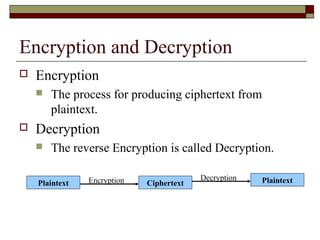
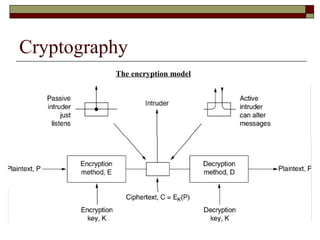
The document discusses cryptography concepts including encryption, decryption, symmetric and asymmetric encryption techniques, cryptanalysis methods like brute force attacks, and the importance of secret keys. Symmetric encryption uses a shared secret key by both sender and receiver, while asymmetric encryption uses different public/private keys. Cryptanalysis aims to discover plaintext or keys by techniques like brute force trials or exploiting algorithm weaknesses. Longer cryptographic keys increase the difficulty of brute force attacks breaking the encryption.