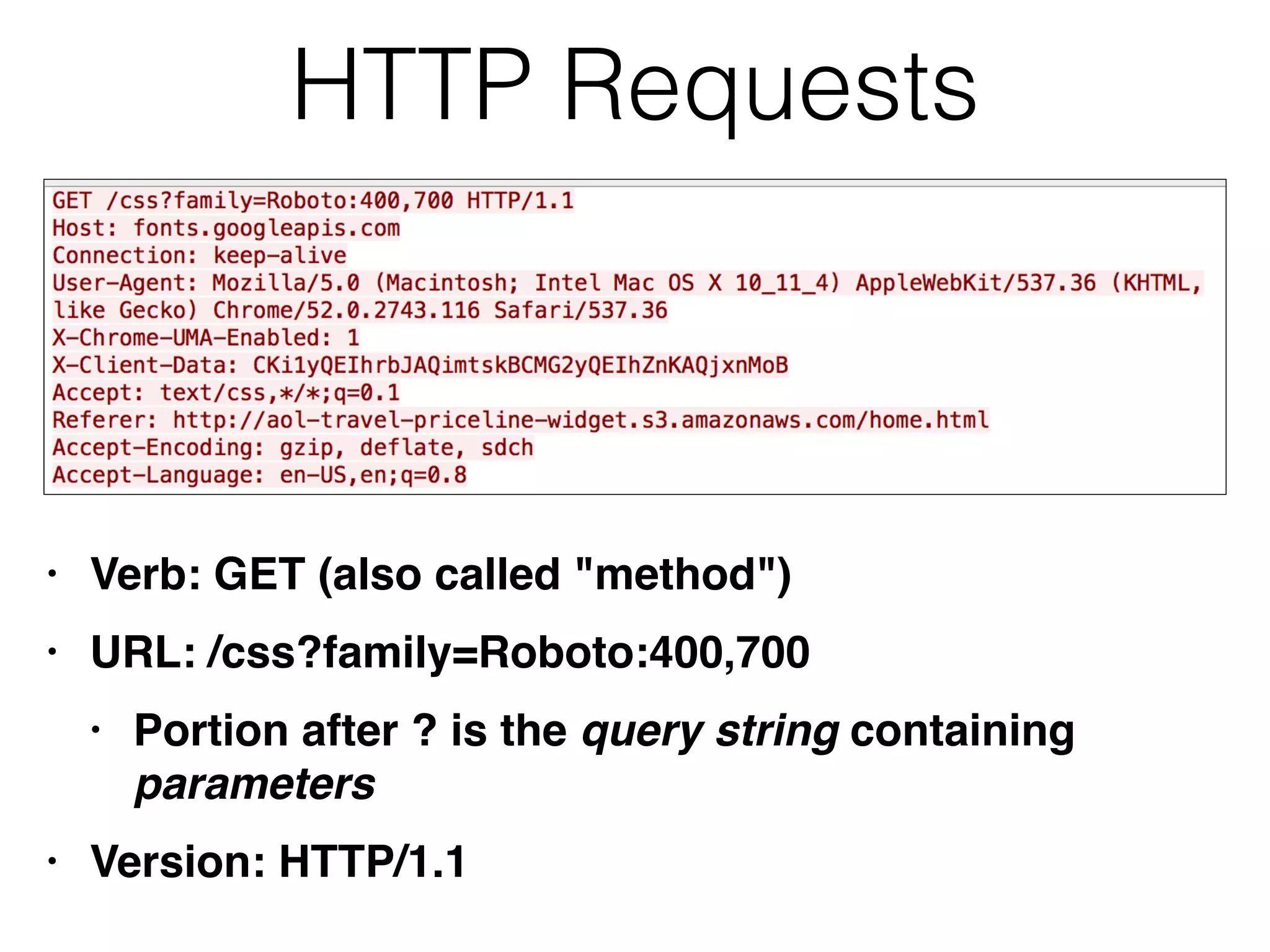
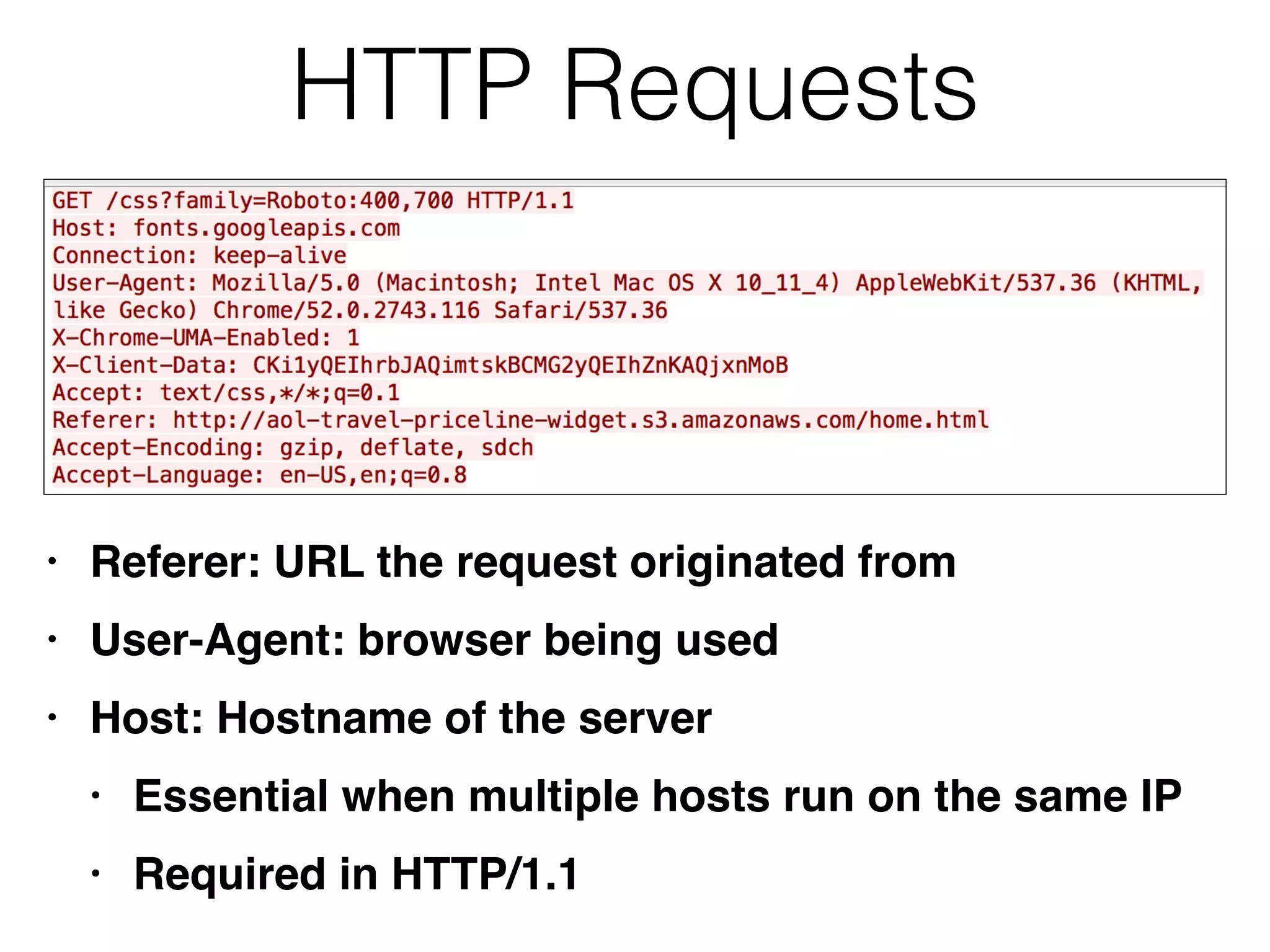
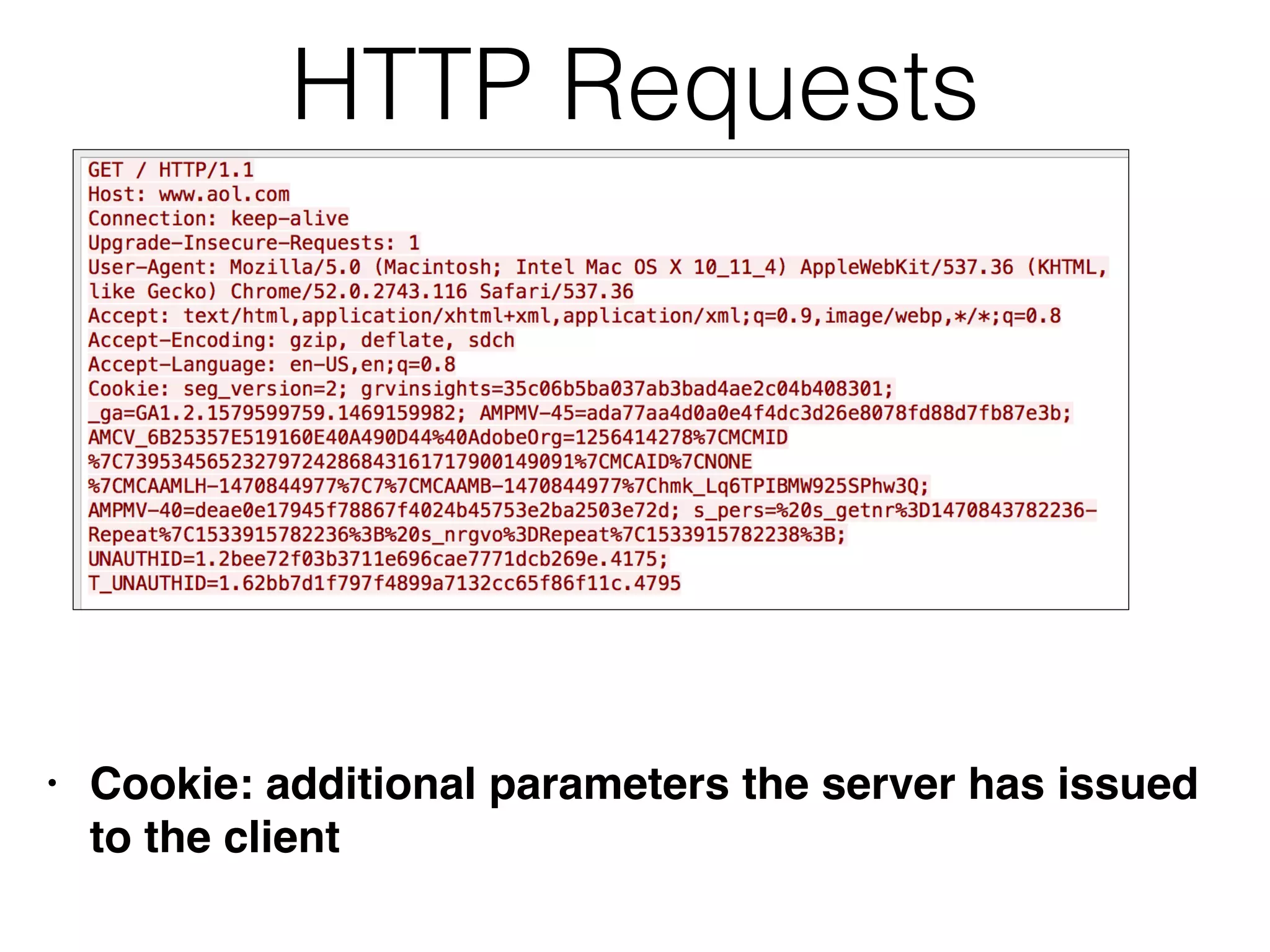
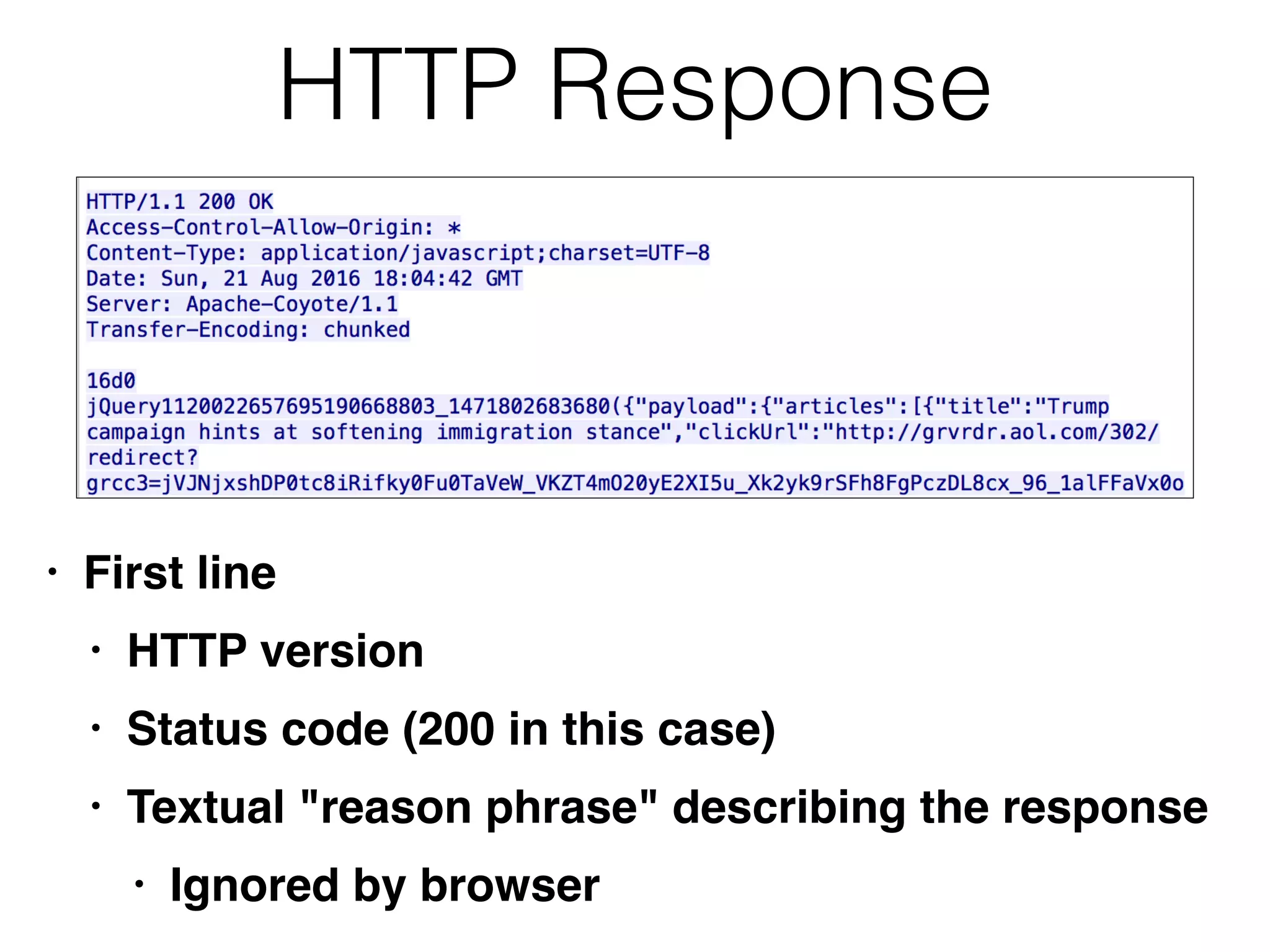
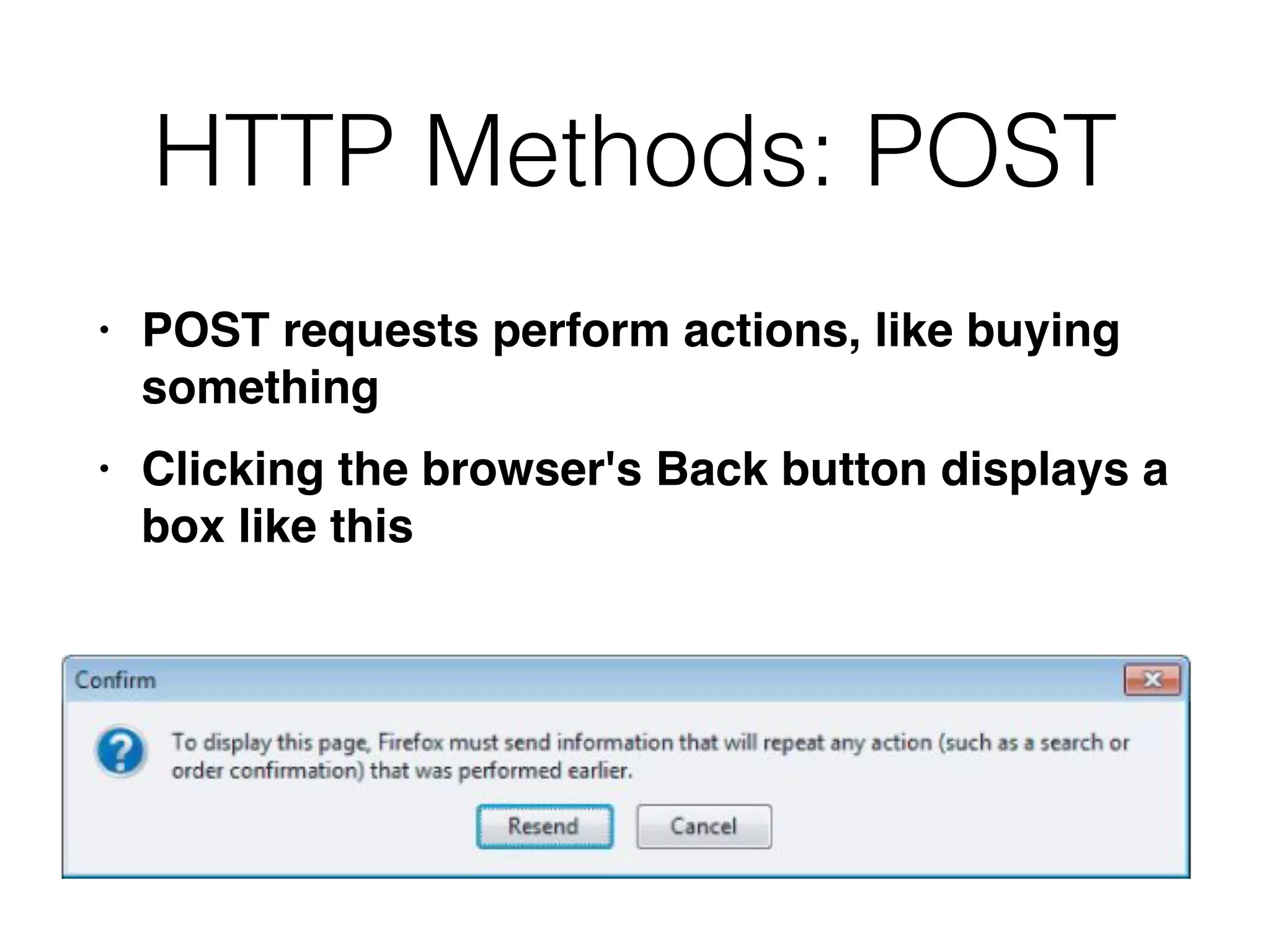
