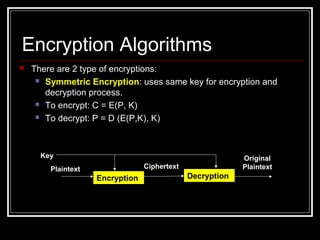
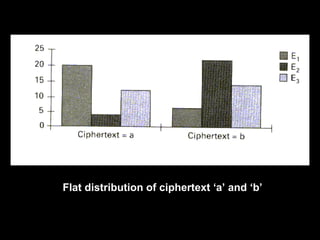
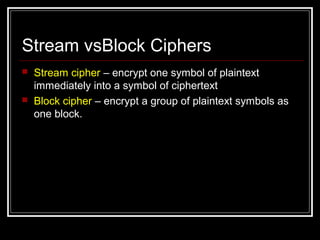
The document defines various terms related to encryption and decryption such as encryption, decryption, cryptosystem, plaintext, and ciphertext. It describes different types of encryption algorithms including symmetric encryption which uses the same key for encryption and decryption, and asymmetric encryption which uses different keys. It also explains different encryption methods such as substitution ciphers including monoalphabetic and polyalphabetic substitutions as well as transposition ciphers. The Caesar cipher and Vigenère cipher are provided as examples. Factors that can be analyzed to cryptanalyze ciphers are also outlined.