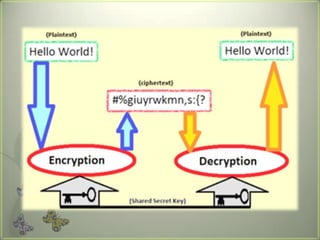
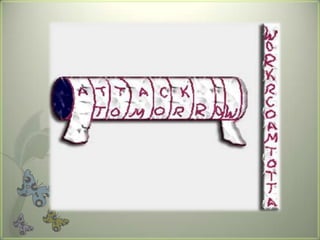
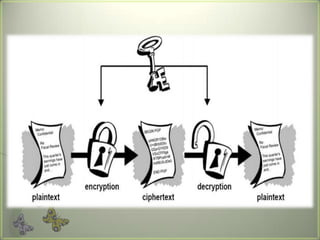
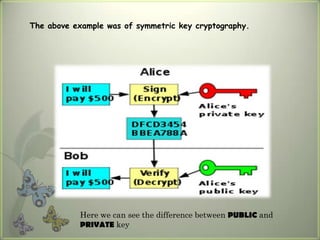
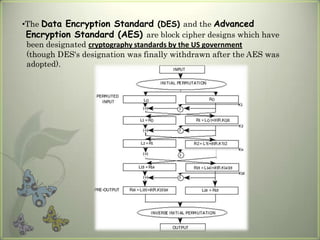
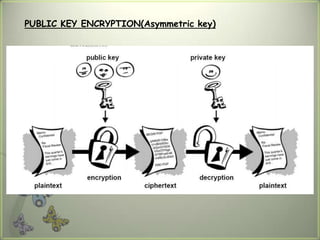
Cryptography is the practice of securing communications through techniques like encryption and decryption. It involves constructing algorithms to protect information from adversaries and ensure data confidentiality, integrity, and authentication. The main types are transposition ciphers, which rearrange letters, and substitution ciphers, which replace letters. Modern cryptography expanded with computers to encrypt any data and uses symmetric key cryptography, where senders and receivers share a key, and public key cryptography, where they have different keys. It has many applications including ATMs, email, remote access, and smart cards.