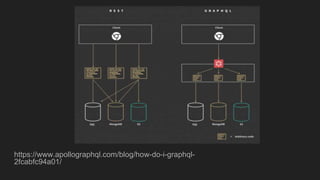
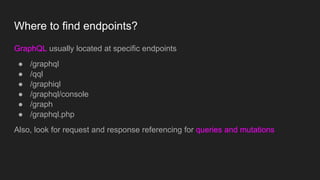
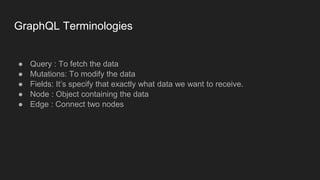
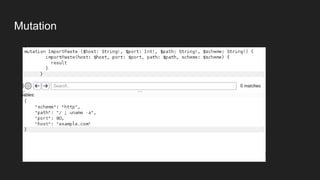
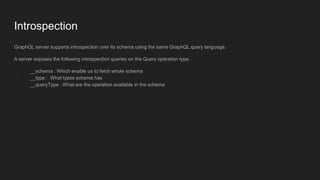
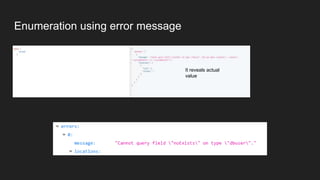
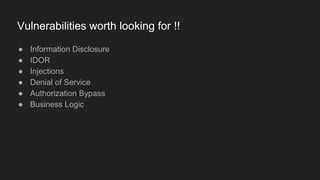
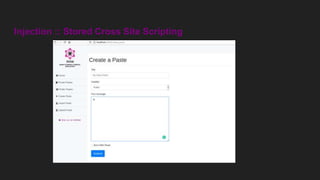
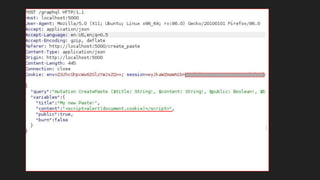
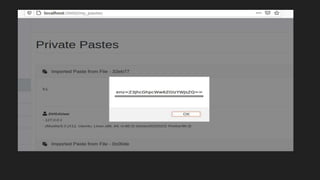
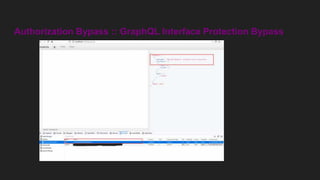
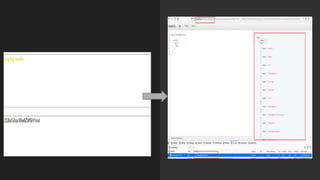
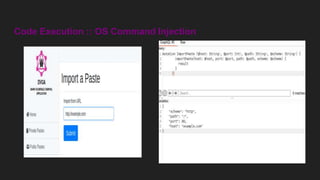
This document discusses attacking GraphQL APIs. It begins with an overview of GraphQL, how it differs from REST APIs, and key GraphQL concepts like queries, mutations, and introspection. It then explains how introspection can be dangerous by revealing an API's schema. Various vulnerabilities are covered like information disclosure, IDOR, injections, and authorization bypass. Tools for analyzing GraphQL APIs are also listed. The document concludes with examples of exploiting common vulnerabilities like stored XSS, authorization bypass, and OS command injection.