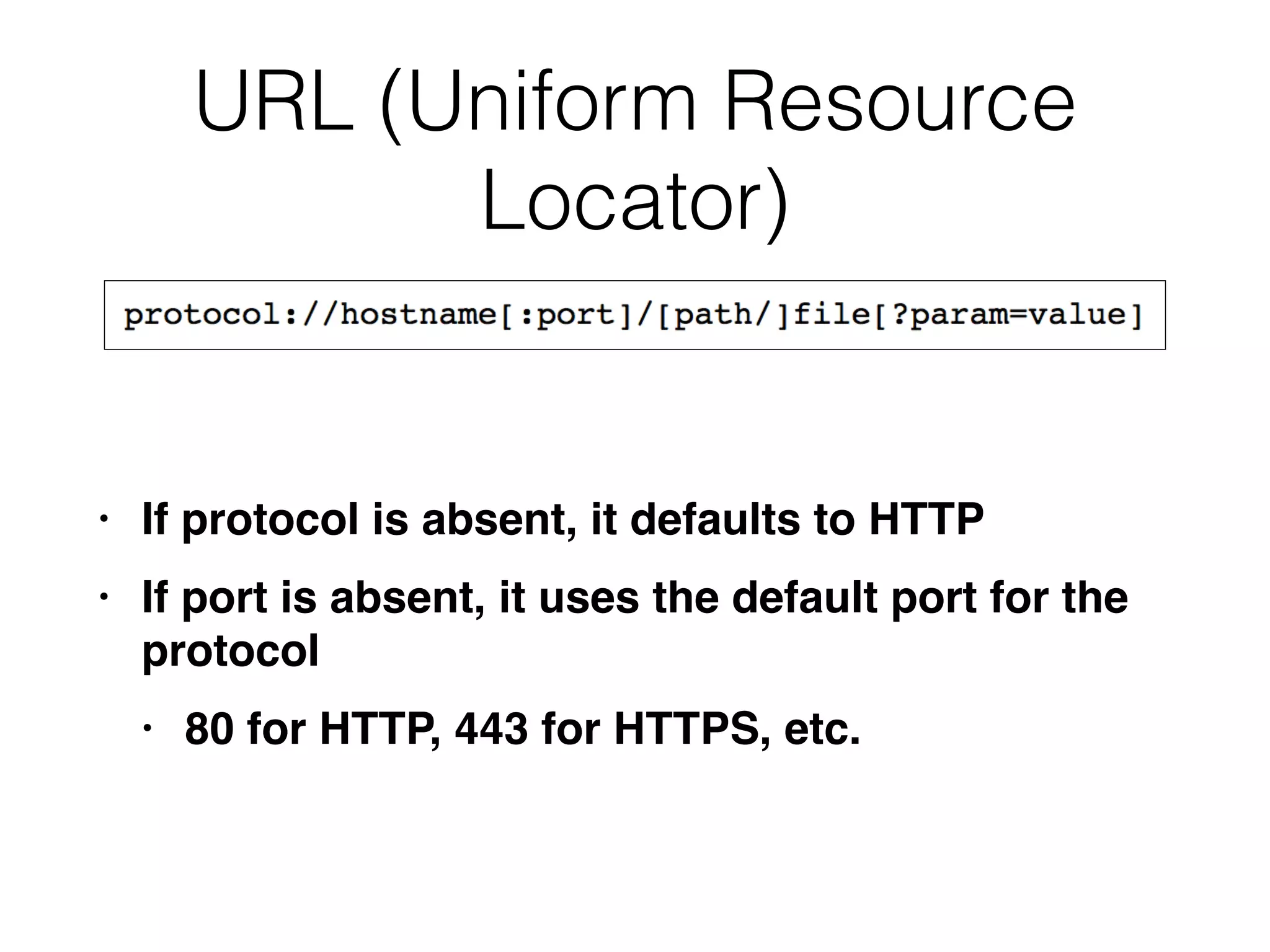
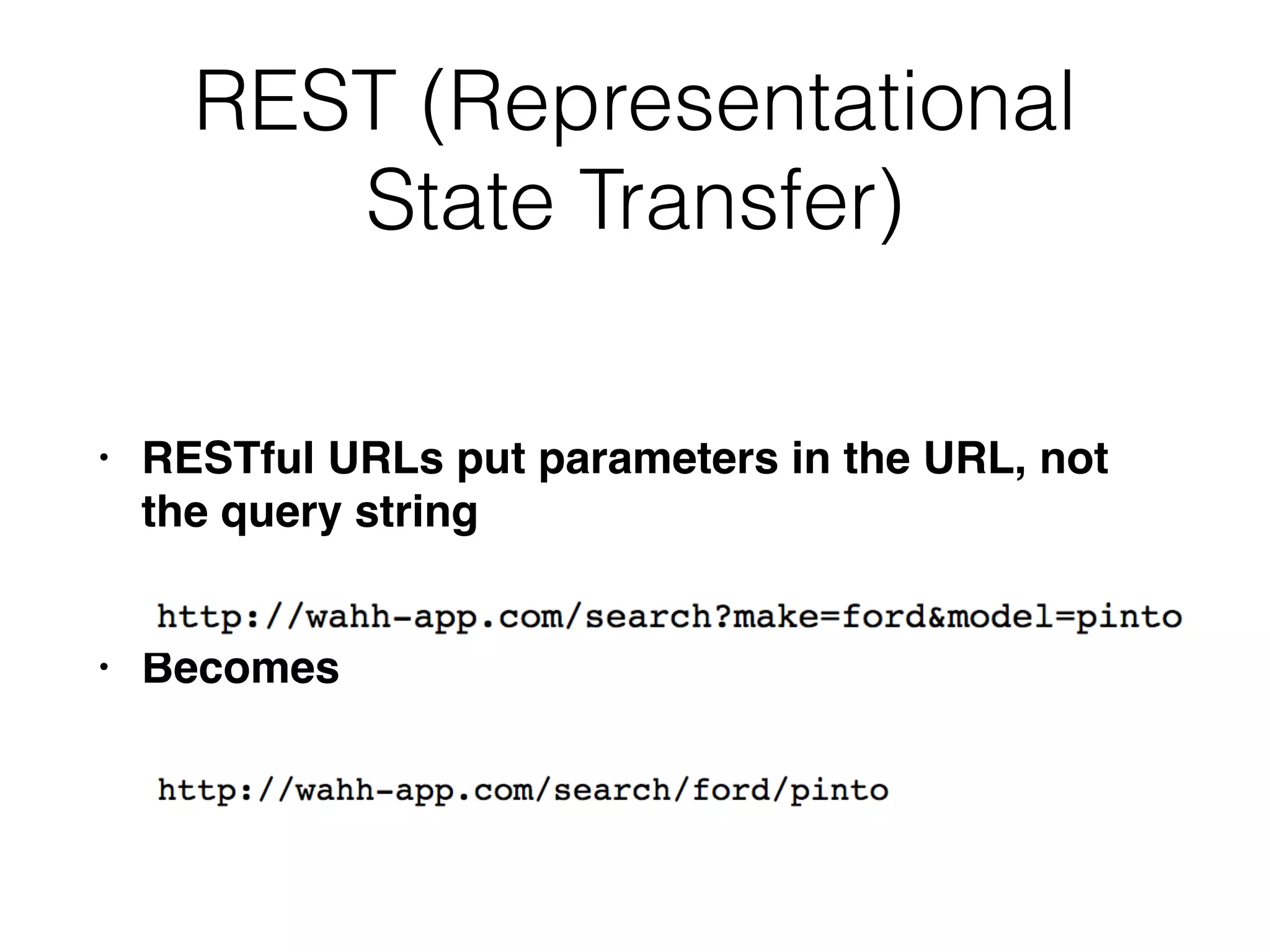
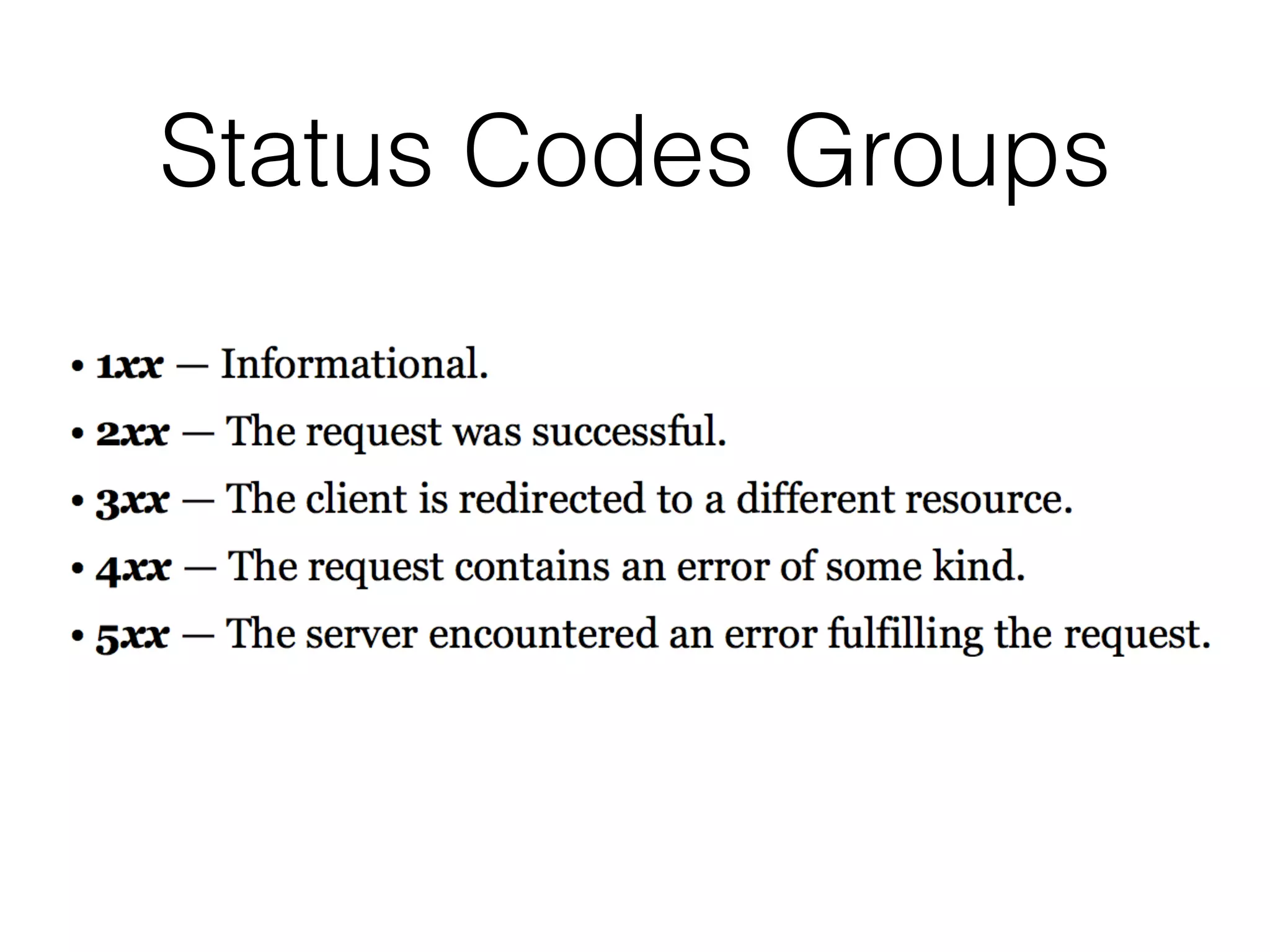
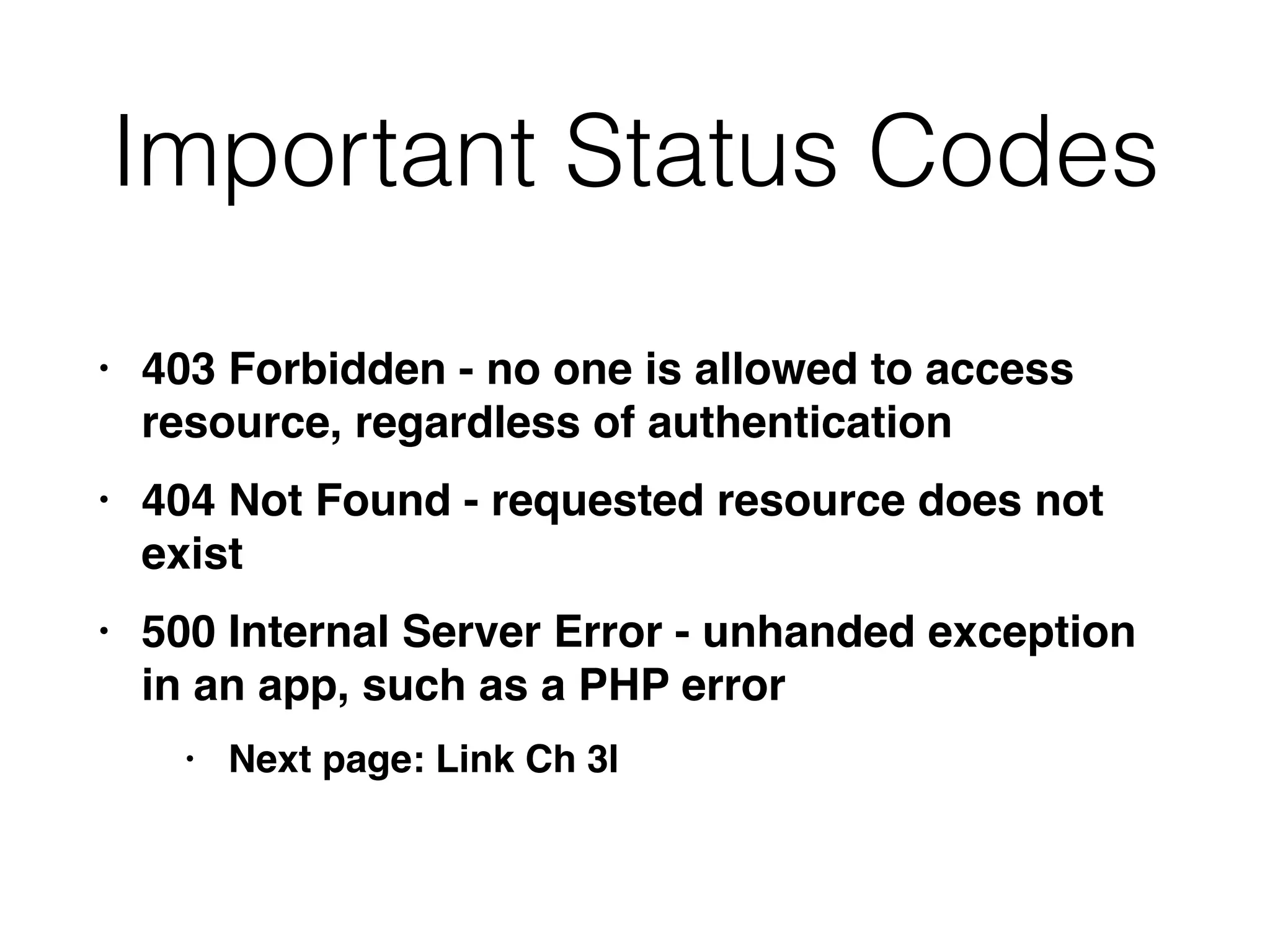
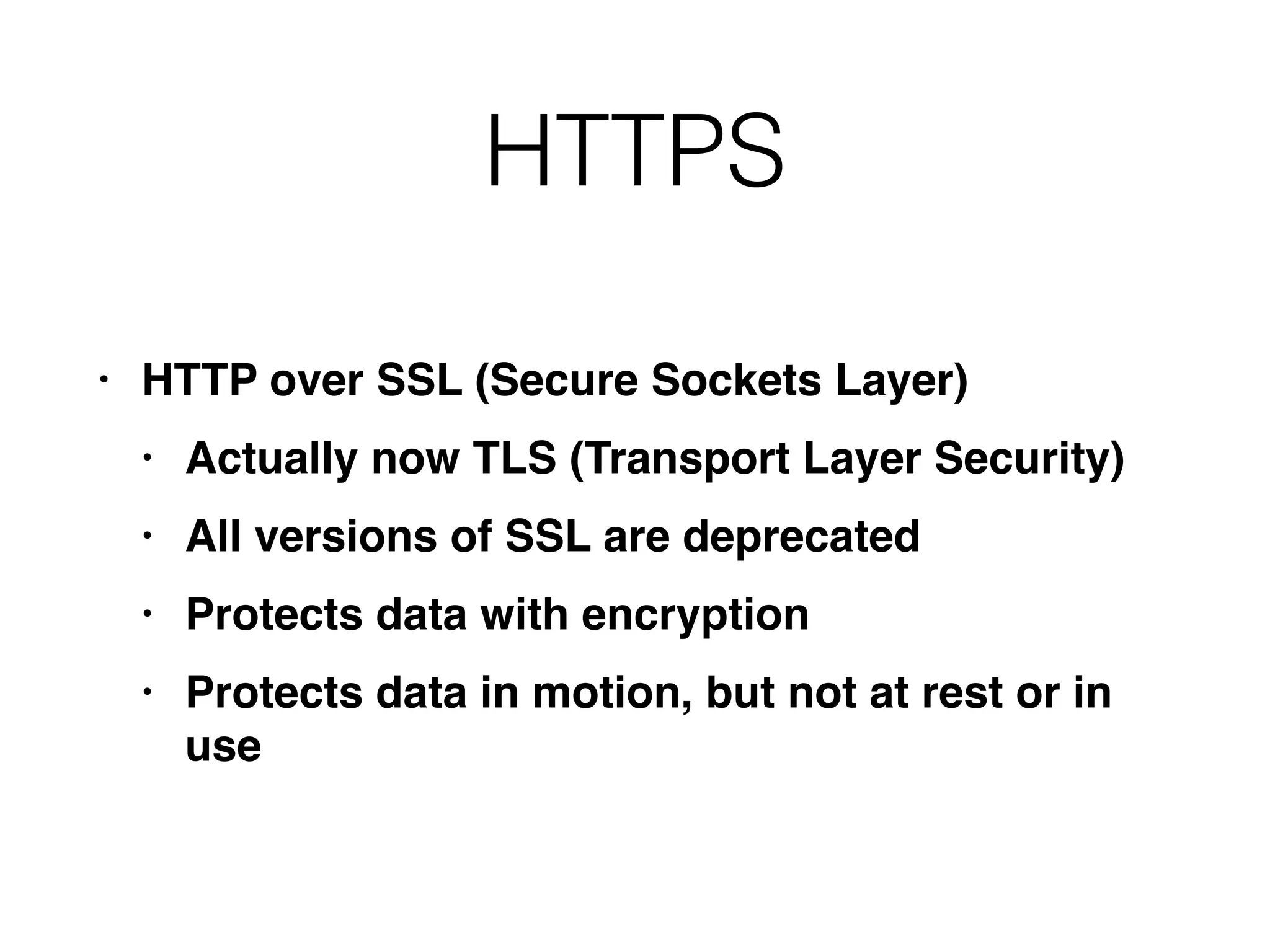
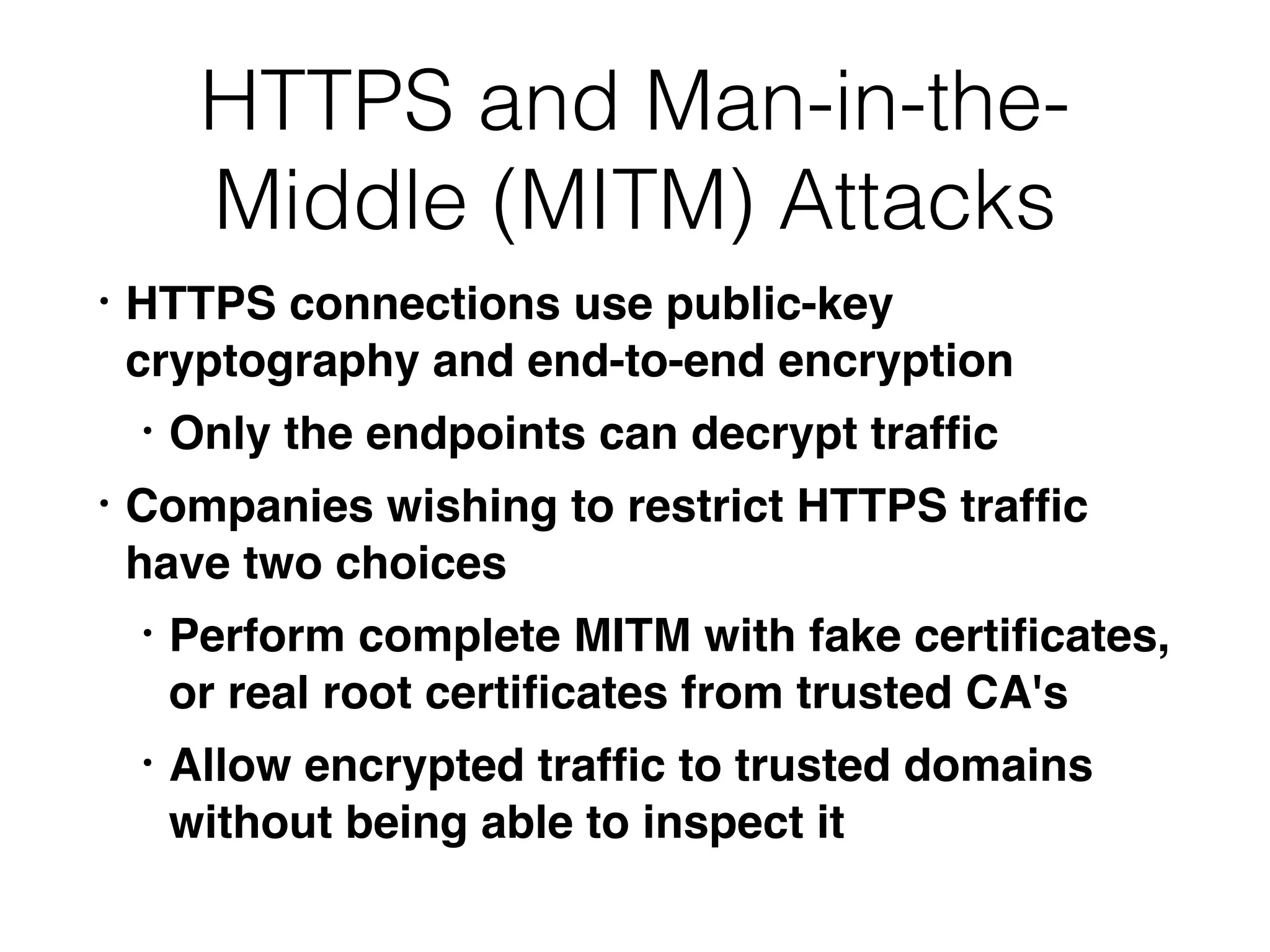
