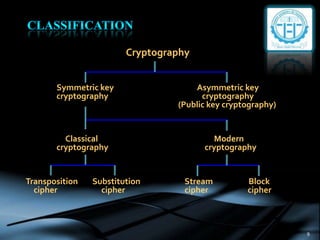
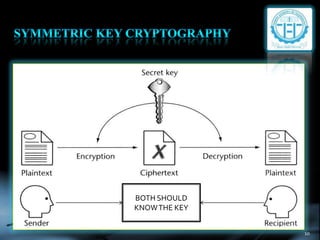
The document provides an overview of cryptography, defining key concepts such as encryption, decryption, and cryptanalysis. It discusses the two main types of cryptography: symmetric and asymmetric, along with various techniques used for securing data transmission. Additionally, it highlights the importance of cryptography in network security to protect sensitive information from unauthorized access.