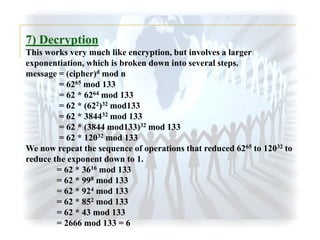
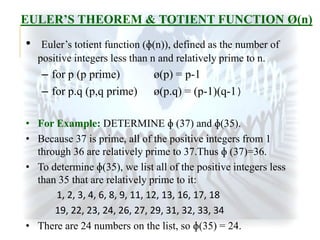
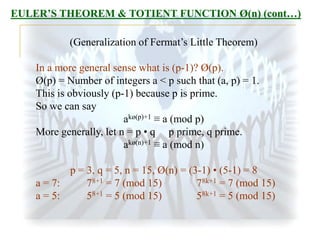
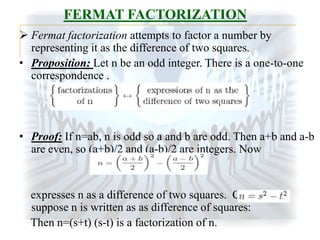
The document summarizes the RSA encryption algorithm. It begins by explaining that RSA was developed in 1977 by Rivest, Shamir and Adleman. It then provides an example to demonstrate how RSA works step-by-step, generating keys, encrypting a message and decrypting the ciphertext. Finally, it discusses some challenges with breaking RSA encryption, including brute force attacks and mathematical attacks based on factoring the encryption keys, as well as timing attacks that aim to deduce keys based on variations in processing time.
















![RSA - 640 November 2, 2005
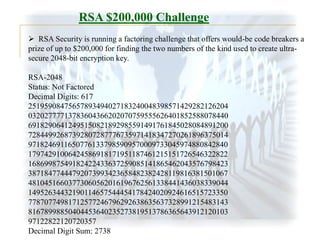
The factoring research team of F. Bahr, M. Boehm, J. Franke, T. Kleinjung
continued its productivity with a successful factorization of the challenge
number RSA-640, reported on November 2, 2005. The factors [verified by
RSA Laboratories] are:
16347336458092538484431338838650908598417836700330
92312181110852389333100104508151212118167511579
And
1900871281664822113126851573935413975471896789968
515493666638539088027103802104498957191261465571
The effort took approximately 30 2.2GHz-Opteron-CPU years according to
the submitters, over five months of calendar time. (This is about half the
effort for RSA-200, the 663-bit number that the team factored in 2004.)
Ref: RSA Laboratories - RSA-640 is factored!](https://image.slidesharecdn.com/rsaslides-140227114040-phpapp01/85/RSA-ALGORITHM-21-320.jpg)

![RSA - 576 Challenge
On December 3, 2003, a team of researchers in Germany and
several other countries reported a successful factorization of
the challenge number RSA-576. According to the
announcement by J. Franke:
The factors [verified by RSA Laboratories] are
3980750864240649373971255005503864911990643623425267
08406385189575946388957261768583317
and
4727721461074353025362230719730482246329146953020971
16459852171130520711256363590397527
Lattice sieving was done by J. Franke and T. Kleinjung
using Hardware of the Scientific Computing Institute and
the Pure Mathematics
REF: RSA Laboratories - RSA-576 is factored!](https://image.slidesharecdn.com/rsaslides-140227114040-phpapp01/85/RSA-ALGORITHM-24-320.jpg)


![References
[1] William Stallings, “The cryptography and network
security”.
[2] RSA Laboratories, http://www.emc.com/emcplus/rsa-labs/historical/the-rsa-factoring-challengefaq.htm.
[3] Dr. Herong Yang, “Cryptography Tutorials - Herong's
Tutorial Example”,
http://www.herongyang.com/Cryptography/.](https://image.slidesharecdn.com/rsaslides-140227114040-phpapp01/85/RSA-ALGORITHM-28-320.jpg)