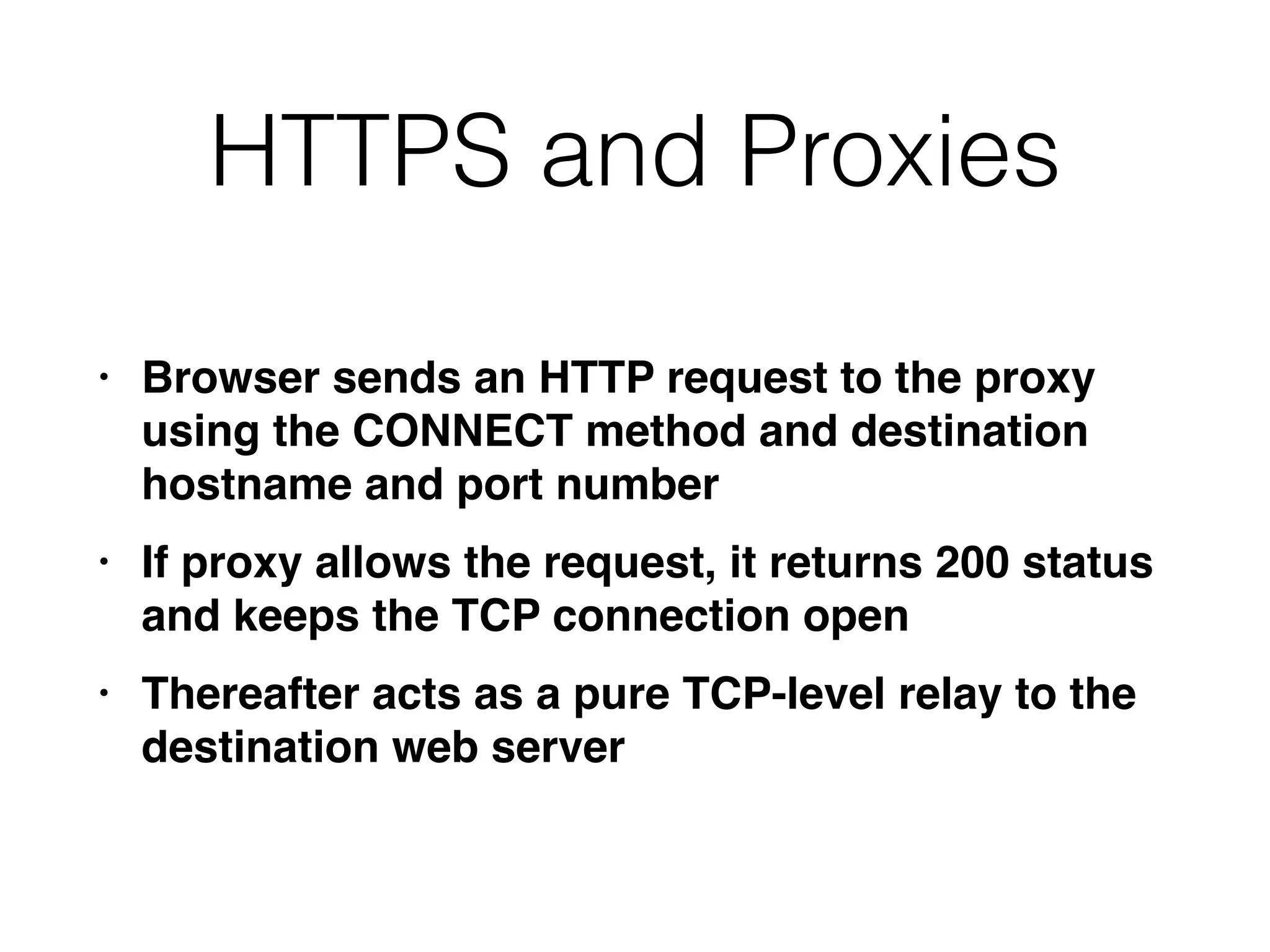
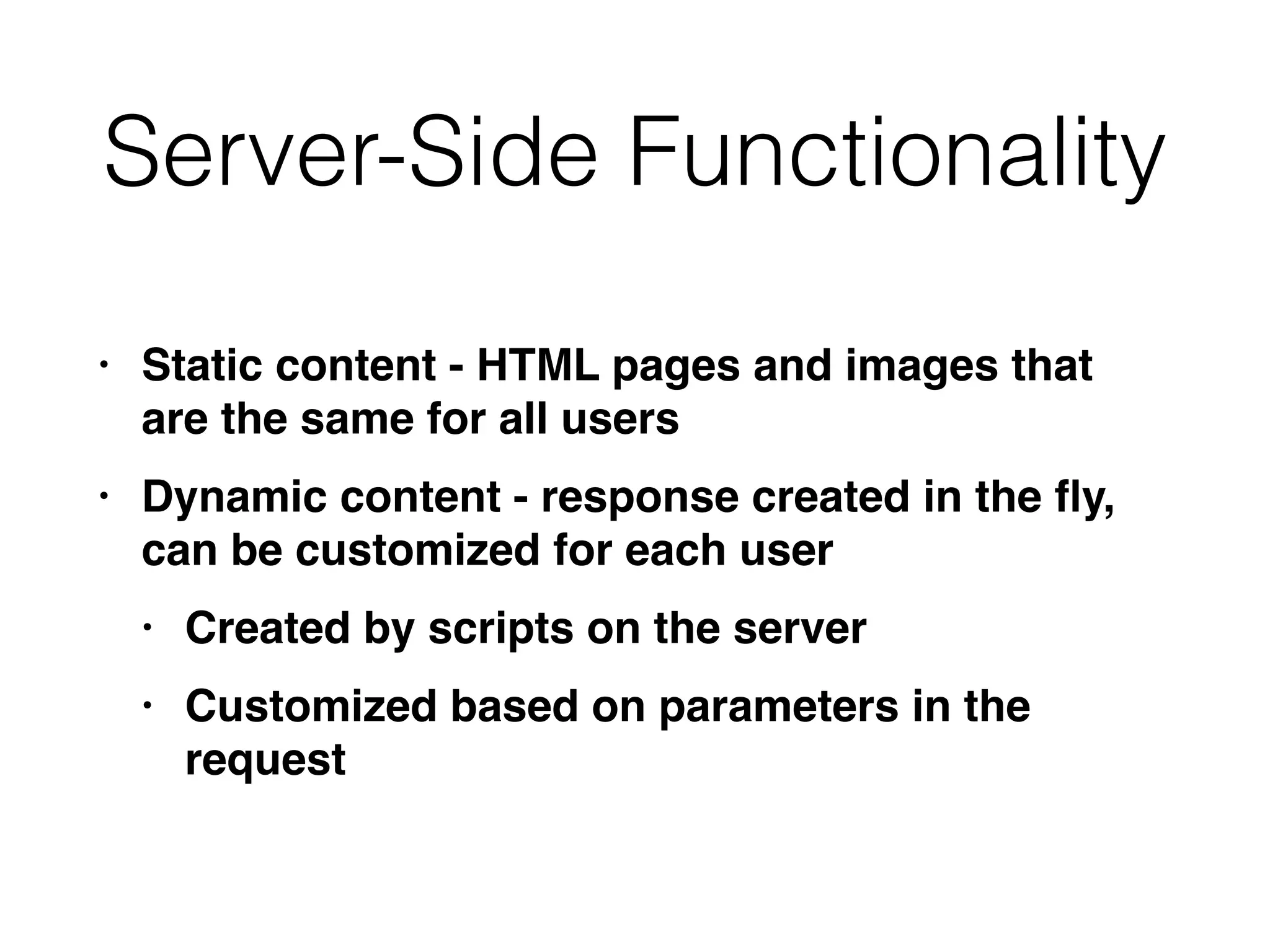
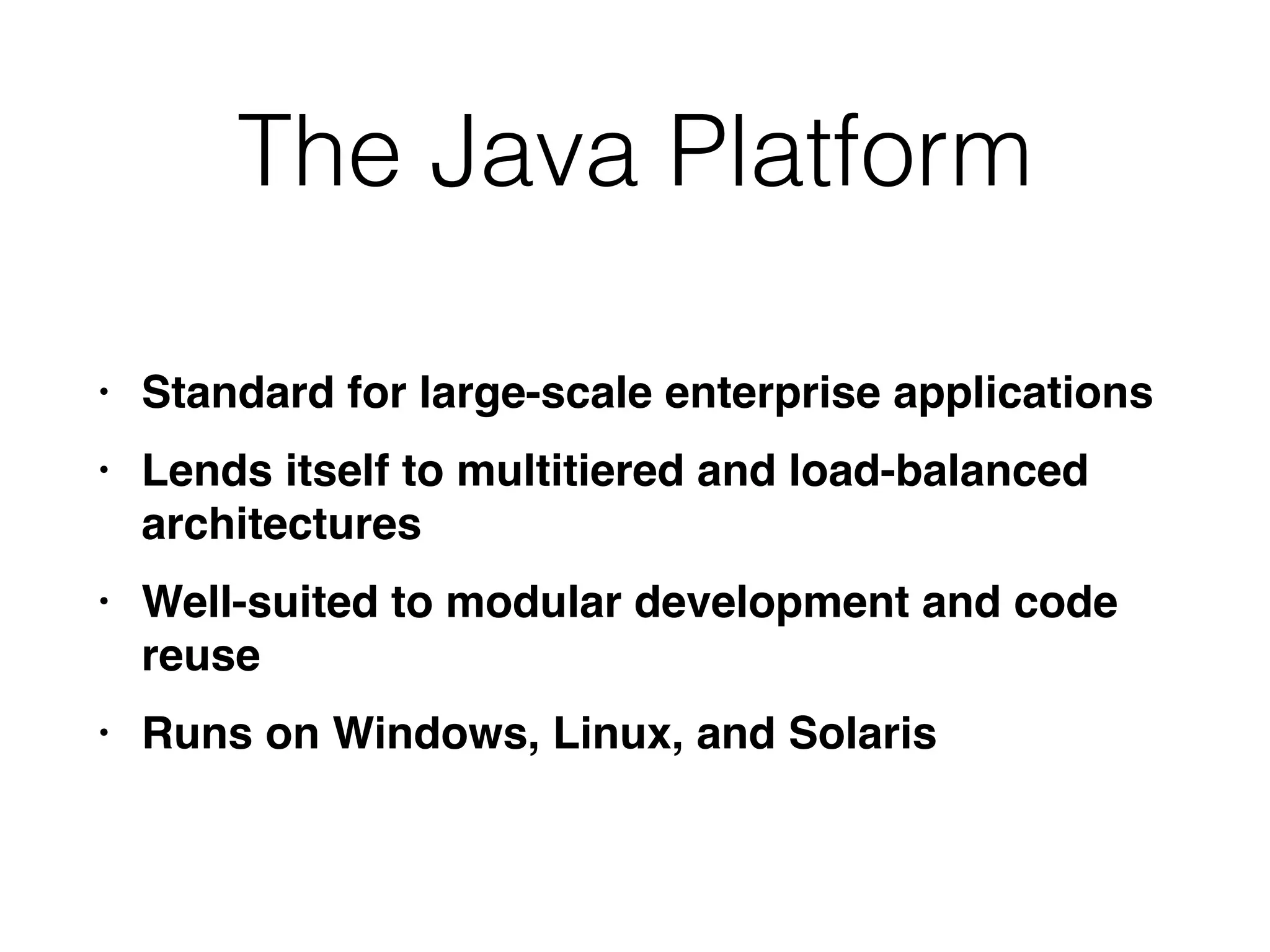
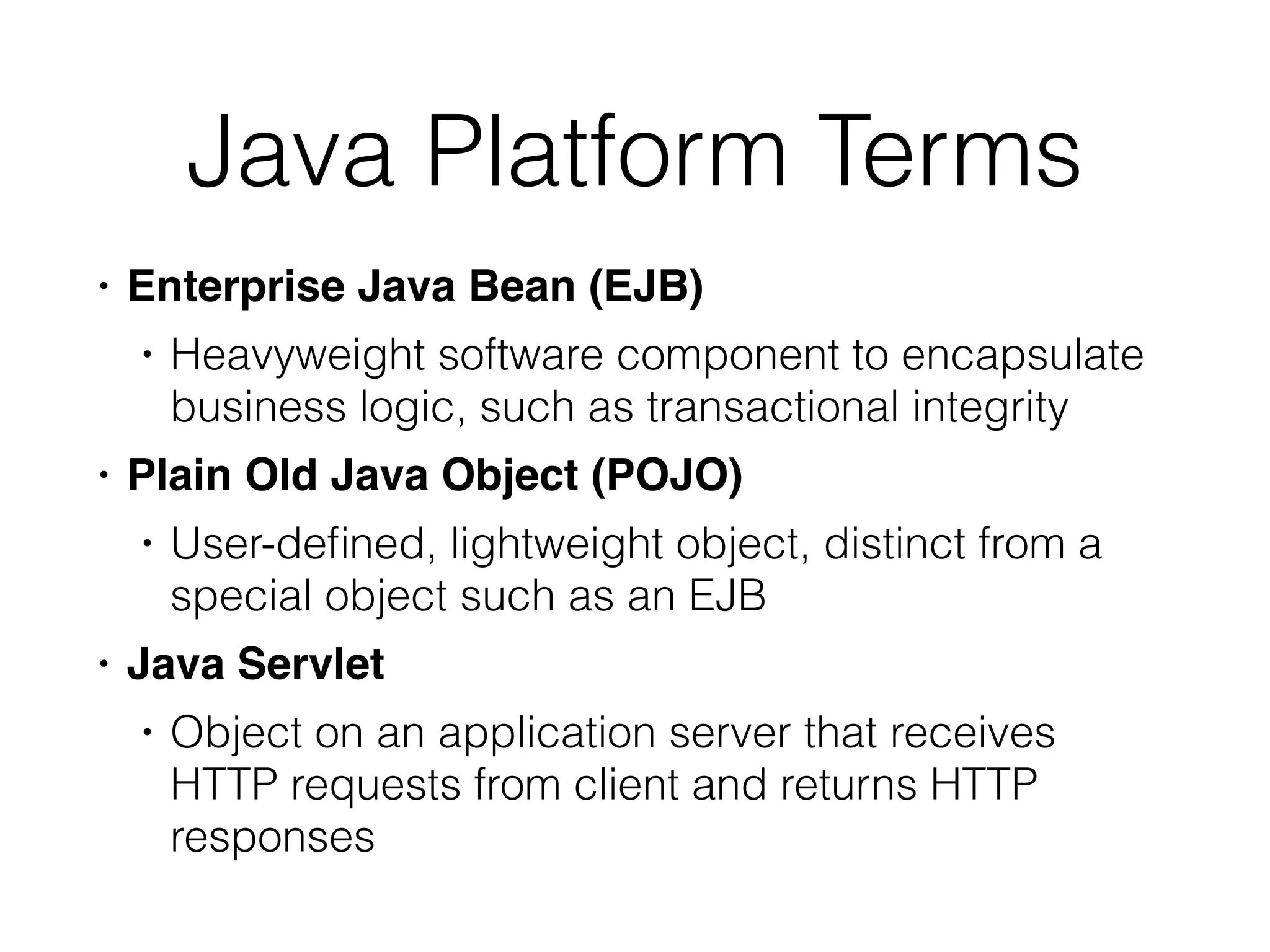
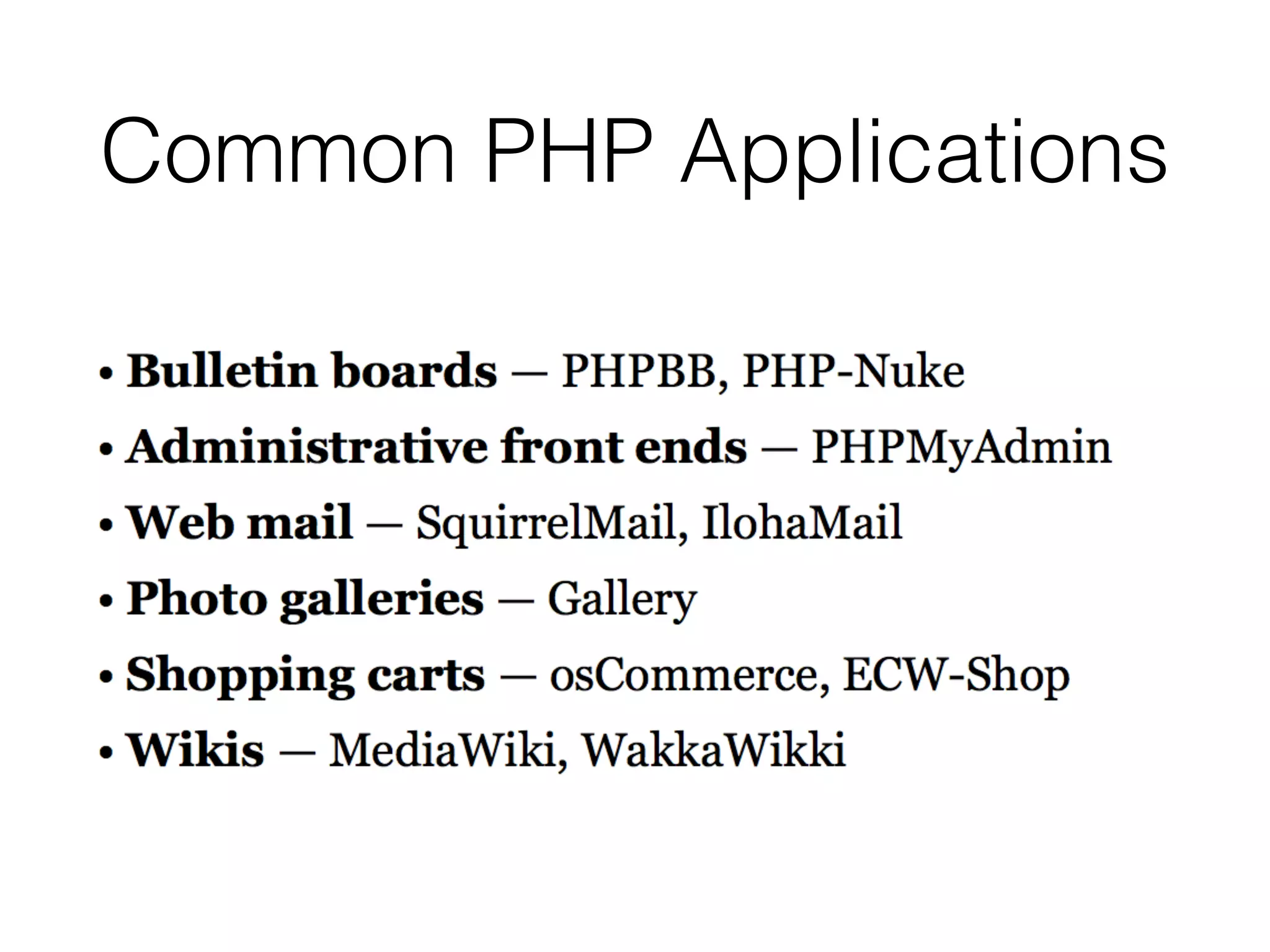
