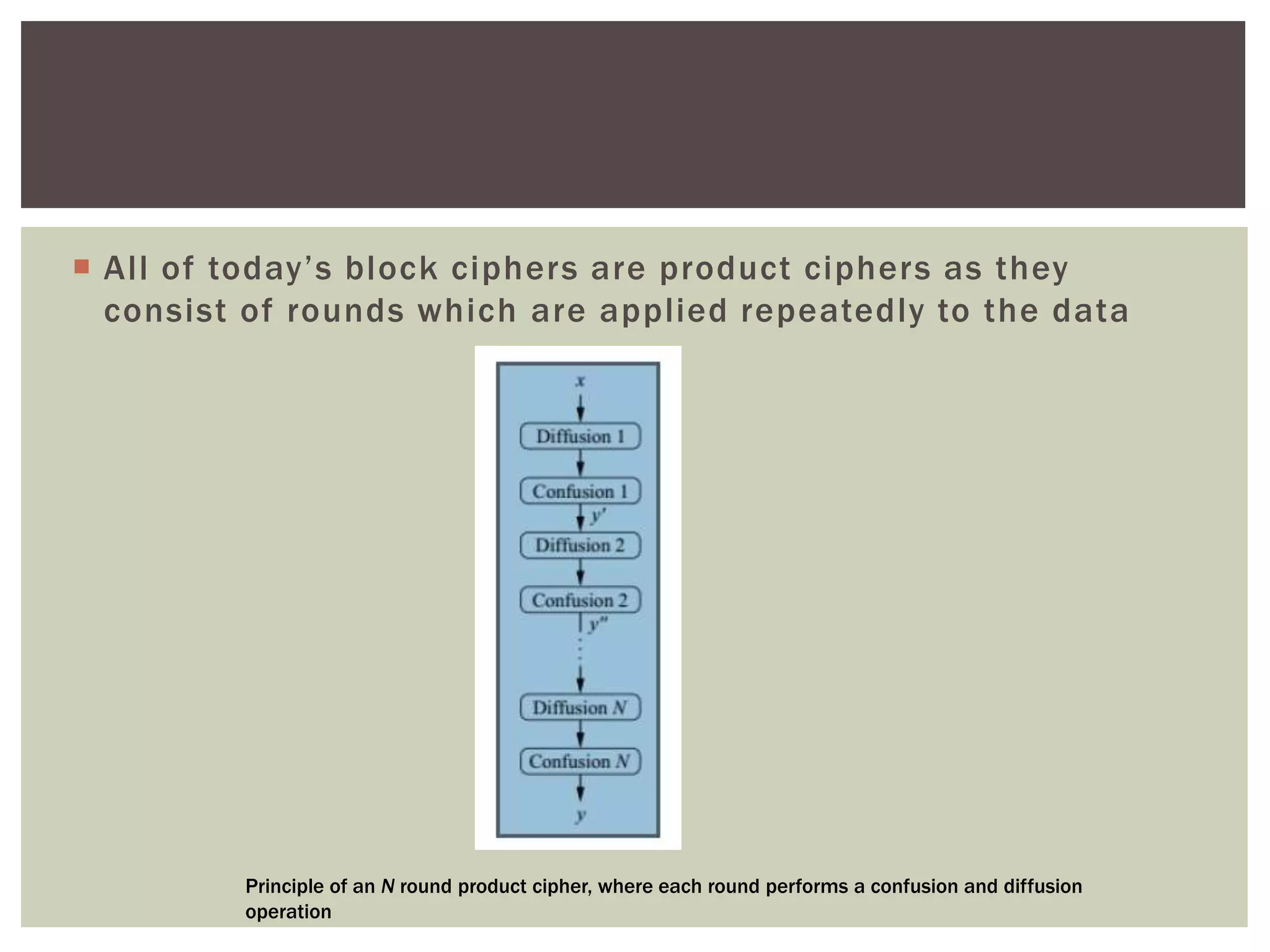
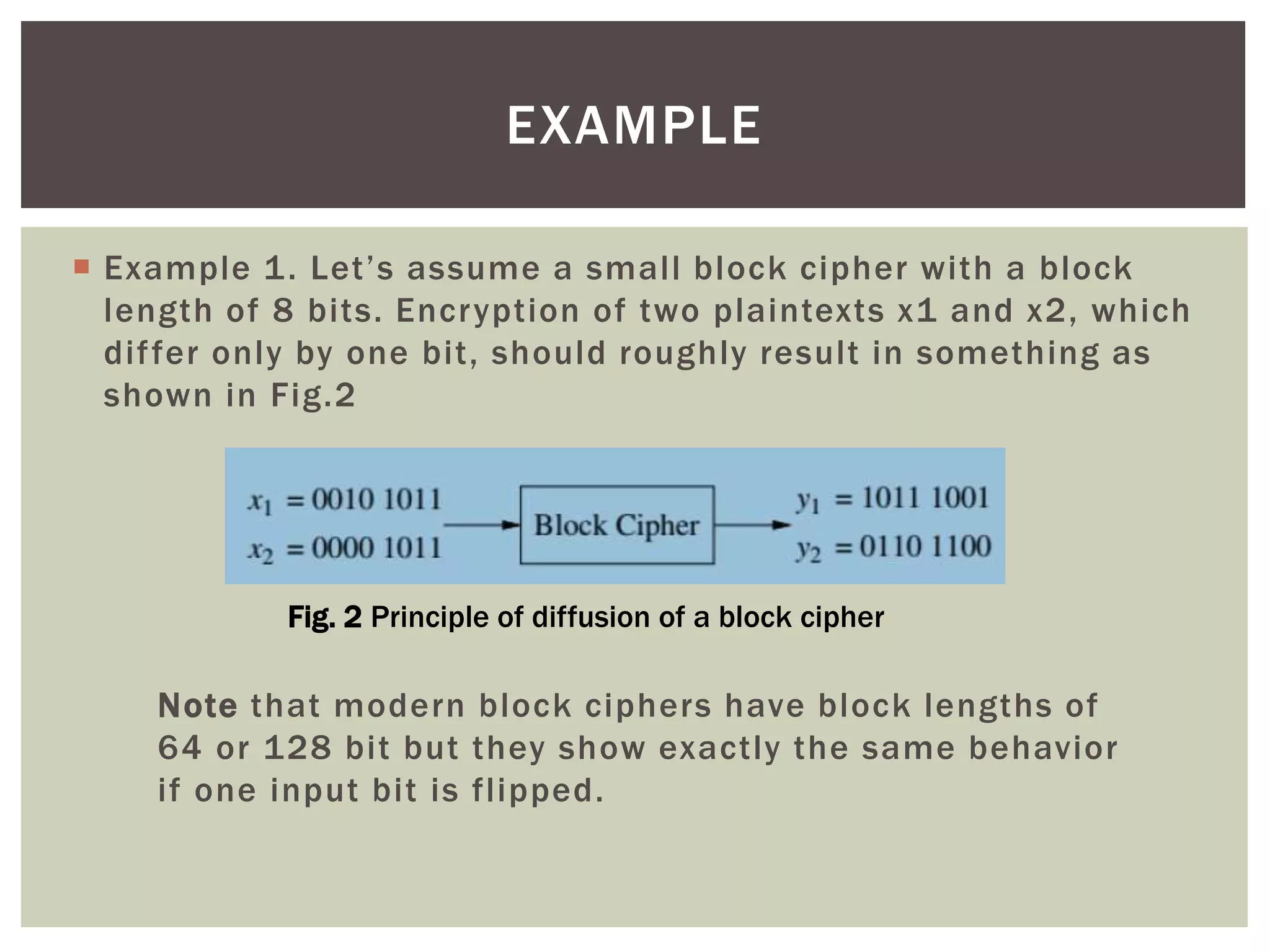
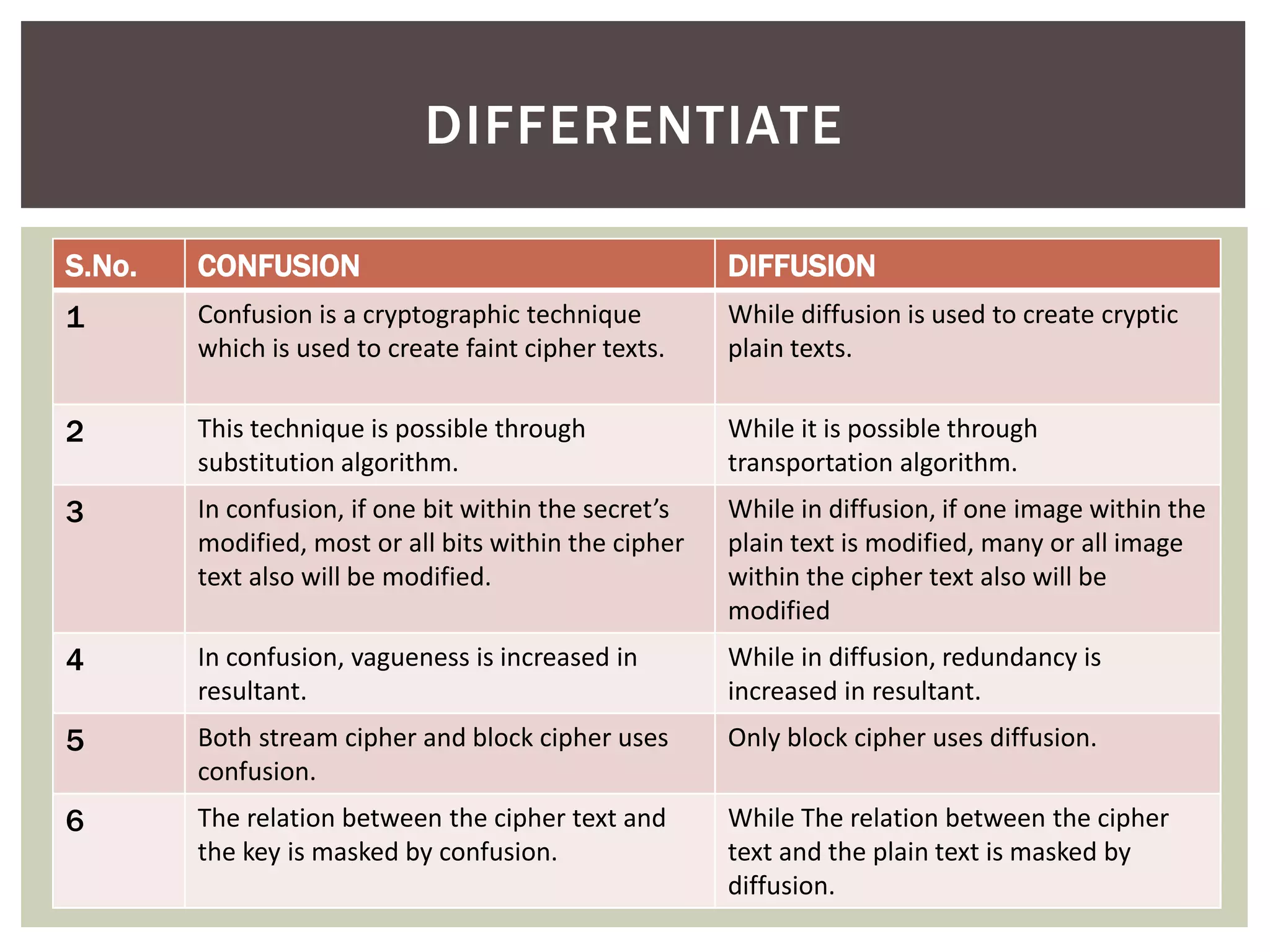
According to Claude Shannon, confusion and diffusion are two key properties for building strong encryption algorithms. Confusion obscures the relationship between the ciphertext and key by having each ciphertext bit depend on multiple key bits. Diffusion spreads the influence of each plaintext symbol over many ciphertext symbols. Modern block ciphers use repeated rounds of confusion and diffusion operations to build strong encryption.