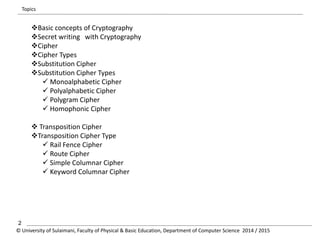
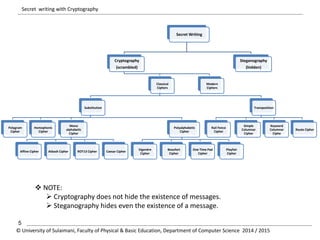
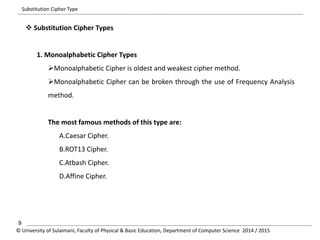
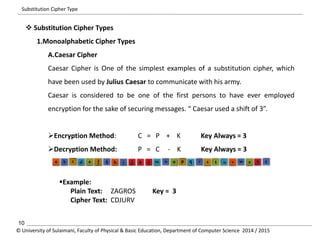
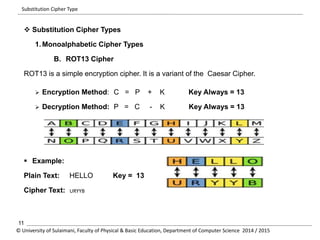
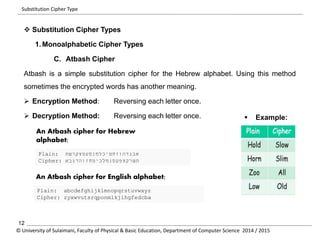
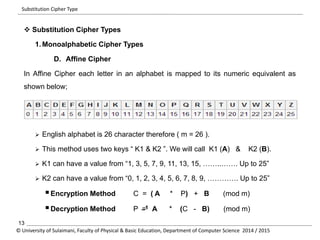
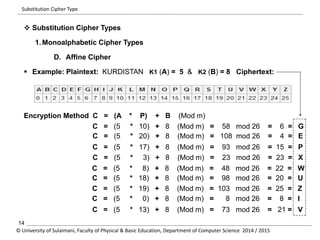
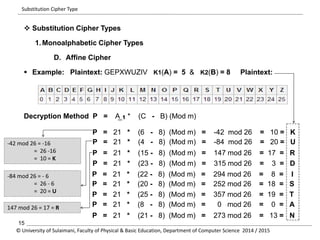
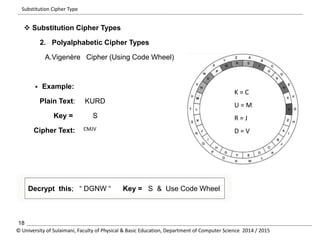
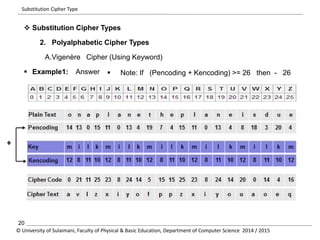
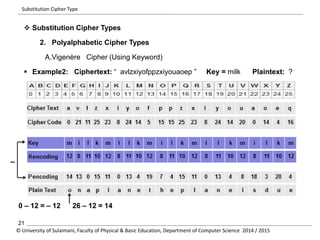
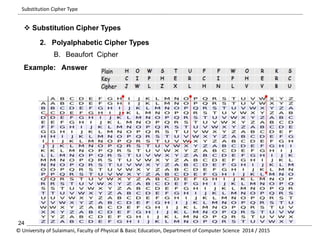
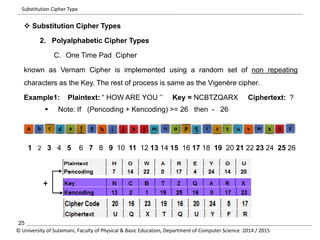
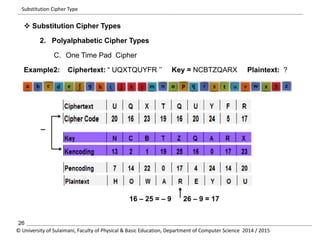
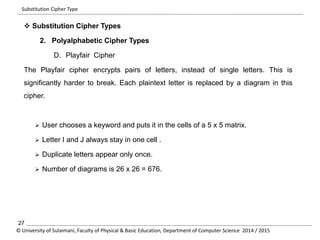
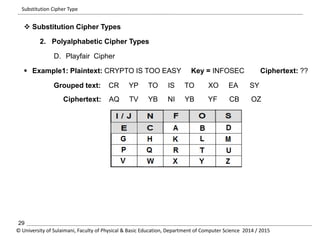
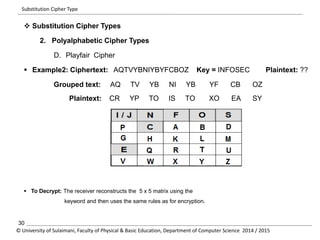
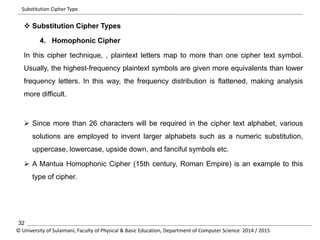
