Here are the solutions to the questions:
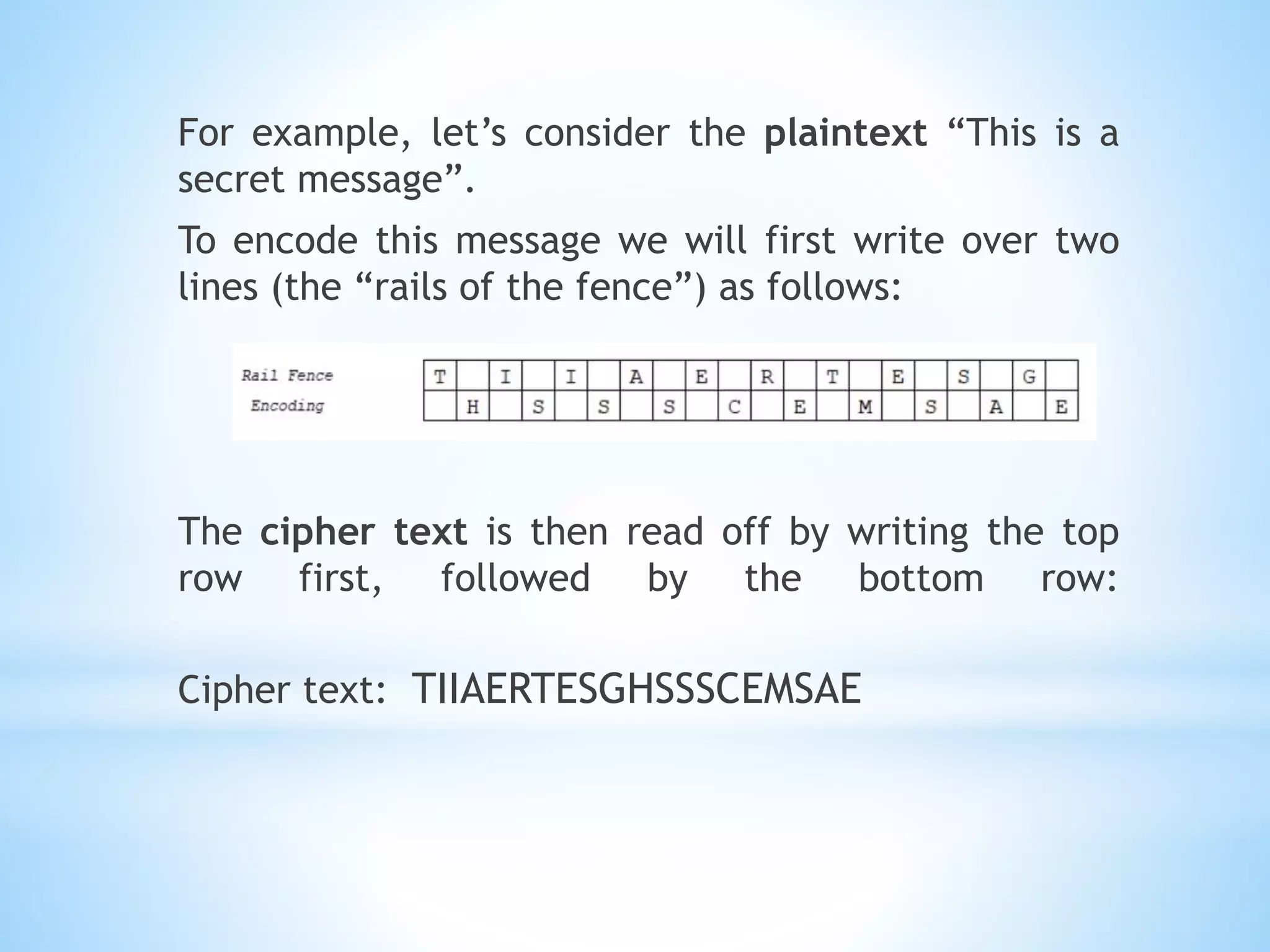
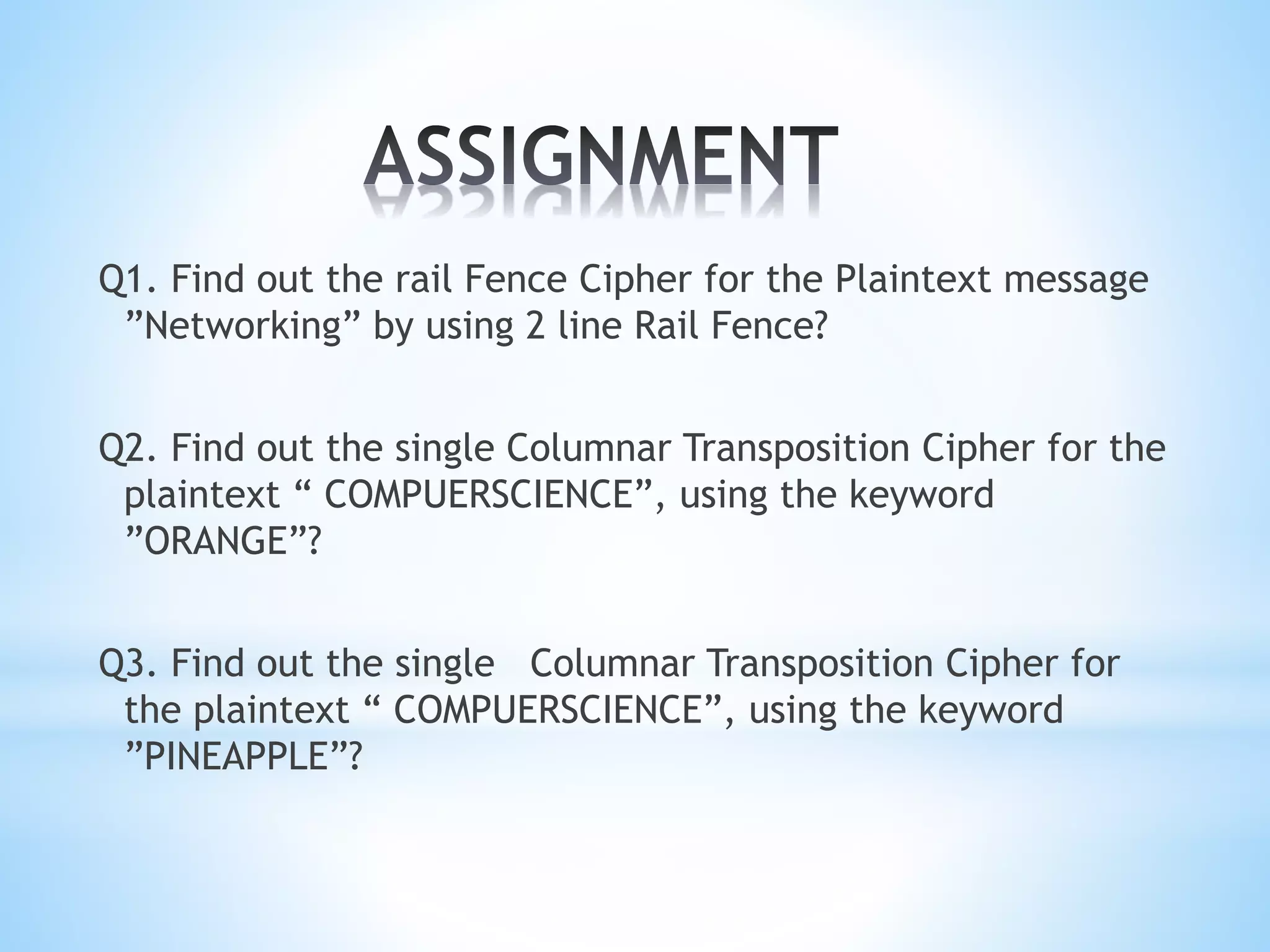