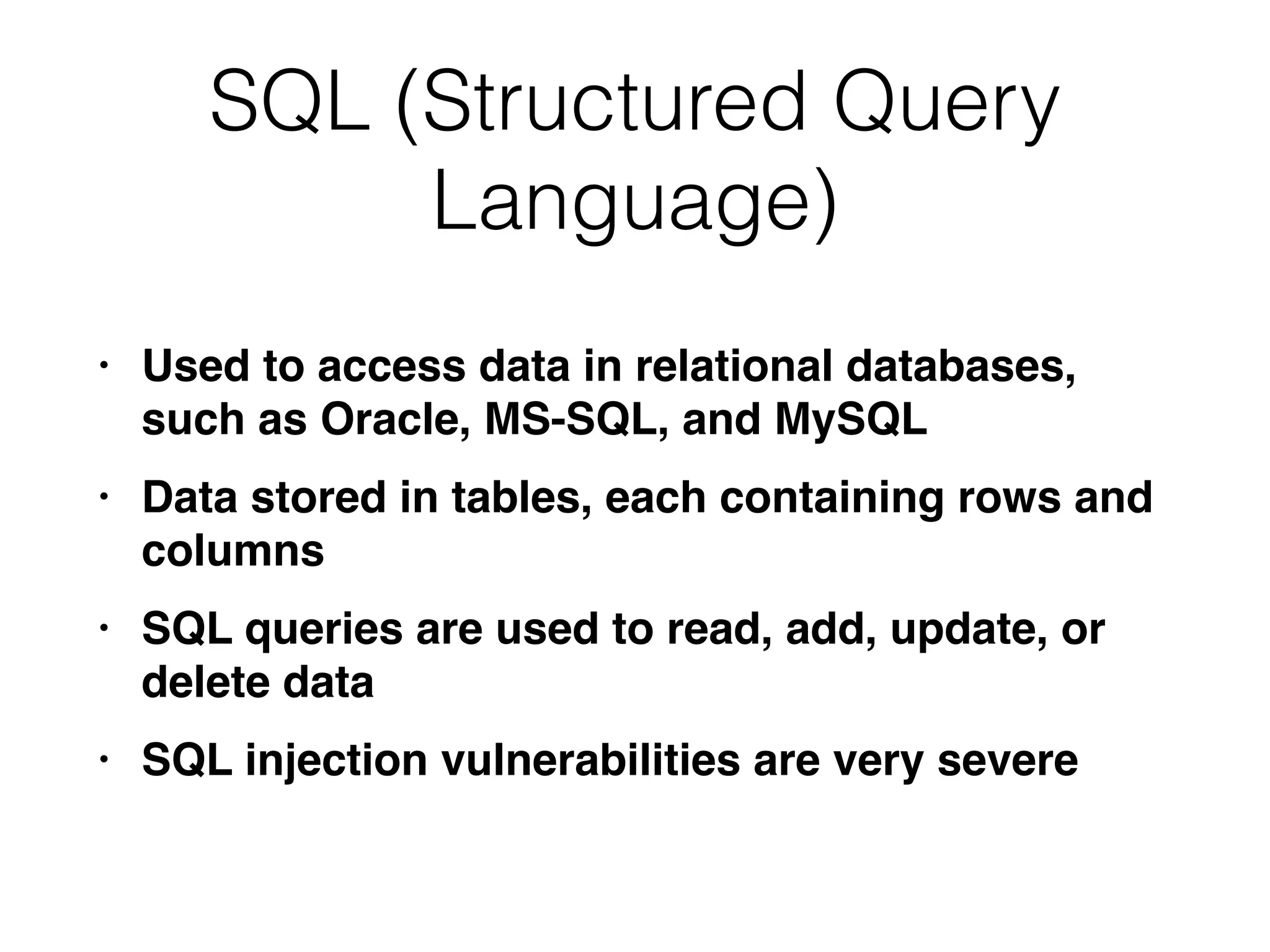
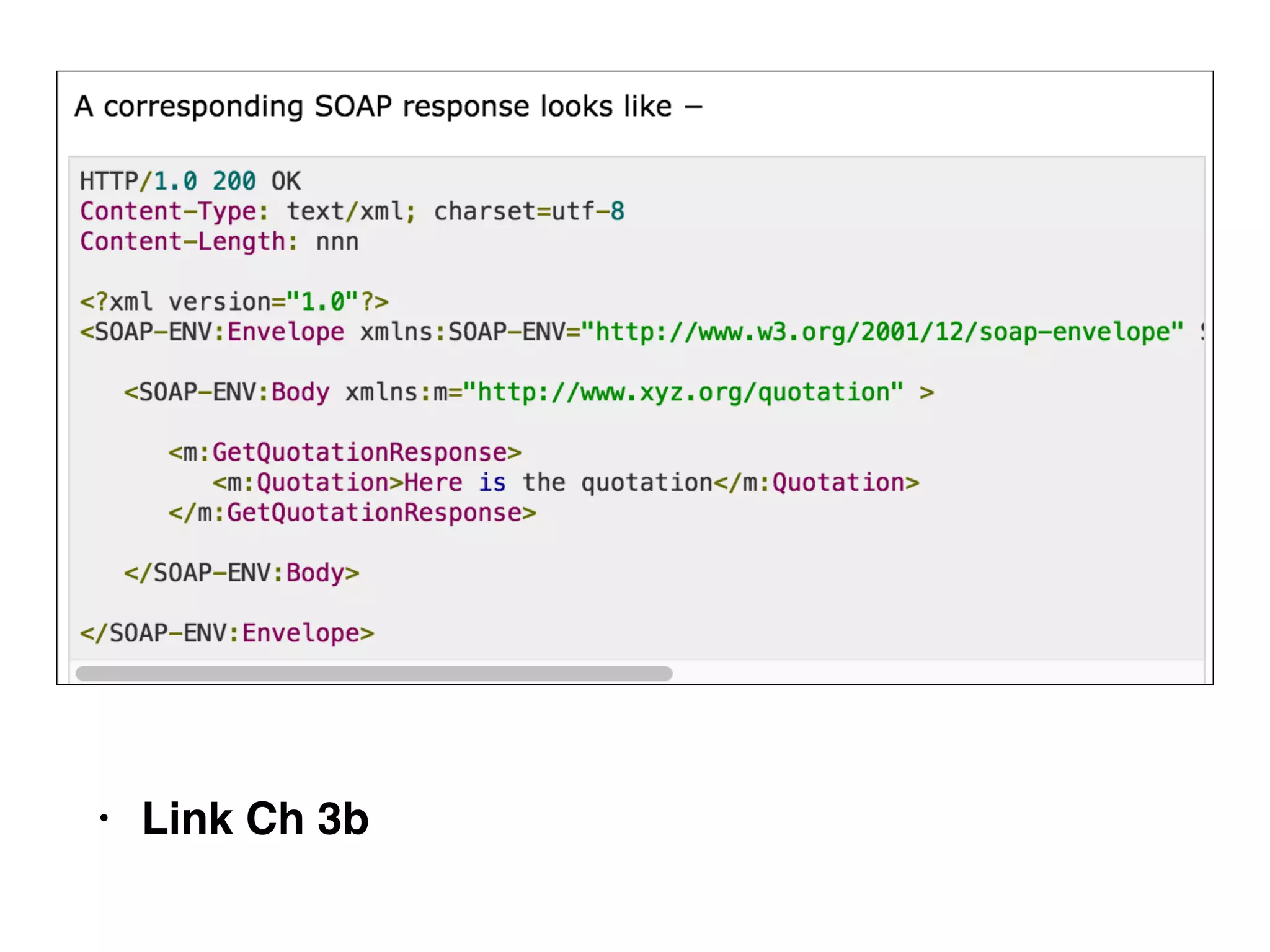
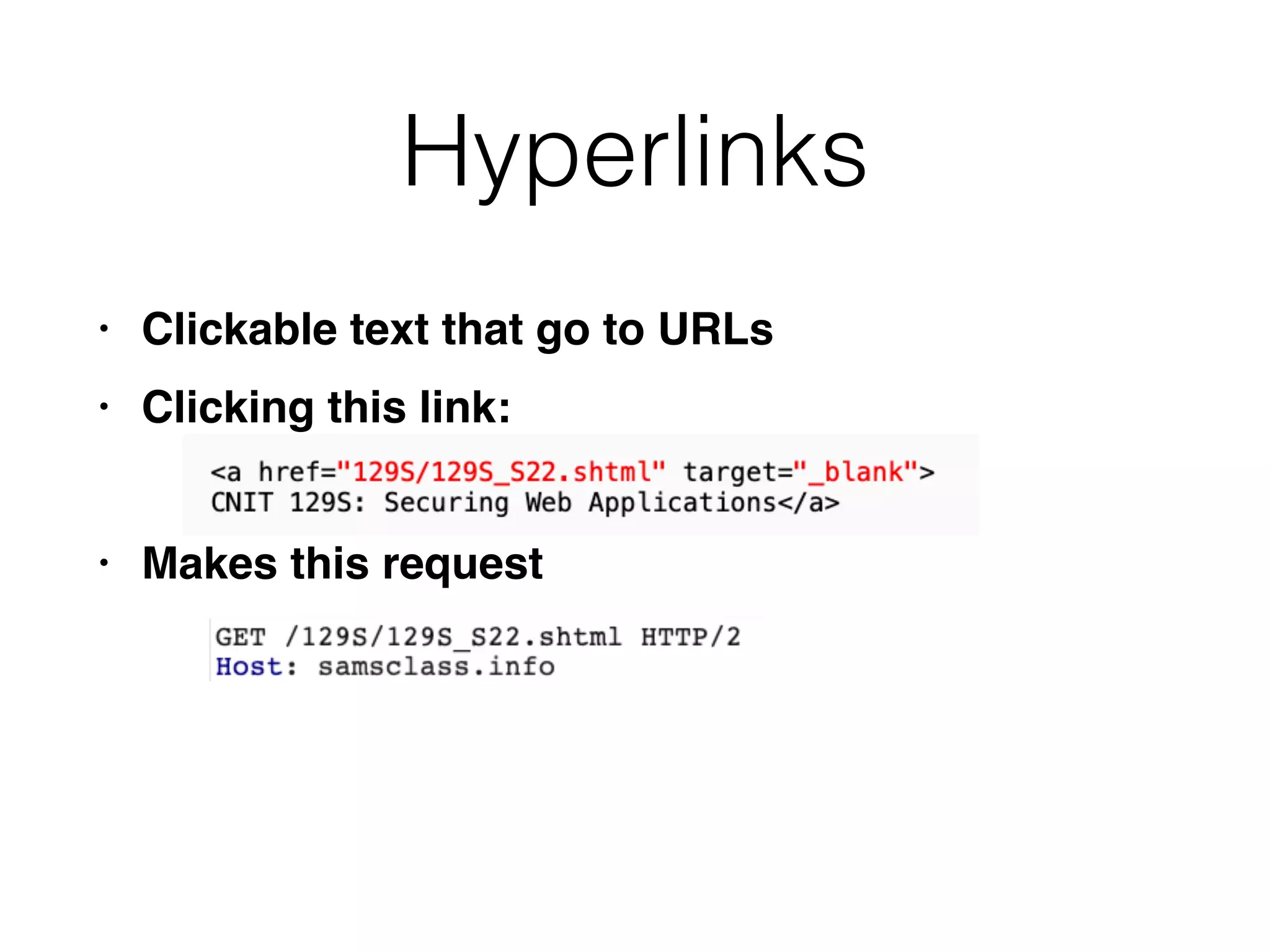
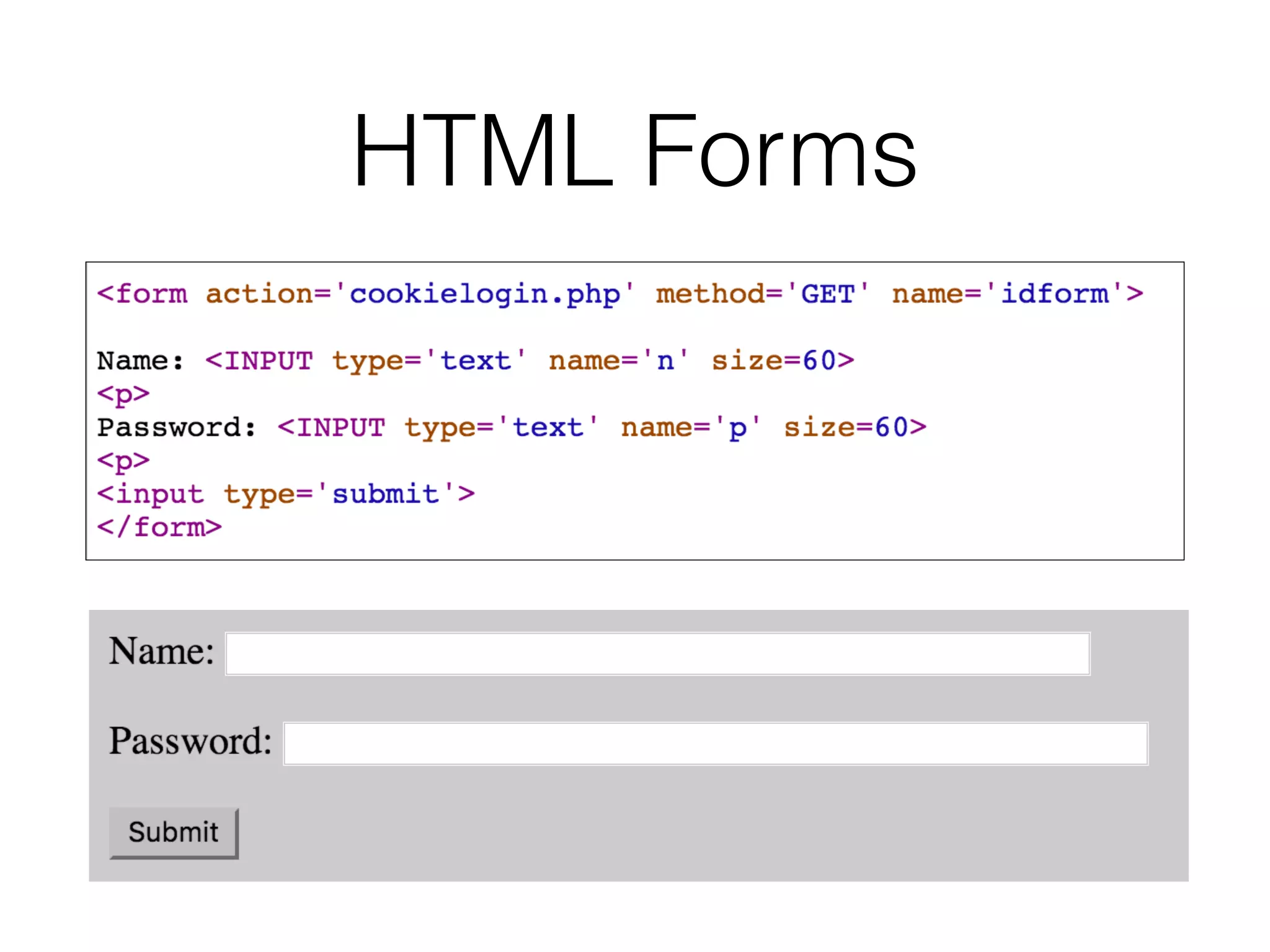
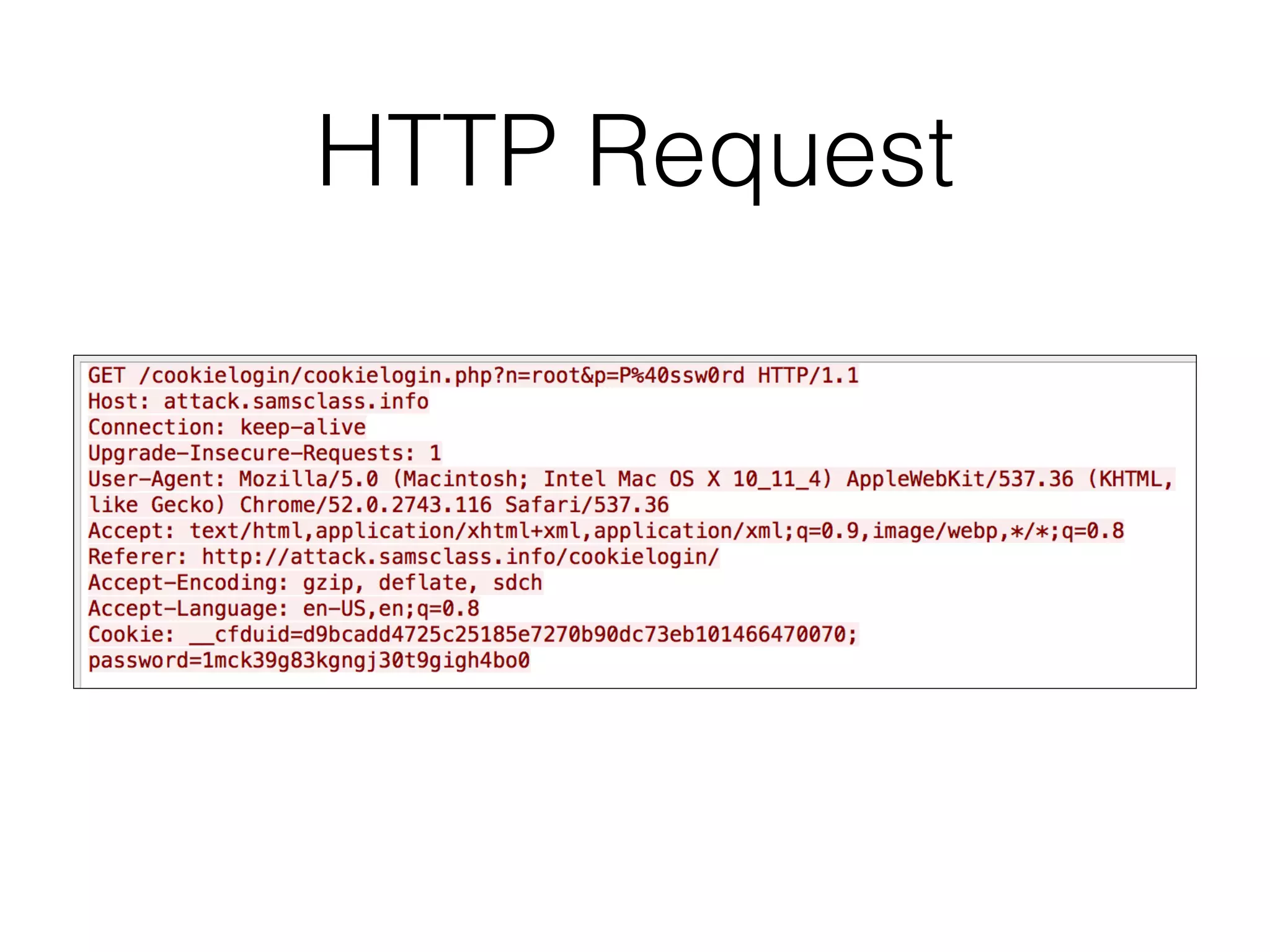
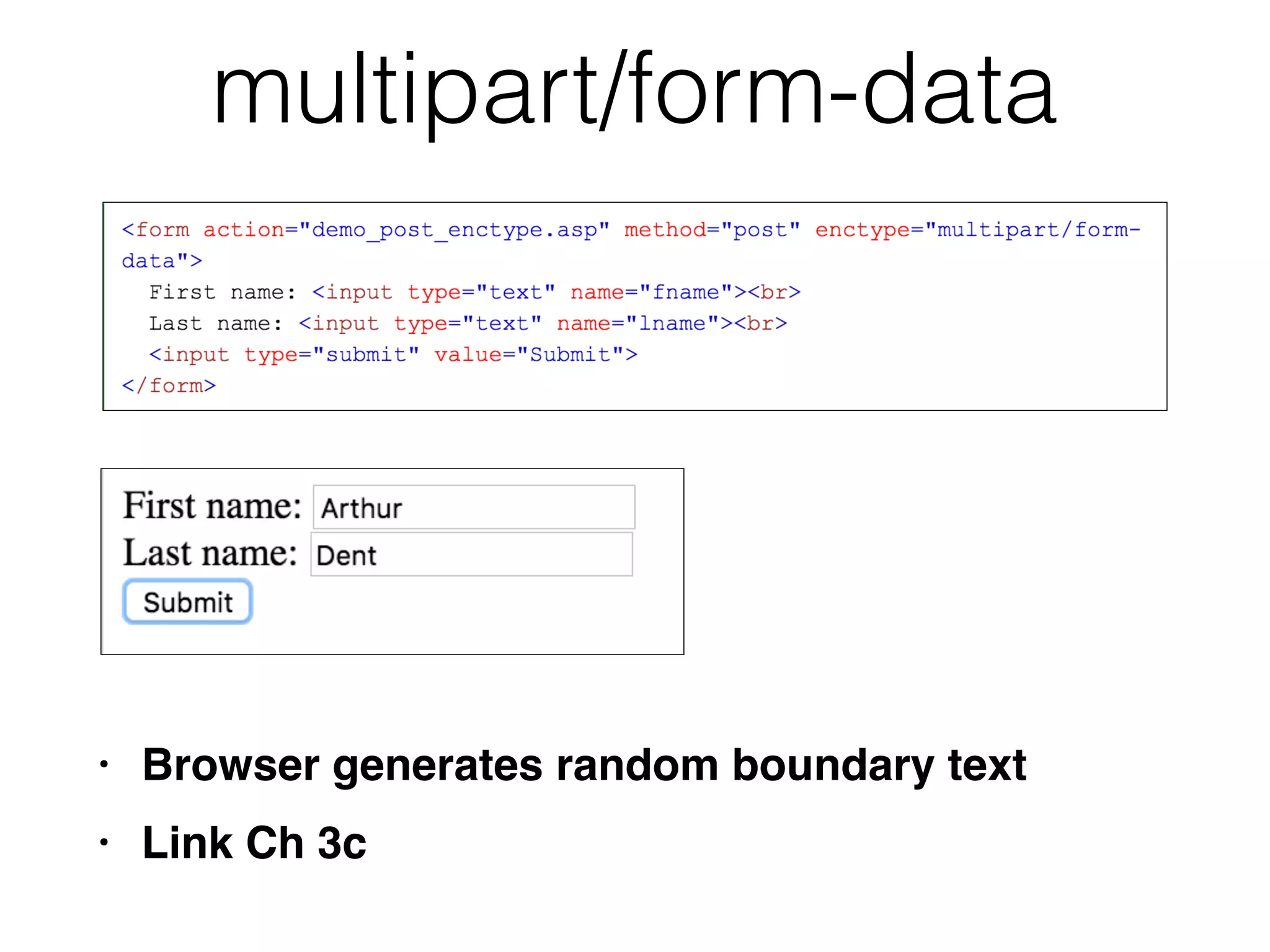
