
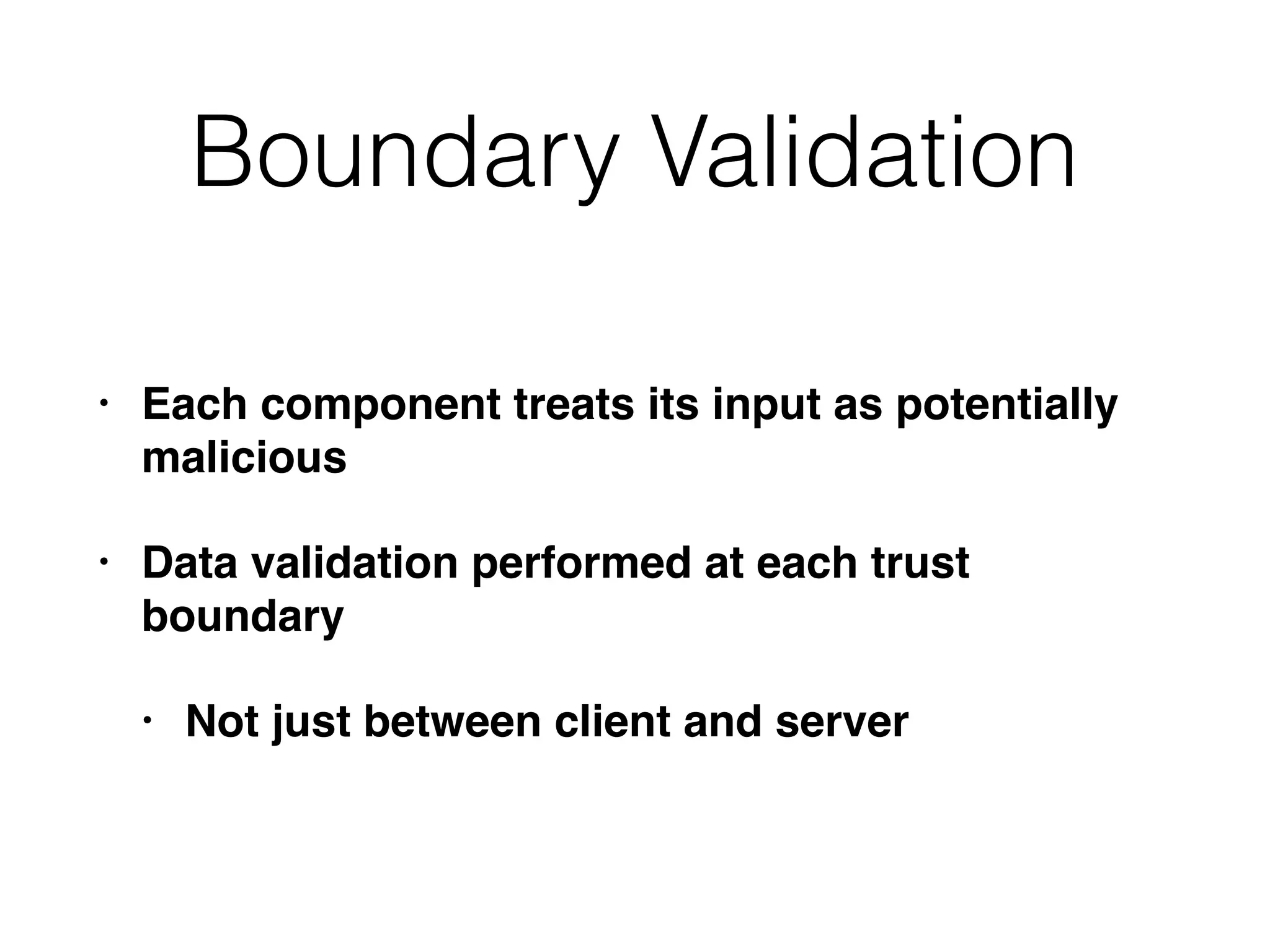
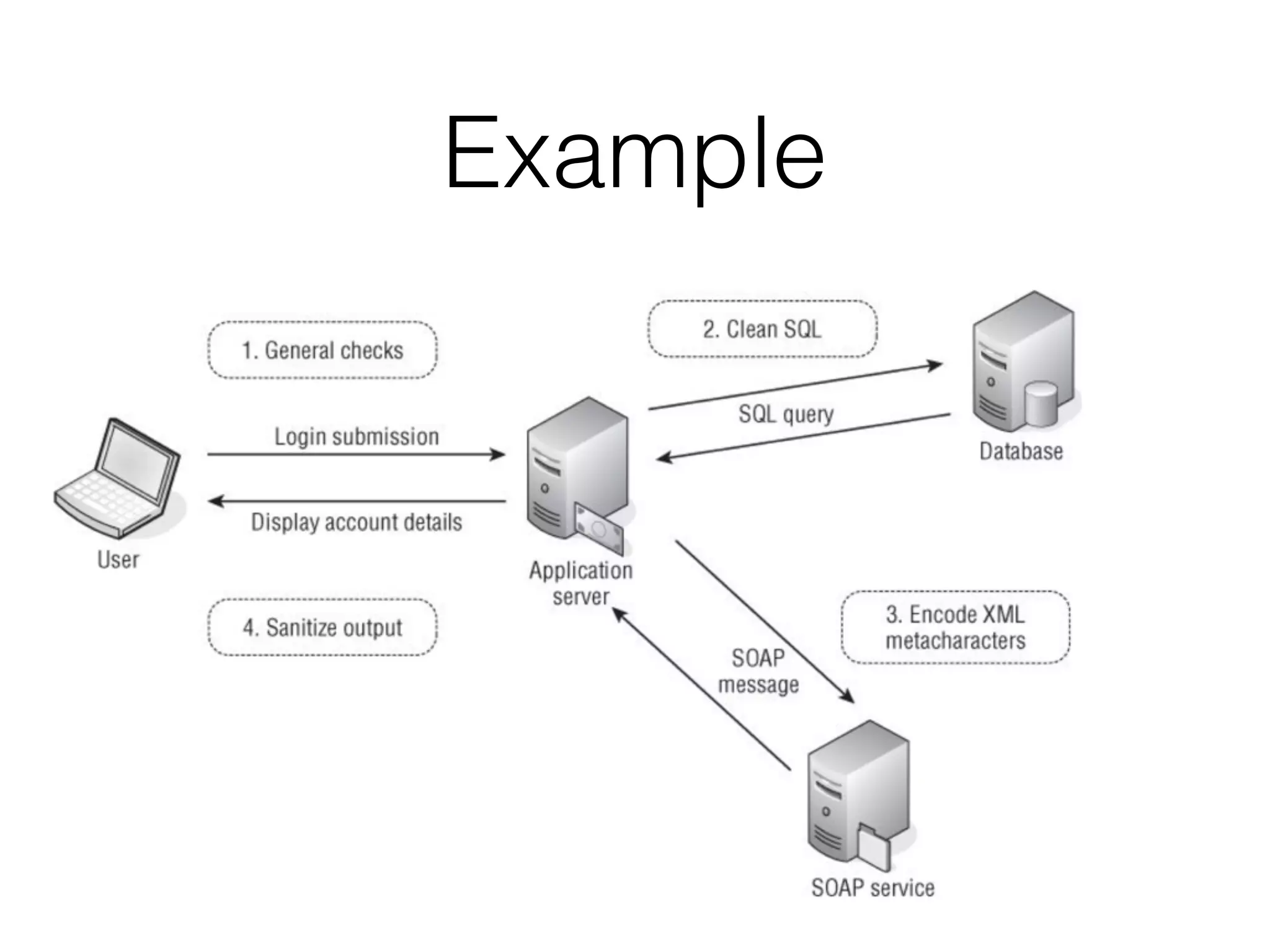
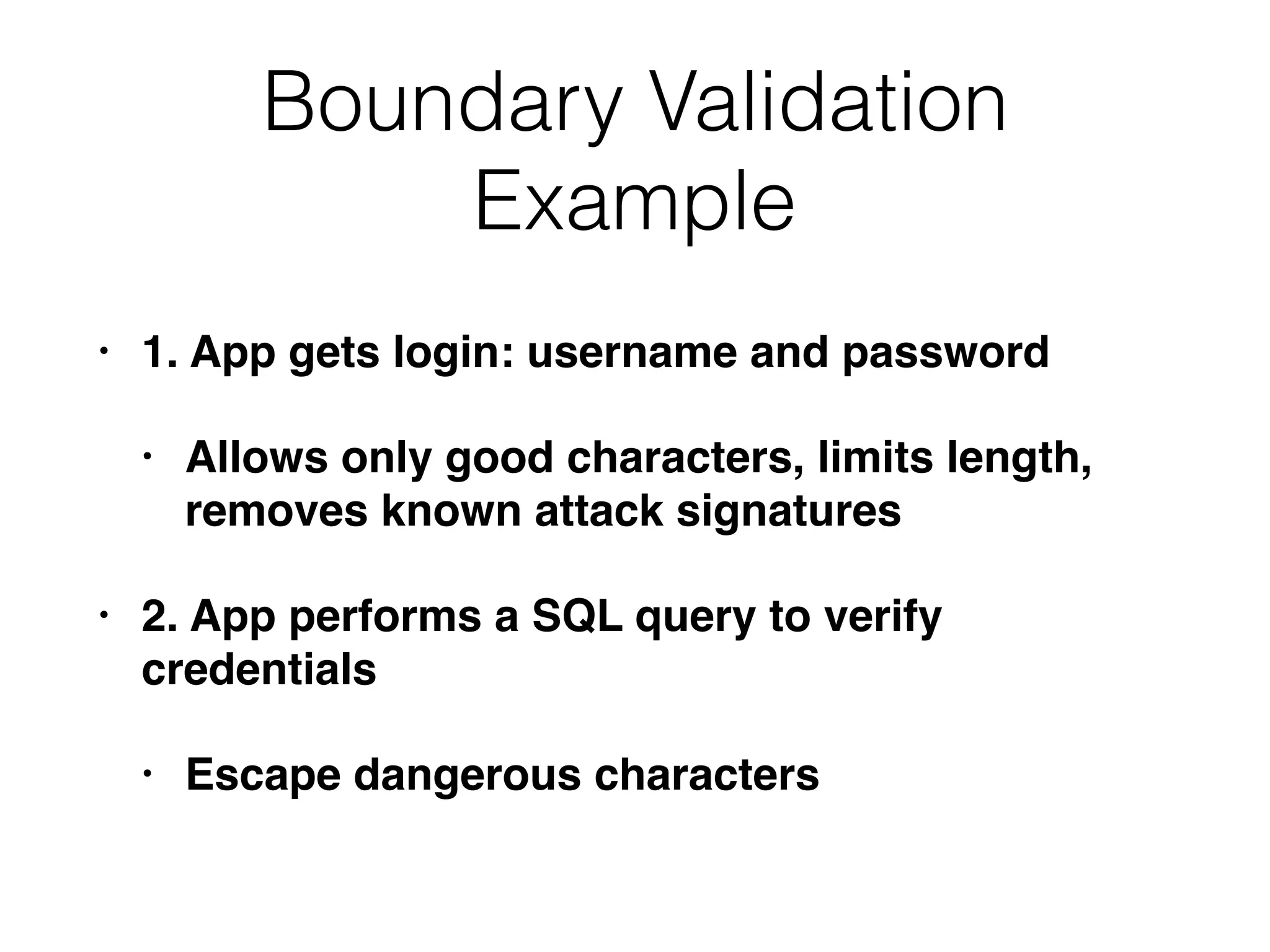