Q1. Rail Fence Cipher for "Networking" using 2 lines:
Nkttn
eorwige
Ciphertext: Nkttnorwige
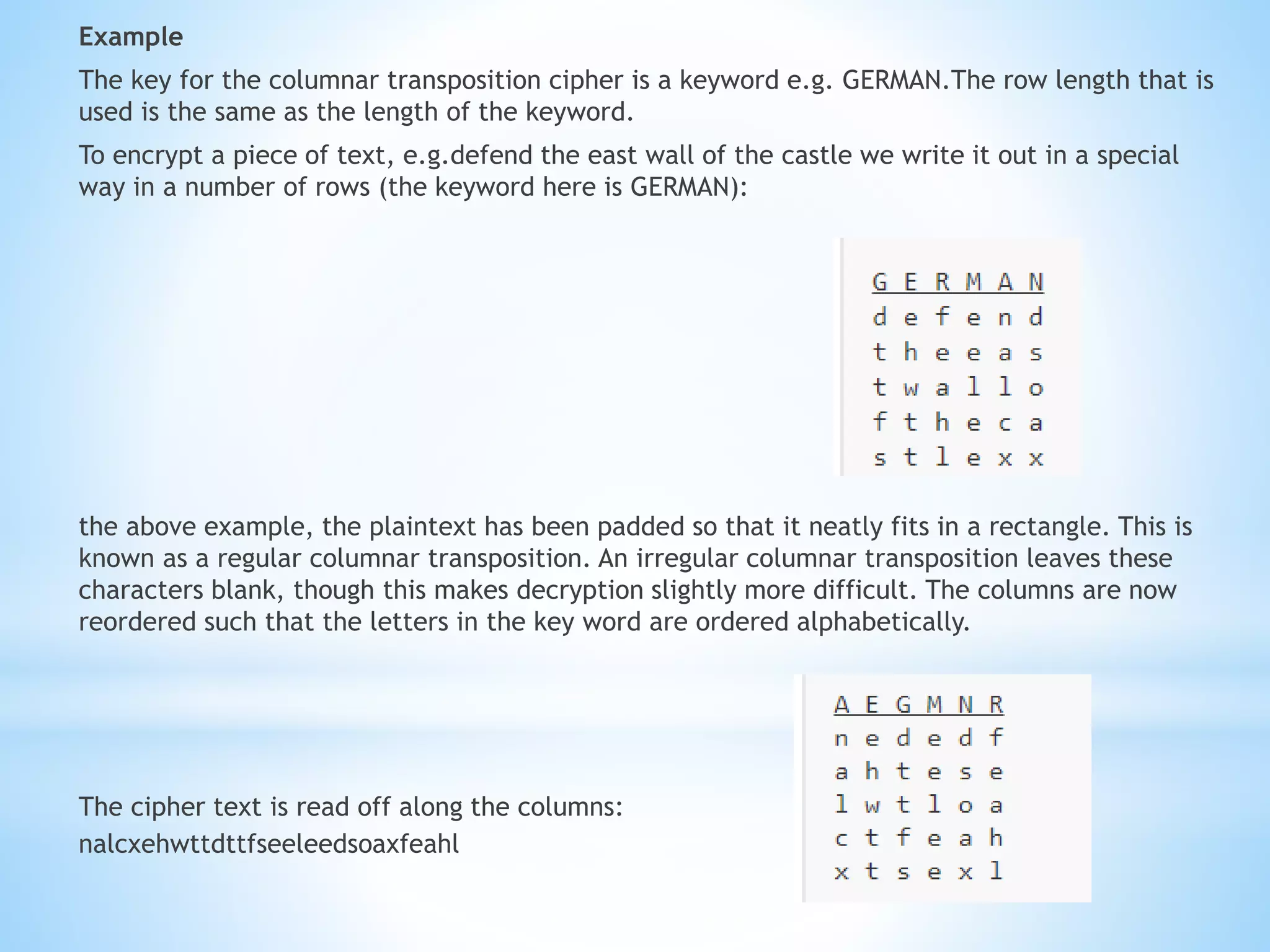
Q2. Single columnar