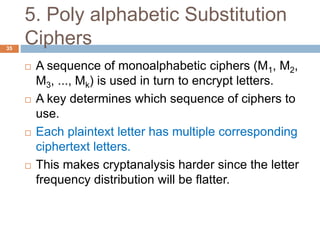
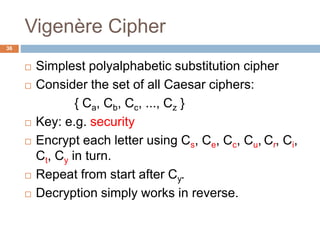
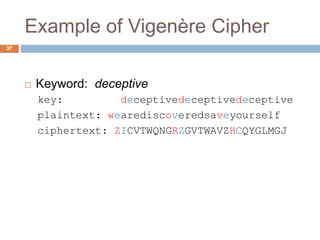
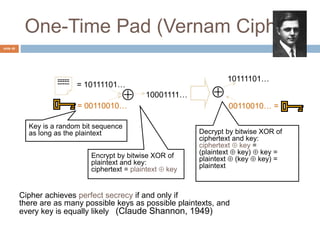
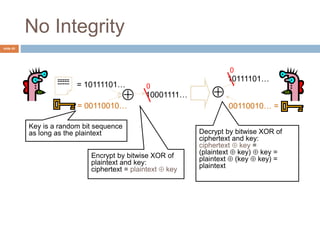
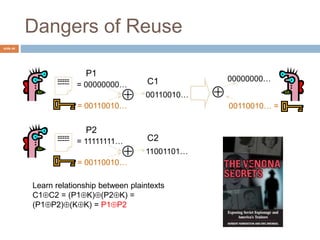
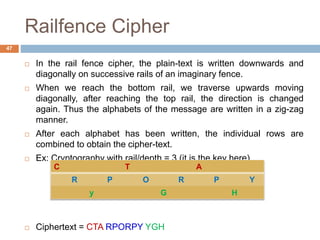
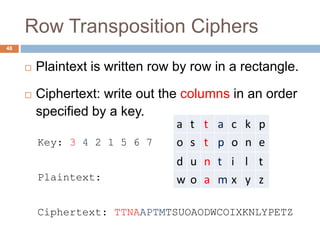
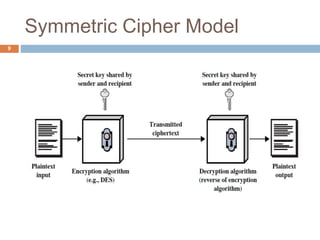
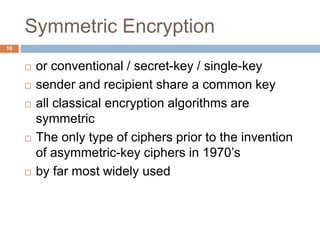
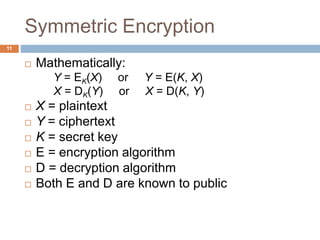
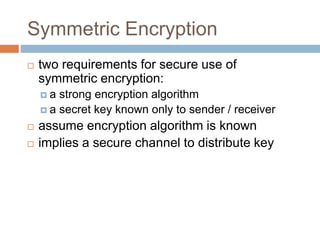
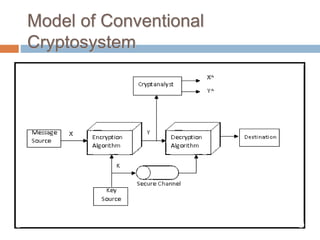
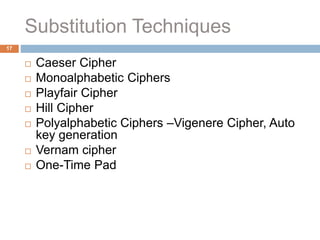
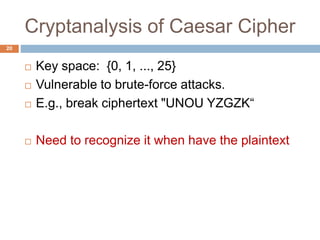
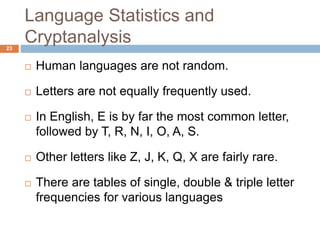
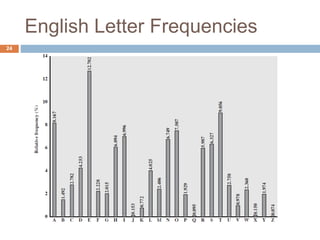
The document discusses classical encryption techniques such as substitution ciphers like the Caesar cipher and monoalphabetic cipher, transposition ciphers like the rail fence cipher and row transposition cipher, and polyalphabetic ciphers like the Vigenere cipher. It introduces basic concepts and terminology in cryptography such as plaintext, ciphertext, encryption, decryption, and secret keys. The goals are to introduce basic concepts and terminology of encryption and to prepare for studying modern cryptography.














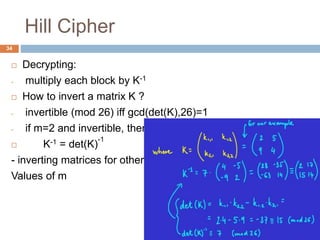
![4. Hill Cipher
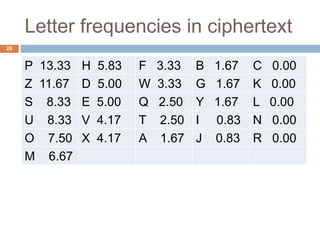
33
Key: an invertible m x m matrix (where m is the block
length)
[defines a linear transformation]
Encryption:
-view a block of m letters as a vector, multiply by the key
Example:
key K =
What is m ?
How to encrypt blah ?
2 5
9 4](https://image.slidesharecdn.com/classicalencryptiontechniques-200823190738/85/Classical-encryption-techniques-33-320.jpg)