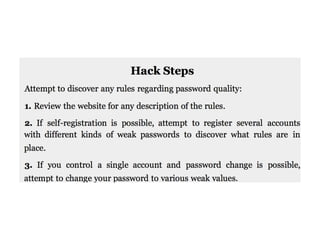
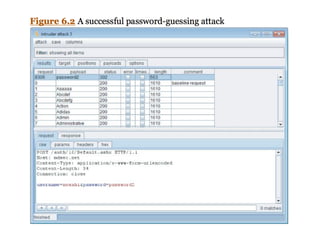
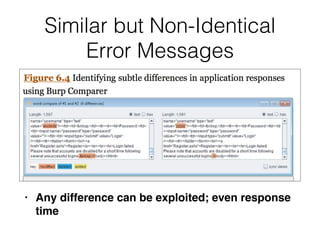
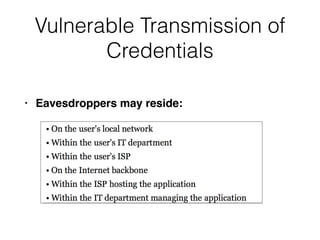
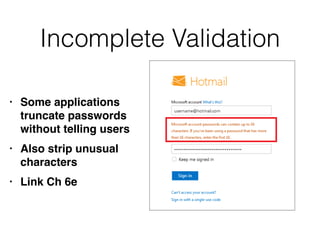
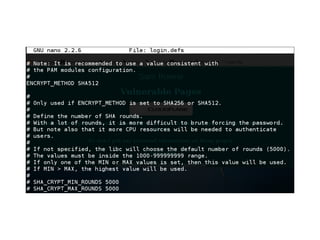
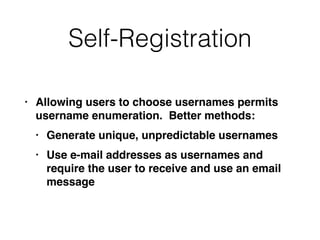
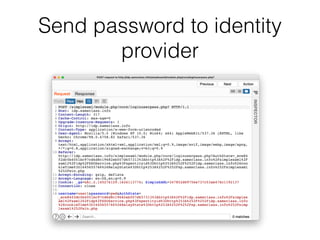
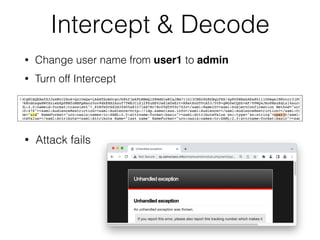
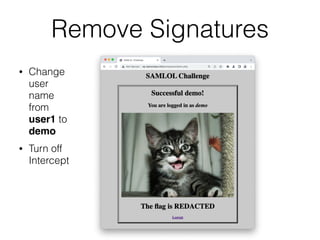
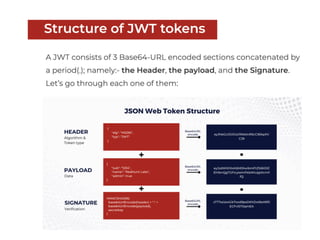
This document provides a summary of authentication techniques and common vulnerabilities. It discusses how over 90% of applications use usernames and passwords for authentication. More secure authentication methods like two-factor authentication are also described. The document outlines various authentication protocols like HTTP, SAML, and JWT. It then details common design flaws such as weak passwords, password change vulnerabilities, account recovery issues, and information leakage. Specific attacks like brute force, credential stuffing, and session hijacking are examined. The summary recommends approaches to secure authentication like strong credentials, hashing passwords, multi-factor authentication, and logging authentication events.