transposition for "COMPUTERSCIENCE" using keyword "ORANGE":
C O M P U T
E R S C I E N
C E
Ciphertext: COEMNPUSTIERC
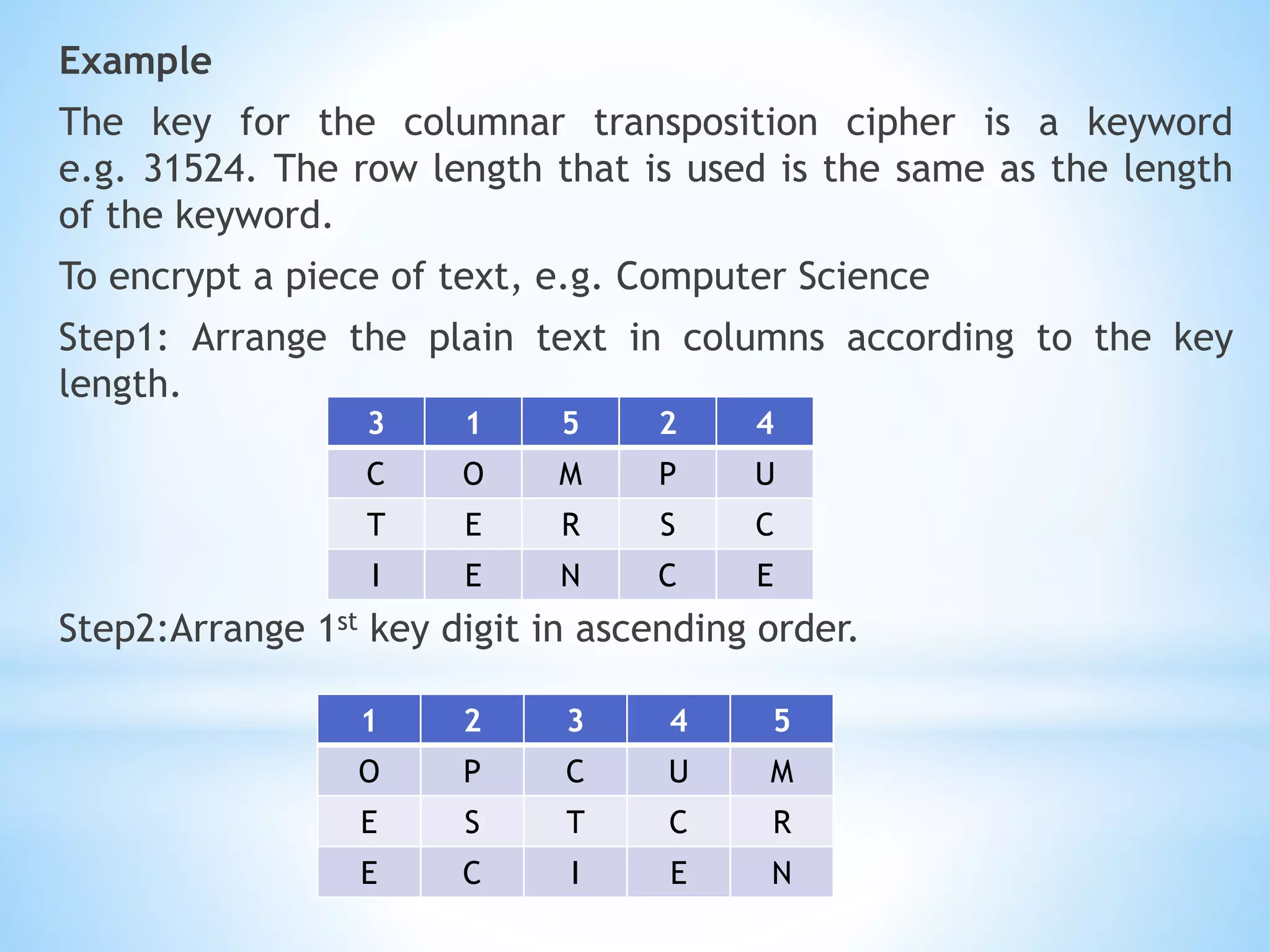
Q3. Single columnar transposition for "COMPUTERSCIENCE" using keyword "PINEAPPLE":
C O M P U T
E R S C I E N
C E
Ciphertext