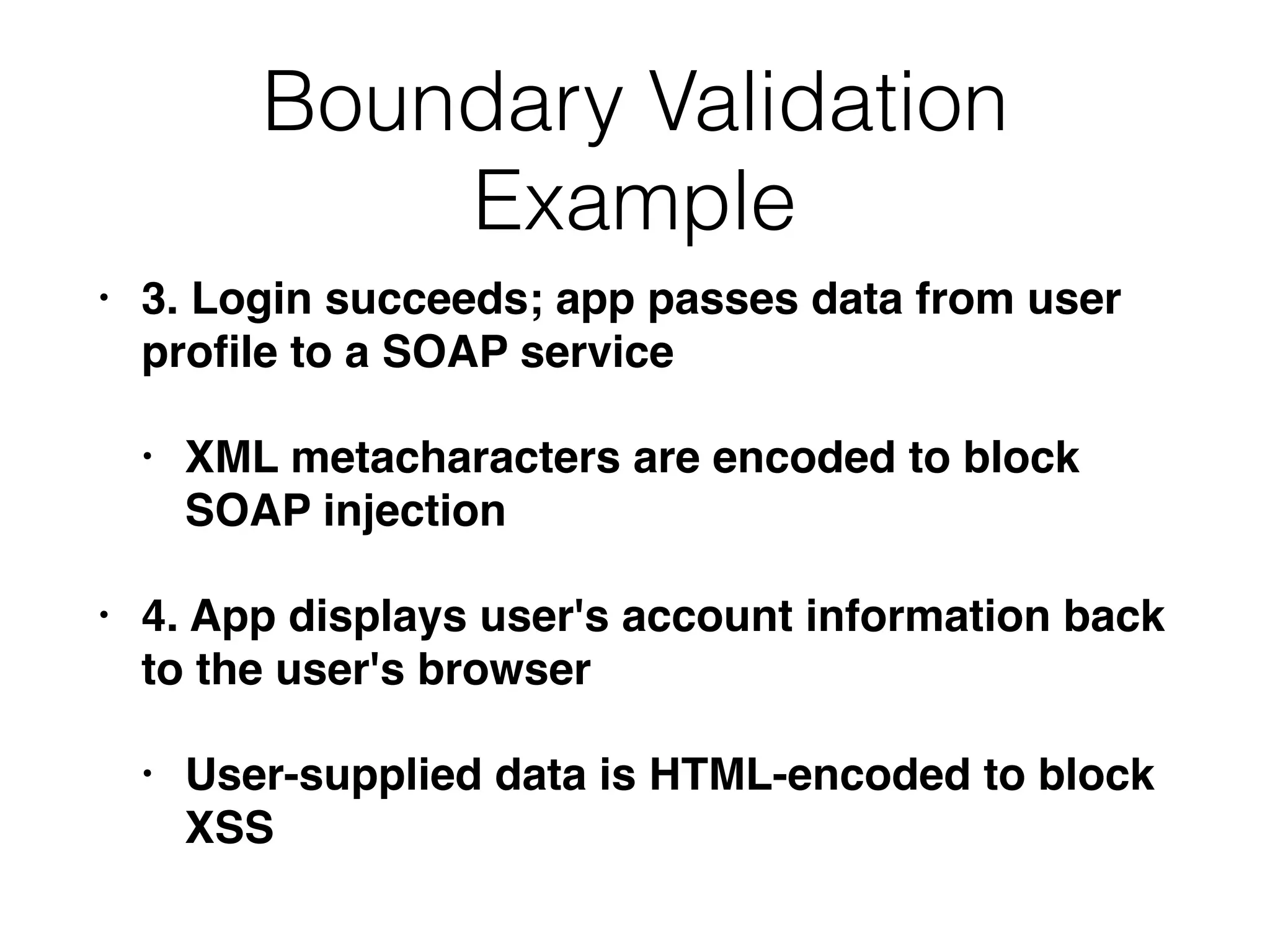
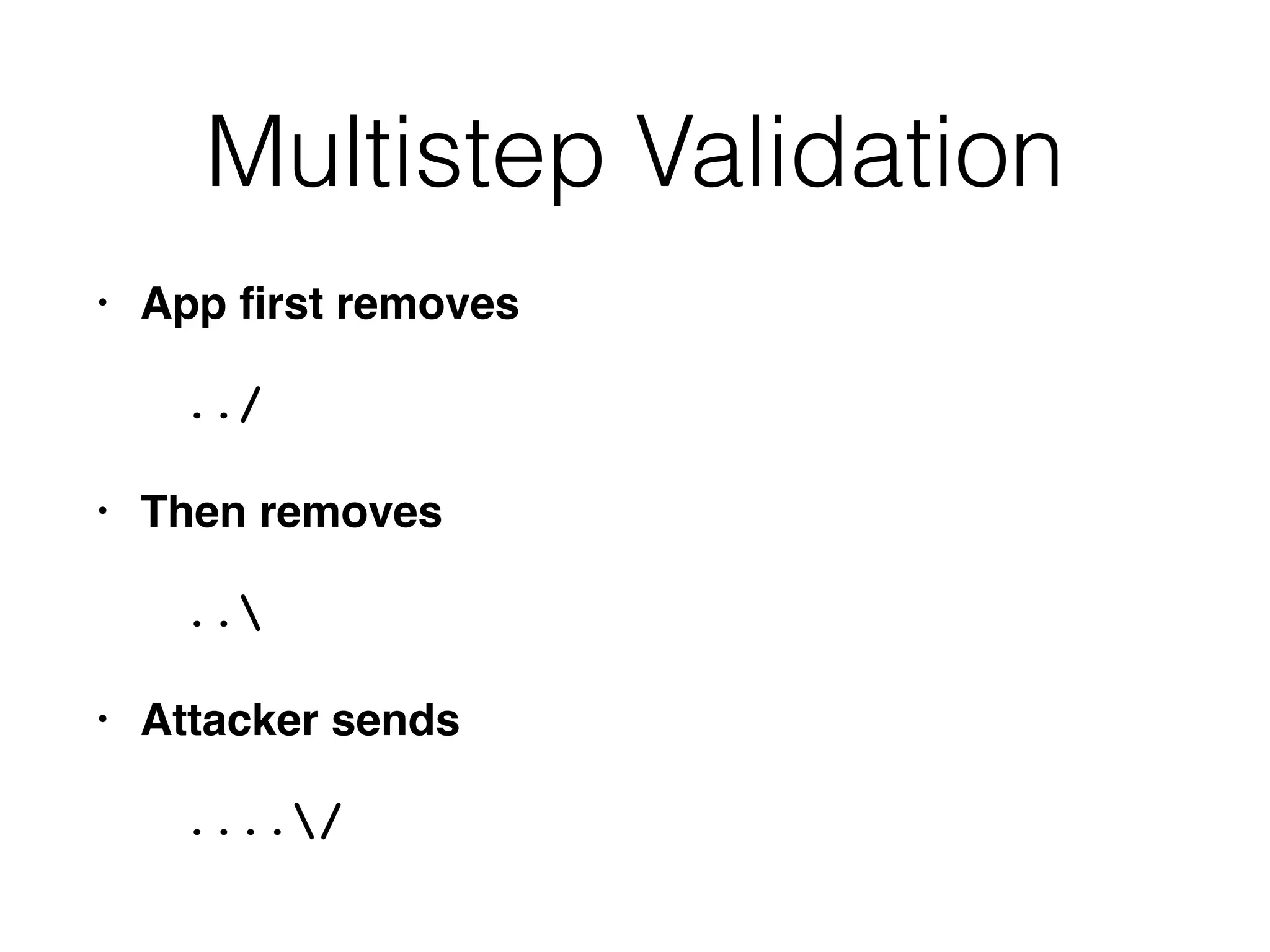
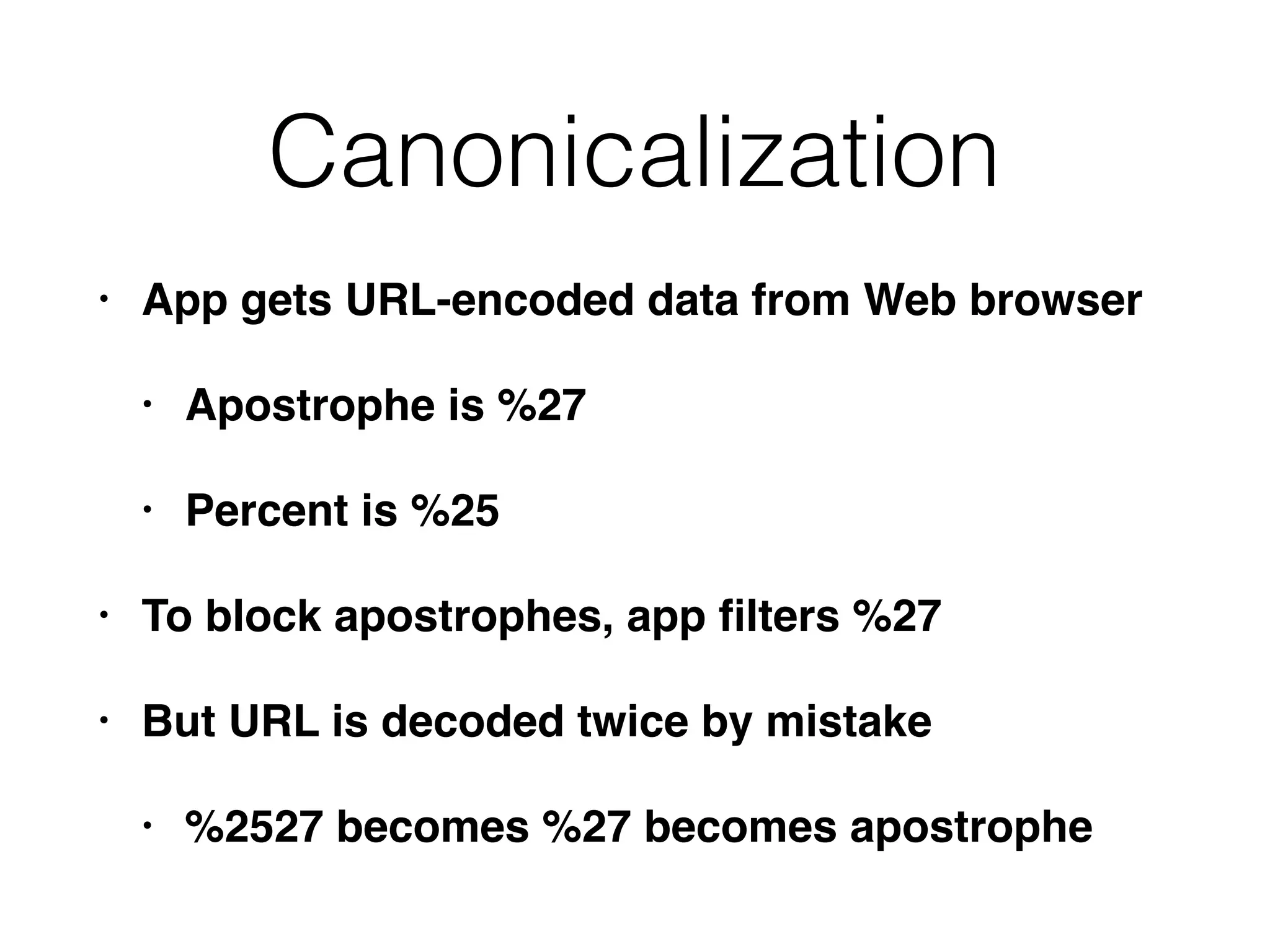