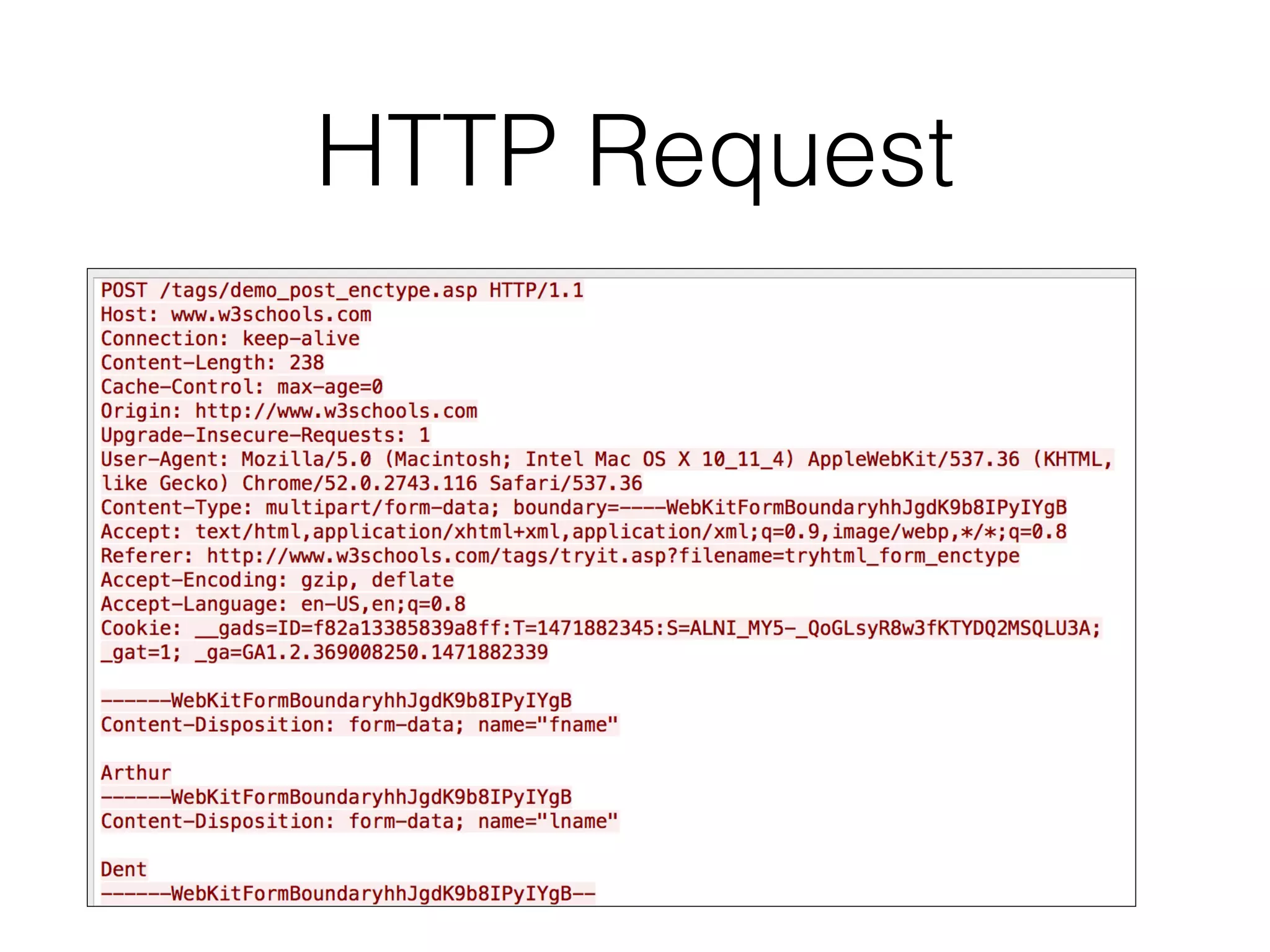
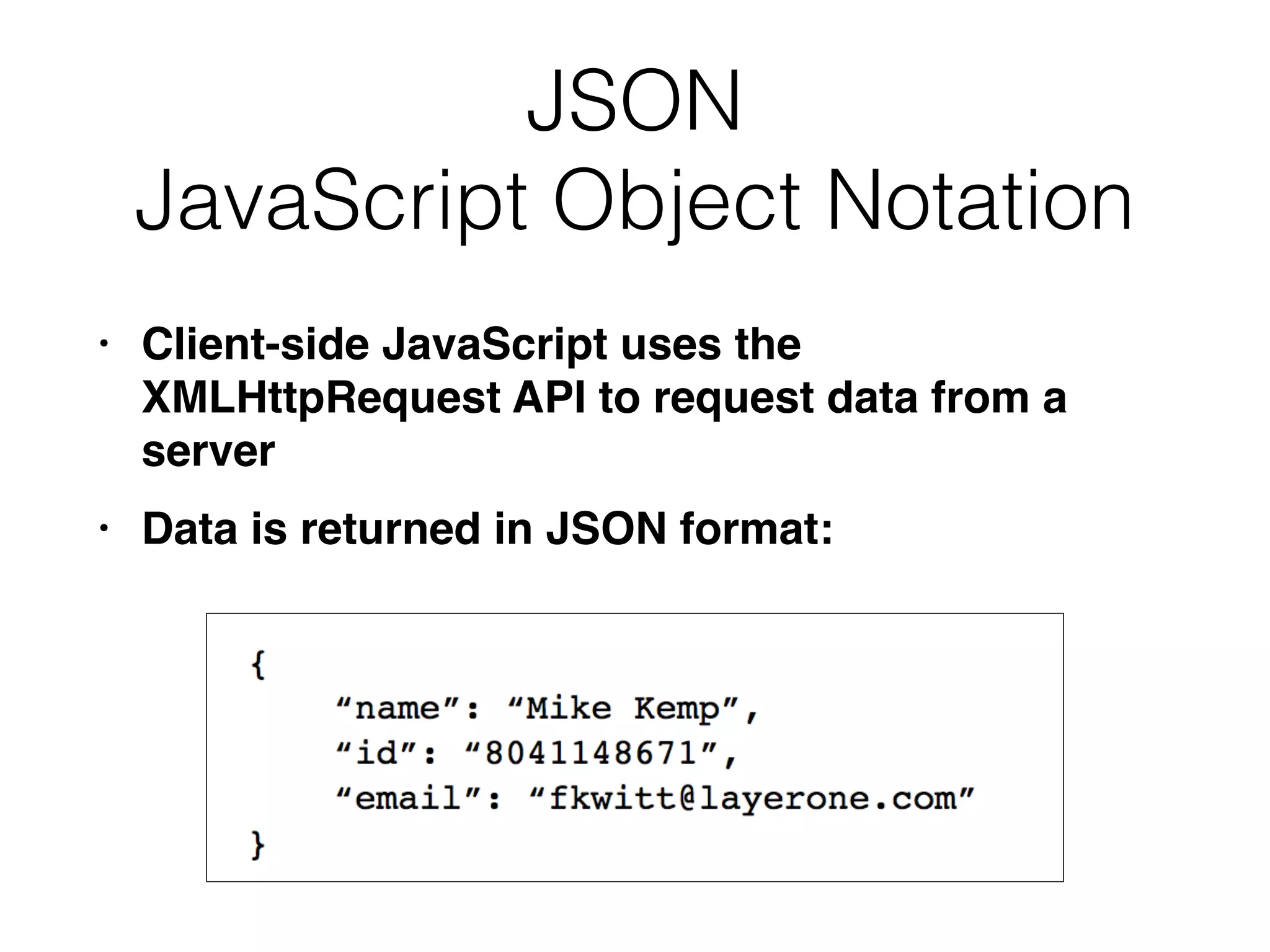
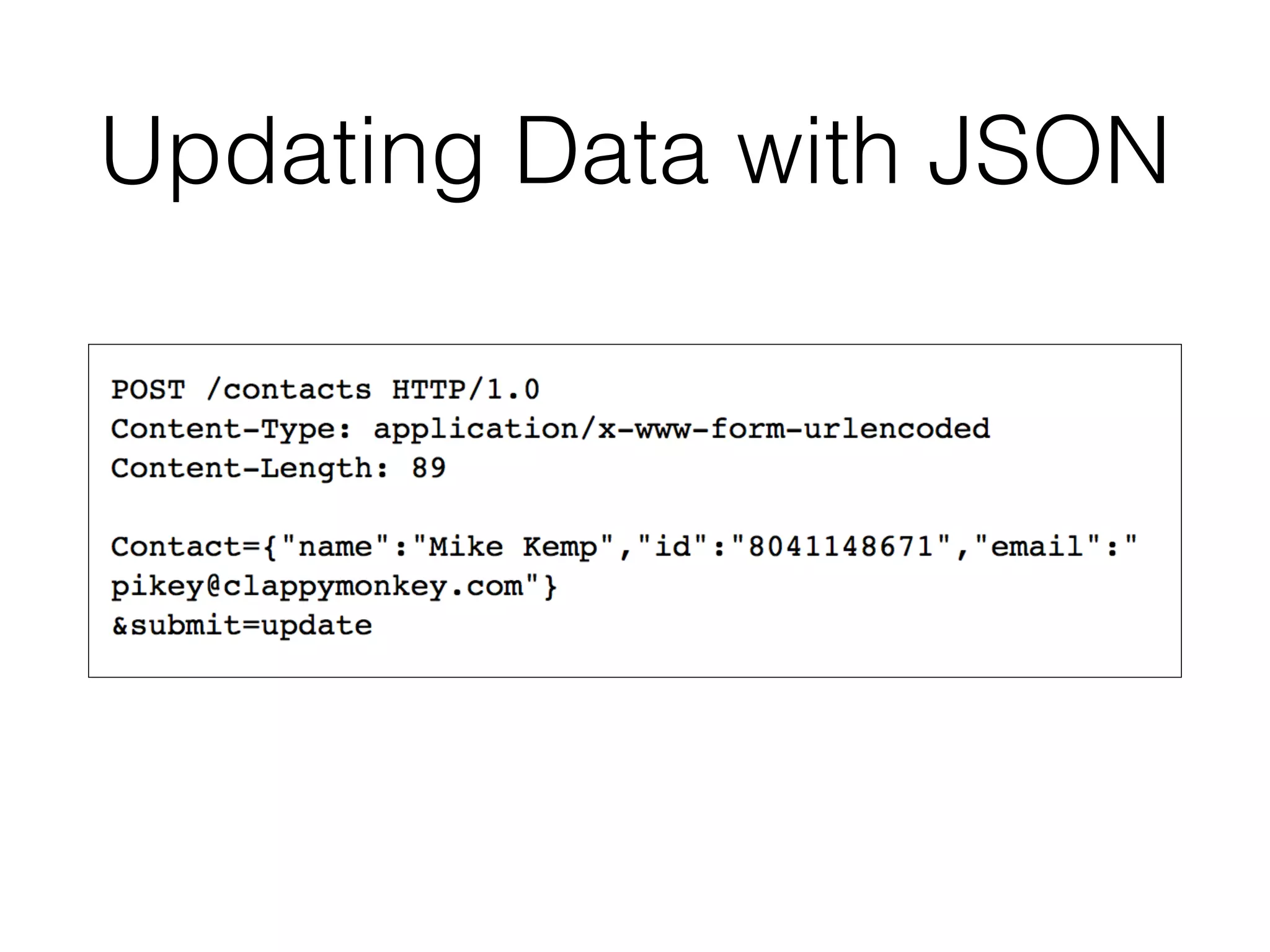
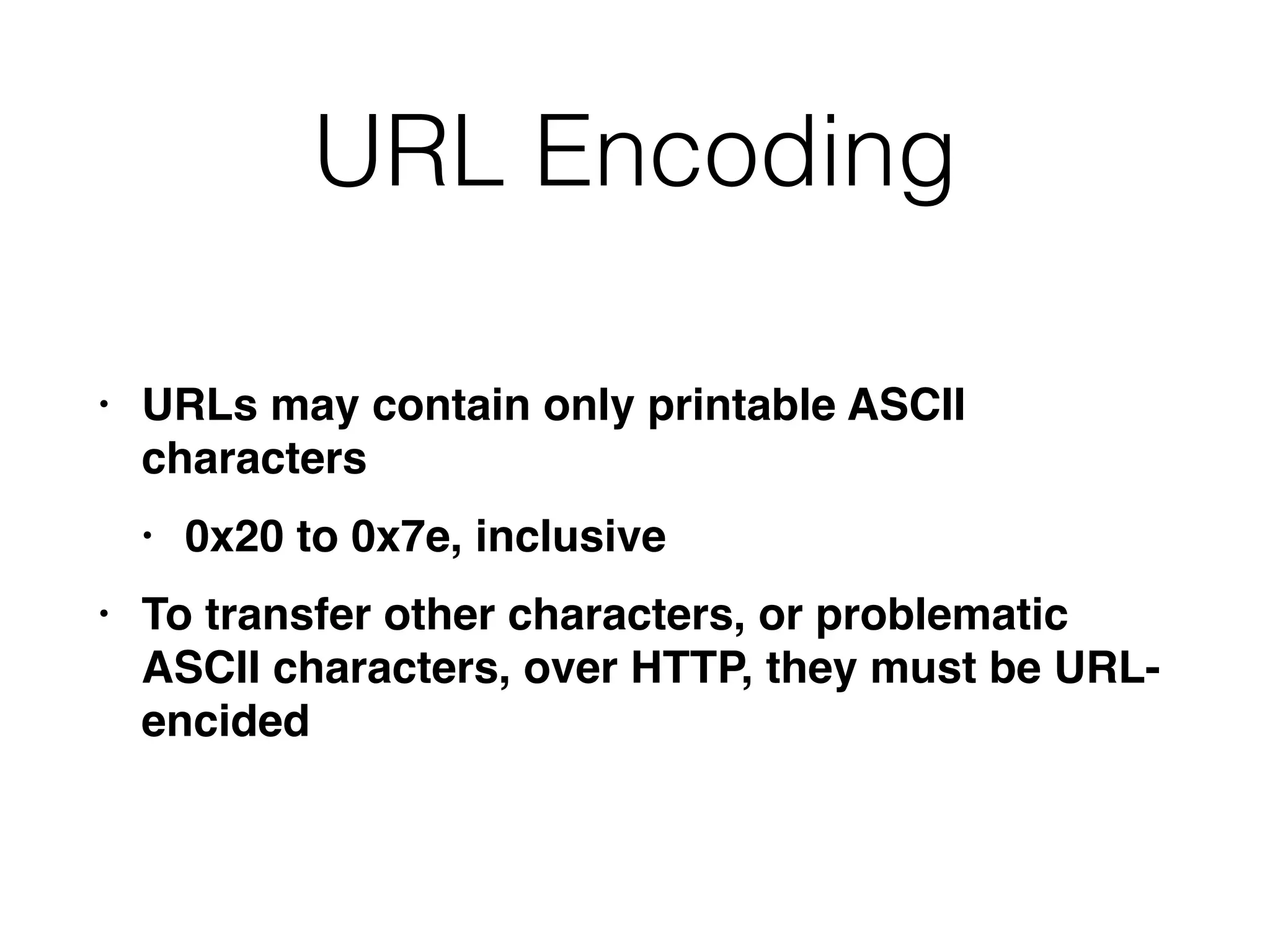
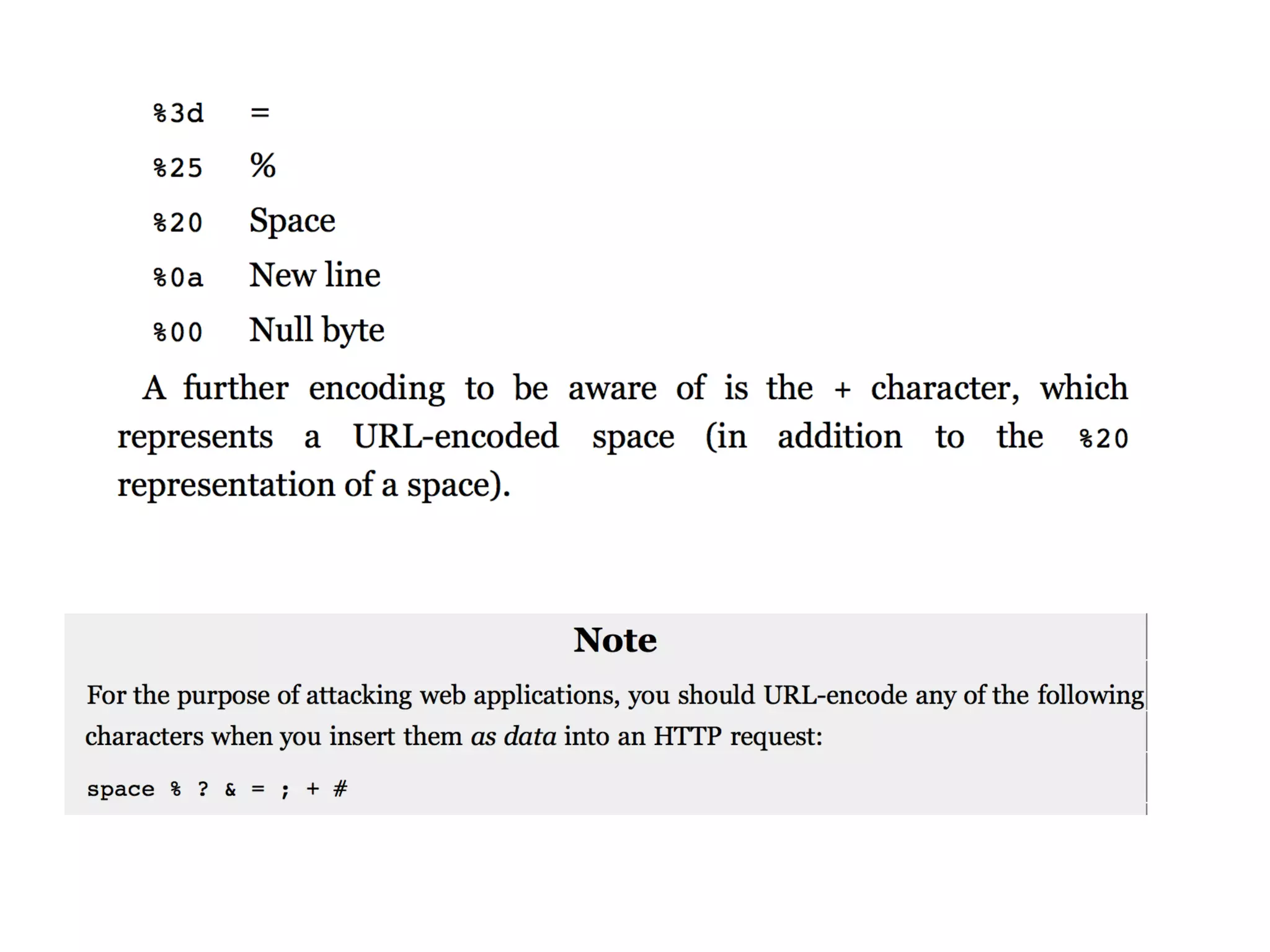
