Embed presentation
Download as PDF, PPTX



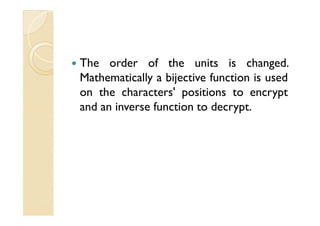


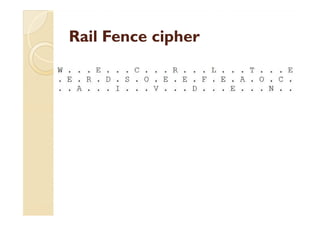


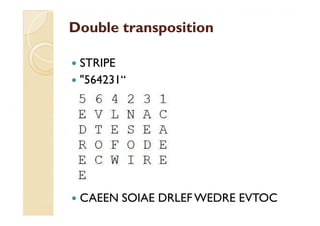





This document discusses transposition ciphers, which is a method of encryption where the positions of plaintext units are shifted according to a regular system to produce the ciphertext. The order of units is changed by using a bijective function on the characters' positions to encrypt and an inverse function to decrypt. Some common transposition ciphers mentioned include the rail fence cipher, route cipher, columnar transposition, double transposition, and Myszkowski transposition. Cryptanalysis techniques for transposition ciphers involve analyzing letter frequencies and determining the number of columns. One-time pads are also briefly discussed, which use random bit strings for encryption but have limitations such as requiring the key to be securely transported.