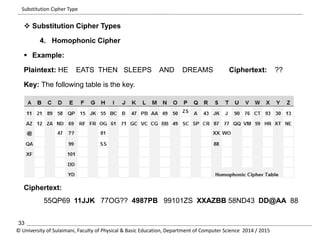
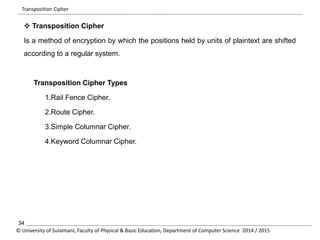
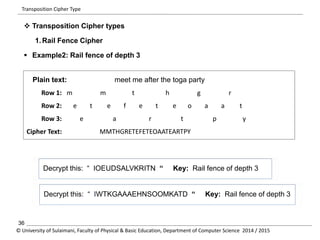
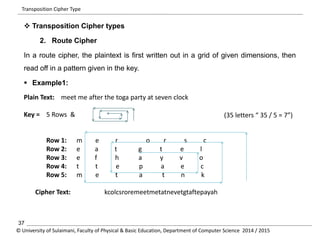
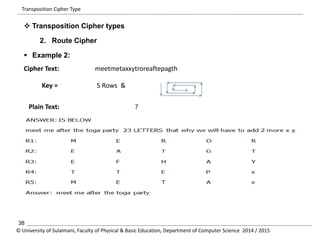
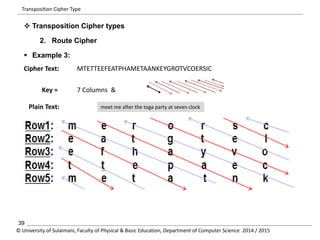
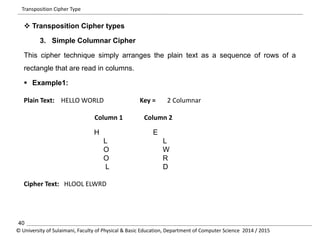
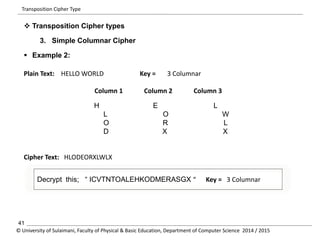
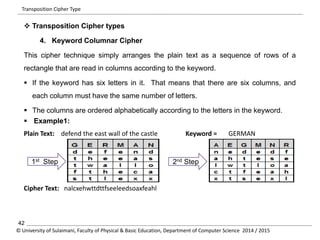
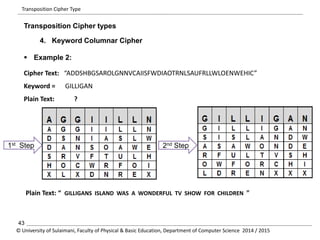
The document discusses the principles of cryptography, covering classical and modern ciphers, including substitution and transposition types. It outlines various encryption methods and their historical significance, such as the Caesar and Vigenère ciphers. Additionally, it explains the terminology related to cryptography and cryptanalysis, emphasizing the importance of secure communication.