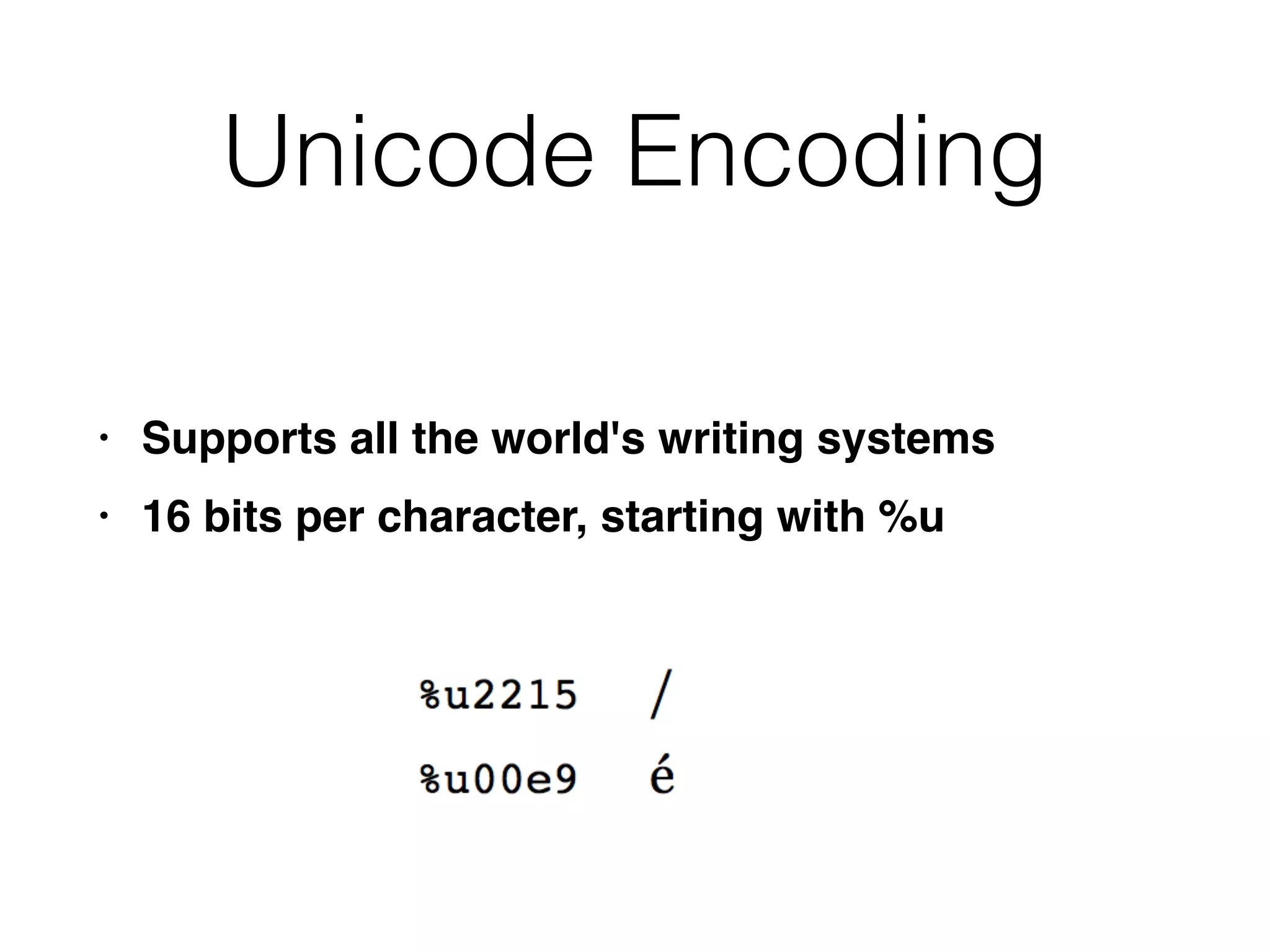
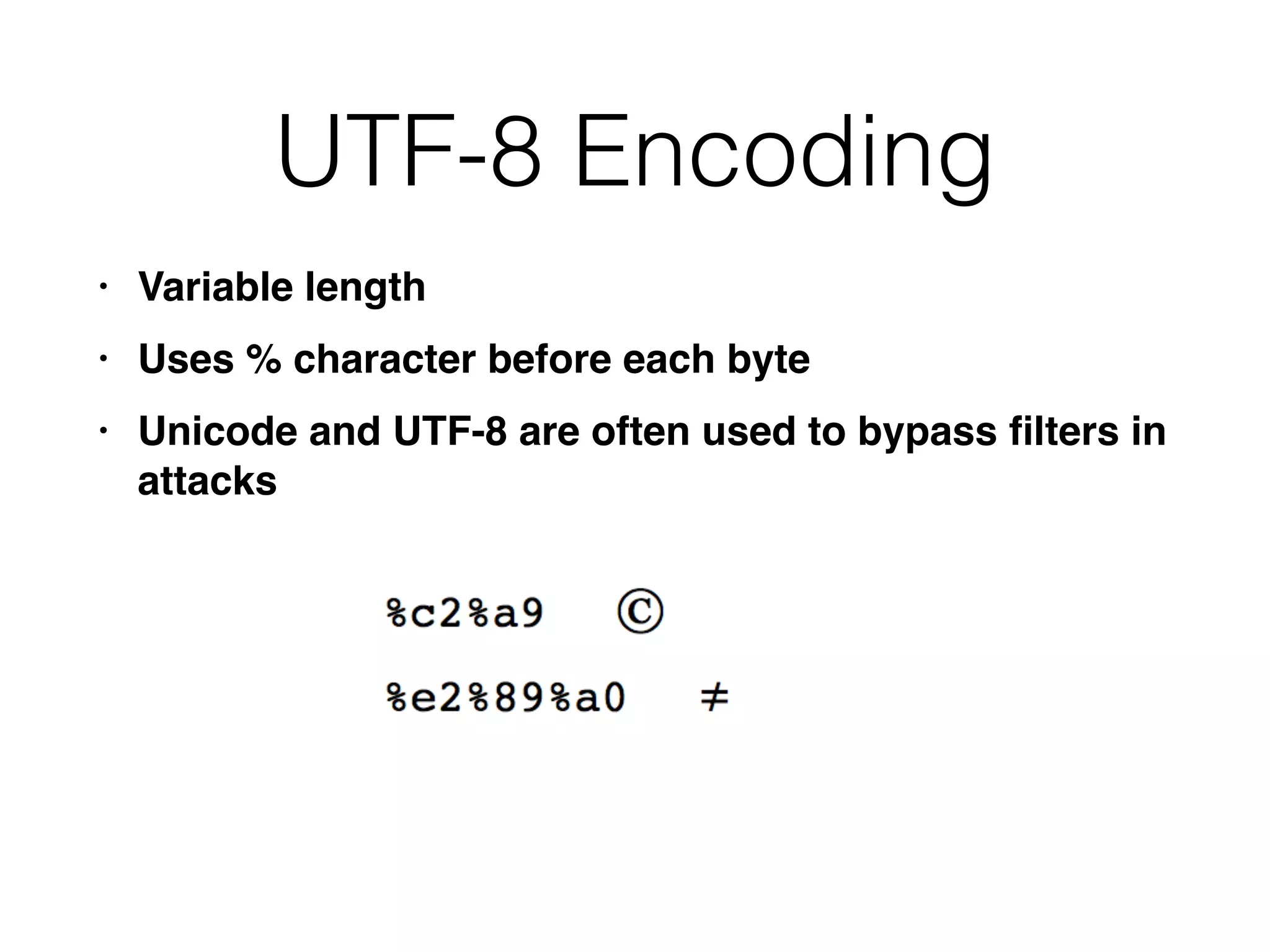
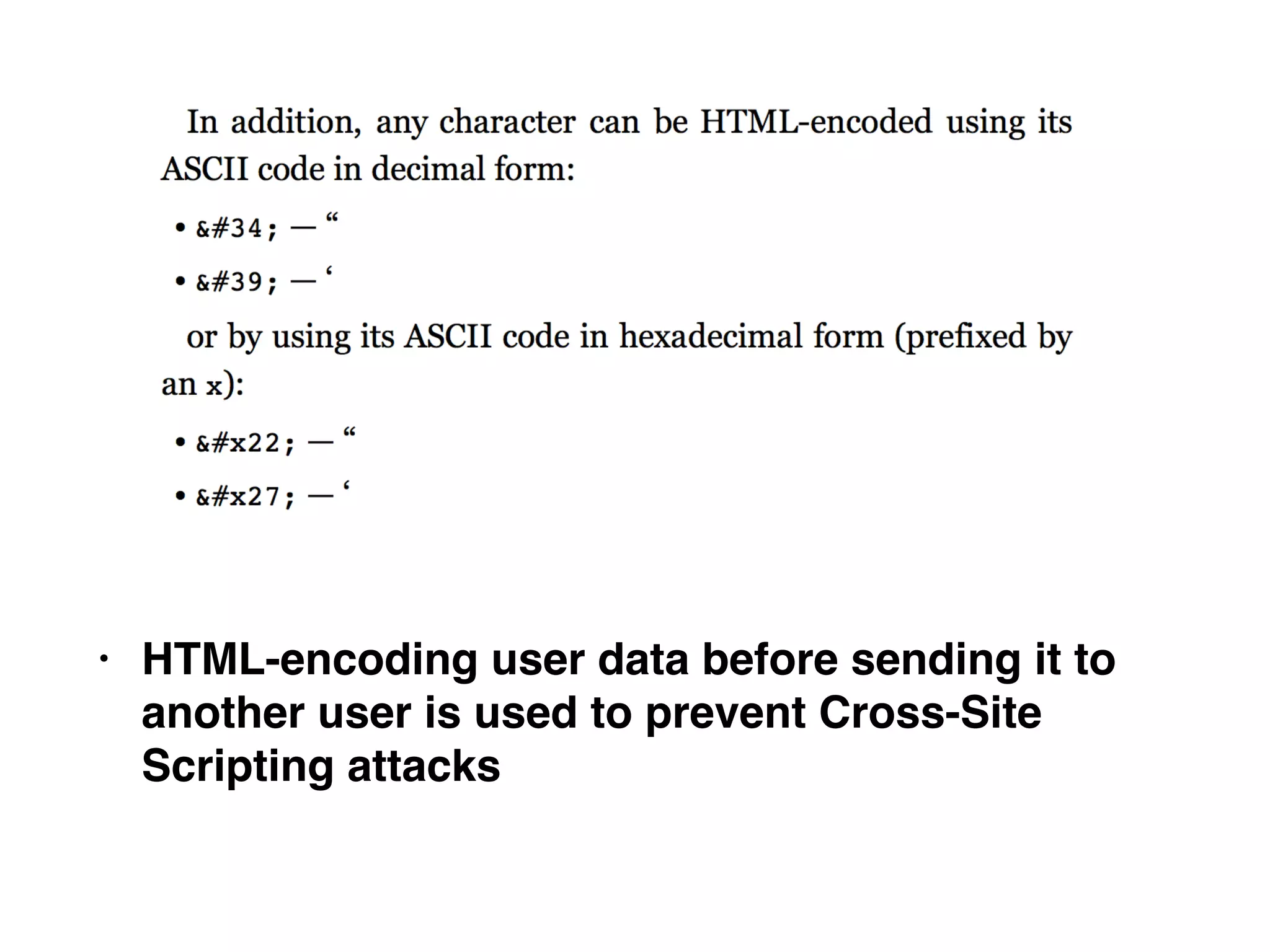
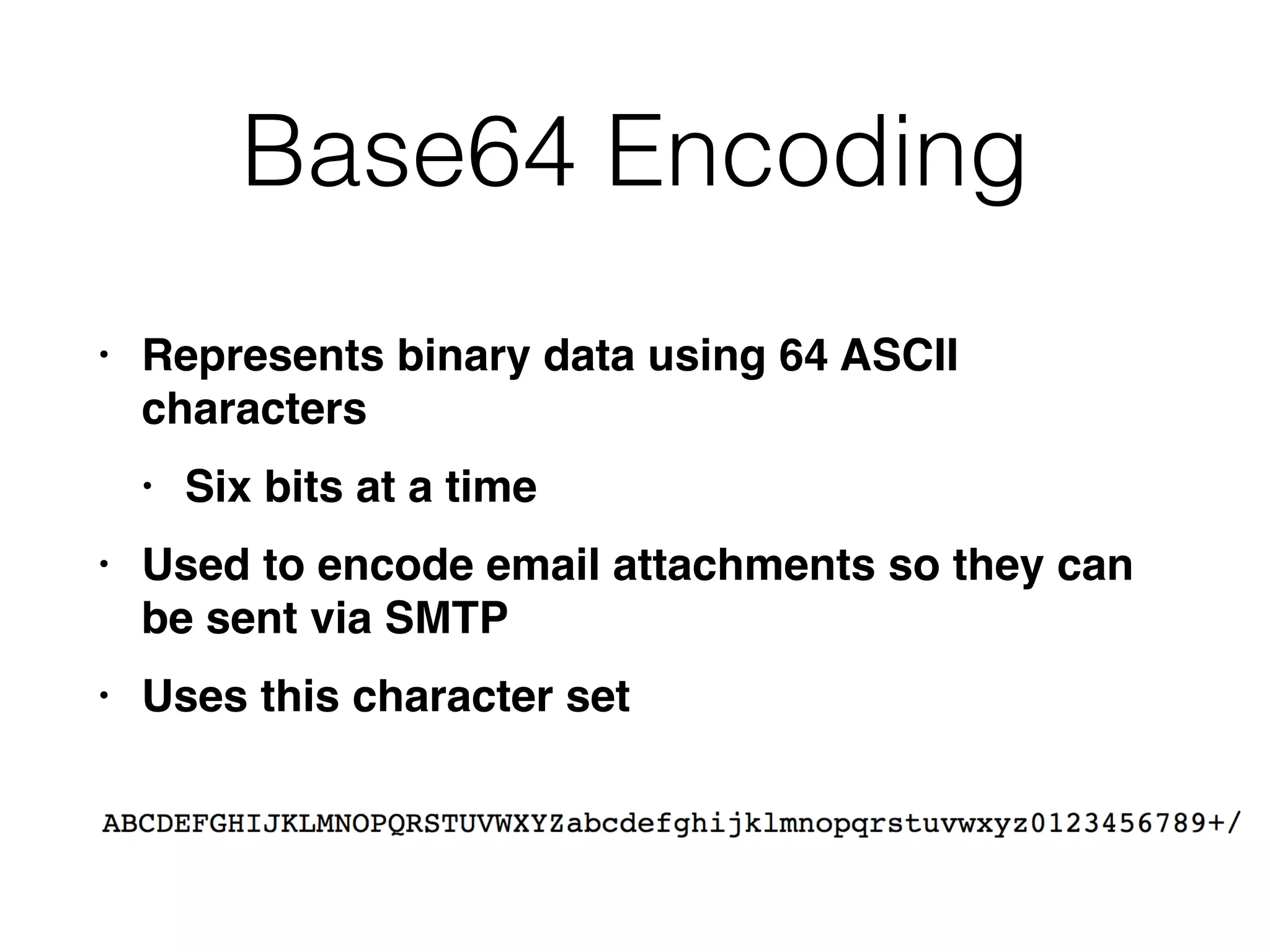
This document provides a summary of key concepts related to web application technologies. It discusses HTTP and HTTP requests/responses, including common headers. It also covers client-side technologies like HTML, CSS, JavaScript, and how they interact with the server via HTTP. On the server-side, it discusses programming languages and frameworks like Java, ASP.NET, PHP, and common databases. It also covers concepts like cookies, sessions, and different encoding schemes used to transmit data.