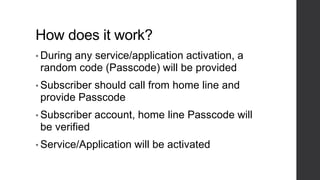
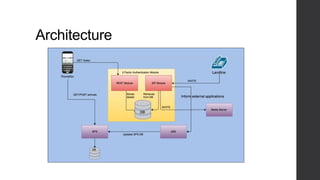
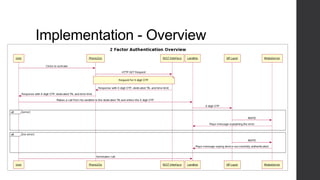
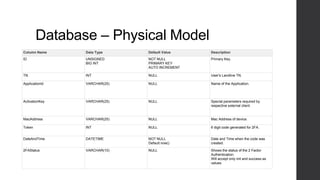
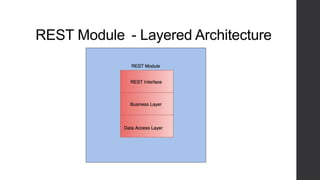
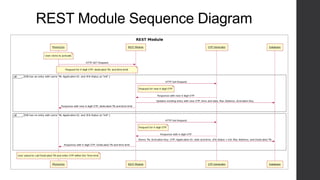
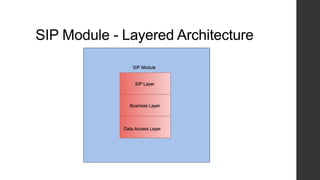
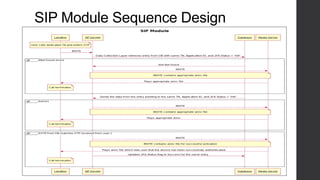
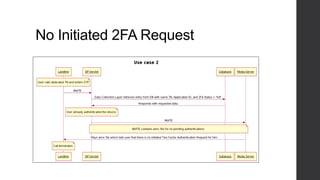
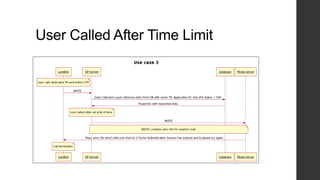
Two-factor authentication adds an extra layer of security beyond just a password. It works by providing a random code during service activation that the subscriber must then confirm by calling from their home phone line and providing the code. This helps verify that the subscriber is who they claim to be and is accessing the service from a trusted device. The system was implemented using technologies like Java, MySQL and Dialogic to allow two-factor authentication for any voice applications like Phone2Go. It includes REST and SIP modules with a layered architecture and uses cases like validating codes within the time limit or for incorrect codes.