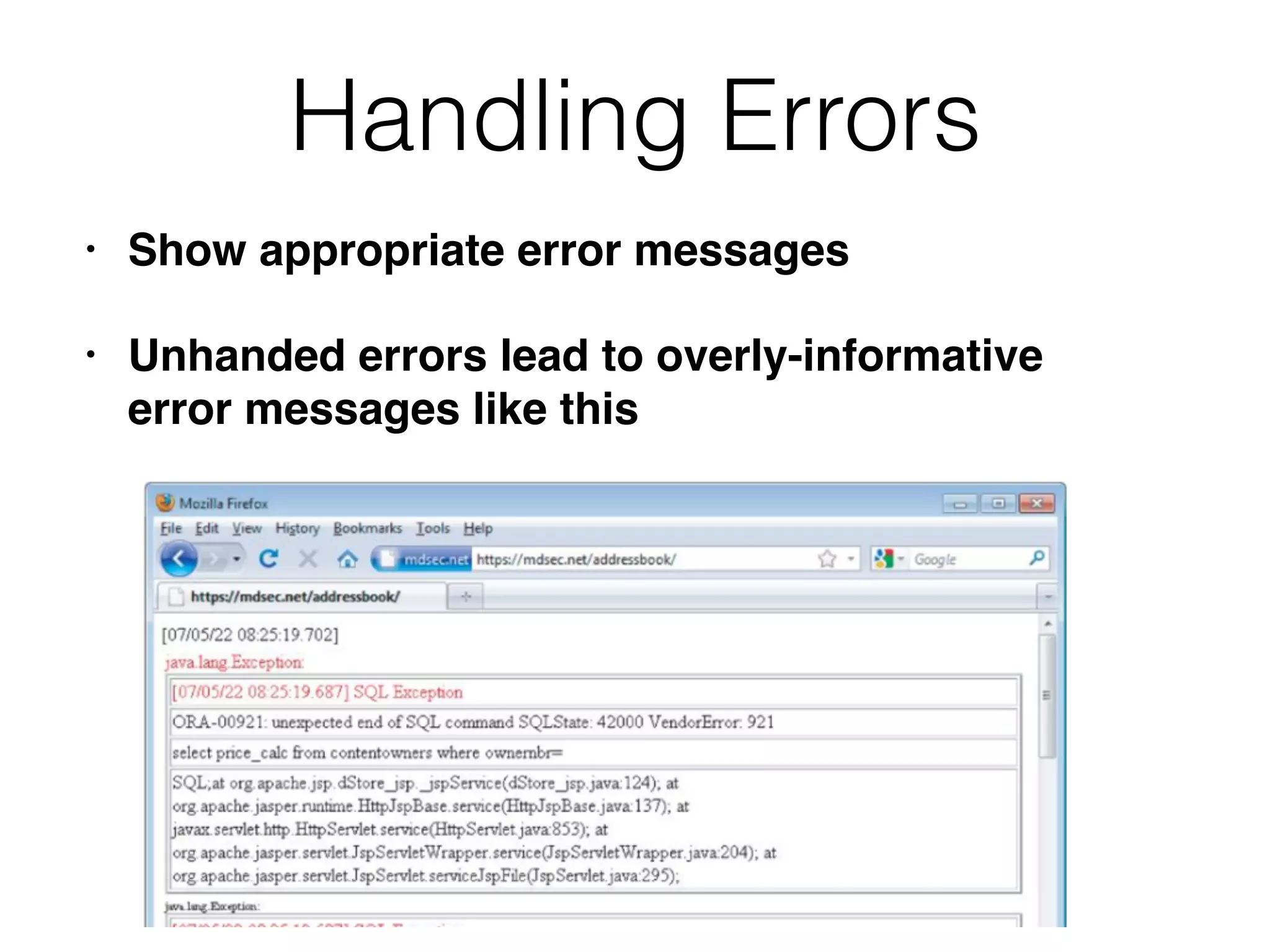
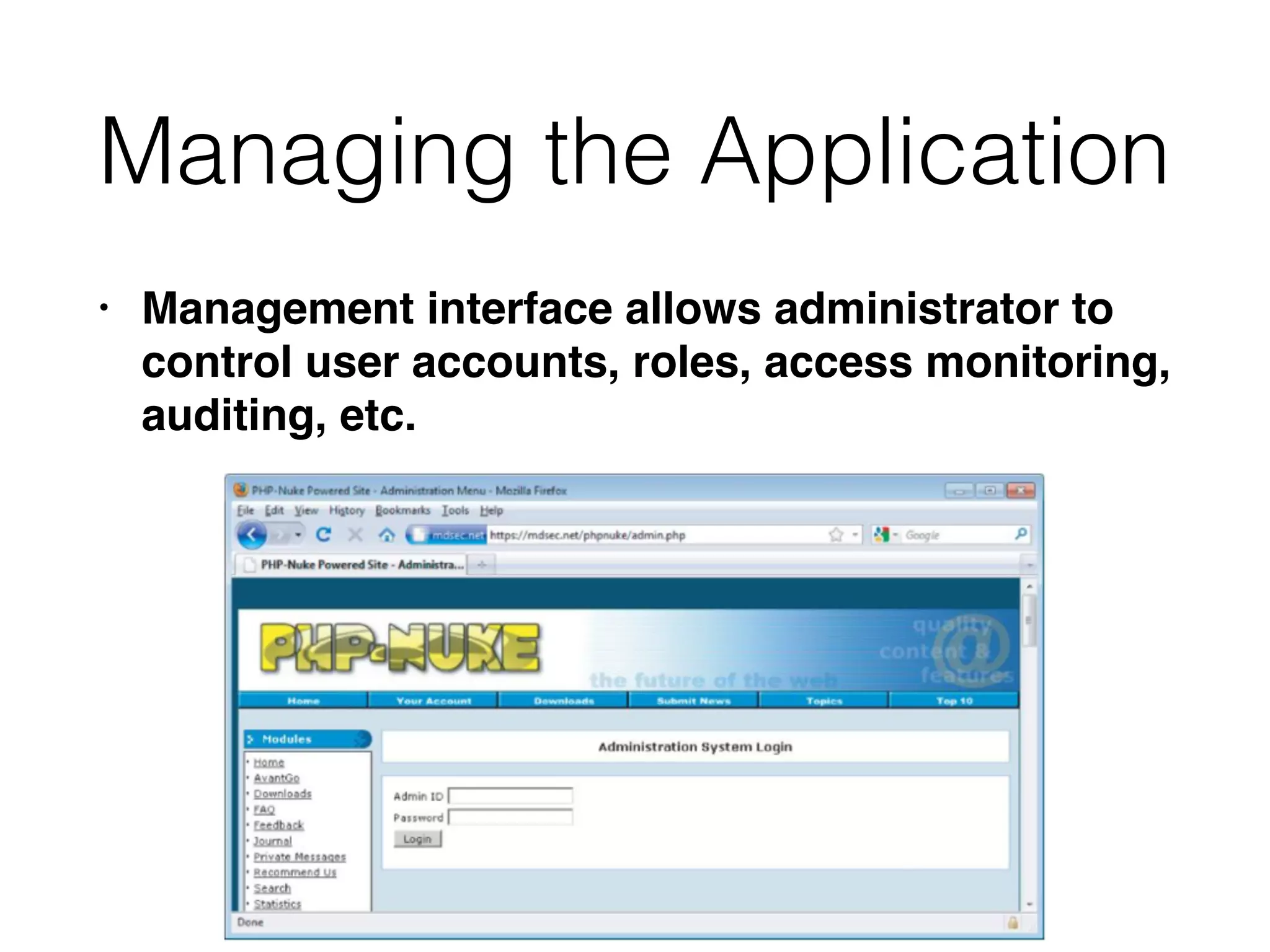
The document discusses the vulnerabilities of web applications, highlighting the dangers of arbitrary user input which can lead to security breaches such as data theft and unauthorized access. It outlines the evolution from static websites to dynamic web applications that require robust security measures, including user authentication, session management, and input validation to mitigate risks. Key security strategies involve limiting access, sanitizing input, performing boundary validation, and maintaining comprehensive audit logs to detect and react to potential threats.