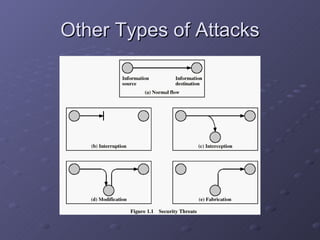
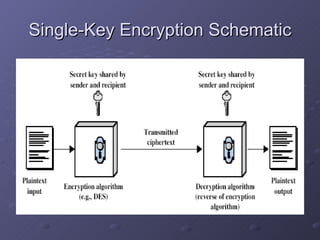
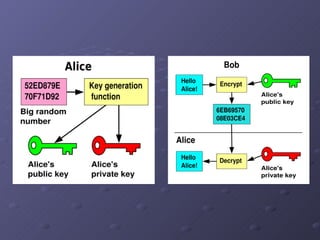
The document discusses the need for network security and cryptography due to the increasing use of computers and data transmission, highlighting various security attacks and mechanisms, including passive and active attacks. It covers conventional and public-key cryptography methods, detailing key generation and encryption processes such as RSA. Additionally, it emphasizes the importance of evolving security measures to keep pace with technological advancements.